What Is Security Posture? Definition & Why It Matters


In cybersecurity, an organization’s security posture is its overall readiness to prevent, detect, and respond to cyber threats. You can think of it as a “cyber health report” for your business that shows how well your defenses, policies, and people will withstand evolving attacks. Security posture isn’t just about having firewalls or antivirus tools; it’s about how well all of the layers of your security function to protect data, systems, and people.
A good security posture enables visibility into risk, promotes the speed of incident response, and generally helps ensure compliance. In contrast, a weak security posture has gaps introduced from outdated systems, unpatched vulnerabilities, or poor access controls; any of these can be leveraged by the attacker to enter the organization's defenses.
In this blog, we will take a look at what security posture is, its key components, why it matters for today’s enterprises, and some action items on how to assess and improve it.
Key Takeaways
- Security posture is a true measure of your organization’s cyber resilience and your ability to defend, detect, and recover from threats.
- A mature posture combines the right set of technologies, policies, monitoring, and awareness of personnel.
- Weak or antiquated postures result in elevated risk exposure, hinder compliance requirements, and diminish the credibility and trust of stakeholders.
- The use of repeated assessments and automation solutions can ensure appropriate levels of visibility into risks and overall system health in real-time.
- Continuous improvement, not a single audit, is the key as the threat landscape continues to grow and change.
Security Posture Definition
The security posture of an organization is a measure of its cybersecurity preparedness and is an indication of how well an organization can prevent, detect, respond to, and recover from cyber threats. A strong security posture is not just about having the latest tools or software in place, but rather the policies, procedures, employee awareness, and monitoring systems that function together to minimize risk and maintain compliance. It is essentially a snapshot of the organization's preparedness to defend itself against an evolving cyber threat at a point in time.
Example of Strong Security Posture vs Weak Security Posture:
| Strong Security Posture | Weak Security Posture |
|---|---|
| Up-to-date security tools that include firewalls, encryption, endpoint protection, identity access controls, etc. | Using outdated and inconsistent security tools, limited integration without meaningful connections to security processes and privileges |
| Policies and incident response plans that are written and updated periodically, and enforced strictly | Policies exist but are mostly disregarded, and little effort is made to enforce and revise those policies. |
| Employees are trained at least periodically on Social engineering attacks, cyber hygiene, and organizational security policies. | Employees are unaware of potential cyber threats or frequently exhibit careless behaviours. |
| Continuous monitoring, vulnerability management, and threat detection tools are employed. | System logging is limited, if even monitored at all (to detect threats being realized), and/or vulnerability management tools perform sub-optimized procedures with delayed detection. |
| Audits and assessments are performed regularly to ensure systems are in place to identify gaps or deficiencies. | There are no regular assessments of resources, leading to gaps in compliance without awareness of the gaps and leaving organisations with an increased exposure to an attack. |

Key Components of Security Posture
A strong security posture is built on many layers that interconnect and work together to assist in preventing, detecting, and responding to threats. It is these components that define how effectively your organization will mitigate risk, achieve compliance, and remain resilient against cyber threats. You should think of these components as the pillars that support your cybersecurity infrastructure; if one foundation is weak, the structure, as a whole, will become unstable.
1. Tools and Controls
Having a strong security posture begins with a solid set of integrated tools and controls that will form the defensive architecture of your organization. Firewalls and intrusion detection/prevention systems (IDPS) will be in place to help block or detect malicious traffic, endpoint protection will protect user devices, and data loss prevention (DLP) tools (and/or user encryption) will help protect sensitive data. Also, identity and access management (IAM) will ensure that only authorized users and systems can access critical resources. SIEM and SOAR platforms will aggregate security data, authorize an automated response, and provide real-time visibility for potential threats. Collectively, these technologies give you the power to continuously monitor (and automate) the detection, prevention, and response to risks like phishing, ransomware, DDoS attacks, and insider threats before they inflict damage.
Example: An endpoint detection and response (EDR) solution can automatically isolate an infected endpoint to stop the spread of malware, limiting downtime to the affected endpoint, and protecting the other endpoints and organizational network from the incident.
2. Policies and Procedures
Policies define the rules of engagement for the entire security ecosystem. They outline how data is to be handled, when to take action in the event of an incident, and the IAM system is one way to detail who is enforcing controls.
Procedures operationalize those policies by formalizing the actions taken to secure the organization and allowing others to reference whether those actions are compliant and defensible.
Example: A well-documented incident response plan enables the incident response teams to work effectively and collaboratively during a security breach, lowering the potential damage and recovery time.
3. Employee Training
People are frequently regarded as the weakest link in security, but trained employees become your first line of defense. Regular training, phishing simulations and awareness campaigns aid in recognizing threats and acting responsibly.
Example: When staff can identify and instantaneously report a phishing email, they prevent credential theft and unauthorized access before it even begins.
4. Vulnerability & Risk Management
This component seeks to identify, prioritize, and resolve weaknesses before the adversary has a chance to exploit them. Routine vulnerability scans, penetration tests, and automated patching all contribute to adopting a proactive approach against risk.
Example: A risk management dashboard that prioritizes vulnerabilities based on severity allows teams to patch the most important systems first, creating a risk vs reward mitigation approach to avoid the consequences of a high-impact breach.
5. Monitoring & Visibility
To sustain a robust security posture, continuous monitoring and real-time visibility across systems are essential. Tools such as SIEM (Security Information and Event Management) manage threat detection by aggregating and analyzing network data, while SOAR (Security Orchestration, Automation, and Response) focuses on automating an organization’s response to an incident to cut down the time it takes to react. EDR (Endpoint Detection and Response) features ongoing monitoring and leads to the investigation of suspicious activity to better protect endpoints. Security reporting and communication at regular intervals create visibility and accountability, and enable informed decision-making, all designed to lead to enhancements.
Example: Ongoing monitoring in a hybrid cloud environment, for instance, can detect unusual login patterns that might suggest compromised identities.
💡Learn how a Security Operations Center (SOC) enhances continuous monitoring and threat detection across your environment.
6. Governance & Compliance
Governance provides structure and accountability for the management of security. Governance holds policies, tools, and practices accountable to standards such as ISO 27001, NIST, or GDPR. The goal of compliance processes is to prove that controls are performed as intended and are documented - the basis of trust with customers and regulators alike.
Example: Regular audits and access reviews, for example, would ensure that only authorized users can access sensitive environments, reducing both risk and compliance.
💡 Identity Confluence simplifies governance by automating compliance reporting, enforcing access policies, and ensuring every identity, human or non-human, remains auditable and compliant by design.

Why a Strong Security Posture Matters
A strong security posture is not merely about stopping attacks but about keeping your organization resilient, compliant, and trustworthy. As threats become more complex and compliance stricter, a mature posture enables organizations to detect, absorb, and recover from threats on time without a lot of friction.
1. Threat Mitigation
A mature security posture allows early detection and fast remediation. Continuous monitoring, layered defenses, and proactive patching procedures make it difficult for attackers to exploit vulnerabilities. For example, if an endpoint security system detects ransomware behaviour and quickly isolates the device in real time, the attack cannot spread across the network. A strong posture does not eliminate risks, but it allows the organization to respond faster, reducing overall damage.
2. Business Continuity
Cyber incidents destabilize operations, delay projects and revenue impact on businesses. Creating a mature security posture originating from processes and policies, as well as backup systems and a recovery plan, makes it possible for organizations to continue operating amid an attack. For instance, if there is a compromise to a cloud service, organizations with redundant systems or automated failover can use the other system while they contain the issue. In summary, a strong and resilient posture allows the business to carry on, significantly protecting productivity and the customer experience.
3. Regulatory Compliance
Maintaining a robust posture allows you to align your security practices to frameworks such as ISO 27001, NIST, GDPR, or HIPAA. Conducting periodic assessments, enforcing policies, and implementing access controls demonstrates to your clients that their data is protected, which is critical information for any regulated business, so that they are not penalized and maintain their certification.
For example, if a healthcare provider has strict IAM and audit controls, they would not only comply with HIPAA but also mitigate insider threat risks. Regulation is not just a matter of avoiding fines or other penalties; regulation means developing an organized, auditable security practice that regulators and stakeholders easily identify as trustworthy.
4. Customer Trust & Cost Savings
A breach can tarnish trust and reputation much faster than any technical control failure. When a customer sees and trusts your security posture, it reassures them that their data is kept safe and that reasonable care is taken when handling it. Trust can certainly lead to loyalty, market opportunity, and incident cost reductions over time.
For example, companies that engage and monitor their posture proactively and consistently report breach incidents had considerably lower total costs associated with recovery, remediation and increased premiums (or other costs) than companies that waited and reacted to incidents after they happen.
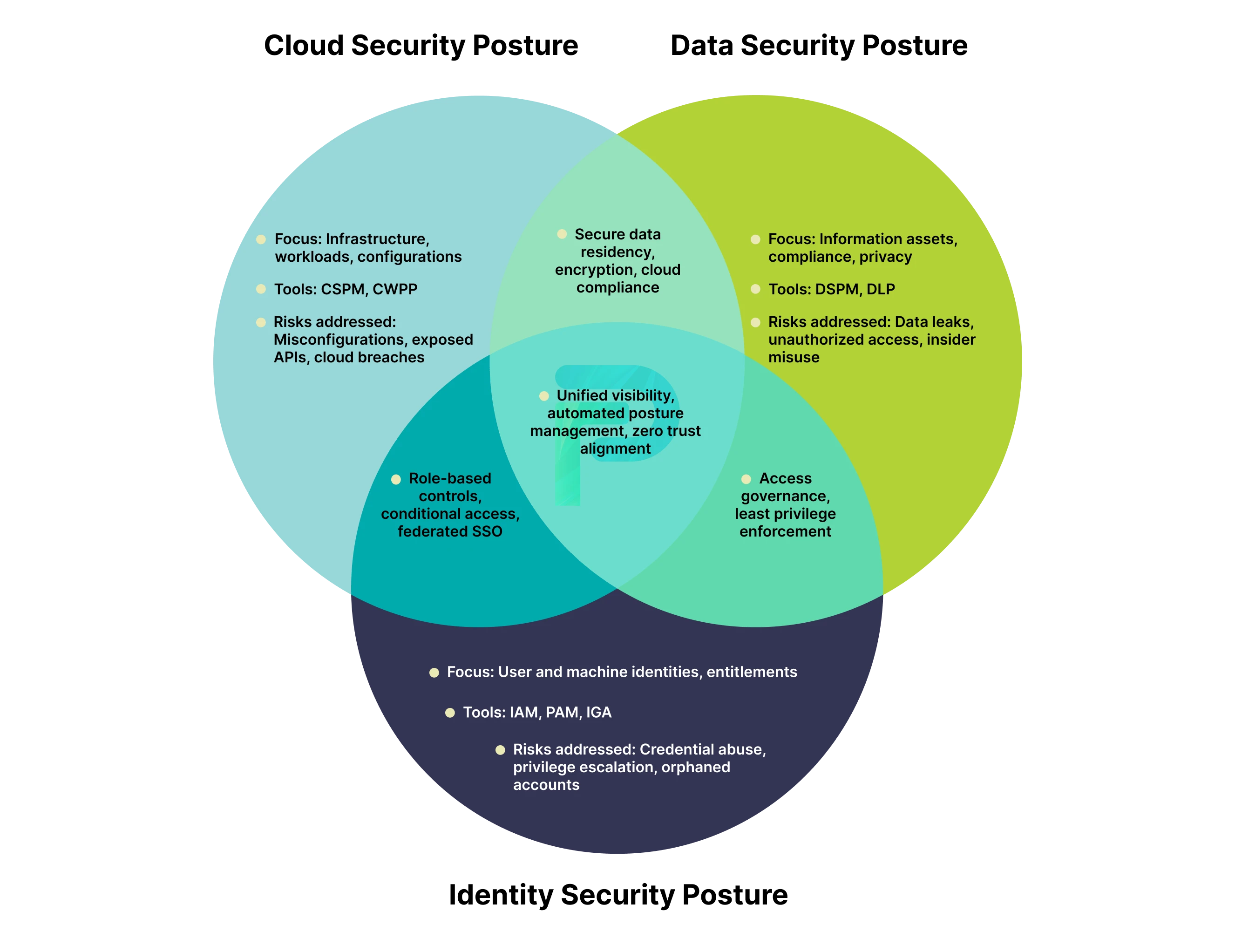
Types of Security Posture
Security posture is not something uniform and singular; it varies depending on which component of your digital environment you're securing. The three primary areas, cloud, data, and identity, overlap and, in unison, describe your organization’s overall resiliency.
Each domain supports the other: secure identities protect data; secure data enables compliance; secure cloud environments minimize exposure. Understanding how these layers of security interact enables an organization to understand security blind spots and better its defenses as a whole.
1. Cloud Security Posture
Cloud security posture focuses on securing your cloud environments, workloads, and configurations. It is the continuous evaluation of misconfigurations, access controls, and compliance across cloud providers.
A mature cloud security posture includes:
- Continuous monitoring of cloud configurations (CSPM)
- Identity and access management to cloud resources
- Encrypting sensitive data in transit and at rest
- Overseeing shadow IT and compliance audits
Its objective is to avoid data exposure, misconfigurations, and unauthorized local access across hybrid or multi-cloud environment infrastructure.
2. Data Security Posture
Data security posture describes how well your organization secures sensitive information and regulated information while it is in use and throughout its lifecycle. The data security posture includes processes for data discovery, classification, encryption and access governance (i.e., ensuring the appropriate person has access at the right time).
A mature data posture includes:
- Data discovery and classification that is automated
- Policy-based access control and masking
- Data loss prevention (DLP) solutions
- Continuous inspection for anomalous access or data leak
The objective is to protect sensitive data wherever it is - on-prem, in the cloud or shared outside the organization.
3. Identity Security Posture
Identity security posture is concerned with managing and protecting human and non-human identities throughout the enterprise. It is an assessment of how strong the governance is around identity systems, privileges, and authentication.
A strong identity posture includes:
- Strong authentication and MFA policies
- Privileged access management (PAM)
- Continuous identity lifecycle management
- Real-time detection of anomalous access behaviour
The objective is to mitigate identity-based risk, eliminate standing privileges, and maintain accountability at every access point.
Security Posture Assessment: How to Evaluate It
A security posture assessment allows you to learn how well your organization can prevent, detect, and mitigate threats. Think of it as a health check; it allows you to know your strengths and weaknesses, in addition to the maturity of your cybersecurity ecosystem.
Taking a structured approach means that you are not simply reacting to incidents but building your defense continuously. Here’s how you can conduct an effective assessment:
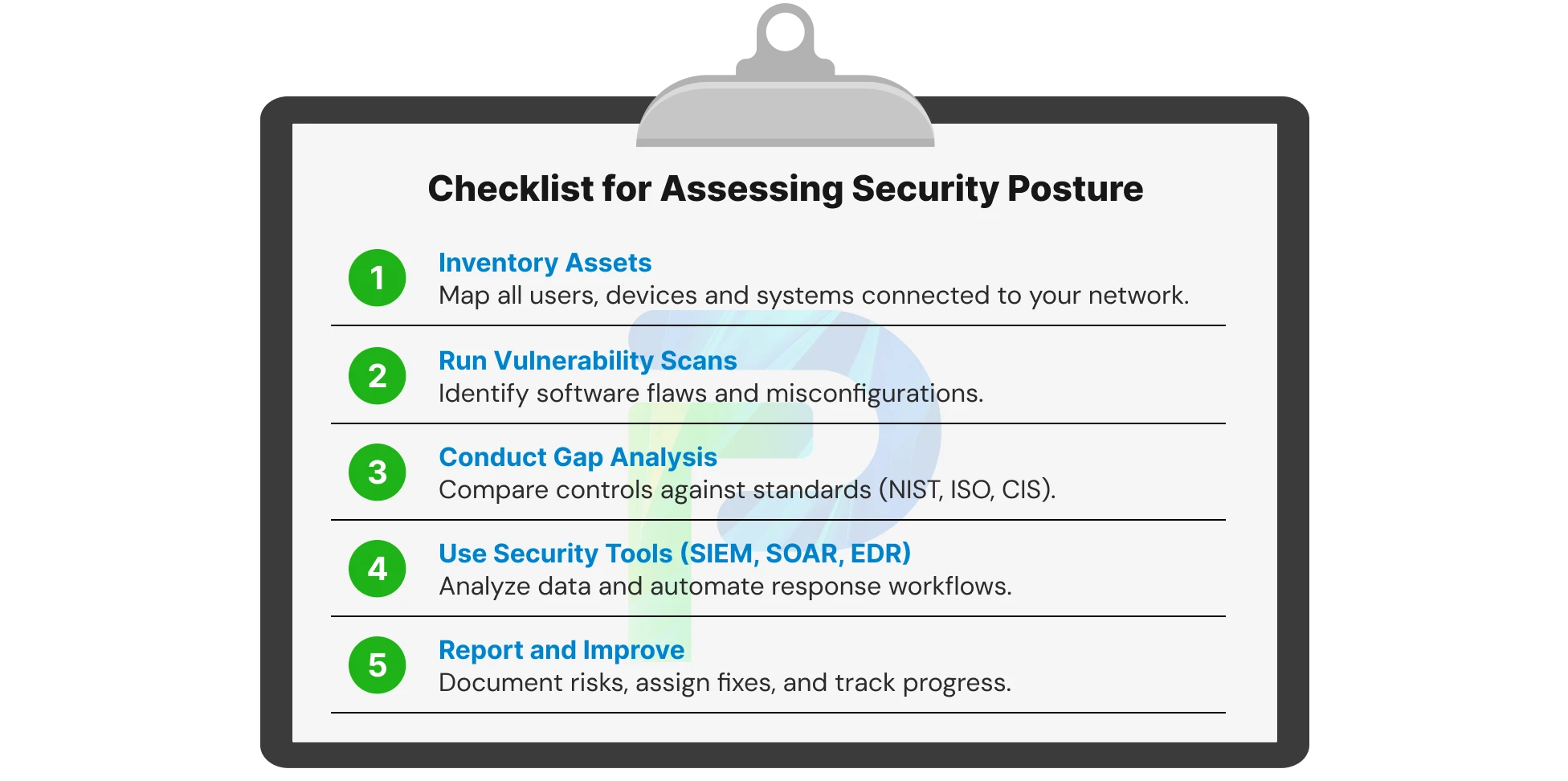
Step 1- Inventory All Assets
Begin by identifying everything that is connected to your environment, such as personnel, devices, servers, applications, cloud instances, and APIs.
- You should classify assets by criticality and sensitivity.
- You should document ownership and routinely update your asset inventory.
Purpose: You cannot protect what you do not know exists.
Step 2- Assess Identities and Access Controls
Examine all human and non-human identities in your environment, including users, service accounts, APIs, and automation scripts.
- Assess for over-permissioned accounts, orphaned identities, and inactive users.
- Verify that least privilege principles are applied consistently.
- Confirm multi-factor authentication (MFA) and single sign-on (SSO) configurations.
- Map identities to business-critical systems and sensitive data.
Purpose: Knowing who or what has access—and if that access is appropriate—is essential to reducing attack surfaces and improving security posture.
Step 2- Conduct Vulnerability Scans
You should run automated vulnerability assessments across all of your systems, applications, and networks. Vulnerability assessments will identify outdated software, weak configurations, and unpatched services.
- Some vulnerability assessment tools you can use are Nessus, Qualys, and Rapid7.
- You should determine priorities based on exploitability and business impact.
Purpose: Identify weaknesses before the adversary does.
Step 3- Conduct a Gap Analysis
Assess your current controls and practices against industry standards (NIST CSF, ISO 27001, CIS Controls)
- Identify gaps in technology, policies, and training.
- Map each gap to a remediation plan.
Purpose: Close the current state versus desired security maturity gap.
Step 4- Analyze and Correlate Data
Use analytic tools to identify trends, anomalies, and indicators of compromise in your environment.
- Use a SIEM (Security Information and Event Management) to correlate logs and identify threats.
- Use SOAR (Security Orchestration, Automation, and Response) to automate workflows.
- Use EDR/XDR (Endpoint Detection and Response, Extended Detection and Response) to get visibility at the endpoint.
Purpose: Get insight into where you are in terms of your security posture, and to detect and respond faster to new threats.
Step 5- Review and Report Results
Document, summarise, and report the key findings, risky observations, and recommendations in a simple and actionable manner.
- Provide prioritized recommendations for remediation and identify an owner.
- Provide some KPIs to measure improvement over time.
Purpose: Turn findings from the assessment into a roadmap for continuous security improvements.
How to Improve Your Security Posture
Enhancing security posture is not a defined endpoint but rather part of a looping, ongoing effort. When one area is improved, it enhances another area, making the overall cybersecurity posture more resilient and adaptive. Organizations should take on these essential activities:
1. Automate Asset Inventory
Having an up-to-date record of all the assets, their hardware, software, users and cloud resources, is fundamental.
- Employ tools that automatically discover all assets hosted on-premises, in cloud environments, and in SaaS environments, and watch for flatpoints to identify new assets or assets not previously recorded.
- Identify and prioritize criticality, sensitivity and business impact level of assets for monitoring and further protection.
- Combine the asset inventory with the CMDB ( Configuration Management Database) for one view of accountability.
This helps in understanding blind spots, ensures that critical systems receive protection, and provides additional context around reducing risk in processes to improve overall vulnerability management and efficiencies.
2. Update Policies & Incident Response Plans
Conduct reviews of security policies, procedures, and incident response plans to update based on current threat profiles and compliance changes.
- Standardize access control rules, acceptable use policies, escalation, and incident reporting practices.
- Tabletop exercises, simulated attack scenarios, or red-team exercises would enable systems to identify current state readiness towards incident response and complete processes as documented.
- Keep policies aligned with regulatory requirements such as GDPR, HIPAA, or ISO 27001.
This collecting, maintaining, tracking and reporting of policies improves organizational resilience against incidents, decreases incident response reaction time, and ensures continued compliance with agreements and regulations.
3. Train Employees Regularly
Often, your employees are the first line of defense, so follow up with continuous education on cybersecurity.
- Conduct phishing simulations and social engineering tests and offer refresher courses, which can be customized to specific job roles.
- Have a simple way to report suspicious emails, emails that contain links, and strange system activity and continue communicating this information to your employees.
- Train employees on cloud hygiene, password best practices, and data handling procedures.
This helps diminish human error, which is still one of the leading causes of all breaches, while also creating a security-wise workplace culture.
4. Implement an IGA Solution
The purpose of Identity Governance & Administration (IGA) solutions, like Tech Prescient’s Identity Confluence, is to centralize and automate user access and authorization management across an organization.
- Automatically provision and deprovision accounts, including human and non-human identities.
- Enforce least-privilege access and segregation of duties policies.
- Automated user access reviews and certification of compliance.
- Provide a single source of truth for all identities and their entitlements.
This ensures appropriate access is maintained, reduces the amount of risk from over-permissioned accounts, improves compliance, and adds to your Zero Trust and monitoring efforts.
5. Apply Zero Trust Principles
Zero trust follows the principle of ‘never trust, always verify,’ which assumes that no user, device, or application should be trusted. It is a process of constant verification. Utilize these zero trust frameworks across networks, systems, or applications.
- Constantly have users, devices, and applications verify identity before allowing them access.
- Utilize least-privilege access, micro-segmentation, and conditional access policies to help limit lateral movement.
- Use Zero Trust to enforce the protection of your cloud, APIs, and even non-human identities, such as automation scripts or service accounts.
This limits the blast radius from a potential breach, contains a compromised system, and enforces access policies that are context-aware, provide access based upon time, and limit access.
6. Use Continuous Monitoring Tools
Implement solutions that monitor your traditional networks, endpoints, cloud resources, and applications in real-time.
- Utilize SIEM (Security Information and Event Management), SOAR (Security Orchestration, Automation, and Response), or EDR/XDR platforms that facilitate alerting or automated response.
- The analysis of logs and the correlation of events can uncover anomalies, unusual access patterns and potential threats.
- Effective monitoring of your environment should also take place across on-prem, cloud, and hybrid environments to ensure consistent monitoring.
This will assist you in detecting considerations early, taking proactive remediation steps, and maintaining a robust overall situational awareness throughout the organization.
7. Conduct Periodic Security Audits
Complete an in-depth review of all systems, configurations, access privileges, and compliance posture periodically.
- Consider auditing permissions, account provisioning, patch levels, and configuration reviews.
- Document your findings, remediation activities, and rule changes in light of the audit outcomes.
- Re-evaluate both internal and external perspectives (or third-party audit) in an objective evaluation of the organization’s posture.
This guarantees the security controls are effectively in place and supporting continual improvement, while also producing potential reporting for regulators.

Common Challenges & Risks in Security Posturing
Assuring a strong security posture will always have challenges associated with it. Organizations frequently face persistent gaps, creating vulnerability and lowering the value of the associated cybersecurity program. Here are some of the more common challenges for organizations:
1. Over-Permissioned Users
Challenge: Users often amass excessive access permissions over time, meaning they have more permissions than are necessary for their role. Over-Permissioned users are a result of changes in role, temporary projects, and stale access reviews.
Risk: Over-Permissioned users increase the impact of a compromised account, allowing attackers to move laterally and access sensitive infrastructures and data.
Quick Fix: Implement least privileged access policies, and regularly review entitlements to ensure permissions are in line with the user's current role.
💡See how identity lifecycle management ensures proper provisioning and deprovisioning of user accounts to reduce risk from over-permissioned identities.
2. Shadow IT
Challenge: Employees may deploy unauthorized applications, devices, or cloud services without IT approval. This “shadow IT” subverts established security controls.
Risk: Shadow IT introduces blind spots and unmonitored data flows that can create vulnerabilities for pervasive attacks, and even potential compliance violations.
Quick Fix: Maintain an up-to-date inventory of approved/purposed-for-use tools, keep usage policies enforced and encourage sanctioned and secure alternatives.
3. Outdated Tools & Technology
Challenge: Many legacy systems, unpatched software, or outdated security tools do not align with today's threat landscape.
Risk: Attackers can easily exploit weaknesses in outdated tools. Unsupported systems may not be compatible today with current monitoring or response technology.
Quick Fix: Create a regular patch management schedule and upgrade programs for systems and tools; ensure critical updates are prioritized; integrate modern security tools and systems that allow for automation and continuous monitoring.
4. Lack of Training & Awareness
Challenge: Employees are often the weakest link in an organization's cybersecurity; however, without security training, they may become victims of phishing, mishandle sensitive data, or bypass security protocols.
Risk: Even with technical controls in place, breaches or compromised data may still happen due to human error, and the risk may ultimately harm the entire organization's security position.
Quick Fix: Implement regular role-based security training programs; simulate phishing attacks; and highlight policies to safely handle sensitive data and secure credentials.
5. Inconsistent Policy Enforcement
Challenge: Policies can be created, but have inconsistent implementation across areas such as departments, networks, or cloud environments.
Risk: The uneven implementation creates areas of opportunity for an attacker and defeats the purpose of compliance with an organization's overall security posture.
Quick Fix: Implement automatic compliance where adequate, implement a central compliance management tool, and periodically audit compliance.
6. Insufficient Visibility & Monitoring
Challenge: Organizations are unable to detect anomalous activity or vulnerabilities in real time without comprehensive monitoring.
Risk: Areas of blind spot allow threats to go unnoticed, increasing breach risks and delaying response to incidents.
Quick Fix: Implement continuous monitoring solutions to on-prem, cloud, and hybrid environments, combine the logs with SIEM/SOAR tools and set alerting for suspicious behaviour.
Final Thoughts
An organization’s security posture is not the one-time completion of a checklist but rather an ever-changing journey that demonstrates the organization’s ability to prevent, detect, and respond to threats. A robust security stance reflects the amalgamation of people, processes, and technology while confidently assuring that risks are known, monitored, managed, compliance is achieved, and business vitality is secured. Regular assessments, policy and procedure modifications, continuous monitoring, and training of staff are crucial components to maintaining and improving an organization’s cybersecurity posture over time.
A security posture entrusts responsibility for understanding how to stay secure at every state, level, and team column. Achieving a solid security posture takes commitment and drive from financial sponsors of security, IT and security leadership, and even the front-line teams comprising the organization, engraining security into the organization’s DNA. By proactively managing vulnerability to inform patching, enforcing policies and frameworks, and leveraging automation and modern security frameworks, organizations can reduce risk, protect sensitive information, and develop customer and partner trust.
NEXT STEPS
Take Control of Your Security Posture Today
Ensure continuous protection and compliance by assessing risks, monitoring systems, and enforcing policies across your organization.
- Become secured with Identity Confluence
- See Identity Confluence in action.
Frequently Asked Questions (FAQs)
1. What is the security posture in cybersecurity?
The security posture defines the overall strength and readiness of an organization's defenses in cybersecurity. It gauges the organization's ability to prevent, detect, respond and recover from cyber threats, including their tools, policies, procedures, and employee awareness.2. What is another word for security posture?
Security posture can also be called a security stance or cybersecurity readiness. All terms describe the organization's overall behaviour to secure its digital assets and efficiently respond to possible security threats.3. What are the three components of security posture?
There are three main components:- Policies and Controls: Rules, firewalls, access management, and encryption that specify how the systems are secured.
- Monitoring and Detection: Tools and processes enable visibility into systems, user activity, and new threats.
- Incident Response and Recovery: Plans and procedures that allow the organization to respond to the security concern(s) and to return to normal operations as safely and quickly as possible.
4. What is an example of a security posture assessment?
In most evaluations, you would run vulnerability scans, assess system configurations, and perform gap analysis to find weaknesses. This would then feed into a report explaining risks, compliance shortfalls, and recommendations for mitigation.5. How can companies improve their IT security posture?
Organizations could improve their security posture by:- Revising their policies and incident response plans to reflect potential threats and compliance requirements.
- Educating employees on phishing attacks, password hygiene, and safe practices to reduce human error.
- Utilizing zero trust to ensure strict verification for every user, device, and application.
- Establishing continuous monitoring and regularly auditing to discover emerging vulnerabilities and remediate them before being exploited.