
What Is Access Certification in Identity Governance & Why It Matters?

Access certification is a security practice that entails periodically reviewing and validating user access rights to ensure they are in line with organizational policies and business requirements. It serves as a vital element of Identity and Access Management (IAM), helping to prevent unauthorized access, lower the risk of data breaches, and ensure adherence to regulatory standards. Thus, helping organizations improve their network security, protect sensitive data, and meet regulations like SOC 2. It is a key part of good management that prevents unauthorized access to the systems and keeps operations running smoothly.
In a modern zero-trust environment, with increasing insider threats and strict compliance rules, access certification has moved from being just a good practice to a business necessity. In fact, by 2026, it’s projected that half of all cloud security failures will stem from inadequate identity, access, and privilege management, which highlights the need to regularly check internal access. If you are a compliance officer, IT leader, or business stakeholder, being able to check that only the right people have the right access and at the right time is crucial not just for security but also for business accountability.
Key Takeaways:
- Access certification helps stop unauthorized access by reviewing user permissions regularly.
- It supports compliance with laws like SOX, HIPAA, and GDPR through scheduled access reviews.
- Automation reduces manual work and helps avoid reviewer fatigue.
- It enforces Zero Trust and PoLP by checking and updating access as needed.
What Is Access Certification?
Access certification is a process within an organization's security protocols that verifies and validates user access rights and permissions across business systems and applications.
It involves methodically reviewing and validating that individuals have the correct access to resources in accordance with their roles and responsibilities within the organization. This process plays a critical role in maintaining the security, integrity, and compliance of an organization's data and IT systems.
Access certification focuses on the following key areas:
- Access Review: Access certification entails examining the permissions assigned to users to verify that they correspond with their roles and responsibilities within the organization. This helps safeguard systems by preventing unauthorized access and lowering the chances of data breaches.
- Permission Validation: It ensures that users hold only the necessary permissions to carry out their responsibilities effectively, without becoming overprivileged. It helps strike the right balance between maintaining strong security controls and enabling workplace productivity.
- Issue Detection and Remediation: The access certification process often reveals discrepancies or inconsistencies in how access rights are managed. Common issues include inappropriate access, orphaned accounts, and users with excessive privileges. Addressing these problems promptly is critical to ensuring a secure and well-governed IT environment.
- Stakeholder Participation: Key stakeholders such as application owners, managers, and compliance officers play an essential role in the access certification process. They are responsible for reviewing and approving access rights based on their understanding of user roles and the organization's security policies.
- Compliance Assurance: Access certification plays a critical role in meeting regulatory requirements and upholding industry standards for data security and privacy. Through regular validation of access rights, organizations can effectively demonstrate compliance during audits and assessments.
Why Access Certification Matters in 2025?
With the advent of hybrid work culture, an increase in the use of cloud-based tools, and strict regulatory practices, access certification has become a must-have strategy in 2025. Leading IGA platforms now offer access certification as a solution to help organizations automate access control, reduce manual effort, and maintain compliance. As the risks from insider threats increase and audits get harder, not validating access controls regularly can lead to privilege creep, orphaned accounts, and penalties for breaking the rules.
- Responding to Zero Trust Demands
Zero Trust architecture is based on the principle that threats can emerge from both within and outside the network. It mandates ongoing verification of access rather than relying on one-time approvals. Access certification reinforces this approach by facilitating periodic and on-demand entitlement reviews, enabling the detection and removal of unauthorized or excessive access before it leads to potential security risks. - Enforcing Least Privilege at Scale
It is almost impossible to manage the principle of least privilege manually for a large number of users. Access certification platforms automate the process by routinely reviewing user access rights, confirming their necessity, and initiating revocation workflows when appropriate, ensuring that least privilege is consistently enforced and maintained across the organization. - Avoiding Audit Penalties
Regulatory compliance frameworks such as SOX, HIPAA, GDPR, and ISO 27001, along with recently introduced regulations like NIS2 and DORA, mandate continuous, periodic, and well-documented access reviews. Access certification plays a critical role in meeting these requirements by providing the necessary evidence during security audits. Failure to implement these controls can expose organizations to substantial financial penalties and reputational damage.
“Access reviews ensure the right people have the right access, nothing more, nothing less. It’s the foundation of trust and compliance.”
— Tech Prescient IAM Consultant
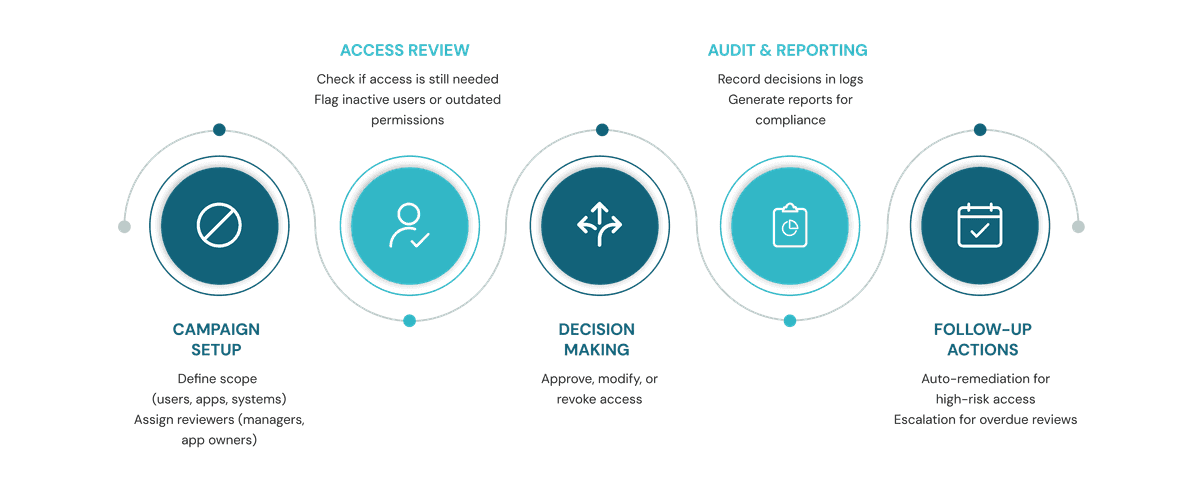
Core Elements of the Access Certification Process
A strong access certification strategy involves regular and well-organized review campaigns which has clear roles, defined review areas, and reports ready for the audits. These steps are crucial for timely reviews, which are useful for spotting risks and supporting compliance. Modern IGA platforms make this process easier by using automation, real-time monitoring, and alerts to manage the process smoothly.
1. Campaign Setup & Reviewer Roles
Effective access certification within an IGA platform depends on a structured campaign setup and the clear assignment of reviewer roles. The process begins by defining the campaign scope, identifying the specific users, entitlements, or applications that require review during a given cycle. Reviewers such as direct managers, application owners, or compliance officers are assigned based on their familiarity with and responsibility for the access in question.
These campaigns typically incorporate defined deadlines, automated reminders, escalation workflows for overdue tasks, and configurable review logic (such as direct certification, deny, or delegation). Modern IGA solutions enhance this process by automating campaign orchestration, enabling real-time progress tracking and reporting. This significantly reduces manual workload while ensuring timely, auditable reviews that support both regulatory compliance and risk mitigation.
2. Access Reviews & Recertification
Access reviews are a core component of identity governance, involving the systematic verification of users' existing permissions to confirm that access entitlements remain valid and are necessary for their current job functions. These reviews can be conducted on a periodic basis (e.g., quarterly or semi-annually) or initiated in response to contextual risk factors, such as access to sensitive systems, high-risk roles, or specific regulatory requirements. Well-executed review processes help uncover and remediate issues like inactive users, orphaned accounts, and permissions that are excessive or fall outside established policy.
Access recertification expands on access reviews by formally requiring designated reviewers, such as managers, application owners, or data stewards, to attest that users’ assigned permissions are appropriate for their current responsibilities. Recertification becomes particularly important following organizational changes like team transfers, promotions, or new project assignments, helping to prevent privilege creep and uphold least-privilege access models.
3. Audit & Compliance Logs
Keeping regular audit trails is important for meeting regulatory standards like SOX, GDPR, HIPAA, and ISO 27001. Access certification platforms create logs that record each and every review, approval, rejection, or removal across all campaigns. These logs are important for showing accountability during audits to avoid last-minute stress. Dashboards and reports also give auditors a centralized view of past certifications, any issues, and overall trends.
Key Technologies: IGA Tools for Certification
Modern access certifications rely on advanced IGA platforms like TechPrescient offering automation, smart workflows, and scalability. In today’s hybrid setup, businesses need secure and compliant solutions, not spreadsheets.
Here's what a mature IGA platform delivers:
- Automated Workflows & Scheduled Campaigns
IGA tools streamline the access review process by automating the scheduling of regular campaigns to evaluate user access rights and certifications. This minimizes manual effort while ensuring timely reviews, thereby enhancing both compliance and the organization’s security posture. - RBAC Enforcement
Role-Based Access Control (RBAC) is a fundamental element of IGA. It ensures that users are granted access only to the resources necessary for their defined roles within the organization. This approach helps reduce the risk of over-privileged users and potential security breaches. - SoD Conflict Detection
Segregation of Duties (SoD) is an essential security control designed to prevent fraud and human error. IGA tools help by analyzing user access rights to detect potential conflicts, situations where a single user holds conflicting permissions that could result in malicious actions or accidental errors. - Real-Time Alerts & Auto-Remediation
IGA tools provide continuous monitoring of user access and system activity. When potential security threats or policy violations are detected, such as an SoD conflict or unauthorized access, the system can generate alerts and automatically initiate remediation actions, like revoking access or modifying permissions.
Benefits of Effective Access Certification
Effective access certification goes beyond compliance; it strengthens your overall identity security posture and boosts operational efficiency.
Conducting regular, structured certification campaigns within an IGA platform enables organizations to:
- Strengthen Security Posture
By systematically reviewing and removing unnecessary or excessive access rights, organizations can minimize the risk of insider threats, privilege creep, orphaned accounts, and unauthorized entitlements. Early identification and remediation through access attestation enable IT and security teams to mitigate risks before they escalate into security incidents. This leads to stronger security, better compliance, and tighter access control. - Reduced Identity Sprawl
Certification processes help detect and remove dormant accounts and outdated roles, enhancing the accuracy of identity repositories and minimizing the organization’s attack surface. This cleanup is particularly critical following role changes, employee exits, or project completion, where residual access often remains. It ensures a leaner, more secure access environment with reduced exposure to threats. - Enhance Cross-Functional Collaboration and Accountability
Engaging line managers, application owners, compliance officers, and HR in structured certification workflows helps ensure that access reviews are contextually accurate. This distributed attestation enhances accountability, minimizes the risk of oversight, and promotes a culture of shared responsibility in identity governance. It results in more reliable access decisions and stronger overall governance. - Streamline Audit Readiness
Automated certification ensures a defensible audit trail, streamlines the process of gathering evidence for regulatory mandates, and showcases ongoing compliance with standards such as SOX, GDPR, and HIPAA. It simplifies audits and strengthens your organization's regulatory posture.
Best Practices for Access Certification in IGA
Following these best practices can help turn access certification from just a normal task into a strong governance tool. With the right approach, organizations can lower identity risks, make compliance easier, and also make sure that the right people always possess the right access. These strategies can also help build and maintain a strong identity governance system as the business grows.
1. Enforce Least Privilege & RBAC
Always make sure that access is given based on roles and not just requests. Use RBAC to assign access according to each person’s job and keep reviewing it regularly. Following the principle of least privilege means users can only get the access they truly need. Comparing access to role definitions regularly can help reduce over-privileged accounts and strengthen access control. RBAC also makes certification easier by standardizing permissions around clear job roles.
2. Collaborate With Line-of-Business Managers
Business managers are often the best people to know if a user still needs access. Involving application owners and department heads makes access decisions more accurate. These managers understand the daily work needs and can spot outdated and risky access that IT might overlook. Thus, working together on reviews builds stronger accountability across the organization.
3. Automate With AI-Driven Tools
Use machine learning to detect any unusual access, like excessive permissions or strange access patterns, and get smart suggestions during reviews. AI-powered IGA platforms can study access behavior, detect abnormal activity from baseline, and suggest fixes. This will help reduce the burden on reviewers and speed up the decisions, especially in large companies with thousands of users and roles to monitor.
4. Monitor Continuously & Audit Often
Do not treat certification as something you do once every few months. Continuous access monitoring can help catch issues faster and improve visibility. Monitoring access activity in real time makes it easier to spot problems between review cycles. It also helps organizations quickly respond to role changes, during offboarding, or policy violations, making audits easy and more effective.
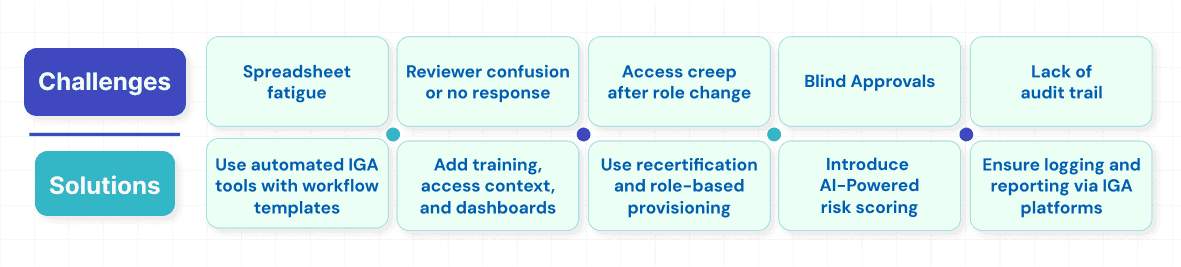
Common Challenges and How to Overcome Them
Access certification is the key in modern identity governance, but it often faces challenges that can impact its effectiveness. Several issues, including process fatigue and unclear roles, can weaken your security if not handled properly.
Let us look at the most common problems in access certification and how to fix them.
- Manual fatigue from spreadsheet-based reviews
Using spreadsheets and emails for access reviews is not only a slow process but also a risky one. Reviewers can get tired of the repetitive work, which will increase the chance of blind approval of access or missing out on something important. To address this, organizations should implement automated access certification processes that enable faster, more accurate reviews, minimizing errors while keeping reviewers engaged and accountable. - Reviewer inaction or confusion
Access reviews are often given to managers or application owners who may not have enough context to make the right decisions, or worse, sometimes do not respond at all. This causes delays and also incomplete reviews. Providing clear training with easy-to-understand dashboards and helpful access details (like user roles, their last login, and how often access is used) can help reviewers certify accurately and also on time. - Access creep from role changes
When users switch between departments or take on new responsibilities, their previous access rights and entitlements are often not fully revoked. This buildup of unnecessary permissions is known as “access creep” or “privilege creep.” Over time, it results in over-provisioning, which increases the risk of unauthorized data exposure, policy violations, and non-compliance with regulatory requirements.
To mitigate access creep, organizations should implement automated, role-based access provisioning (e.g., RBAC), which grants permissions strictly based on users’ current job roles. In addition, conducting regular access recertification or attestation campaigns ensures that access rights are periodically reviewed and updated to reflect personnel and organizational changes. These practices support the principle of least privilege and help proactively reduce compliance and security risks caused by excessive or outdated access.
Access Certification vs. Access Recertification
The terms access certification and access recertification serve different purposes in identity governance and are often confused. Even if both ensure that users have the right access and at the right time, they vary in timing, frequency, and purpose. Knowing when to use which one can help organizations stay compliant, lower the risks, and enforce the principle of least privilege, without adding extra manual work.
Quick Comparison: Certification vs. Recertification
| Criteria | Access Certification | Access Recertification |
|---|---|---|
| Goal | The goal is to grant and validate appropriate access when a user is onboarded or assumes a new role. | The goal is to periodically revalidate existing access to ensure it is still appropriate and necessary. |
| Frequency | It is typically performed during onboarding, system rollout, or when new access is requested. | It is conducted on a regular schedule, such as quarterly or biannually, depending on policy. |
| Focus | The focus is on ensuring that users receive only the access they need from the start. | The focus is on reviewing whether users still require the access they were previously granted. |
| Trigger | It is triggered by events like new hires, implementation of new tools, or organizational changes such as mergers. | It is triggered by scheduled review cycles or compliance-driven requirements. |
| Output | The result is access that is approved based on the user’s role and current business needs. | The result is a decision to retain or revoke access based on whether it aligns with the user’s current responsibilities. |
Use Case Examples:
- Onboarding a New Employee (Access Certification)
When new employees join an organization, they need the right access and tools to do their job. Access certification makes sure that their initial access matches their job title and fits their duties and also that it is approved by the right people, which helps enforce the principle of least privilege from day one. - Quarterly Review for Existing Users (Access Recertification)
To stay compliant and also to avoid any privilege creep, organizations perform access recertification every quarter. Managers and system owners validate if users still need their current access or if it should be changed or removed due to role changes or inactivity.
What Our IGA Expert Suggests
“Certification is essential to scalable, secure access control in any modern IGA strategy. Without it, you're blind to who can do what inside your organization.”
— Tech Prescient Identity Architect
At Tech Prescient, we believe that access certification is not just a compliance task but also a key to strong identity governance. In today’s hybrid work culture and cloud-based world, managing access at a large scale needs more than just manual spreadsheets and outdated tools. It requires certification, processes that are not only automated but also smart, trackable, and flexible to fit your business. If done right, access certification gives IT and security teams the visibility and control they need to reduce risks, pass audits, and support Zero Trust. It is not just about technology but also a security-first culture where every access decision is clear, justified, and viewed regularly.
Final Thoughts
Access certification is not just about checking boxes, but it is also about building a security-first culture, which protects what matters the most. When done right, access certification can reduce risks, make compliance easier, and improve collaboration between IT, HR, and different business teams. If you are ready to move past spreadsheets and manual reviews, it is time you explored a smarter approach.
Let Tech Precient help you automate, improve, and scale your access certification process with confidence.
Frequently Asked Questions (FAQs)
1. What is access certification, and why is it important?
Access certification is the process of regularly checking who has access to systems and data. It ensures that only the right users keep the right access, helping reduce risks and avoid data breaches. It’s crucial for both security and compliance.2. How often should access certifications be done?
Access certifications are typically done every quarter, six months, or yearly, depending on risk and industry rules. Frequent reviews help catch issues early. The right timing ensures better control and compliance.3. What tools support automated access certification?
IGA platforms like SailPoint, Saviynt, and Tech Prescient automate access certification. They reduce manual work, highlight unusual access, and simplify decision-making. These tools make reviews faster, accurate, and audit-ready.4. Is access certification required for compliance?
Yes, laws like SOX, HIPAA, and GDPR require regular access reviews. Certification proves your organization controls access properly. It supports audit readiness and helps avoid compliance penalties.5. How does access certification fit into Identity Governance?
Access certification is a key part of Identity Governance, helping ensure access is correct and updated. It supports security models like Zero Trust and least privilege. It also improves visibility and accountability across the organization.