
Privileged Access Management (PAM): Why It’s Critical in 2026

We are aware of the fact that when attackers break into an organization, they don’t waste time picking locks. They go straight for the master keys. These keys can be best described as privileged accounts that give users deep access to sensitive systems and related resources, applications, and data.
Now here’s the worrying part: According to IBM’s Cost of a Data Breach Report, compromised credentials are the most common initial attack vector, with the average breach costing over $4.45 million. So how do you protect such accounts that, if misused, can quietly unlock everything?
That’s where Privileged Access Management (PAM) steps in. It's not just a security tool it’s a gatekeeper. Whether you're running a fast-moving tech startup or a global enterprise, PAM ensures that elevated access is controlled, monitored, and revoked when no longer needed.
In the following blog, we will explore what PAM really means, why it’s become non-negotiable, and how organizations are using it to regain control over their most powerful accounts.
What Is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a cybersecurity framework that is designed to control and secure high-level permissions of certain privileged accounts. This is done to ensure that only the right individuals and systems can have access to privileged accounts. Having access that too only when it’s truly needed.
Organizations generally rely on certain users, systems, and applications to manage their sensitive infrastructure. These accounts, known as privileged accounts, have elevated permissions that go far beyond what a typical user might need. They can modify configurations, access confidential data, and even out down the entire system.
Overall, we can say that Privileged Access Management (PAM) is a cybersecurity framework designed to control and secure these high-level permissions. It reduces the attack surface by putting in controls like session monitoring and recording, time-based access, and approval of workflows. It ensures that only the right individuals or systems have access to privileged accounts, and only when needed.
Why Privileged Access Matters in 2025
We are aware of the fact that privileged accounts are the easiest and most fatal entry points into an organization's entry point. Attackers are well aware of this fact; hence, they either steal credentials to act like a legitimate user or an insider trying to act maliciously.
Keeping in mind the above fact, we can say that In 2025, privileged access is no longer limited to just human users/accounts. Machines, bots, scripts, and third-party applications also need elevated access to execute day-to-day tasks. Hence, with organizations heavily relying on cloud environments, DevOps, and automation tools, the number of privileged accounts that exist has also increased manifold.
So, this ever-increasing expansion also means more endpoints, more systems, and more opportunities for attackers to exploit. A single exposed PAM account on a developer laptop or an unmonitored service account in the cloud can open doors to lateral movement and widespread damage.
So for these reasons, privileged access management tools are more important than ever. They help remove unnecessary privileges, monitor usage, detect anomalies in real time, and shut down risky behavior. It also raises alarm before it escalates.
PAM isn’t just limited to security. Additionally, it also simplifies audits, strengthens compliance, and enhances visibility across the organization. Most of the business work under strict regulations, hence implementing a privileged access management solution can be the differentiator between passing an audit or facing heavy fines.
In our experience, companies that prioritize PAM early on tend to experience fewer breaches, lower recovery costs, and a more confident security posture overall.
What Can Be Considered as a Privileged Account?
In an organization not all user accounts are defined as equal. Some carry far more sensitivity and are riskier in comparison to others. These are accounts known as privileged accounts, and they also come with elevated permissions. These allow users or systems to access sensitive data, manage configurations, or even control entire IT environments.
If you're wondering why attackers are so focused on privileged accounts, it's very simple: once the hackers are in, they can do almost anything. They are eligible for actions such as modifying files, shutting down services, and even stealing data. This is the reason why privileged access management (PAM) is designed to keep these accounts under close scrutiny by keeping a closer watch.
A privileged account could belong to a person, a machine, or even a script. The key differentiator is the level of access it holds.
Let’s break it down:
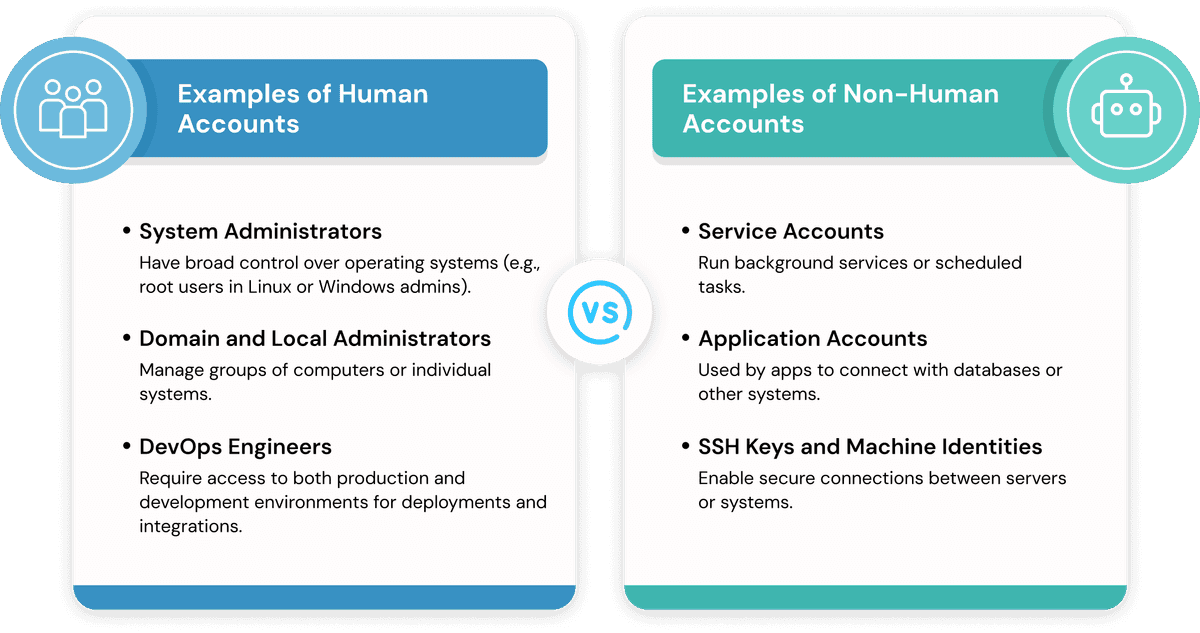
Examples of Human Accounts:
Human accounts are those that are used by actual people in technical/administrative roles. They usually have access to critical systems and are often the first targets when it comes to a scenario such breach.
1. System administrators: These users have broader and deeper control over operating systems. Think of root users in Linux or Windows admins.
2. Domain and local administrators: Responsible for managing groups of computers or local systems. One misstep here can ripple across an entire network.
3. DevOps engineers: Often need both production and development access, which gives them control over deployments, integrations, and pipelines.
These roles often require high-level access to get the job done, but without proper oversight, they can also become a vulnerability.
Examples of Non-Human Accounts
Not every privileged account has a face behind it. In fact, many operate in the background quietly running tasks, moving data, or connecting systems.
1. Service accounts: These accounts run background services or scheduled tasks. They often go unmanaged for years and can become ticking time bombs if misused.
2. Application accounts: Used by apps to communicate with databases or other apps. These accounts can hold access to everything from user records to transaction histories.
3. SSH keys and machine identities: These enable secure connections between servers or systems. If stolen or duplicated, they can silently open doors across your infrastructure.
In our experience, non-human privileged accounts often fly under the radar. They’re not visible on org charts, but they hold critical roles in keeping operations running.
PAM vs IAM vs PIM: What’s the Difference?
Let’s face it cybersecurity jargon can get confusing fast. PAM, IAM, PIM... it’s a lot. But once you break it down, the differences are clear and important.
Identity and Access Management (IAM) is the broadest of the three. It handles how users across an organization are identified, authenticated, and granted access. From your everyday employee login to access rights for contractors, IAM ensures people get the access they need—and nothing more.
Privileged Access Management (PAM) is a specialized branch of IAM. It focuses on accounts with elevated permissions those that can access sensitive systems, change configurations, or manage other accounts. PAM helps secure these accounts through password vaulting, session monitoring, and least privilege access.
Privileged Identity Management (PIM) zooms in further. It provides time-bound and approval-based access to privileged accounts. Think of it as PAM with a stopwatch—access is granted only for a specific task or time period, and then revoked. PIM often includes features like just-in-time access, multi-factor authentication, and access reviews.
So, while they all help manage access:
- IAM is the umbrella for identity lifecycle and general access
- PAM secures high-risk privileged accounts
- PIM manages how and when privileged access is granted
Key Features of PAM Solutions
A strong privileged access management solution goes beyond just locking down admin accounts. It offers a full toolkit for managing, monitoring, and securing access in a dynamic IT environment. Here’s what you should expect from a modern PAM system:
1. Password Management: Centralized storage, auto-rotation, and enforcement of strong credential policies.
2. Session Monitoring: Real-time visibility into privileged user sessions. Useful for both security teams and audit logs.
3. Access Control: Granular permission settings based on roles, tasks, and context. Helps enforce least privilege at scale.
4. Activity Logging: Keeps a detailed log of every privileged action taken. Essential for forensics and compliance reporting.
5. Just-in-Time Access: Grants temporary access only when needed, then revokes it. Ideal for minimizing standing privileges.
6. Integration with Other Tools: Seamless connectivity with IAM systems, SIEM platforms, cloud security tools, and more.
7. Additional Capabilities:
- Multi-Factor Authentication (MFA) for extra protection
- Secure Remote Access for third-party vendors and remote teams
- Privileged Account Discovery to uncover unmanaged or hidden accounts
- Reports and Alerts to surface unusual behavior before it becomes a breach These features work together to reduce risk, simplify compliance, and ensure high-level accounts are always under control.
Benefits of Privileged Access Management
Companies that invest in a robust PAM solution aren’t just checking a security box—they’re building a stronger foundation for everything else.
Here’s what they gain:
- Reduced Attack Surface: By limiting access and exposure, PAM closes off common attack paths used in breaches.
- Improved Visibility and Accountability: Every privileged action is logged and monitored, making it easier to detect and respond to threats.
- Better Compliance: Whether it's SOX, HIPAA, PCI-DSS, or internal governance, PAM simplifies audits with clear access trails.
- Support for Zero Trust and ITDR Models: PAM enforces least privilege, identity verification, and continuous monitoring—all core to Zero Trust and Identity Threat Detection and Response.
- A Must-Have for Cyber Insurance: With rising requirements, PAM is increasingly essential for securing or renewing cyber insurance coverage.
Common PAM Risks and Challenges
Even with the right tools in place, privileged access management isn’t always smooth sailing. Many organizations run into technical limitations, process gaps, or internal resistance that can put their entire security posture at risk. Let's break these challenges down.
Technical Challenges
Some of the most dangerous risks live under the radar—often in the form of poor practices or overlooked systems.
Developers sometimes embed passwords directly into code or scripts. Once released, these credentials can be nearly impossible to track or rotate.
When employees leave or roles shift, their privileged accounts are often left active. These forgotten accounts can become a silent entry point for attackers.
If a privileged account is compromised, attackers can move across systems and escalate access quickly. One weak link can compromise an entire environment.
Organizational Challenges
Even the best PAM tools won’t work without internal alignment and awareness.
IT teams and developers may resist PAM due to perceived friction or slowed productivity. Change management becomes just as critical as technology.
PAM platforms can be feature-rich, but without proper implementation and training, they can overwhelm teams or remain underused.
You can’t protect what you can’t see. Many organizations lack visibility into all existing privileged accounts, especially in hybrid or multi-cloud environments.
Real-World Breaches PAM Could Have Prevented
Most of the cyberattacks didn’t just happen because hackers were brilliant and they used high-tech tools. They happened because privileged access wasn’t properly managed. And many of these incidents could have been prevented with a strong privileged access management solution in place.
Here are three real-world breaches that highlight what goes wrong when PAM security is overlooked:
1. Edward Snowden and the NSA: The Ultimate Insider Threat In 2013, Edward Snowden, a contractor with privileged access to NSA systems, exfiltrated massive amounts of classified data without triggering alarms. His actions exposed sensitive surveillance programs and changed global conversations around privacy.
Had PAM tools like just-in-time access, session monitoring, and activity logging been fully enforced, the unauthorized access could have been flagged or at least significantly limited. Privileged account management would’ve made it much harder for a single user to download, store, and leak sensitive data without detection.
2. Uber’s GitHub Leak: Hardcoded Credentials Gone Wrong In 2016, attackers gained access to Uber's AWS environment through a simple mistake: hardcoded credentials stored in a private GitHub repo. Once inside, they accessed personal data of over 57 million users and drivers.
This is a textbook case of why privileged access management is critical, even during development. A proper PAM solution could’ve ensured credential rotation, enforced secure vaulting, and prevented hardcoded secrets from being exposed. In environments where DevOps and automation move fast, PAM tools act as a safety net.
3. Bangladesh Bank Heist: When Hackers Hijack SWIFT In 2016, cybercriminals infiltrated the Bangladesh Bank and used stolen credentials to submit fraudulent SWIFT transactions, attempting to steal nearly $1 billion. They successfully moved $81 million before being detected.
This incident involved poor monitoring of privileged activity and a lack of visibility into critical financial systems. With PAM access controls, real-time session monitoring, and alerts on anomalous behavior, this kind of financial exploitation could have been prevented or stopped much earlier.
PAM Across Industries – Who Needs It Most?
| Industry | Risk Example | PAM Application |
|---|---|---|
Finance | Wire fraud, insider trading | Vaults, MFA, JIT |
Healthcare | PHI access, compliance | Session monitoring |
SaaS / DevOps | CI/CD pipeline secrets | Secrets mgmt, JEA |
Public Sector | Insider leaks, espionage | Least privilege, logging |
Retail | POS attacks, third-party risk | RBAC, remote access control |
How PAM Works
Privileged Access Management (PAM) is designed to ensure that only the right people (or systems) have access to sensitive resources and only when it’s actually needed. Here's how a typical PAM solution functions across its lifecycle:
- Discover Accounts and Privileges: The first step is visibility. PAM tools scan your environment—on-premises, cloud, and hybrid—to identify all privileged accounts. These could be admin accounts, service accounts, or even automation scripts with elevated access. Without discovery, it’s impossible to secure what you don’t know exists.
- Store Credentials in a Secure Vault: Instead of relying on users to remember or share passwords, PAM systems store credentials in an encrypted vault. Access to these credentials is brokered through the vault, so no one ever sees the actual password. This eliminates the risk of password reuse, theft, or hardcoding.
- Grant Just-in-Time (JIT) Access: PAM solutions minimize the risk of privilege misuse by providing temporary, task-specific access. A user or system is given elevated permissions only for the duration of the task. Once the job is done, the access is revoked automatically, reducing the attack surface significantly.
- Monitor and Record Privileged Sessions: Every privileged session, whether initiated by a human or a machine, is monitored in real-time. Session recording, keystroke logging, and behavior analytics give security teams full visibility and traceability. If something unusual happens, alerts are triggered instantly.
- Revoke or Expire Privileges: Access that’s no longer required shouldn’t linger. PAM tools allow you to set expiry times for access rights or automatically revoke them after session end. This prevents privilege creep where users accumulate more access than they need over time.
- Log and Report All Activities: PAM creates a detailed, tamper-proof audit trail of every privileged action. These logs are essential for compliance, investigations, and internal governance. Many organizations also integrate PAM with SIEM platforms for proactive threat detection.
PAM Implementation Best Practices (2025 Edition)
Deploying a privileged access management solution is not just plugging in an additional security tool, but it's also about building a sustainable access control strategy. These best practices reflect what modern organizations are doing right in 2025:
- Enforce the Principle of Least Privilege: In an organization, every user, system, or process should only have the minimum permissions necessary to perform its tasks and nothing more.Moving forward this limits potential damage if a privileged account is compromised. PAM tools make this easier through its granular access control policies along with real-time enforcement.
- Combine Multi-Factor Authentication (MFA) with Session Monitoring : MFA ensures that access requires more than just a password like a one-time code or biometric factor. Combined with session monitoring, it gives security teams visibility into who accessed what, when, and how. This dual-layer defense stops both credential theft and misuse.
- Automate Password and Credential Rotation: Static credentials are a security liability. PAM automates the rotation of passwords and secrets at set intervals or after every use, reducing the risk of credential exposure. This is especially important in environments with frequent changes or third-party access.
- Implement Just-in-Time (JIT) Access Controls : JIT access ensures that elevated privileges are granted only when needed and for a limited duration. This eliminates the persistent admin rights, one of the top reasons used in lateral movement and privilege escalation attacks.
- Secure DevOps Secrets and Automation Credentials: DevOps environments rely heavily on scripts, APIs, and automation tools, all of which use credentials to operate. PAM solutions integrate with CI/CD pipelines to manage secrets securely, prevent hardcoding, and apply access controls even in fast-moving deployments.
- Audit, Analyze, and Report All Privileged Activity: Every access request, approval, session, and change should be logged. PAM provides real-time analytics and historical reports that help with compliance (e.g., SOX, HIPAA, PCI-DSS), but also help security teams spot trends, anomalies, and potential insider threats before they escalate.
Expert Suggestion: Choosing the Right PAM Tool
Selecting a PAM solution isn’t just about ticking a security box; it’s about finding the right fit for long-term risk reduction. With so many tools available, the real question isn’t what PAM does, but which one aligns best with your environment and security goals.
“When evaluating a PAM solution, go beyond surface features and prioritize tools that offer dynamic privilege elevation, real-time session monitoring, and deep integration with your IAM and SIEM stack. Many breaches happen not because access was granted, but because it was never re-evaluated. The most effective PAM systems treat every access request as a risk signal, not just a formality."
Frequently Asked Questions (FAQs)
What is the difference between IAM and PAM?
IAM (Identity and Access Management) manages who can access what across your organization—think login access and general permissions. PAM (Privileged Access Management)focuses on high-risk accounts those with elevated privileges that can change settings, access sensitive data, or manage systems. In short: IAM handles everyday access. PAM secures the keys to the kingdom.What is an example of a privileged access?
A system administrator logging into a production server to update code is a classic example of privileged access. They're not just using the system; they're controlling it.Why is PAM needed?
PAM is needed because privileged accounts are a top target for attackers. If compromised, they can be used to steal data, shut down systems, or move laterally across your network. PAM helps control, monitor, and limit that powerful access before it becomes a problem.What is an example of PAM?
A PAM solution that vaults administrator passwords, records privileged sessions, and grants time-limited access to critical systems (like CyberArk, BeyondTrust, or even native tools in Azure AD) is a real-world example. It keeps sensitive access under lock and key—with full oversight.