
What Is Role Based Access Control (RBAC) and Why It’s the Backbone of Secure Access Management?

Access is power - but only if it’s controlled.
Role-Based Access Control (RBAC) is becoming essential as controlling access within an organization gets more complicated, especially with growing teams, distributed work environments, and constantly evolving tools. As hybrid work becomes common, employees can now access the systems from different locations. The old ways of managing access weren’t built for such flexibility. At the same time, insider threats are a growing concern. This makes it important to have a secure and structured approach to access control.
That is when Role-Based Access Control (RBAC) comes in, bringing structure, security, and control to access management at scale.
To understand the value RBAC adds, let us know what is RBAC, why it is crucial for modern businesses, and how to implement it effectively with Tech Prescient’s IGA platform.
Key Takeaways:
- RBAC gives access based on job roles, so managing permissions gets easier.
- It follows the idea of least privilege, so people only get what they need.
- At its core, RBAC manages users, roles, permissions, and hierarchies for extra control.
- Real-world examples show how RBAC works across HR, DevOps, and Finance.
- Tech Prescient’s IGA platform enhances RBAC with automation and contextual access.
What Is Role-Based Access Control (RBAC)?
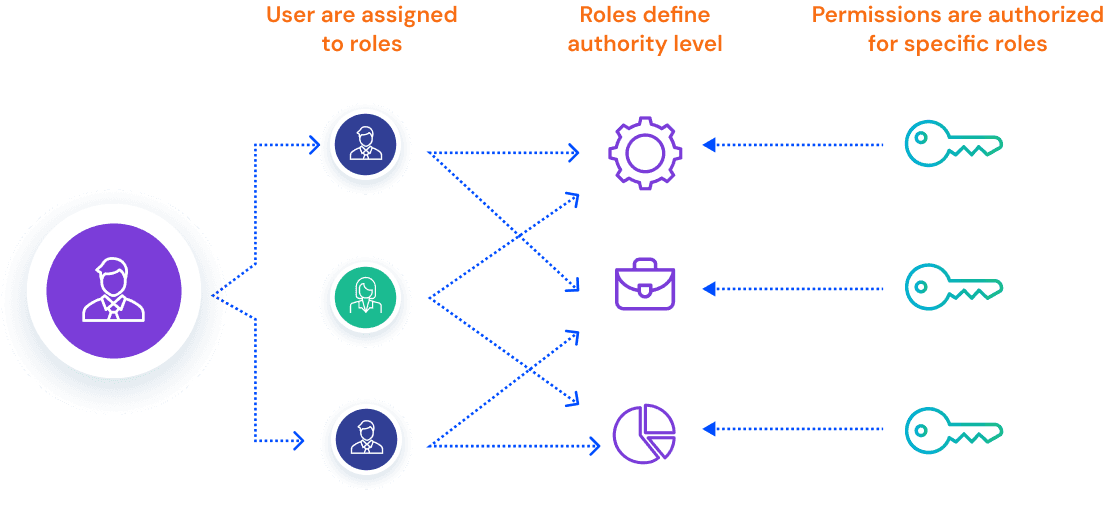
Role-Based Access Control (RBAC) is a method of managing access to systems and data by assigning permissions based on a user's job role within an organization. Instead of granting access to individuals one by one, RBAC allows you to define roles, like HR manager, developer, or sales executive, and assign permissions to those roles. Users are then added to roles, ensuring they only have access to what they need to do their job.
For instance, an HR recruiter can update employee records, while others can only view them. Each individual gets exactly the level of access they need to do their job. Nothing extra. Nothing missing.
- No confusion
- No constant checking
- Just easy and safe access control
It’s simple, secure, and works smoothly, even as your team grows.
With the advent of hybrid work culture, rapid scaling, and an increase in insider risks, having RBAC is a must. It helps to keep your system compliant, secure, and in control, even as your business keeps growing.
“Think of RBAC as your organization’s digital bouncer; only those on the list can get in.”
Why RBAC Matters in Modern Cybersecurity?
A report from Gartner states that 70% of organizations will switch their access governance with models like RBAC by 2026.
Every organization has sensitive data and records. When employees have access to more than what they need, it opens the door to potential risks, misuse of information, and security issues, often without any particular intent. Also, at the same time, locking away everything too tightly can slow down the teams. That is where RBAC steps in by giving the right people the right access based on their title or role, so work can flow smoothly. The key is finding the right balance between both.
Here’s how RBAC in cybersecurity stands out:
- It reduces mistakes when assigning or changing access
- It brings clarity by defining roles and access across departments
- It sticks to the “only what’s needed” rule, so no one gets more access than necessary.
- It makes staying compliant with standards like SOX, HIPAA, and GDPR a whole lot easier.
Core Components of RBAC
Every effective RBAC system is built on four core pillars: Users, Roles, Permissions, and Role Hierarchies. These elements work together to create a structured, scalable approach to access control. By understanding and designing each component clearly, you can avoid common pitfalls like access creep, inconsistent privileges, or manual errors, and ensure your RBAC setup remains secure and easy to manage as your organization grows.
Users can be anyone who needs access, whether it's a person, a machine, a bot, or even an API service account. Instead of giving permissions one by one, you simply assign roles, which act like permission bundles. It saves time and keeps things organized. And in more advanced setups, users can have more than one role, so their access adjusts based on everything they’re responsible for.
Roles are like handy permission bundles built around what someone does in their job. Whether it’s an HR manager, a developer, or a sales rep, each role includes exactly the access they need to do their work. The best part is that you can assign the same role to dozens or even hundreds of people, making access quick, clean, and consistent. No need to manage each person’s permissions one by one. And if someone fits into more than one role, they simply get the combined access they need.
Permissions are the actions someone’s allowed to take, like viewing info, making updates, deleting files, or using certain tools. Instead of setting these up person by person, they’re tied to roles. That means when you change something in a role, it automatically updates for everyone in it. For example, take away permission from the role, and it’s gone for everyone who has that role. It keeps things simple and clean and saves you from a ton of manual work.
Some RBAC systems let you set up roles in a hierarchy, which is kind of like a ladder. A senior role, like "Senior Engineer," can automatically access everything that an "Engineer" can do, plus a few extra permissions. Think of it like a parent-child relationship. The senior role automatically gets everything the junior role has; there is no need to set the same permissions again and again. It saves time, keeps things tidy, and makes access much easier to manage.
Real-World Examples of RBAC
Role-Based Access Control (RBAC) helps manage access to resources by assigning permissions based on a user's role within the organization. This approach ensures that individuals have only the access they need to do their jobs, nothing more, thereby minimizing the risk of unauthorized access and data breaches. Let’s explore some real-world examples to understand how it works in practice.
Take HR software, for example. HR managers need full access to handle salaries, performance reviews, and onboarding documents, while regular employees can only view their payslips, leave balances, and tax forms. This ensures sensitive information stays protected, and everyone gets exactly what they need.
In technical environments, access needs to be tightly controlled. Developers and DevOps engineers require entry to testing environments, deployment tools, and server logs to get their work done, while teams like Finance or HR don’t even see these systems on their dashboards, because they don’t need to. That’s the point of smart access control: reducing risk, protecting critical systems, and preventing accidental changes by those who shouldn’t have access in the first place.
In finance tools like ERP systems, access is carefully tailored to roles. Finance leads have full access to approve budgets, update payment records, and publish reports, while auditors are given read-only access; they can review everything but can’t make any changes. This setup maintains security, supports compliance, and ensures there’s a clear, auditable trail of every action.
Benefits of Role-Based Access Control
“The fewer keys you hand out, the fewer doors that can be opened.”
RBAC isn’t just about locking things down; it’s about making access easier to manage, safer, and ready to grow with your business. Here’s how it adds real value in everyday situations:
RBAC ensures individuals get access only to what they truly need for their job, nothing more. It’s like giving someone a key to just one room, not the entire building. If something goes wrong, the impact stays limited. It’s a straightforward way to reduce risk and maintain security, just the way modern access control should work.
When a new intern or software developer joins your team, you don’t need to set up their access manually. Just assign them the “Developer” role, and they instantly get all the tools and permissions they need. It’s faster, easier, and far less error-prone than configuring access one by one. RBAC simplifies onboarding and role changes, which is especially valuable when your team is growing fast.
Manually assigning access often leads to problems; someone gets too much access or not enough to do their job effectively. RBAC eliminates that guesswork. Once roles are set up, they can be consistently applied across the organization, reducing errors and keeping security tight without the need for constant oversight.
Audits can be stressful, but RBAC makes them much easier to manage. With clearly defined roles and consistent access patterns, it becomes easier to demonstrate compliance, whether it's showing who accessed what, verifying appropriate access levels, or producing audit logs on demand. Whether you're dealing with GDPR, HIPAA, or any other compliance standard, you have clear records and audit logs ready, no guesswork, no confusion, just straightforward reporting.
Whether you're running your backend on AWS, using Salesforce for CRM, or storing files on local servers, RBAC works seamlessly across all environments. Roles are defined once and can be applied consistently across cloud platforms, SaaS tools, and even legacy systems, eliminating the need to rebuild access controls every time your tech stack evolves.
RBAC vs DAC vs ABAC
Every organization has unique needs; some prefer a straightforward setup, while others require more flexibility or tighter control. Access management isn’t a one-size-fits-all approach, which is why there are different models like RBAC (Role-Based), DAC (Discretionary), and ABAC (Attribute-Based). Each has its strengths, and understanding how they work can help you choose the right fit for your environment.
Feature | RBAC | DAC | ABAC |
|---|---|---|---|
Based On | Based on predefined roles within the organization | Based on data ownership and user-defined permissions | Based on multiple contextual attributes like role, time, or location |
Flexibility | Medium – fixed roles offer structured flexibility | High-level users control who accesses their data | Very High – highly dynamic access decisions based on attributes |
Ease of Use | Easy – straightforward to assign and manage | Complex – depends on user decisions and setup | Complex – requires detailed attribute mapping and policy rules |
Best For | Enterprises with defined job functions | Small teams with informal structures | High-security organizations need fine-grained access contro |
Choosing between RBAC and ABAC comes down to prioritizing structure or flexibility. RBAC keeps things straightforward by assigning access based on roles, making it easy to manage, especially when job titles and responsibilities are clearly defined. ABAC, on the other hand, offers more granular control by factoring in attributes like location, time, or device, making it highly flexible but more complex to implement. The right choice depends on what your organization values most: simplicity, security, or strict compliance.
How to Implement RBAC in Your Organization?
Planning to roll out RBAC in your organization? Here's a simple step-by-step roadmap to help you get started, without giving your IT team a headache.
Start by identifying roles in your organization based on actual responsibilities, not just job titles. For instance, a marketing team member may need access to campaign tools and analytics, while a support agent needs visibility into tickets and customer data. Group individuals with similar tasks into well-defined roles. Keeping these roles clear and consistent makes access management easier to implement and even simpler to monitor over time.
Once roles are clearly defined, the next step is to determine exactly what each role should have access to, no more, no less. For example, a finance manager might need access to payroll and invoicing tools but have no reason to access the codebase. By keeping permissions tightly aligned with job responsibilities, you reduce unnecessary access and strengthen overall system security.
With roles and permissions in place, the next step is assigning users to those roles, ideally through your HR system or identity management tool. This ensures that new employees receive the right access from day one, without any manual setup. And when someone changes roles or gets promoted, their access updates automatically within the system, keeping everything accurate, efficient, and secure.
RBAC is not a one-time thing. People change roles or leave the company. So your access setup needs to keep up. It is desirable to do a quick check every few months. See who has access to what, and make sure it still makes sense. Remove old permissions, clean up unused accounts, and update roles when needed. It keeps things tidy and secure.
How Our IGA Platform Powers RBAC?
“Static RBAC is outdated; automated, contextual RBAC is the future.”
At Tech Prescient, we’ve taken RBAC a step further by building it right into our smart IGA platform.Here’s how we make access governance faster, smarter, and more seamless.
Roles within a company naturally evolve as teams expand, projects shift, and responsibilities change. Our platform adapts to these changes automatically, when someone switches roles, joins a new team, or takes on additional tasks, their access adjusts seamlessly. This ensures your access controls remain accurate and up to date, no matter how your organization grows or transforms.
Traditional RBAC grants access based on job roles, but what if someone logs in from an unsecured public Wi-Fi? That’s where our IGA platform adds an extra layer of intelligence. It evaluates context like time of day, device type, IP address, and location to adjust access dynamically. So, if a user logs in from the office, they get full access, but if they’re on a public network, permissions are limited or restricted. This maintains tight security without disrupting productivity.
Access creep occurs when users retain permissions they no longer need, a subtle but serious security risk. Our platform helps prevent this by enabling regular review check-ins, prompting managers to verify who has access to what and whether it’s still necessary. It’s a simple yet effective way to keep access up to date, eliminate unnecessary privileges, and strengthen your overall security posture.
Why repeat the same access rules across every system you use? With our platform’s real-time policy engine, you define access policies once and they’re enforced everywhere, whether it’s cloud apps, on-prem tools, or hybrid environments. This unified approach eliminates redundancy, ensures consistent enforcement, and keeps your access management both streamlined and secure.
Final Thoughts
RBAC (Role-Based Access Control) might sound technical, but it’s simply a smarter way to manage who can access what within your organization. When access gets confusing, like not knowing who has permission to see or do what, RBAC brings clarity and control. It reduces security risks, cuts down on manual effort, and makes scaling your access management far easier as your team grows. At Tech Prescient, we help organizations build secure, scalable access systems with RBAC at the core. If you're ready to simplify access and strengthen security, let’s connect and future-proof your setup.
Frequently Asked Questions (FAQs)
-
What is the difference between RBAC and ABAC?
RBAC works by giving access based on your job role. If you're in sales, you get access to sales tools and data, plain and simple. ABAC, on the other hand, takes things a step further. It looks at additional factors like your department, location, time, or even the device you’re using. So while RBAC says, “You’re in Sales, here’s your access,” ABAC says, “You’re in sales but working from home on a Sunday; let’s restrict what you can do for now.” -
What are the 4 types of access control?
RBAC assigns access based on roles, like job titles; DAC lets the data owner decide who gets access; MAC is strict and rule-based, often used in military settings; and ABAC grants access based on multiple factors like role, location, or even time of day. -
What are the different types of RBAC?
There are three types of RBAC: Basic RBAC assigns straightforward roles and permissions; hierarchical RBAC builds on that by stacking roles, so a “manager” inherits all permissions of an “employee” plus additional ones; and constrained RBAC adds rules or restrictions, such as preventing someone from approving their expense report, offering a smart way to avoid conflicts of interest.