
What is Identity Governance and Administration (IGA)?

Definition of identity governance and administration
Identity Governance and Administration (IGA) is a crucial component of the modern identity and access management (IAM) solution. The focus is on managing user identities, defining which individual has access to what resources, and ensuring that such access is not just secure but also compliant with internal policies and regulatory requirements.
Through Identity Governance and Administration (IGA), organizations can actually have a centralized and clear view of all user identities present, as well as their access rights. With this visibility, teams can define and enforce access policies that align with the business needs and compliance standards. IGA solutions not only ensure that users have the right level of access, but it also safeguards digital assets from unauthorized access. This is done through continuous monitoring of permissions and access-related activity, which helps reduce risk, prevent misuse, and simplify compliance audits. Overall, we can say that IGA strikes the right balance between operational access and governance, giving organizations the control they need without slowing down their productivity.
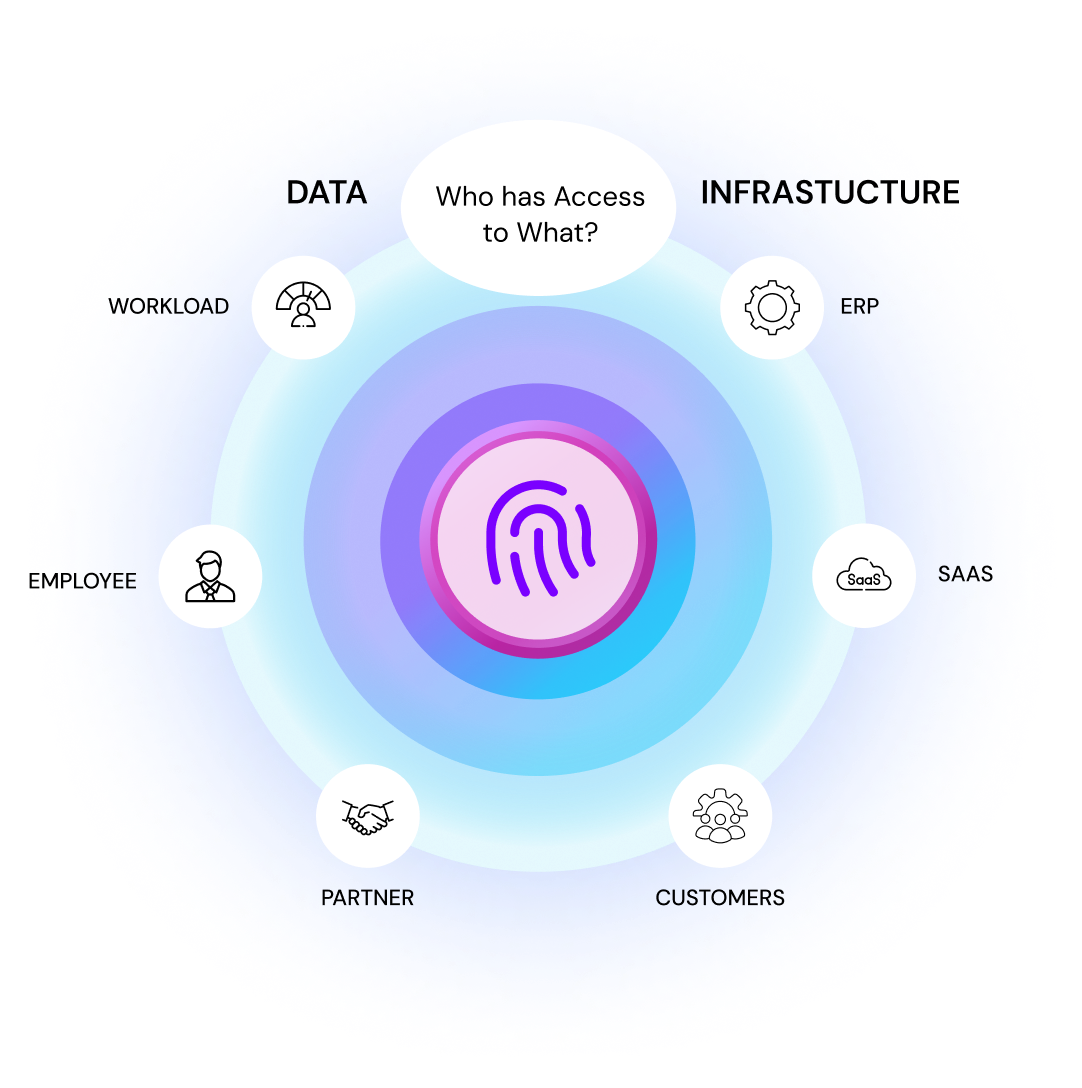
Why Organizations Need IGA
Most of the companies in today’s times are dealing with scaling users, devices, applications, and data both on-premises and in cloud environments. Without a proper strategy to oversee user identities and their access control, this complexity can open the door to various security-related risks, policy violations, and compliance failures.
This is where Identity Governance and Administration (IGA) comes into play.
-
Enhances Security & Reduces Risk
IGA solutions help in identifying and eliminating excessive rights, unrequired and unauthorised access. Not just this, it also marks and flags any risky user behavior and suspicious user activities. All these enable faster rectification of any issue before any threat escalates further. -
Regulatory Compliances
Ranging from several crucial compliances from GDPR to HIPAA, IGA solutions help enforce access policies and automate audit trails. This makes it easy to meet and fulfill complex regulatory compliance requirements. -
Improves Operational Efficiency
By automating tasks and offering self-service capabilities like password resets, access requests regarding specific systems/apps/services on an ad hoc basis, IGA solutions reduce manual workload with little to no IT involvement and enable users with various self-service tools. -
Enabling Business Productivity
Fast, policy-based access to critical resources helps users stay productive while ensuring access management doesn’t compromise on the security aspect. -
Reduces insider threats
IGA solutions offer real-time dashboard insights, along with analytics for risk management on a proactive basis. Insider threats are taken care of by timely identifying and revoking orphaned accounts. Additionally, it also seamlessly integrates with the existing security infrastructure, offering a unified security posture.
Features of an efficient IGA Solution
IGA solutions are designed to enhance visibility and control over the way organizations manage user identities and user access across their systems. Let us now take a detailed look at the key features of a modern Identity Governance and Administration (IGA) solution:
-
Integration of Connectors for Identity Management
IGA solutions come with a set of pre‑built connectors. These connectors integrate with various enterprise directories, HR systems, as well as applications, both on-premises and cloud-based within the IGA platform. This helps to unify user identity data while allowing seamless synchronization of access permissions. The integrations support federated identity, enabling users to securely access multiple systems with a single set of login credentials. -
Automated Access Request Workflows
With the help of automated workflows, users can request access to any resource or application, and managers have the right to approve or deny access based on pre-defined roles and policies. All of this streamlines the identity administration processes while ensuring enforcement of access management rules. -
Provisioning and De-Provisioning
Right from the moment an employee joins the organization, gets onboarded, and changes roles within the organization, an IGA solution assigns and manages access rights (also known as entitlement management) until the point of the user’s offboarding journey. Overall, effective IGA solutions not only automate access provisioning and de-provisioning but also ensure real-time updates when roles change and track all access activities. -
Entitlement Management
With entitlement management, admins can define what specific actions a user can perform in different applications and in the systems. For instance, a few users may be able to add, edit, or remove any particular data, while the rest of the users may only have view access. On the other hand, users such as super admins can even delete data. -
Role-Based Access Control (RBAC)
In Role-Based Access Control, the user access is restricted based on job responsibilities or job roles and only has access to the permissions attached to the same. During the time of employee onboarding, IGA automatically provides the required access to the associated role. This ensures least privilege access and enhances security. -
Access Review and Certification
IGA platforms provide regular access reviews and access certification campaigns, enabling organizations to validate whether users still require access to particular resources. This supports both regulatory compliance efforts and internal policy enforcement. -
Segregation of Duties (SoD) Controls
To reduce risk and prevent fraud, Identity Governance enforces Segregation of Duties by ensuring that no single user has conflicting access rights, such as the ability to initiate and approve transactions. SoD policies are critical for maintaining compliance and strengthening internal security controls. -
Analytics and Reporting
Real-time analytics and reporting capabilities allow security teams to monitor user identity activities, detect anomalies, and generate detailed audit logs. These insights help address security concerns proactively and support external audits.
How Identity Governance and Administration (IGA) Integrates with Existing Security Systems
IGA doesn’t work in isolation; it’s built to connect and strengthen the tools you already use in your security ecosystem. Think of it as the control center that manages who gets access, to what, under what conditions, and how that access is governed. Here’s how IGA fits into your current security infrastructure:
-
Authentication Systems
IGA works hand-in-hand with tools like:- Single Sign-On (SSO) – so users log in once and access many systems
- Multi-Factor Authentication (MFA) - for extra identity checks
- Identity Providers (IdPs) – like Okta or Azure AD that handle login credentials
This connection ensures access isn’t just fast, but secure and policy-driven.
-
Directory Services (e.g., Active Directory)
IGA connects with directory services like LDAP, Active Directory, and Azure AD to:- Sync user accounts and groups
- Manage access rights centrally
- Keep permissions updated in real time
This helps keep user data and access consistent across all systems.
-
Applications and Cloud Services
IGA platforms integrate with:- SaaS apps like Salesforce, Google Workspace
- Cloud platforms like AWS, Azure (IaaS)
- Legacy systems via connectors (SCIM, APIs)
This makes it easy to manage access to all systems—new and old, all from one place.
-
IT Service Management (ITSM) Tools
IGA works with platforms like ServiceNow or Jira to:- Automate access requests and approvals
- Trigger identity workflows (onboarding, offboarding)
- Track issues and incidents tied to identity access
This makes access part of the same process your IT team already uses.
-
Mobile Device Management (MDM) & Endpoint Security
IGA checks if a user’s device is secure before granting access. For example:- Is the phone encrypted?
- Does the laptop have an antivirus?
Access is granted only if both the user and the device are trusted.
-
Privileged Access Management (PAM)
IGA teams up with PAM tools to handle high-risk access (like admin or root users). It helps:- Approve and monitor privileged account usage
- Ensure such access is temporary and reviewed regularly
This keeps your most sensitive data and systems extra secure.
-
SIEM (Security Information and Event Management)
IGA sends access logs and user activity data to SIEM platforms like Splunk or IBM QRadar. This helps:- Detect risky behavior in real-time
- Investigate unusual access patterns
- Prove compliance with audit logs
You get deeper visibility and context into threats and events.
IGA vs IAM: A Strategic Comparison
| Identity Governance and Administration (IGA) | Identity and Access Management (IAM) |
|---|---|
| 1. Delivers end-to-end control over the identity lifecycle, from onboarding to deprovisioning, with governance at its core. | Focuses on basic identity creation and access control, primarily for authentication and authorization. |
| 2. Ensures that access is appropriate, auditable, and aligned with business policies through access reviews, policy enforcement, and risk-based controls. | Authenticates users and grants access based on predefined roles or credentials, without ongoing governance. |
| 3. Provides automation for provisioning, deprovisioning, access reviews, and compliance reporting, reducing manual workload and audit effort. | Automates login and access permissions, but lacks full lifecycle oversight and compliance tooling. |
| 4. Built to meet compliance and regulatory requirements by maintaining detailed access logs, SoD policies, and certification workflows. | Helps meet basic access control needs, but relies on external tools for audit and compliance support. |
| 5. Integrates across your IT ecosystem, unifying HR systems, apps, directories, cloud platforms, and security tools for contextual access governance. | Primarily integrates with authentication systems, focusing on validating identity at the point of access. |
| 6. Reduces insider threats and policy violations by enforcing least-privilege access and continuously monitoring user access behavior. | Lacks deep governance visibility, often unable to track or revoke outdated or risky permissions. |
Discover Identity Governance with Tech Prescient
Modernize Your Identity Strategy
As identity becomes the new security perimeter, organizations can no longer rely on fragmented, manual access control methods. Tech Prescient helps enterprises transition to a unified, automated, and policy-driven identity governance framework.
Why Choose Tech Prescient?
Tech Prescient’s IGA capabilities, powered by platforms like Identity Confluence, streamline lifecycle management, enforce least-privilege access, and automate compliance, delivering measurable outcomes in security, efficiency, and cost savings.
Future-Ready IGA for Secure Growth
From AI-powered risk detection to seamless integrations with HRMS, ITSM, and cloud infrastructure, Tech Prescient empowers security teams to scale governance effortlessly as business needs evolve.
Ready to Elevate Your Identity Governance?
See Tech Prescient in Action
Discover how Tech Prescient’s IGA solutions help enterprises reduce risk, achieve compliance, and accelerate digital transformation.
Frequently Asked Questions (FAQs)
-
What is IGA in identity?
IGA, or Identity Governance and Administration, is the manner in which organizations manage who has access to what across all systems, applications, and data. It ensures that access is granted based on job roles and business policies only. It also tracks and reviews access to maintain security and compliance.
-
What does the IGA stand for?
IGA stands for Identity Governance and Administration. It combines access management with governance processes like access reviews, policy enforcement, and compliance reporting to ensure secure and appropriate access to digital resources.
-
What is provisioning and deprovisioning?
Provisioning is the process of giving a user access to the tools, apps, or systems they need to do their job. Deprovisioning is the process of removing access when it’s no longer needed like when someone leaves the company or changes roles. Together, these steps help prevent unauthorized access and reduce security risks.
-
What is provisioning in IGA?
In IGA, provisioning refers to the automated assignment of access to users based on their role, department, or responsibilities. For example, when a new employee joins, IGA ensures they automatically receive access to the apps and data needed for their role without manual setup.
-
What is Deprovisioning?
Deprovisioning is the removal of access rights from users who no longer need them. This typically happens when someone exits the organization, changes roles, or no longer requires access to specific systems. It helps avoid security gaps caused by leftover or inactive accounts.
-
What does IGA mean in cybersecurity?
In cybersecurity, IGA is a key part of protecting systems from misuse. It helps organizations manage and monitor digital identities, enforce access rules, and ensure only the right people have the right access. IGA also plays a critical role in preventing data breaches, meeting compliance requirements, and reducing insider threats.