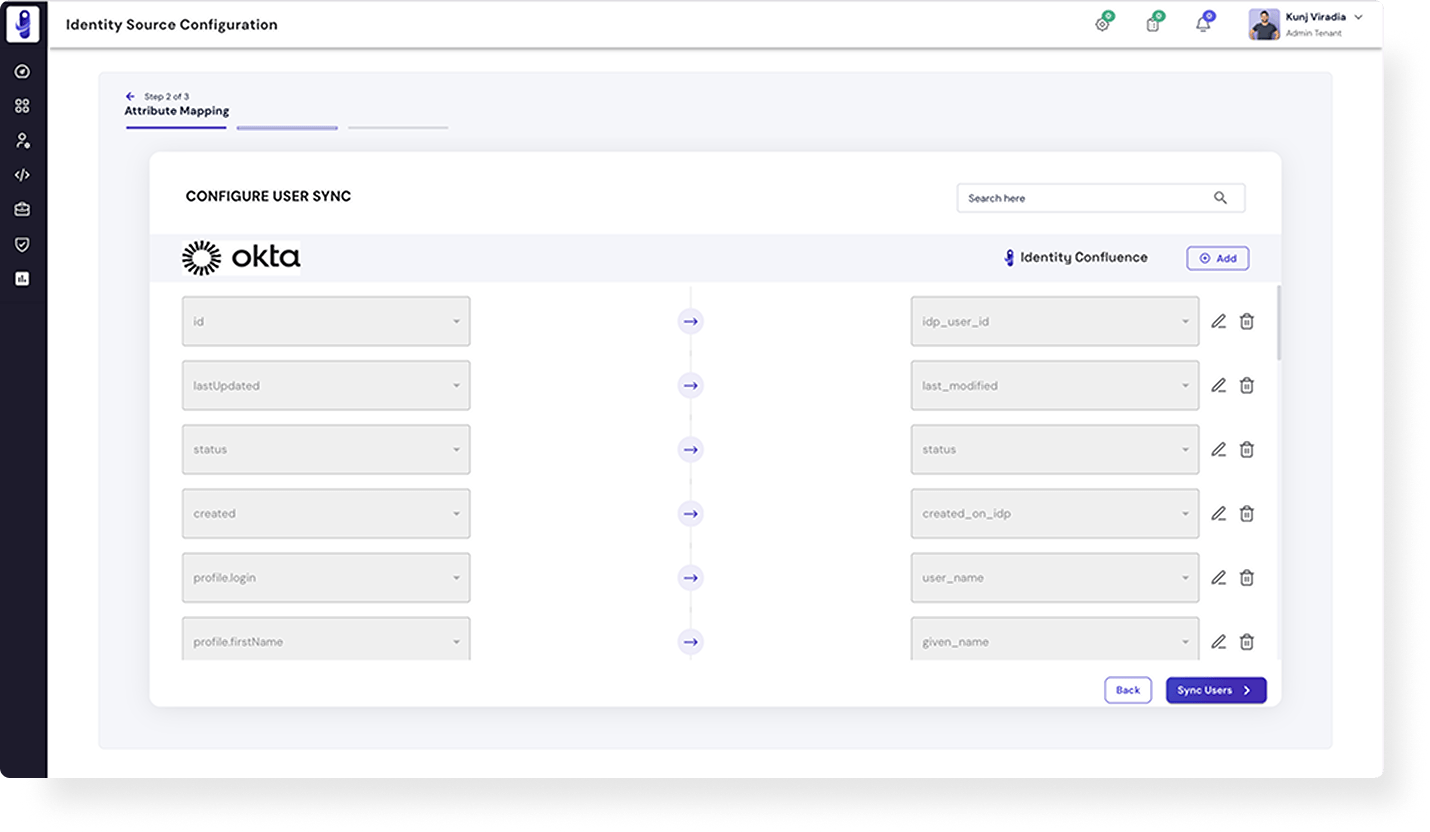
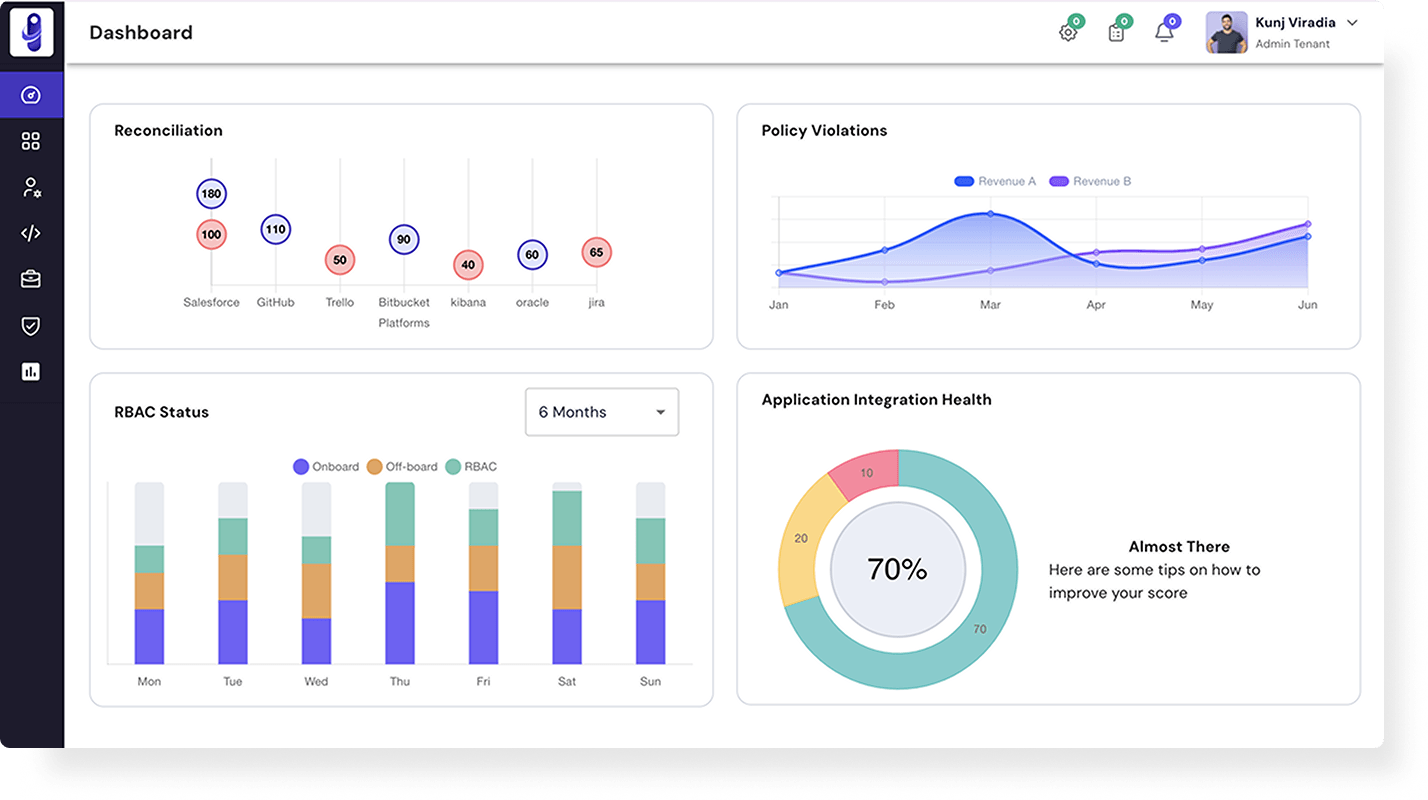
Intelligent Identity & Access Management
Simplify, manage and secure identities and access to business critical applications through a single pane of
glass for every enterprise.
glass for every enterprise.
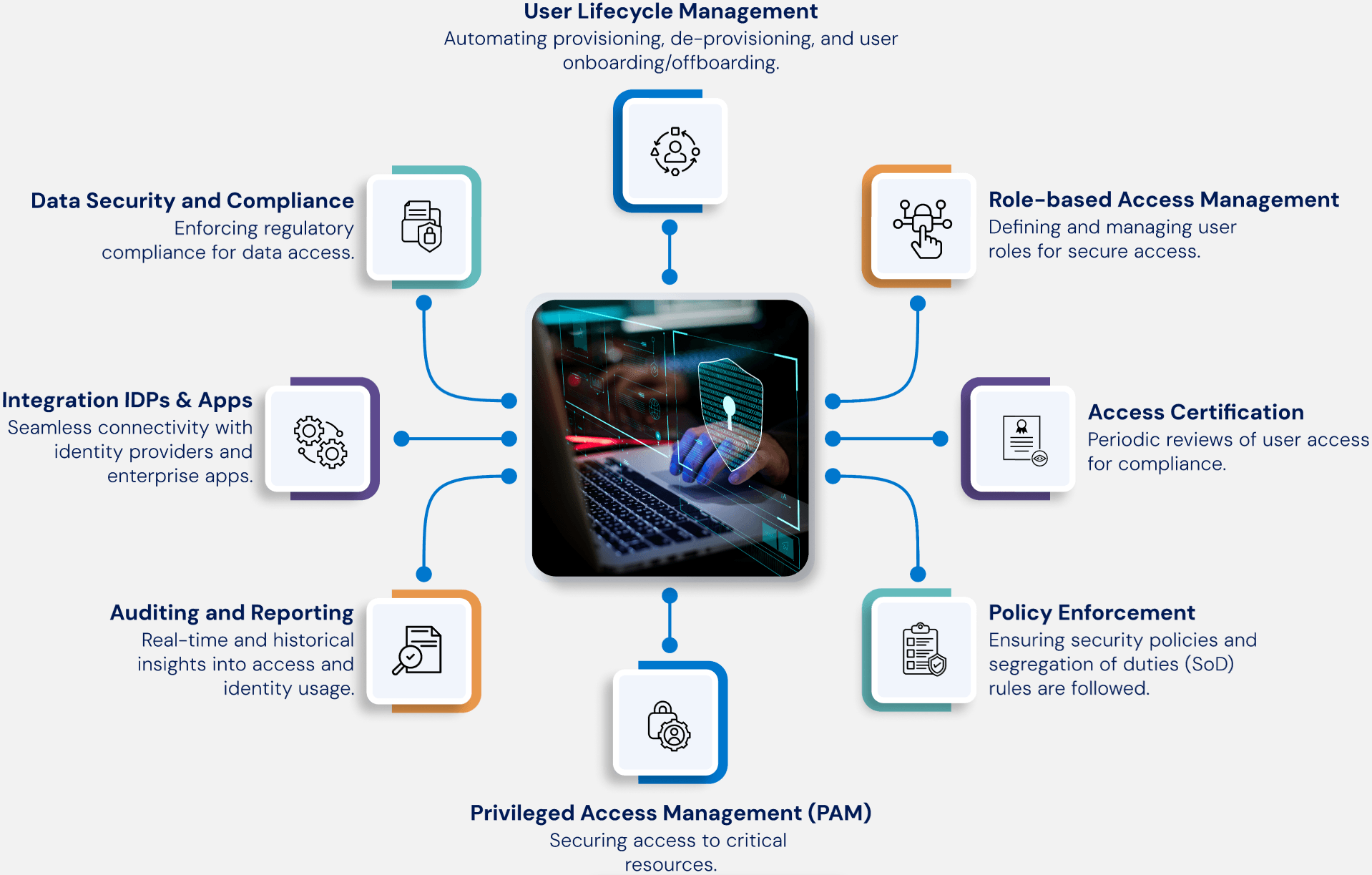

Why Choose Identity Confluence?
Identity Confluence helps enterprises Optimize identity management with governance,
compliance, and automation.
compliance, and automation.
VALUE PROPOSITION
Simplify Compliance
Automatically meet regulatory requirements like GDPR and HIPAA.
Ensure Security
Protect user data with real-time monitoring and threat detection.
Boost Efficiency
Automate user access provisioning and deprovisioning at scale.
Reduce Risk
Implement role-based policies to prevent privilege misuse.
Achieve Scalability
Integrate seamlessly with your existing systems.
Improve Visibility
Track user activity with customizable reporting and analytics.
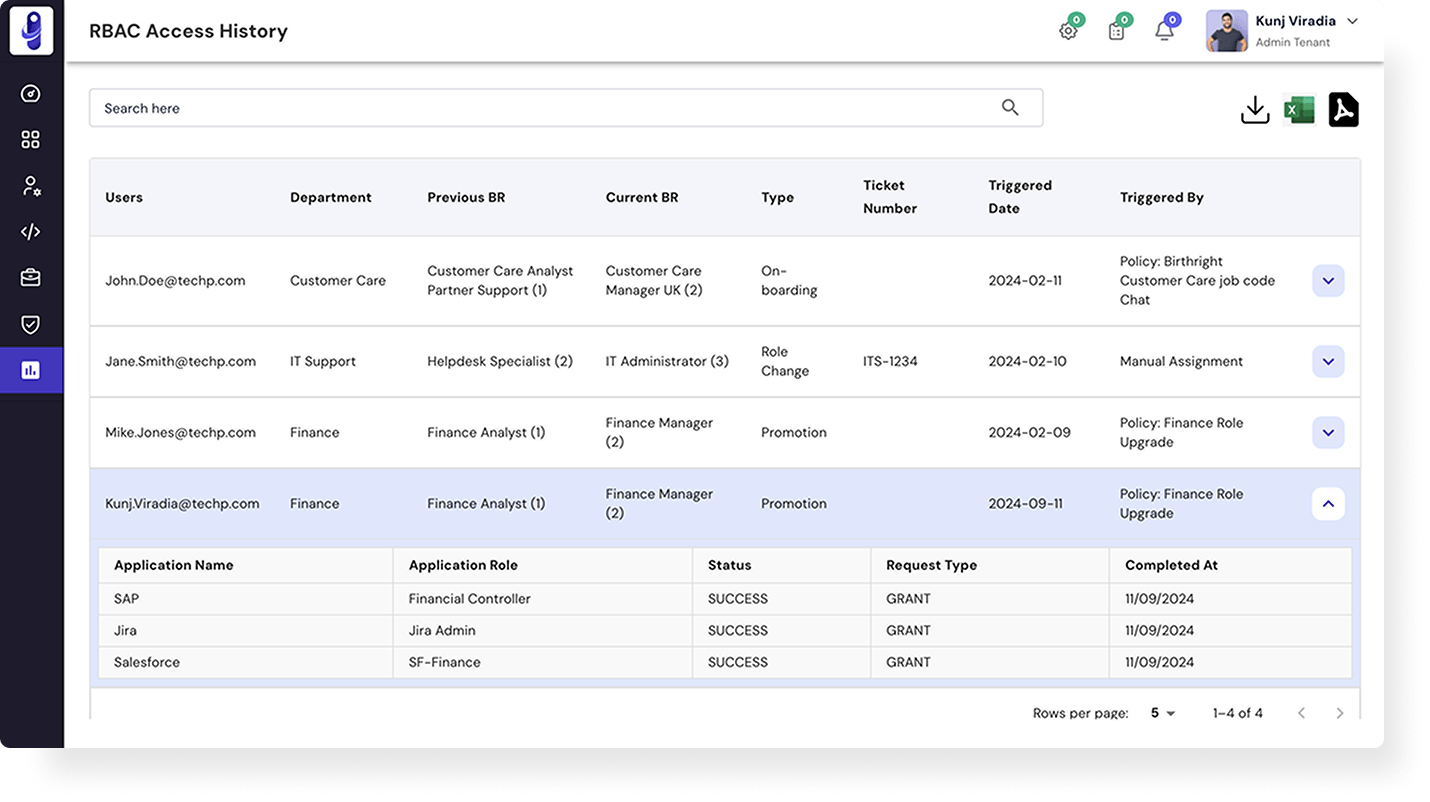
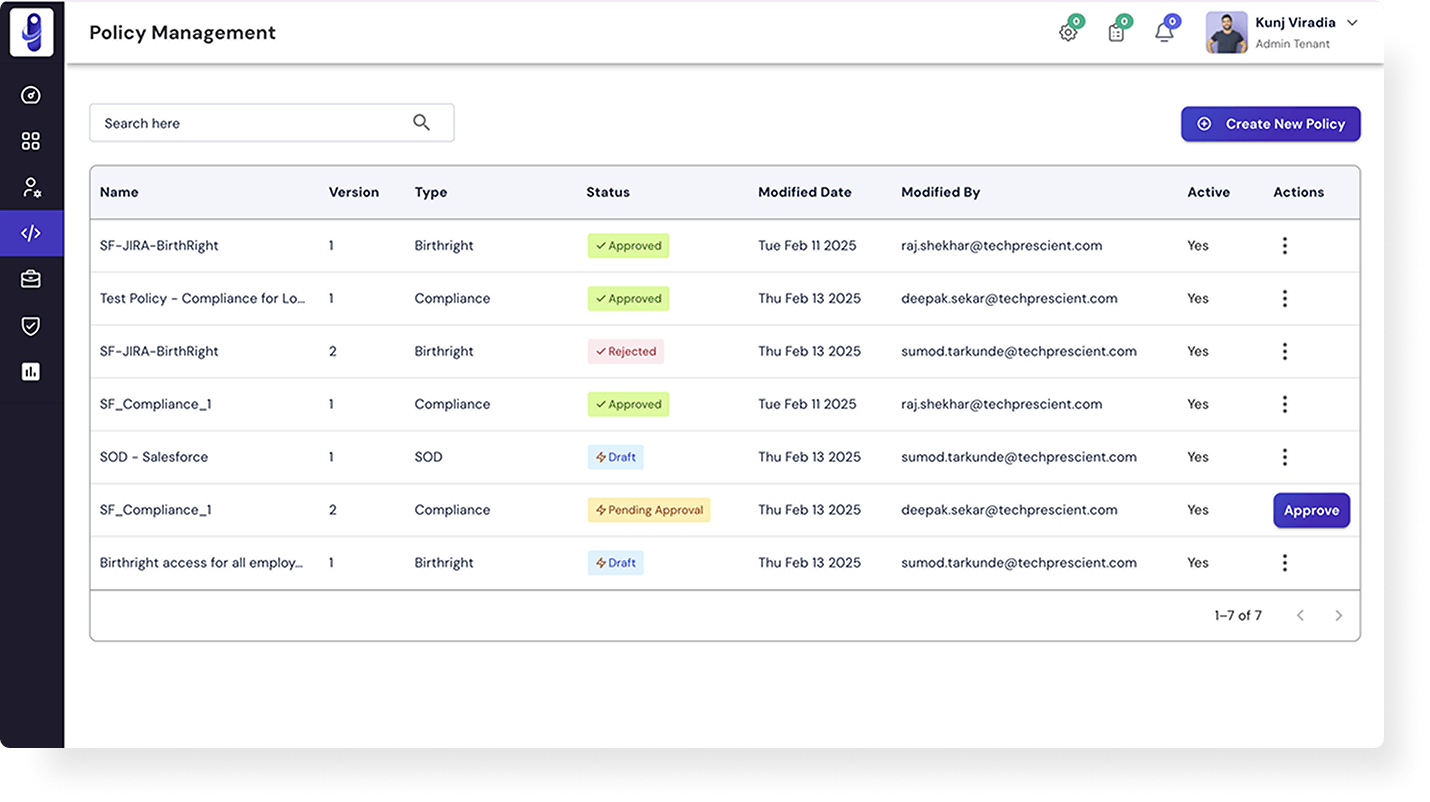
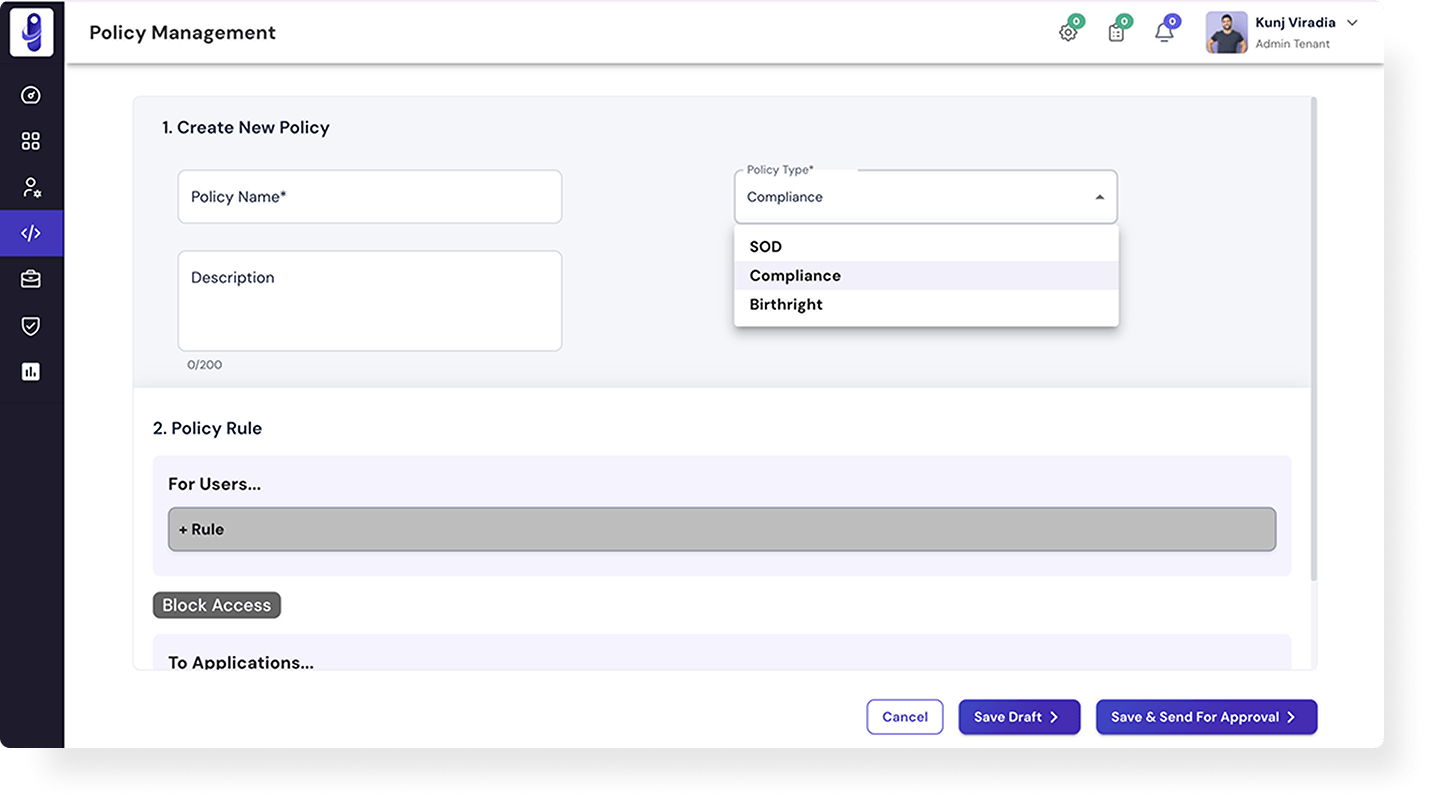
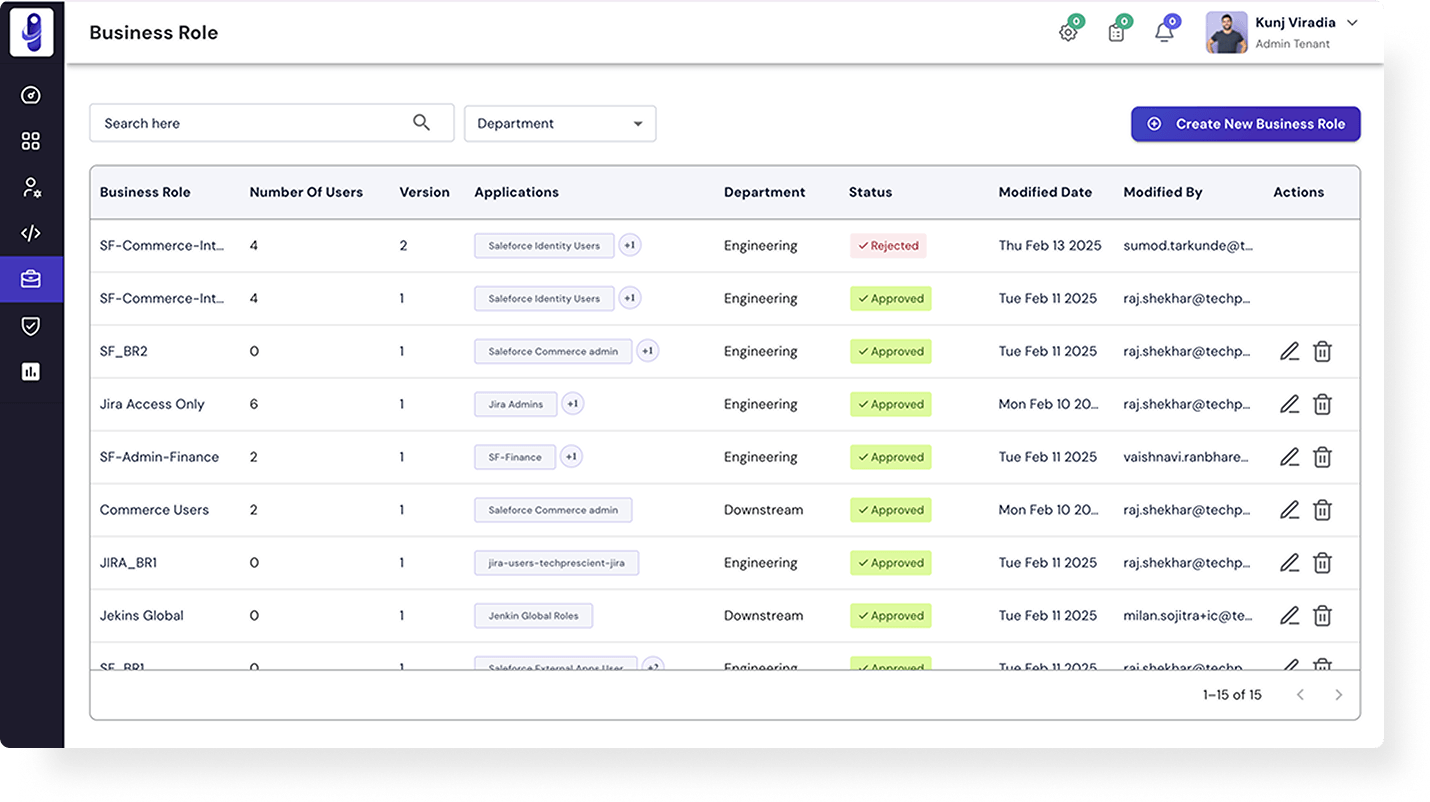
Use Cases and Benefits
An IGA platform that truly ensures compliance across enterprise systems.
Powering breakthrough success
Our customers are innovating faster and achieving accelerated outcomes while still reducing their cost.