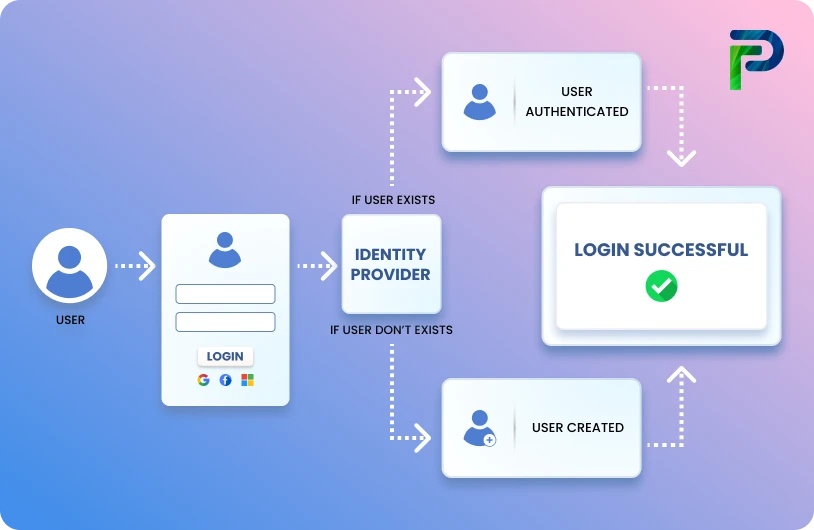
Identity and Access Management (IAM) Checklist for 2026


Identity and Access Management (IAM) was once a technology-heavy, back-end IT process, but now it has emerged as more than just a process/function of managing identity access for systems and applications. IAM has matured to become the first line of defense for organizations as they face the real threats of data breaches, insider abuse, regulatory fines and penalties, etc. With ongoing SaaS adoption and an increase in hybrid work, the attack surface for cybercriminals has expanded. Additionally, multi-cloud deployments have increased the number of unmanaged identities in an organization, which is often the easiest target for attackers.
For IT leaders and CISOs, the question they face is not simply the deployment of an IAM program or IAM platform, but how every aspect of their IAM program (access control, authentication flow, compliance, etc) can be consistent, measurable, and scalable. Failing to achieve the key aspects of a foundational IAM implementation will produce a threat of active privilege creep, orphaned accounts, audit failures, and business disruption.
This is why relying on an IAM checklist is now mandatory. Following a framework that is structured, step-by-step, you can harden your authentication, enforce least privilege, empower wide and deep audit capacity, or perhaps most importantly, ensure you have an IAM program that continues to grow with your business. In this blog, we will provide a useful 8-step checklist for you to enable secure identities and access, better compliance, and future secure access.
Key Takeaways
- Having a documented IAM policy and governance model ensures audibility and repeatability of access decisions.
- Automating the identity lifecycle (provision → modify → deprovision) eliminates orphan accounts and privilege creep.
- Strong authentication (MFA, SSO, adaptive controls) mitigates credential theft without negatively impacting UX.
- Authorization must enable least privilege according to RBAC/ABAC and PAM for privileged accounts.
- Regular user access reviews, maintained centralized logging, and SIEM integration provide efficiency to audits and faster incident investigations.
- Regular training and continuous improvement enable IAM controls to stay up to date with changes in systems and risks.
1. Define IAM Policy and Governance
An effective Identity and Access Management (IAM) strategy essentially begins with the foundation of firmly established policies and governance. An IAM policy is the definition of access rights; it defines the rules for which users and systems can perform what actions on which resources in what conditions. Moreover, IAM policies serve as guardrails from which users can base access decisions consistently, in an enforceable manner, and along desired business requirements.
However, policies alone can only take the IAM process so far. IAM governance provides the structure associated with policies that is necessary for IAM to be actionable and sustainable. Governance considers the policies themselves as part of a bigger system that establishes processes, oversight, and levels of accountability that ensure that access policies are established, implemented, reviewed, and improved. IAM policies working individually and collectively, supported by governance, establish the foundation for identity security. Policies and governance recognize the operations for individuals and groups, distinguish responsible parties with levels of responsiveness (or lack of) to limit ambiguity, and enhance compliance in an organization.
Elements of IAM governance include:
- Policy development: Creation of rules for provisioning, authentication, authorization, and auditing, and consistent reviews to ensure they are still relevant.
- Separation of Duties (SoD): IAM policies must also include the notion of separating duties so no single identity has untethered authority (e.g., one individual creates and approves a transaction).
- Compliance standards: This element is key when IAM policies are created from a compliance perspective. It is easier to map IAM policies to elements of the compliance framework: GDPR, HIPAA, SOX, etc. Coordinating IAM oversight and compliance activities can reduce the risk of failures during audits.
If the elements of IAM governance are well established and executed, IAM moves from a technical security layer to also include a regulatory compliance enabler and assurance tool for the business.

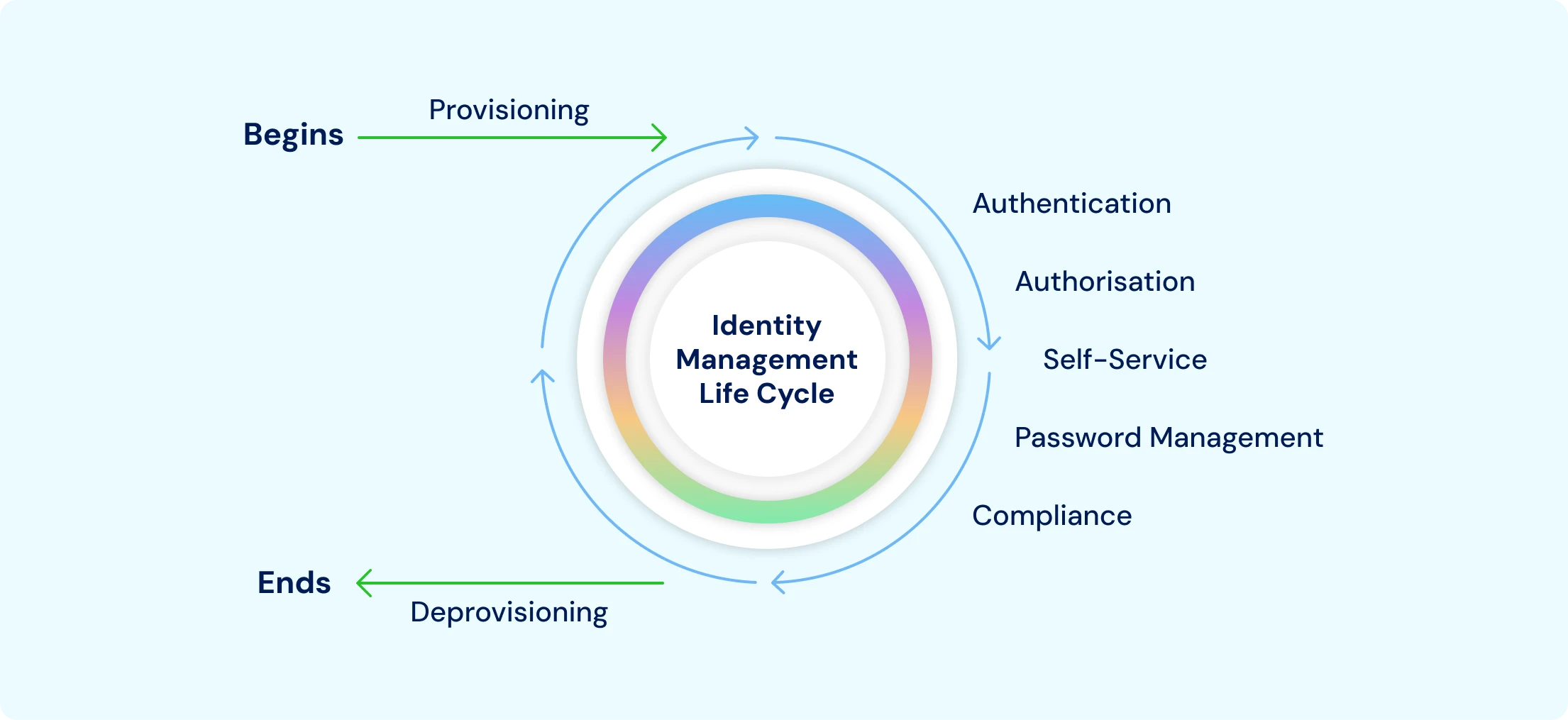
2. Manage the Identity Lifecycle
The identity lifecycle establishes how a user’s access to resources is managed from when they are onboarded until they are offboarded. Each event of the lifecycle, such as onboarding, role changes, project assignments, and offboarding, presents opportunities for operational efficiencies as well as risks when poorly managed. It is common for weak access control lifecycle management to result in orphaned accounts (ex-employees that can still log in) and access creep (users with privileges retained long after their need for those privileges). Additionally, when onsite auditors conduct access reviews, they identify organizations with control gaps for compliance.
Risk mitigation from the identity lifecycle requires lifecycle management to be automated, consistent, and policy-based. This way, a user’s access is aligned with their role, responsibilities, and context in every instance.
Key best practices include:
-
Automated provisioning and deprovisioning: When new employees or contractors join an organization, their access should be provisioned immediately in accordance with fixed roles. When they leave, their permissions should also be revoked immediately to avoid lingering accounts that attackers can use. Using automation for provisioning and deprovisioning tasks to reduce IT workload and time delays.
-
Just-in-Time (JIT) access: Not every user needs permanent (real-time) access to systems. Just-in-Time (JIT) Access is a security framework that grants users access for time-bound actions. The access is then automatically turned off once their task or timeframe elapses. For example, a 3rd party vendor could be given access for 24 hours to perform scheduled maintenance on the system. After a 24-hour duration, the credentials would automatically expire.
-
Centralized directory integration: Directories like Active Directory (AD), Azure AD, or LDAP serve as a centralized repository for identities. Organizations can integrate all applications through a unified directory for a centralized repository of identities, cutting through silos, providing uniform policies, and simplifying compliance reporting.
When an organization's lifecycle management process is considered a core function of IAM, organizations achieve two key outcomes:
- Improved security with the accuracy of access in real time, reducing attack vectors.
- Finite operational efficiency since IT teams are not wasting time manually granting or removing access, and employees are gaining access more readily.
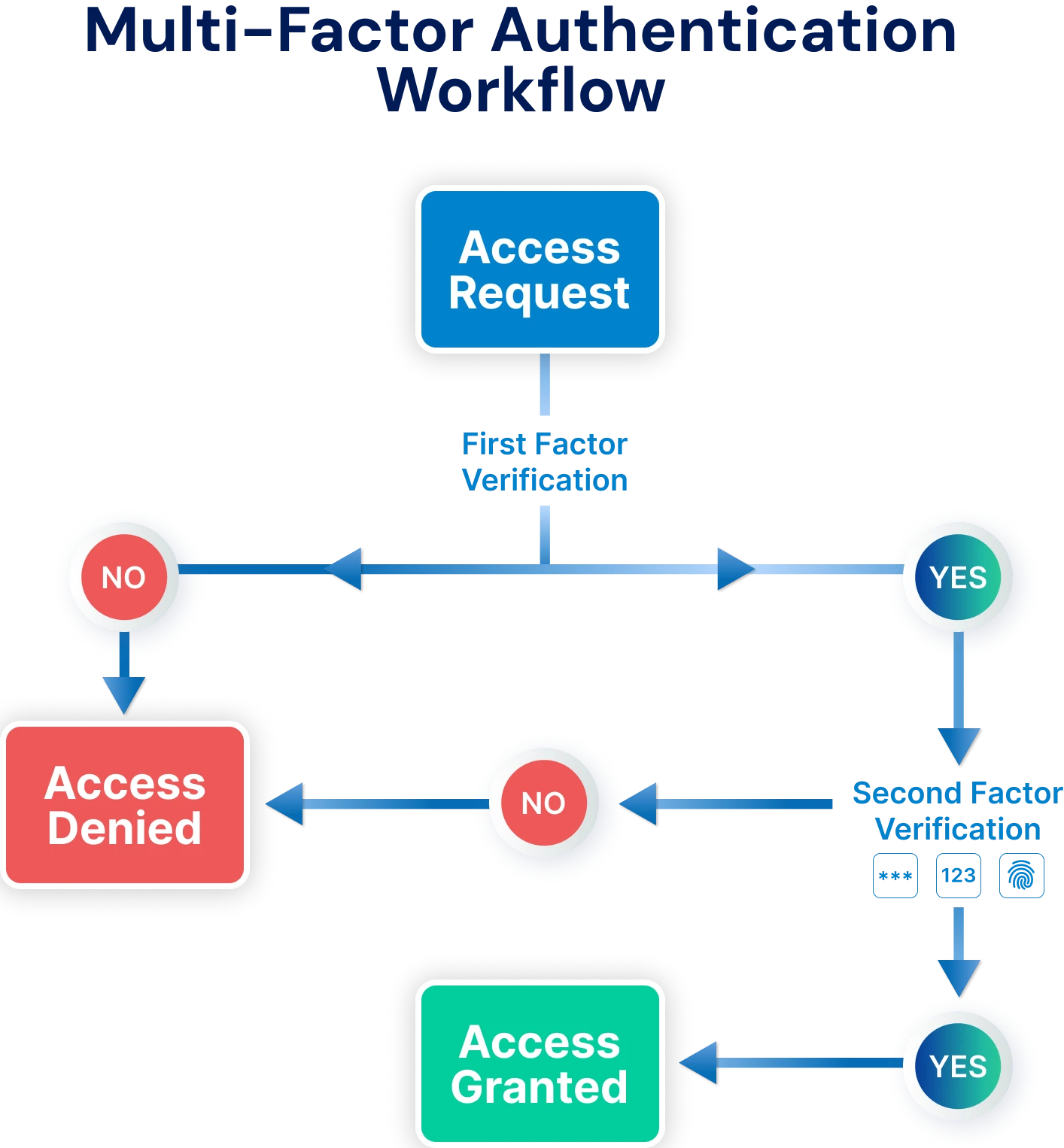
3. Strengthen Authentication
Authentication is the first line of defense for any IAM program, as it establishes that users are who they say they are before providing access. Weak or reused passwords are one of the top reasons for a breach, which is why it is of the utmost importance to thoughtfully layer authentication methods beyond logging in simply with a password.
Key practices include:
-
Multi-Factor Authentication (MFA): Requires users to provide at least two factors of verification (something they know, something they have, or something they are). Multi-factor authentication generally stops there, as even stolen credentials won't typically provide access. Adaptive MFA goes further, using contextual information like device, location, or time of access, to approve or deny the attempt to log in.
-
Single Sign-On (SSO): Securely logging someone onto all applications when they authenticate in just one place improves the user experience and lessens password fatigue. When utilized along with MFA, SSO has minimal drawbacks while providing better security than many traditional operational scenarios.
-
Biometrics: Fingerprints, facial recognition, and voice ID can be used in addition to a password as an additional layer of security. They do reduce the reliance on a password altogether, but they are better suited for environments requiring additional security.
How to have a strong password policy?
→ Minimum 12 characters, including upper- and lowercase letters, numbers, and special symbols.
→ No reuse of the last 5 passwords.
→ Mandatory rotation every 90 days.
→ Block weak or common passwords (e.g., “123456” or “Password@123”).
4. Authorization and Access Control
Authorization is the process of defining and enforcing what an authenticated user can access and what they can perform in a system. Authentication confirms identity (who you are), while Authorization controls entitlements (what you're allowed to do) by applying policies, roles, or attributes to determine access privileges, such as read, write, administrative, etc, for the applications, systems, or data.
The authorization step is important because not every user requires the same level of access. For example, a finance analyst may need access to financial applications, but not the engineering source code. Likewise, a contractor may need temporary access to one system, but not necessarily to the entire company's network. Proper authorization gives a person's role access that matches their responsibilities and risk profile.
To enforce authorization, organizations rely on structured access control models:
-
Role-Based Access Control (RBAC): Access is provided based on the user's position in an organization (e.g., HR, finance analyst, IT). In this manner, access tends to be consistent, scalable, and easier to audit. For example, all finance analysts can view transaction history; however, they cannot change HR records.
-
Attribute-Based Access Control (ABAC): This type of access control expands on roles by incorporating attributes such as user location, device, time of day, or resource sensitivity. In this way, ABAC is both role- and context-aware access, making it increasingly valuable for hybrid and remote environments.
-
Principle of Least Privilege (PoLP): Users should only have access to the minimum level of access required to perform their required tasks. The enforcement of least privilege rights, especially with rights to privileged accounts, is an effective way to prevent insider threats and significantly reduce the impact of compromised accounts.
-
Privileged Access Management (PAM): Users account for higher-level access, such as system administrators, database owners, or cloud administrators add special measures to these accounts. PAM ensures that privileged accounts are monitored in use, time-bound, and require administrative approval before use to protect against abuse.

5. User Access Reviews (UAR)
User Access Reviews (UARs) are structured assessments where the access rights of employees, contractors, and third parties are evaluated to ensure the access captures only what is necessary to perform job functions. The access a person has may not accurately reflect their current responsibilities (due to role change, project change, or separation from the organization), so over time, permission creep can be a significant security and compliance risk.
UAR best practice features include:
-
Quarterly reviews: Ideal for high-risk users, privileged accounts, and systems that store or process sensitive data. The goal is to ensure access rights for important and sensitive resources are frequently reviewed to reduce the opportunities for misuse or insider threats. Examples: Users with administrative access, accounts that access financial reporting systems, or users with broad access to customer PII.
-
Annual reviews: Best for standard users and systems with little risk exposure. Employers can complete annual reviews to ensure access aligns with business roles while not overwhelming IT teams. Annual reviews help eliminate dead accounts and stale accounts while fulfilling compliance without additional burden. Examples: General employee accounts for tools that enable collaboration, non-critical internal portals, or systems with limited access.
-
Vendor & third-party access validation: External partners and contractors usually have temporary access. The audit process will identify them frequently and help justify their access or revoke it accordingly.
-
Deactivate dormant accounts: Unused or inactive accounts are low-hanging fruit for attackers. All review cycles should identify inactive accounts and deactivate them.

6. Monitoring and Logging
Monitoring and logging are essential pillars of an IAM strategy because they offer the visibility and accountability that access controls inherently do not offer. IAM determines who should have access, while monitoring and logging grant visibility in regards to how access is actually being used. The combination of the two allows organizations to quickly monitor, detect, and contain risk posed by insider threats, insider risk, misconfigurations, and compromised accounts.
Key components of IAM monitoring & logging are:
-
Log Collection Across Systems - Collect all logs related to identity activity in an aggregation and in a single source of truth across user directories, i.e, AD, Azure AD, applications, databases, and cloud.
-
SIEM Integration - Integrate these logs into a Security Information and Event Management (SIEM) tool to correlate identity events with network and endpoint behavior. For example, if a privileged account logs in with an unusual origin IP while simultaneously downloading sensitive files, the SIEM tool can catch this immediately.
-
Behavioral & Anomaly Detection - Having static alerts is just the start. Also look for patterns like multiple failed sign-ins, or someone who signs in from two different geographies within minutes (sometimes referred to as "impossible travel"), or that an account has excessive privilege escalation. AI-based analytics can complicate detection efforts, but can improve detection accuracy.
-
Audit Trail for Compliance - Compliant documentation of immutable logs with timestamps for auditing is important, especially for GDPR, HIPAA, SOX, or ISO 27001 audits. When strong IAM logging practices are followed, every access event is traceable, documented, and can be mapped to business policy.
-
Privileged Session monitoring - For accounts with elevated rights, not only can sessions be reviewed, but they can be recorded for additional visibility. A recording of a session provides the ability not only to ascertain who accessed what but also what they were doing when they accessed the resource(s).
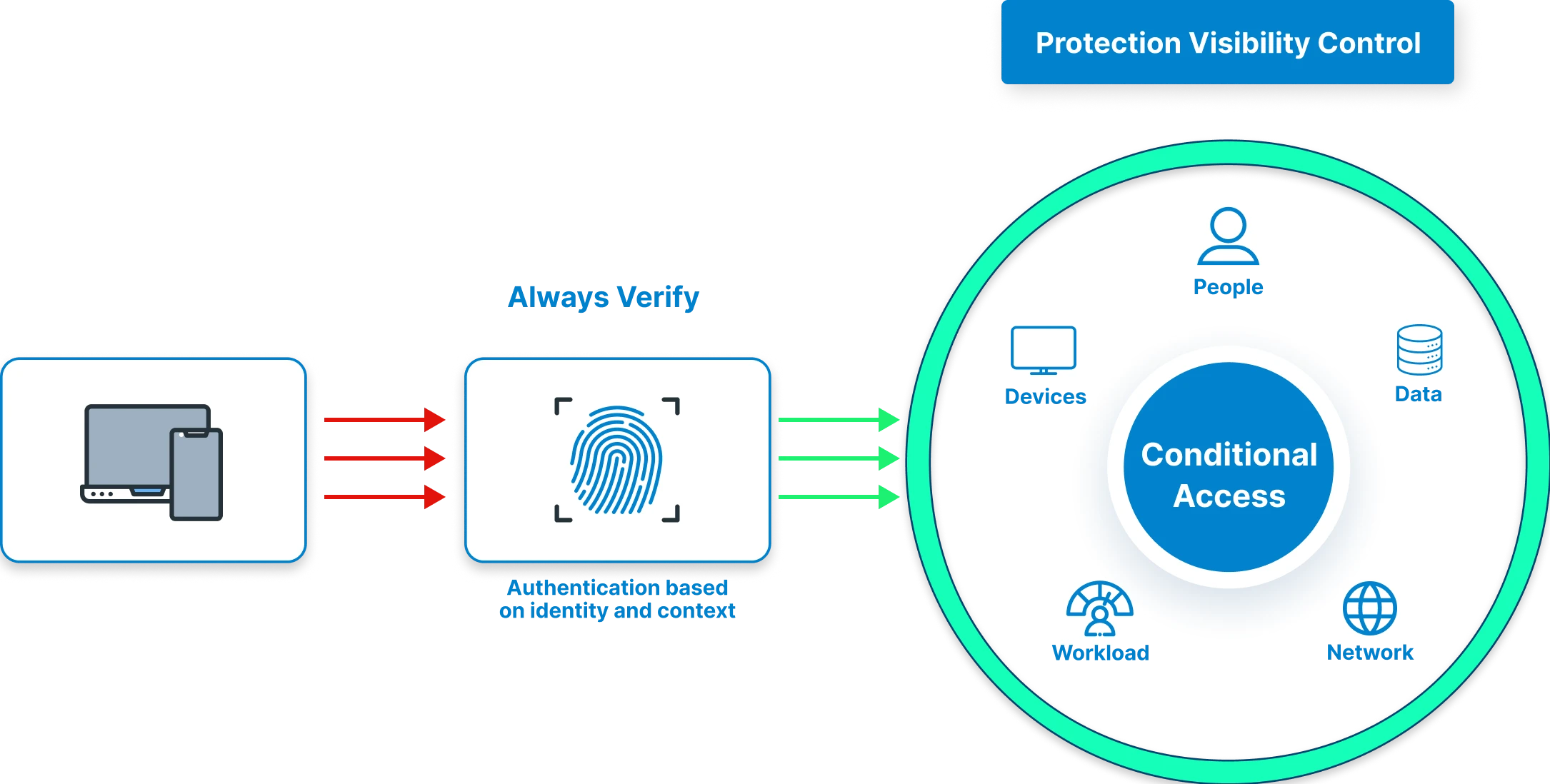
7. Security Controls and Zero Trust
Modern IAM goes far beyond authentication and authorization, and needs to include security controls that embrace the ideas of Zero Trust. In a Zero Trust model, no user, device, or application is trusted right out of the gate, either inside or outside of the corporate network. Instead, everything is continuously verified, and access is restricted to the least amount of access necessary.
Some of the key security controls include:
-
Encryption In Transit & At Rest - User credentials, tokens, and identity data must always be encrypted, both in transit across the networks and in storage. When it comes to data in transit, TLS 1.3 (Transport Layer Security) is the standard for the industry, and it provides the strongest protection against eavesdropping and interception. For data-at-rest, AES-256 is one of the most secure symmetric encryption algorithms available, which uses a 256-bit key length that makes brute-force impossible. Collectively, these standards ensure that sensitive identity data is protected end-to-end.
-
Conditional Access based on Risk - With new IAM technology, your IAM platform will assign risk scores to login events by evaluating context using adaptive authentication(device health, location, IP reputation, and time of access). A risky login from Sweden on an unknown device would not be treated the same as a login from an employee's known office in Seattle; it may prompt stronger authentication requests or be denied completely.
-
Zero Trust Enforcement - Instead of granting wide and static access, IAM enforces least privilege with continuous validation. If an access request is made for a SaaS app, cloud workload, or application on-premises, IAM is taking its real-time verification of access and validating it to the user's behavior and their security posture.
8. Training and Continuous Improvement
An IAM program is only as effective as the human and process elements to back it up. Regular security awareness training helps ensure employees are aware of the need to protect credentials, identify and report phishing attempts, and follow best practices to authenticate trusted systems. IAM can only be successful if there is an underlying layer of human readiness. Even the most sophisticated IAM capabilities can be compromised.
Organizations should also assess their IAM maturity against established models (for example, NIST or Gartner’s IAM maturity models). An assessment uncovered a gap that may not be easy to identify, such as governance, automation, or some aspect of Zero Trust. These findings help identify opportunities for continuous improvement.
Next, differentiate your IAM program by deploying Identity Governance and Administration (IGA) tools that will not only automate the access certification process, but also automate compliance reporting and automate lifecycle workflows. Automation is beneficial because it removes manual overheads associated with IAM, reduces human error, and allows the IAM program to remain agile to shifting business and regulatory requirements.
Final Thoughts
Creating a checklist is only the initial phase. IAM is not a one-time exercise but is a dynamic program that needs to adapt as your business goals, workforce composition, and threat landscape change over time. Successful IAM requires more than technology, as organizations need governance, cultural alignment, and continued adjustment to keep up with change. Successful organizations see identity not only as a form of protection for critical assets but as a strategic enabler of trust, productivity, and organizational resilience over time.
NEXT STEPS
Ready to go beyond the checklist?
With Tech Prescient’s Identity Confluence, you can automate access reviews, enforce Zero Trust, and unify IAM with governance, without adding complexity.
- Get started faster → Explore now
- See it in action.
Frequently Asked Questions (FAQs)
1. What are the 4 pillars of IAM?
The four pillars of identity access management (IAM) include governance, authentication, authorization, and auditing. Collectively, they build a secure identity framework - ensuring that the right people are able to access (authentication and authorization), that their activities are governed by policy, and that all activities are monitored for compliance and accountability.2. What are the 4 A’s of IAM?
The 4 A's of IAM are authentication, authorization, administration, and auditing. Authentication verifies identity, authorization enforces what a user can access based on role or entitlement, administration manages the accounts and entitlements, and lastly, auditing provides transparency and accountability by tracking an activity for records. Each aspect ensures IAM systems are secure and manageable.3. How do you audit IAM effectively?
A good IAM audit will review policies, review user roles, provide an overview of privileged accounts, and review compliance logs. An IAM audit will verify when given a role that the user has only what they need to do their job (least privilege), run a check on third-party or vendor accounts, and verify they have not lost access to the user logs required for compliance under frameworks like GDPR, HIPAA, and SOX. All of these activities take place to help prevent structures from allowing excessive permissions or access or to detect anomalies in user access.4. What comes under IAM?
IAM encompasses many capabilities, including user provisioning and deprovisioning, authentication mechanisms like MFA/SSO, access control models like role-based access control (RBAC), attribute-based access control (ABAC), and privileged access management (PAM), continuous monitoring, and compliance enforcement. IAM is both an operational system as well as a governance layer providing visibility into an organization’s identity security posture to meet business needs.5. What is the difference between IAM and IGA?
IAM is about allowing, managing, and protecting access to resources, and ensuring that the correct users receive the correct access. IGA (Identity Governance and Administration) is an extension of IAM, which not only allows access but also provides a level of oversight around access. This includes reviewing entitlements, enforcing policies like separation of duties, and ensuring regulatory compliance. In other words, IAM provides access, and IGA governs access.