
What Is Access Control? Why It’s the Foundation of Identity Security in 2026

Access control is no longer a mere technical checklist or a technicality; it's the gatekeeper of today's modern cybersecurity. Access control specifies exactly who may interact with your systems, in what context and for what intent and purpose. With organizations facing an unprecedented range of cybersecurity challenges in 2025, including remote work and hybrid clouds, controlling access to sensitive data and applications is more than a security must-have, it's a necessity. This blog will unpack access control, how it works, and why it is central to both a secure and compliant business and still an agile one, through platforms like TechPrescient’s Identity Confluence.
Key Takeaways:
- Access control determines who can access what, when, and how
- Core pillars include authentication, authorization, and enforcement
- Popular models: RBAC (role-based), ABAC (attribute-based), DAC, and MAC
- Identity Governance (IGA) turns access control into a manageable, auditable process
- Enforcing least privilege and MFA is a modern must-have
What Is Access Control?
Access control is a fundamental security mechanism that ensures only authorized users, devices, or systems can access designated resources, be it files, databases, applications, or physical spaces. It governs how identities interact with systems, making sure sensitive information stays out of the wrong hands. Modern access control also accounts for context such as time, location, or device to make real-time, dynamic access decisions.
Why Access Control Matters in 2025
As digital infrastructures become more distributed, the importance of access control gets exponentially more important. In 2025, access control is not just a technical specification; it is a strategic protection against modern threats and a foundation of enterprise resilience.
- Breaches happen due to lack of controlled access: According to global threat reports, 80% of cyber breaches involve misuse of credentials or privilege escalation, either intentional or unintentional. Without an established access control system, organizations operate with a broad attack surface for attackers to traverse laterally through their internal systems.
- The expanding cloud attack surface: Cloud platforms and SaaS are widespread, and the use of remote work has blurred the true perimeter boundaries. Access control creates borders in their hybrid ecosystems and establishes clear boundaries so that identity not location on a network is a new identity security perimeter.
- Compliance pressures and audit requirements: Modern IGA-enabled access control requires role-based provisioning, access reviews, and audit logs for audits as part of compliance, that can ensure organizations have controls in place for who can access sensitive data across frameworks such as HIPAA, SOX, or ISO 27001.
- Mitigating Insider Threats and Over-Provisioning: Excess or stale access from current, former (or prospective) employees, contractors or users poses a serious insider risk. When organizations do not consistently enforce least privilege or conduct access reviews, they open themselves up to the risk of data exfiltration, sabotage or regulatory violations.
Access control, especially if managed through modern IGA platforms, is a continuous control. It provides the organization with proactive oversight, automates and reduces human error, and responds to the rapidly evolving business and threat environments.
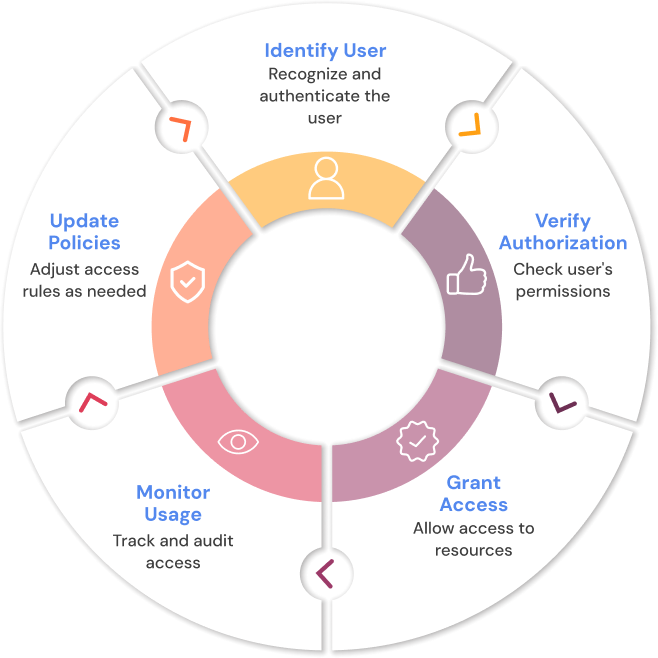
Key Components of Access Control
Authentication
Authentication verifies that the requester actually is who they say they are. Today, strong identity assurance offers passwordless authentication, biometrics (face vs. travel planning with passport), OTPs (One-Time Password), hardware tokens, and behavioral biometrics. MFA is being adopted more frequently because it combines something you know (password), something you have (device), and something you are (biometric), all of which substantially decrease your chances of identity spoofing.
Authorization
Authorization limits access to actions that authenticated users can take. Policies can be based on job functions (RBAC), risk, contextual input signals (device, location) (ABAC), or hybrids. Strong authorization protections limit the attack surface area by only allowing the least amount of access and a user needs to complete a task.
Enforcement
Enforcement ensures that access policy is implemented and maintained at all times. Enforcement engines integrate with applications, APIs, and network-level enforcement entities to provide real-time decisions. Enforcement engines can track an individual user and spot anomalous activity like logging in at 2:00 a.m. or trying to access their account in a different country and dynamically limit or revoke that user's access.
Component | Description |
|---|---|
Authentication | Validates identity (e.g. SSO, MFA) |
Authorization | Determines access levels (read, write, admin) |
Enforcement | Applies policy logic in real-time |
Types of Access Control Models
Various access control models provide different flexibility, security and administrative overhead. The access control model you select ultimately depends on your organization, its structure, its compliance needs, and its appetite for risk.
Role-Based Access Control (RBAC) assumes access control based on roles defined by the organization. Each role has access tokens that are associated with permissions, and it enables large-scale access management. For example, the HR manager can view employee records but cannot edit anything related to finance. Generally, RBAC works well in precise, structured environments where job functions align closely to access requirements.
Attribute-Based Access Control (ABAC) does not use static roles and focuses on a multitude of contextual factors, for example, user location, device type, and time of access to inform access decisions in real-time. ABAC provides more explicit decisions, for example, granting access during business hours from a company-managed device or application. ABAC is an appropriate approach for organizations that are in flexible, cloud-first environments, where any situation can arise.
Discretionary Access Control (DAC) provides flexibility for data owners by allowing them to decide who can, or cannot, access resources. This is often seen in collaborative tools, like Google Drive, which allows a user to share a document or folder at their discretion. While this is convenient for access control, it may create challenges for consistent policy enforcement and auditing at scale.
Mandatory Access Control (MAC) is the strictest model of the three and is enforced regardless of the discretion of the user (i.e., the data owner). Policies are enforced based on the classification and clearances of a user. This is typically enforced in government and military settings. The least privileged user and system administrator are unable to override policies. It is a great option if you desire high security and strict access controls. However, MAC is often too restrictive for general commercial uses.
Model | Description | Example |
|---|---|---|
RBAC | Access by role | HR can access employee records |
ABAC | Access by attributes | Allow access only from corporate IP |
DAC | User-controlled access | Shared Google Drive folders |
MAC | System-enforced | Government/military environments |
Challenges of Traditional Access Control
- Manual Provisioning Errors: Relying on manual access requests results in incorrect permission assignments, delays in decisions, and workload increases on IT teams.
- Orphaned Accounts: When employees or vendors leave the organization, they may keep their credentials who could then reuse them, deliberately or unintentionally exposing your systems.
- Poor Visibility: Access rights that are spread across various disparate systems, and without centralized governance, cannot be audited or risk-assessed.
- Inconsistent Enforcement of Policy: Without consistent tools, security policies might be enforced inconsistently resulting in critical gaps in coverage or duplication across cloud, on-prem, and third party services.
How Identity Governance (IGA) Enhances Access Control
IGA augments and scales access control by automating lifecycle management of identity and enforcing policies and governance. Identity Confluence by TechPrescient helps enterprises through:
- Automated joiner/mover/leaver workflows: Automatically modify access as the employee moves or leaves the enterprise without delays or post-changes updates, based on role and status determined by the enterprise.
- Centralized policies: Define once and apply everywhere. IGA ensures that access control policies are applied consistently in cloud, SaaS, and legacy systems.
- Continuous access reviews and access certifications: Ongoing access policy assessments or access reviews based on events or calendar triggers with the application owner for current access that is still applicable.
- Role mining and SoD policy management: Evaluate access based upon actual usage patterns to identify access roles, and enforce separation of duties to avoid conflicting roles like dual-role fraud.
- Dashboards and audit logging: Provide current data on access history to enable security and compliance teams so they are always audit ready.
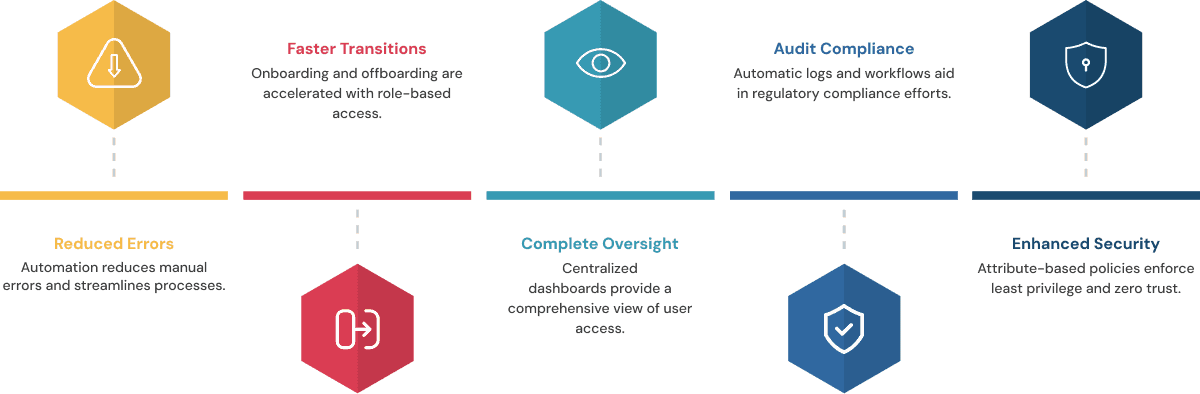
Benefits of Access Control with IGA
- Less Human error and Admin Overhead: We replace manual ticketing with automated workflows, removing configuration errors, and streamlining processes.
- Faster onboarding and offboarding: Users who are offboarded lose immediate access, while new hires get specific access on day 1 based on department and role.
- Total visibility: Centralized dashboards show who has what access across cloud, on‑premise, and third-party systems.
- Audit Readiness: Automatic logs and certification workflows help organizations stay compliant with GDPR, HIPAA, SOX providing ready-to-export proof evidence.
- Enforced Least Privilege and Zero Trust at Scale: Dynamic, attribute-based policies ensure users only have access to what they need when they need it in lockstep with modern Zero Trust frameworks.
Ready to Evolve Your Access Governance?
TechPrescient’s Identity Confluence combines intelligent access models, seamless automation, and enterprise ready governance into a single platform. If you're ready to bring together your fragmented controls and move towards intelligent identity management then simply reach out to our team to optimize your access strategy for 2025 and beyond.
Access Control vs IAM vs IGA
To build a resilient identity security strategy, it’s essential to distinguish between Identity and Access Management (IAM), Access Control, and Identity Governance and Administration (IGA). While the three areas are interconnected, each area serves an important, independent purpose as the following provides an overview.
IAM (Identity and Access Management) identifies the identity lifecycle, from account creation and password resets to user authentication, and IAM answers the question "Who are you?" It is the basis that allows entry for only verified identities.
Access Control takes IAM further by answering "What can you do once you're in?" Access Control identifies authorization: What systems or data can the user access; and the conditions in-place that permit access. This supports organizational policies like least privilege and Zero Trust.
IGA (Identity Governance & Administration) sits above IAM and Access Control with the objective of review, compliance, and alignment with internal policies and external requirements. IGA enables workflows (e.g. onboarding/offboarding), manages/automates access review, and has specific audit trails.
You may think of it as a three-tier system:
- IAM identifies or authenticates identities.
- Access Control governs access decisions for authorized identities.
- IGA governs the organizational whole for compliance and visibility.
Best Practices for Access Control in 2025
It is important to understand the distinctions between IAM, Access Control, and IGA when creating a comprehensive identity security architecture. IAM (Identity and Access Management) primarily relies on identity lifecycle management. This includes creating user accounts, authenticating users with credentials or with multi-factor authentication (MFA), and allowing for self-service functions such as password change or resets. IAM provides an initial construction for how users can access data and applications securely.
Access Control extended from IAM to then enforce the “rules” of what authenticated users can do in a system, specifically authorization management, who can access what data, applications, or systems and under what conditions. Access Control is primarily what then tells the user which resources they can see or interact with based on their Job or Risk Profile.
Identity governance and administration (IGA) provide the policy and oversight structure that governs IAM and Access Control. The goal of IGA is to ensure that access is correct technically, and is compliant with internal governance and external laws. IGA tools allow the organization to operate efficiently and maintain compliance by allowing for policies that govern and automate the provisioning/deprovisioning workflows, posing periodic access reviews, and generating audit-ready reports.
Here is what our expert suggests
We asked one of our senior identity architects at TechPrescient what truly makes access control work in the real world and here’s what they had to say:
“The biggest mistake I see organizations make with access control is treating it like a one-time setup. The truth is access control isn’t static. Your workforce changes, applications evolve, and new risks emerge every day. If your access policies don’t adapt, they become liabilities.”
“Our recommendation? Make access governance continuous. Don’t just assign roles, review them regularly. Don’t just enforce policies, monitor and test them against real-world behavior. And wherever possible, automate it. Automation doesn’t just save time, it eliminates the human error that attackers rely on.”
This expert insight aligns with what we’ve built into Identity Confluence: a dynamic, policy-driven, and constantly monitored access framework that’s built for scale, compliance, and rapid change.
Frequently Asked Questions (FAQs)
Q: What is access control in cybersecurity?
A: In cybersecurity, access control, defines the process of controlling who or what can access digital resources, data or physical assets. It is a way of ensuring that only authenticated and authorized people can interact with sensitive resources, and eliminate the chance of risk from unauthorized exposure or misuse.Q: How does Identity Governance (IGA) improve access control?
A: IGA enhances access control by automating identity lifecycle tasks such as provisioning, enforcing access policies through RBAC and ABAC, conducting periodic access reviews, and also providing compliance-ready audit trails from a central platform.Q: What’s the difference between IAM and IGA?
A: Where IAM manages the identities and authentication processes of users (like login and password reset), IGA is transforming the governance aspects to establish policies, review access and compliance against internal or external mandates or regulations.Q: What are the two most common types of access control?
A: The two most popular styles of access control are role based access control (RBAC), which assigns permissions to a user based on their roles in the organization, and discretionary access control (DAC), which allows a resource owner to determine which persons are able to access their resources.Q: Why is least privilege access important?
A: The least privilege principle provides the minimum access levels that users need to perform their job. This limits the potential for insider threats, data exfiltration, and the extent of damage that could result if an account was compromised.Q: What are examples of access control models?
A: RBAC: HR has access to employee records, not financial data.- ABAC: A user can access a file only from a corporate laptop during business hours.
- DAC: Users share access via Google Drive.
- MAC: Government systems restrict access based on security clearance.
Q: What role does MFA play in access control?
A: Multi-Factor Authentication (MFA) provides a stronger authentication by utilizing 2 or more forms of verification such as a password, plus a fingerprint that lessens chances of unauthorized access by using stolen credentials.