
IGA vs IAM: What’s the Difference and Why It Matters in 2026


Today, securing user access isn’t enough; you need to govern it too. That’s where IAM and IGA come in. While they’re often used interchangeably, Identity and Access Management (IAM) and Identity Governance and Administration (IGA) serve distinct yet complementary roles in a modern cybersecurity framework.
If you’re evaluating identity solutions or seeking to tighten compliance, you must understand the difference between IAM and IGA. IAM is about enabling access, whereas IGA is about validating that access, ensuring that it is justified, secure, and compliant. In simple words, one secures the doors while the other keeps the keys accountable.
We’ve worked with security teams that invested heavily in IAM tools only to discover gaps in access certifications, user deprovisioning, or segregation of duties (SoD) later. That’s where IGA steps in as the missing piece.
In this guide, we’ll explore how IAM and IGA differ, how and where they work together, and how to integrate them in your identity security strategy.
Key Takeaways
- IAM (Identity and Access Management) secures access by managing user identities, authentication, and permissions.
- IGA (Identity Governance and Administration) ensures that access is appropriate, compliant, and auditable.
- IAM is operational. Focused on access control systems, SSO, and provisioning.
- IGA is strategic. Focuses on handling policy enforcement, access certifications, and risk governance.
- You need both to align with a Zero Trust architecture and meet growing compliance, audit demands.
- Investing in both prevents over-permissioning, improves segregation of duties (SoD), and supports least privilege access at scale.
What is IAM (Identity and Access Management)?
Identity and Access Management (IAM) is the foundational system of any organization that helps you identify who a user is and manage what access they’re allowed across the organization’s ecosystem.
At a basic level, IAM answers two important questions for any organization: Who are you? And what are you allowed access to? It makes sure that the right users, be it employees, contractors, or systems, gain the appropriate access to the right resources, streamlining your workflow and strengthening security.
For example, think of an employee logging into your internal portal. They utilize SSO to access their email, files, and tools. Then, MFA prompts their identity verification by sending a code to their phone.
Key functions of IAM:
-
Authentication and authorization
It is fundamental for modern enterprises with challenges such as increasing cloud adoption, usage of SaaS tools, and hybrid workforces. IAM implements strict access control and monitors user activity, reducing the risk of data breaches, simultaneously increasing operational efficiency and cutting IT overhead. That said, there can be implementation risks if the roles aren’t well-defined or if inadequate audits exist.
Common IAM solutions would include Okta, Azure AD, and Tech Prescient, offering robust features, making identity management seamless and secure.
What is IGA (Identity Governance and Management)?
Identity Governance and Management (IGA) adds the governance and oversight layer that IAM alone fails to provide. While IAM handles the “who gets access” part, IGA answers a much bigger question - “Should this person have access to begin with?”
IGA ensures that the access provided is compliant, appropriate, and accountable over time. It is the framework that keeps your organization audit-ready and aligned with necessary security policies.
IGA also streamlines the entire Identity Lifecycle, creating a safer environment for work, increased visibility, and reduced security breaches. For example, let’s say your finance department needs elevated access during the quarterly close. IGA can enforce access recertification every 90 days, automatically flagging accounts that no longer meet the policy.
Key functions of IGA:
-
Access certifications and periodic reviews
-
Segregation of Duties
-
Policy-based provisioning and deprovisioning
-
Audit and compliance reporting
SailPoint, Saviynt, and Oracle Identity Governance are leading platforms offering IGA tools with rich capabilities across hybrid and multi-cloud environments.
Core Principles of Zero Trust Architecture
What is Zero Trust?
Instead of always assuming that users or systems inside your network are ‘safe’ like traditional security models, Zero Trust is a modern security framework that operates on a simple rule: Never trust, always verify.
It treats all users, devices, and applications as non-trustworthy by default. In a Zero Trust environment, access is constantly evaluated, not just granted based on credentials but on context. In such a framework, trust has to be continuously earned, evaluated, and authenticated. This aligns tightly with both IAM and IGA by implementing least privilege access, constant authentication and authorization, and detailed policy enforcement.
Here’s how the core principles play out:
Verify Explicitly
This means making use of all available data and not just your credentials for authorization and authentication of every request.
What all is considered here? - User identity and role
- Device health and security posture
- Location and time of access
- Sensitivity of the requested resource
- Risk scores and behavioural patterns
For example, even if a user logs in successfully, they would still need multi-factor authentication (MFA) to access any sensitive financial data, especially if the login is from an unrecognized device or location.
This constant verification warrants that the access is always intentional, contextual, and secure.
Key Differences Between IAM and IGA
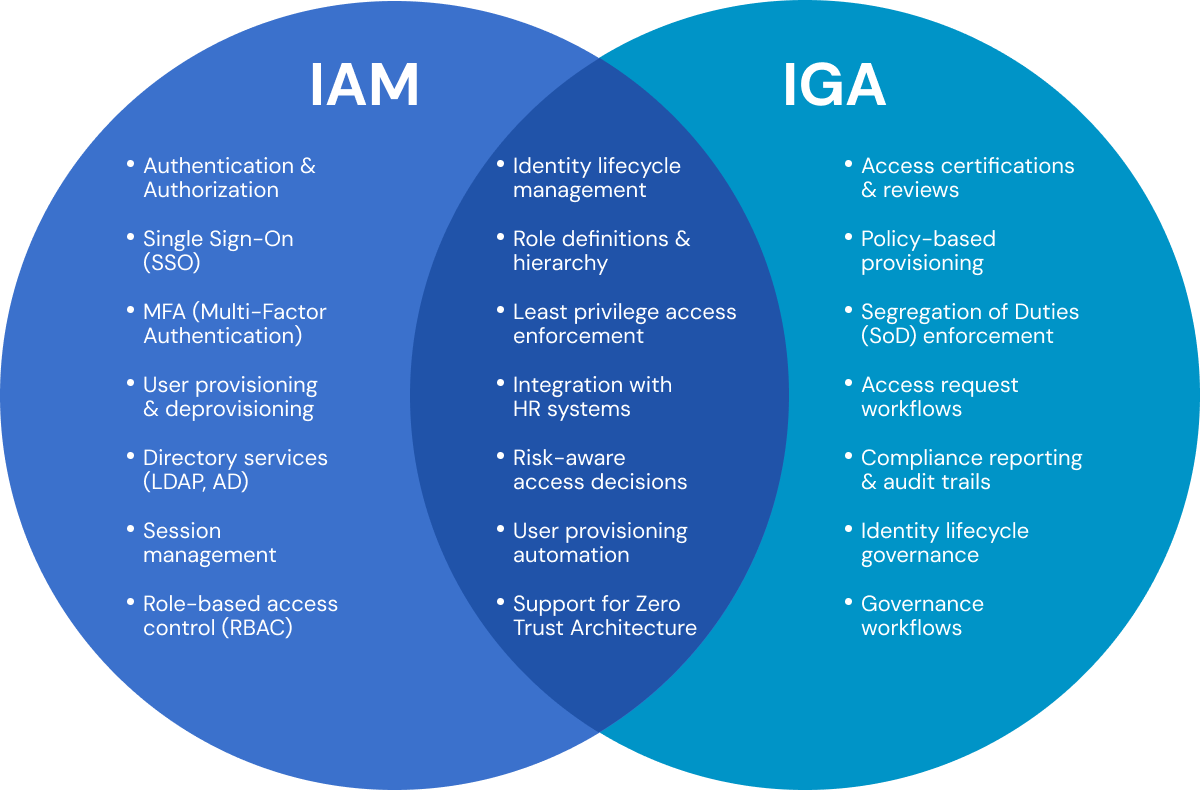
IAM determines who can access what, whereas IGA makes certain that access aligns with policies and regulations. Use the table below to better understand their roles.
| Feature | IAM | IGA |
|---|---|---|
| Purpose | To provide authentication, authorize access, and control it | To ensure access policies are compliant, enforce policies, and review access |
| Scope | Focuses on Operational systems [day-to-day access] | Focuses on Strategic systems [policy, audit, compliance] |
| Automation | SSO, Authentication, and User Provisioning | Access reviews, policy enforcement, and deprovisioning |
| Tools | Okta, Azure AD, OneLogin | SailPoint, Saviynt, Oracle Identity Governance |
| Objective | To secure access for users and apps across platforms | To ensure access is appropriate, auditable, and policy-driven |
Governance and Compliance
Identity Governance is the fundamental layer that enforces security policies, ensures compliance, and reduces the risk of access misuse. While IAM systems control access, they fail to answer critical questions due to a lack of visibility and oversight.
Questions like:
- Why does this user have access?
- Who approved it?
- Is it still needed?
IGA solutions fill this gap by enabling:
- Access certifications to validate entitlements
- Segregation of Duties (SoD) policies to avoid conflicts of interest
- Audit records for every approval, request, or change
For industries like Finance, Healthcare, and SaaS, where compliance is non-negotiable, this governance is crucial.
Risk Management and Audit Readiness
IGA sets your organization up to prove that all access given is compliant and appropriate, while IAM protects this said access.
IGA strengthens risk posture by:
- Spotting over-provisioned accounts
- Flagging orphaned or dormant identities
- Automating risk scoring based on access sensitivity
- Offering detailed audit logs for regulators and internal audits
IGA makes certain that identity-related risks are well-documented, monitored, and remediated, whether it’s SOX, HIPAA, GDPR, or any internal governance frameworks.
Lifecycle vs. Policy-Driven Access Control
IAM takes care of the identity lifecycle by provisioning and deprovisioning users, enabling login access, and streamlining the workflow. But IGA governs access throughout that lifecycle with the right context and control.
IAM handles:
- Onboarding users and enabling SSO
- Setting basic access permissions
- Disabling accounts on offboarding
IGA adds:
- Policy-based provisioning (e.g., only finance users get ERP access)
- Periodic reviews of access
- Automated revocation if policy conditions change
They ensure that access is granted immediately, but only when it’s suitable and only for as long as it’s required.
Why You Need Both IAM and IGA
Unlike what most people think, IAM and IGA are not interchangeable. They solve very different problems, and depending on either of them can leave critical gaps in your identity security posture.
IGA and IAM are two halves of a comprehensive identity security strategy. Without IAM, everyday operations would come to a stop, resulting in a loss of productivity and serious security risks. While IAM can ensure that users can access the right systems, it doesn’t validate why they should do so.
That’s where IGA steps in. It builds structure and keeps IAM in check by enforcing access policies, setting up periodic reviews, and ensuring segregation of duties. Together, they create a resilient and responsive identity fabric.
For Example:
In a hospital, a nurse can securely log in to check patient records using their credentials with IAM. Here, IGA steps in as access alone is not enough and enforces contextual access. What does that mean?
- Nurses can view records of patients assigned to them and no one else
- This access is only limited to during their shift
- Any changes in their role are automatically updated by deprovisioning workflows
This ensures the hospital is compliant with HIPAA and doesn’t risk sensitive health data. Regulations like GDPR, SOX, HIPAA, ISO 27001 require access to be justified, reviewed, and auditable. These demands can’t be fulfilled by IAM alone without IGA’s built-in controls such as policy enforcements, access certifications, and audit reporting.
Use Cases: IAM vs IGA in Action
Across industries, both IAM and IGA play fundamental but very different roles in solving identity-related challenges. Here’s how they show up in the real world:
-
Finance:
IAM enforces multi-factor authentication (MFA) for employees to access banking systems and internal resources.
IGA implements Segregation of Duties (SoD) to ensure no one user can initiate and approve the same financial transaction, curbing fraud risk and enabling SOX compliance. -
Healthcare:
IAM ensures only authorized personnel can log into Electronic Medical Records (EMR) and access sensitive patient data.
IGA automates these access reviews for HIPAA compliance, ensuring this access is maintained only for as long as it is required. -
SaaS Companies:
IAM automates user provisioning and SSO, speeding up the onboarding process and granting access to necessary internal tools.
With IGA, the company has visibility into license sprawl and any unused access. This ensures proper deprovisioning when employees resign or change roles.
What do these use cases reinforce?
A very simple truth is that IAM enables access, and IGA governs it. Together, they create a secure, compliant, and efficient identity environment regardless of the industry.
Best Practices for Implementing IAM & IGA Together
Integrating IAM and IGA ensures scalable, secure, and compliant identity management systems. Here’s how you can implement them to get the most out of your security systems:
Define roles & policies precisely
Begin the process with clarity. Define the user roles based on their function and not titles. Use Role-Based Access Control (RBAC) to map out what each role should access. This ensures a strong foundation for IAM provisioning and IGA governance to be implemented.
Automate JIT (Just-in-Time) access and deprovisioning
JIT provisioning guarantees users only get access when they need it and only for as long as it is required. Organizations should, as a principle, avoid standing access wherever possible. This reduces the risk of orphaned accounts as automated deprovisioning kicks in to remove access when it is no longer needed.
Conduct regular user access reviews
Establish periodic access certifications. They can be monthly or quarterly, based on the sensitivity of the systems. Your IGA platform can track the approvals, automate the review process, and maintain clean audit trails.
Enforce least privilege
Users should only be given the minimum level of access required to perform their roles and nothing more. This significantly reduces the risk in case credentials are compromised and also helps avoid unintentional misuse of sensitive data. Enforce Zero Trust architecture using IAM and IGA.
Enable continuous compliance monitoring
Make use of IGA tools to consistently audit whether the access policies are being followed. These tools can automate policy checks, spot violations, and generate real-time reports, ensuring you are always audit-ready.
Common Pitfalls to Avoid
Even with all the right tools, your systems can fall short if some key steps are missed. Avoid these implementation mistakes that weaken your IAM-IGA architecture.
Treating IAM and IGA as interchangeable
IAM and IGA are distinct and solve very different problems. Using only one of them creates gaps and can jeopardize your security. IAM gives and enforces access, while IGA grants visibility into access and verifies if it is compliant, appropriate, and necessary.
Skipping access review cycles
Skipping certifications can cause privilege creep and compliance violations. Set up access reviews by automating periodic reviews through IGA and tie them to policy enforcement in real-time.
Over-permissioning users
Don’t give standing access to users “just in case”. It might seem convenient, but it increases the possibility of security breaches. It is also one of the most common audit failures. Ensure least privilege access at all times and use RBAC or JIT models.
Poor integration with HR systems
If your IAM and IGA systems are not integrated with HRMS or ERP, it can cause your identity lifecycle management to break down. Users will end up retaining access even after role changes or termination. Ensure real-time provisioning and deprovisioning by using SCIM or API to integrate your IAM/IGA stack with HR systems.
Ignoring governance in cloud environments
Adoption of cloud environments is on the rise with hybrid and remote workforces. They usually bypass traditional access governance systems. To ensure policy-based oversight across platforms, you can extend IGA to your cloud and DevOps environments using CIEM (Cloud Infrastructure Entitlement Management)
Choosing the Right IGA and IAM Tools
Not every IGA and IAM platform is made equal. You need to decide what is best for your organization based on how well it can integrate with the tools you use, your scalability, and compliance regulations. You need to look beyond the feature checklists to make the right choice.
So, how can you evaluate your needs?
Start with asking the right questions:
- Does it support SCIM or API-based provisioning for cloud and SaaS tools?
- How well does it integrate with our HR system or source of truth?
- Can it handle complex roles, entitlements, and SoD policies?
- What kind of audit logs, certifications, and reporting features does it offer?
- Does it support both on-prem and cloud workloads or only one?
- How quickly can we deploy, and how much customization is needed?
The right questions can help you dig into how a platform can fit into your existing ecosystem and future requirements.
On-prem vs. cloud-based IAM/IGA
On-prem tools often require longer implementation timelines and more IT overhead. They make sense if your organization belongs to a highly regulated industry with strict data residency and control requirements.
Cloud-based solutions are better suited for integrating with SaaS environments. They are faster to deploy, easier to maintain, and ideal for hybrid or remote teams.
Role of APIs and SCIM in tool compatibility
Scalable identity management today relies on open standards. Look for tools that support:
- SCIM (System for Cross-domain Identity Management) for automated user provisioning across SaaS apps.
- Robust REST APIs for custom integrations, workflows, and reporting.
- Out-of-the-box connectors for critical systems like Okta, Azure AD, ServiceNow, Salesforce, and your HRIS.
The more interoperable your IAM and IGA tools are, the smoother your identity architecture will scale across departments, clouds, and apps.
The Future of IAM & IGA in the Age of Zero Trust & AI
Digital ecosystems are becoming increasingly complex, and the traditional perimeter-based security model no longer cuts it. IAM and IGA are the foundation of Zero Trust architectures, where access is always verified and never assumed. Now with AI, automation, and cloud-native innovations shaping the future of identity security, here’s what you need to watch out for:
Role of AI in identity governance:
AI and ML have become key in managing identity at scale. Why? Because manually reviewing access and enforcing policy is no longer viable.
- Behavioural analytics detects inconsistent access patterns
- AI-driven recommendations can spot nonessential privileges or propose role changes
- Risk scoring enables real-time contextual access decisions
This enforces proactive governance, preventing risky access before it becomes a breach.
Cloud native identity stacks:
Cloud native identity platforms that are API-first, scalable across hybrid / multi-cloud environments, and built for decentralized workforces are being favoured against legacy IAM / IGA tools. As these modern stacks integrate seamlessly with DevOps pipelines, SaaS apps, and CI / CD workflows, they make identity security a dynamic part of your infrastructure.
CIEM (Cloud Infrastructure Entitlement Management)
Cloud Infrastructure Entitlement Management fills an essential gap in identity security. It governs access to cloud platforms such as Azure, AWS, where traditional IGA tools are inadequate. CIEM helps:
- Discover dormant or excessive entitlements
- Visualize access paths across cloud accounts
- Enforce least privilege at the infrastructure level
This has become requisite as cloud environments are growing faster than most IGA policies can keep up.
Contextual access and continuous authentication
Going ahead, access will be constantly evaluated and not just granted at login. Access will be based on real-time signals like:
- Location and device health
- Recent behaviour patterns
- Session anomalies
This allows for higher security for remote teams and high-risk roles without compromising usability.
Final Thoughts
The theory is simple: IAM controls access, and IGA governs it. But in practice, they form the backbone of a strong and scalable identity strategy.
Identity security is not limited to controlling access but extends to governing it with accountability, precision, and the right foresight. But in today's threat landscape, one without either is simply not enough. As attacks grow more and more sophisticated, your identity stack needs to do more and do it smartly.
At Tech Prescient, we make organizations like yours resilient, secure, and ready to scale with our systems that are powered by automation and built for Zero Trust environments.
Ready to see how it works?
Frequently Asked Questions (FAQs)
Q: Can IAM and IGA be integrated into a single platform?
A: Yes, absolutely. Modern identity platforms, like Tech Prescient’s can seamlessly integrate IAM and IGA with your ecosystem, reducing complexity.Q: What’s the role of SCIM and APIs in Identity Management?
A: SCIM (System for Cross-Domain Identity Management) and REST APIs automate provisioning and deprovisioning. They also integrate with SaaS apps and HR systems, which is key to scalable IAM and IGA implementation.Q: Can access control systems work without IGA?
A: Technically, they can work without IGA. But without IGA, the access control systems lack the governance layer required for policy enforcement, compliance tracking, and audit readiness.Q: How does IAM work with HR systems?
A: IAM systems sync with HR data to control provisioning and deprovisioning when users are onboarded or removed. This requires SCIM support for complete lifecycle management.