Overview
Identity and Privacy are the most important consideration in today’s digital world. Enterprise credibility and trust hinges on how securely they handle user identity and data. Identity Access and Privacy policy defines who has access to what resources in what capacity for how long and at what times. It also defines what the user can do with that data.
Any Digital transformation process needs to consider an automated identity creation, authentication, authorisation, validation, access management, privacy and data access policy to ensure secure and productive business ecosystem.
Tech Prescient has built several custom identity solutions to help our customer achieve their unique business goals. Our expertise in this subject will help you build an integrated and secured identity solution for your business need. We offer a wide range of identity and access management (IAM) solutions to help businesses keep their sensitive data secure from cyber threats. Our expertise in IAM, IGA, and PAM enables us to provide comprehensive services and support to help you manage your identity and access needs. With us you can be confident that your data is secure and protected at all times.
Any Digital transformation process needs to consider an automated identity creation, authentication, authorisation, validation, access management, privacy and data access policy to ensure secure and productive business ecosystem.
Tech Prescient has built several custom identity solutions to help our customer achieve their unique business goals. Our expertise in this subject will help you build an integrated and secured identity solution for your business need. We offer a wide range of identity and access management (IAM) solutions to help businesses keep their sensitive data secure from cyber threats. Our expertise in IAM, IGA, and PAM enables us to provide comprehensive services and support to help you manage your identity and access needs. With us you can be confident that your data is secure and protected at all times.
IAM Offerings & Solutions
Easily build, automate, and optimize data pipelines with an intuitive UI-driven workflow.
OUR EXPERTISE

Expertise in Cloud Identity Management platforms. Tech Prescient signed partnership with Okta as a solution provider.

Built solutions for Workforce and Cloud Identity, MFA and SSO integration, Identity-as-a-Service, RBAC solutions and more.

Seamless integration with third part authentication and authorization services managing identity federation.

Clear understanding of key identity concepts and protocols such as OpenID, OAuth2, SAML 2.0, SSO, MFA, tokens, privileges, RBAC etc.

Developed and deployed several identity management solutions at scale for large enterprises.




IAM Case Studies
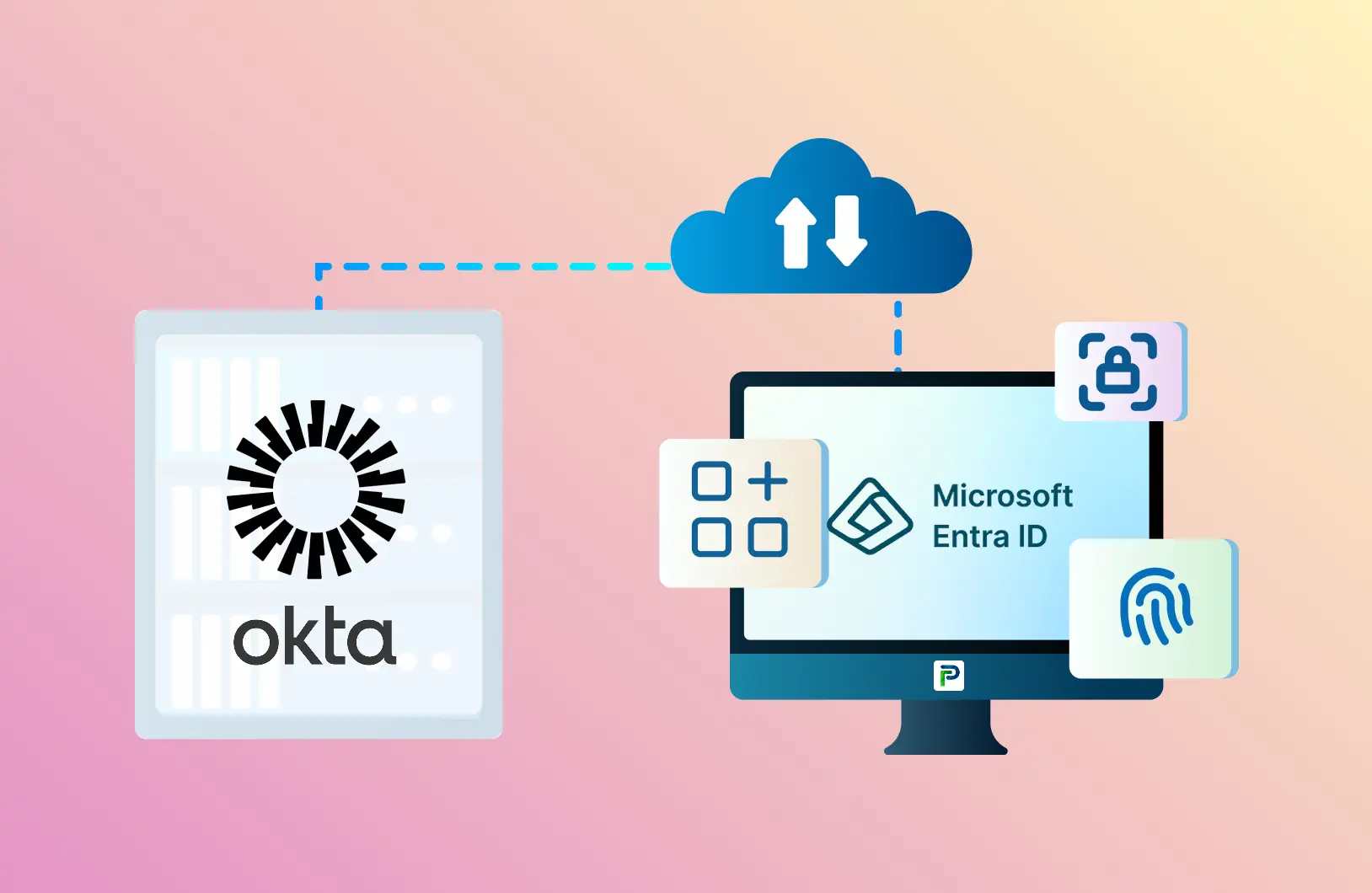
Discover How Tech Prescient Moved 10k+ Users from Okta to Entra ID with Zero Downtime
May 14, 2025
The client, a multinational organization, had been using Okta as their primary identity and access management (IAM) solution for several years. However, due to a strategic organizational decision, they decided to migrate their IAM infrastructure from Okta to Azure Active Directory (Azure AD).
What Our Customers Say
Real experiences, real impact. See how we’ve helped customers thrive with tailored services.
Trusted By The Industry's Best Organizations