Identity Management Best Practices to Strengthen Cybersecurity in 2025

When it comes to protecting digital assets, identity is where it all begins. Identity and Access Management (IAM) isn’t just another tool in the cybersecurity toolkit. It’s the foundation of how access is granted, monitored, and controlled. From safeguarding user identities to enforcing role-based permissions, IAM security helps ensure that the right people have access to the right resources at the right time.
But here’s the catch. Simply having IAM tools in place isn’t enough. To truly strengthen your cybersecurity posture, you need to follow the right IAM principles and implement a clear identity management strategy. In this blog, we’ll walk you through key identity management best practices that can make a real difference. Whether you're just getting started or refining your current approach, these IAM best practices will help you take access security to the next level in 2025 and beyond.
Key Takeaways
- IAM is the foundation of identity security, enabling centralized control over user access and digital identities.
- In 2025, IAM best practices are essential to address evolving threats, remote work models, and regulatory pressures.
- Key principles like least privilege, RBAC vs ABAC, and centralized IAM form the basis for secure, scalable identity management.
- Critical best practices include Multi-Factor Authentication, automated provisioning, access reviews, PAM, Just-in-Time access, and continuous monitoring.
- Common mistakes such as over-permissioning, outdated policies, and weak integrations can expose organizations to unnecessary risk.
What Is Identity Management?
At its core, identity and access management (IAM) is the foundation of access control. It’s a framework made up of policies, processes, and technologies designed to manage digital identities securely. Whether you're dealing with employees, contractors, or third-party apps, IAM security ensures that only verified users can access the resources they’re entitled to. This includes everything from verifying who the user is to authenticating their identity through methods like passwords or biometrics, and finally authorizing access based on roles and permissions.
A strong identity management strategy doesn’t just streamline user access—it actively reduces risk. It enables organizations to manage user accounts efficiently, grant or revoke access as needed, and maintain continuous visibility into who can access what. Beyond just protecting sensitive data, identity management supports compliance requirements and lays the groundwork for best practices like user access management, automated provisioning, and least privilege enforcement. When done right, it becomes a critical pillar of any organization's overall cybersecurity IAM efforts.
Why IAM Best Practices Matter in 2025
The digital landscape is changing fast. With remote work, cloud-first operations, and rising threats like credential theft and insider attacks, following IAM best practices is more critical than ever. Organizations can no longer rely on traditional perimeter-based security. Instead, they need strong IAM security controls that manage user identities, enforce least privilege principles, and secure access in real time. From defending against account takeovers to adopting zero trust strategies, identity and access management best practices help build a resilient defense against today’s complex threats.
There’s growing pressure around compliance with global regulations like GDPR, HIPAA, and others. Robust identity governance frameworks, audit trails, and automated provisioning not only reduce risk but also simplify compliance reporting. At the same time, users demand seamless experiences. Features like Single Sign-On (SSO), adaptive authentication, and user access management best practices make security smarter without making it harder. Simply put, following the right IAM security best practices in 2025 means enabling your business to move faster, stay compliant, and remain secure.
Core IAM Principles for Cybersecurity and Compliance
Building a strong foundation in identity and access management (IAM) starts with applying the right principles. These core IAM principles help organizations stay secure, meet compliance requirements, and streamline user access management. Let’s break down the three most critical ones.
1. Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) is simple but powerful: grant users only the access they need—and nothing more. Whether it’s an employee, contractor, or third-party vendor, limiting access rights reduces the chance of unauthorized access to sensitive systems or data.
Implementing PoLP means conducting regular access reviews, analyzing each user’s responsibilities, and tightening permissions accordingly. This approach not only supports cyber security identity and access management but also aligns with compliance frameworks that demand strict access control policies. It’s one of the most effective IAM best practices for minimizing the impact of insider threats or compromised accounts.
2. Role-Based Access Control (RBAC) vs. Attribute-Based Access Control (ABAC)
Both RBAC and ABAC offer ways to manage access intelligently, but they work differently.
Assigns access rights based on predefined roles—like “HR Manager” or “Finance Analyst.” It’s easy to manage and works well in most structured environments.
Takes it a step further. It uses dynamic attributes such as department, location, device type, or time of day to grant access. This makes it more flexible, especially in complex or hybrid environments.
For many organizations, combining RBAC for standard roles and ABAC for context-aware controls forms a powerful access management strategy. Together, they help enforce user account management best practices while ensuring policy-driven, risk-aware access decisions.
Centralized IAM
A centralized IAM system acts as a single source of truth for managing identities and permissions across the entire organization. Instead of juggling multiple tools or departments handling access separately, a unified IAM platform ensures consistent policy enforcement, better visibility, and stronger governance.
With centralized control, IT teams can implement automated provisioning, detect anomalies faster, and apply security access management policies organization-wide. It’s a must-have for organizations looking to scale securely while meeting regulatory and operational demands.
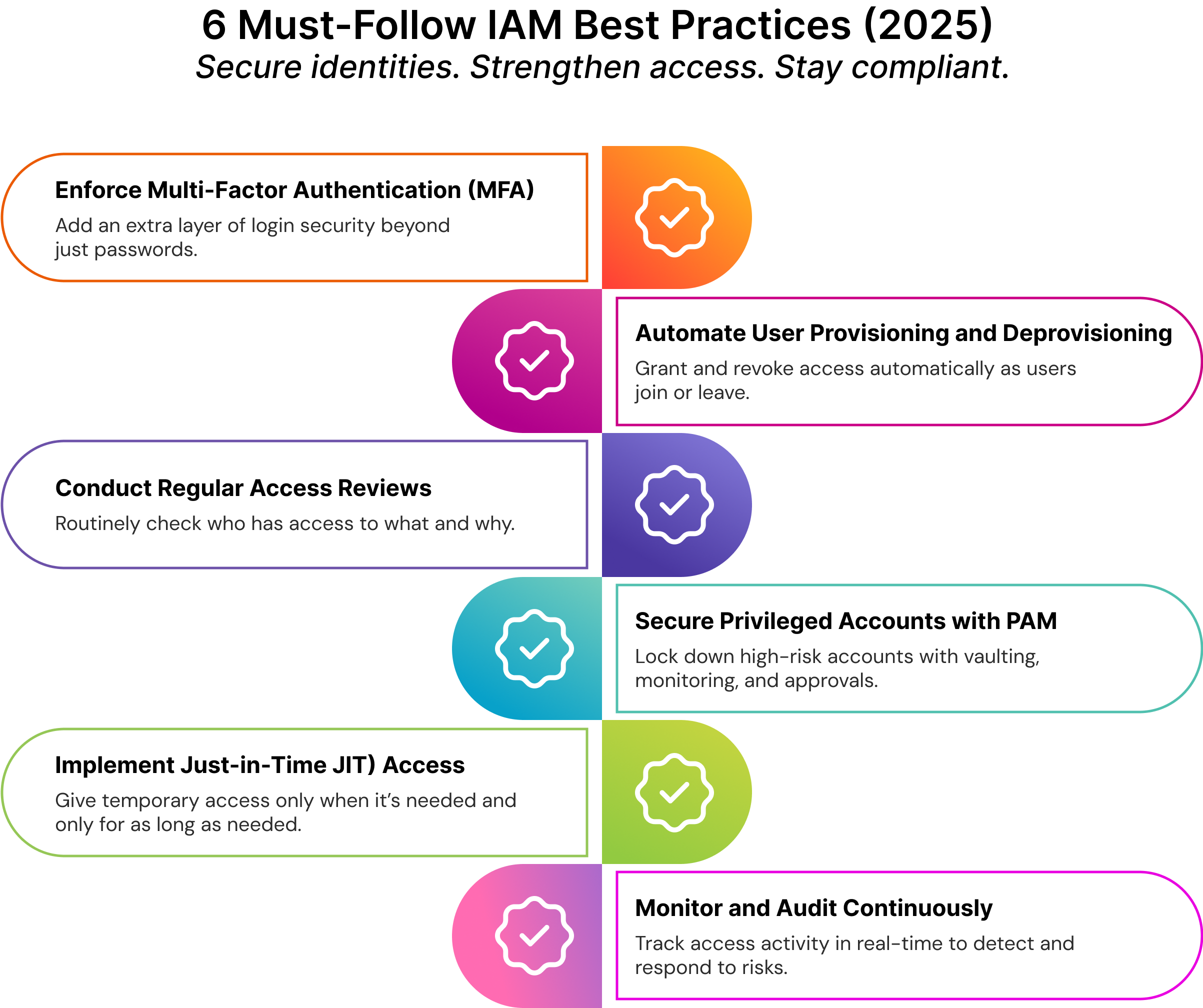
6 Must-Follow IAM Best Practices (With Tools & Examples)
Implementing the right IAM best practices can make all the difference between a secure, compliant organization and one that’s vulnerable to access-related risks. Below are six critical identity practices every security team should adopt in 2025:
- Enforce Multi-Factor Authentication (MFA)
MFA adds a second layer of verification, ensuring that even if a password is compromised, the attacker still can’t access the system. It typically combines something the user knows (password), has (token), or is (biometric).
For example, combining a password with a fingerprint scan or an OTP sent to a registered device significantly strengthens authentication. Adaptive MFA takes this further by evaluating contextual risk factors like location or device type before deciding how strict the login flow should be. - Automate User Provisioning and Deprovisioning
Manual access management is time-consuming and error-prone. Automating user provisioning ensures that new hires get the right access from day one, while automated deprovisioning removes access as soon as someone exits or changes the role in the organization.
Tools that integrate with HR systems (like Workday or SAP) and identity platform-based directories can streamline the process and enforce user account management best practices at scale. - Conduct Regular Access Reviews
Access creep is a silent risk. Users often retain access they no longer need, which violates the principle of least privilege. That’s why regular access reviews, monthly, quarterly, or after role changes, are essential.
Dashboards from leading identity governance tools can help visualize permissions, flag anomalies, and streamline the access certification process, making it easier to stay both secure and compliant. - Secure Privileged Accounts with PAM
Privileged accounts like admin or root users are goldmines for attackers. Privileged Access Management (PAM) helps lock down these high-risk accounts by storing credentials in secure vaults, monitoring session activity, and requiring approval for access elevation.
Whether it’s IT administrators, machine identities, cloud engineers, or third-party vendors, PAM ensures that access is tightly controlled and traceable, supporting both cybersecurity IAM and compliance needs. - Implement Just-in-Time Access Controls
Instead of giving standing privileges, grant temporary, context-based access through Just-in-Time (JIT) access controls. This means users only get elevated permissions when needed, for a limited time.
JIT access is ideal for short-term use cases—like helpdesk agents or vendors—who occasionally require elevated permissions. It ensures granular control without compromising productivity or violating your access management strategy. - Monitor and Audit Continuously
Security doesn’t stop at provisioning. Continuous monitoring and audit trails are key to spotting unusual behavior, revoking stale access, and proving compliance during audits.
Real-time alerts, activity logs, and compliance dashboards provided by IAM security platforms offer the visibility needed to respond quickly and stay aligned with regulatory expectations. This is central to strong identity management cybersecurity.
Common IAM Mistakes That Undermine Security
Even the most well-intentioned IAM security strategies can fall short if they’re not executed thoughtfully. Many organizations unknowingly introduce risk by overlooking key areas of their identity and access management (IAM) setup. Avoiding these pitfalls is just as important as following best practices.
Over-permissioning Users
Granting users more access than they need is one of the most common identity-related mistakes. Over time, these unnecessary permissions pile up, often referred to as "permission creep" and significantly widen the attack surface. Without strict enforcement of the least privilege principle, even non-admin users can end up with access to sensitive systems or data. This not only violates access management best practices but also creates a compliance risk.
Treating IAM as a One-Time Setup
IAM isn’t a one-and-done configuration. It’s an ongoing strategy that must evolve with your workforce, technologies, and threat landscape. Organizations often make the mistake of setting up IAM policies and never revisiting them. Without regular access reviews, audits, and updates, you're left with stale data, outdated roles, and potentially dangerous blind spots. IAM must be treated as a living, breathing part of your overall cybersecurity approach.
Weak Integration with HR or Cloud Systems
IAM can’t operate in silos. If it isn’t tightly integrated with your HRIS or cloud infrastructure, you're inviting delays, misconfigurations, and security gaps. Lack of automated provisioning and deprovisioning is a red flag it often means former employees still retain access to critical systems. Integrating IAM with tools like Workday, Okta, or Azure AD ensures smooth, real-time user access management and supports your access management strategy at scale.
Final Thoughts: Future-Proof Your IAM
As businesses continue to scale and embrace digital transformation, your IAM strategy must do more than just manage access; it needs to grow with you. A future-ready identity framework blends scalability, security, and compliance into one seamless system. Whether you’re onboarding hundreds of users, shifting to the cloud, or preparing for a compliance audit, strong identity and access management best practices gives you the control and visibility you need to stay ahead.
But IAM doesn’t exist in a vacuum. It intersects with broader concepts like identity governance, provisioning automation, and Zero Trust. If you’re ready to take the next step, check out our related blog: [IGA vs IAM: What’s the Difference?] to learn how governance fits into your identity roadmap.
- Learn how our solutions can reduce risk and improve visibility.
- Book a personalized demo to identify hidden gaps.
Frequently Asked Questions (FAQs)
1. How often should access reviews be conducted?
Access reviews should be conducted at least quarterly, but the exact frequency depends on your organization’s risk profile, compliance requirements, and user roles. High-privilege accounts or sensitive data environments may require monthly reviews. Regular audits are key to maintaining least privilege, avoiding permission creep, and staying compliant with frameworks like GDPR or HIPAA.2. What’s the difference between RBAC and ABAC?
Role-Based Access Control (RBAC) assigns access based on predefined user roles (like "HR Manager"). It’s simple and works well in structured environments. Attribute-Based Access Control (ABAC) goes further by considering dynamic factors like time, location, device, or department. ABAC offers granular, policy-driven access control ideal for complex or hybrid environments. Both support strong access management strategies, and in many cases, a blend of RBAC and ABAC works best.3. What are the 4 pillars of IAM?
The four core pillars of Identity and Access Management (IAM) are:- Authentication – Verifying a user’s identity (e.g., via passwords, biometrics, or multi-factor authentication)
- Authorization – Granting appropriate access based on roles or attributes
- User Management – Handling user provisioning, deprovisioning, and lifecycle changes
- Audit & Compliance – Monitoring access logs and maintaining audit trails to support identity governance and regulatory compliance
4. What are the strategies used in identity management?
Effective identity management strategies include:- Enforcing least privilege and just-in-time access
- Implementing automated provisioning through HR system integrations
- Using Single Sign-On (SSO) and adaptive authentication to enhance usability and security
- Applying centralized IAM controls for consistent access enforcement
- Regularly conducting access reviews and audits
These strategies ensure your IAM security is both scalable and compliance-ready.