Identity Orchestration: The Future of Secure, Scalable IAM

Identity orchestration is the control layer that connects and coordinates all your identity systems across cloud, on‑prem, and hybrid environments from a single point of control. It decouples identity logic from individual applications so you can define policies once and enforce them everywhere without custom code or fragile integrations.
Identity today is dynamic, distributed, and spans dozens (sometimes hundreds) of applications, clouds, and user types. Yet, many organizations still rely on outdated IAM systems that are incapable of handling this complexity.
The result? Access silos. Custom code. Security gaps. And a huge operational burden on IT just to keep things working.
Identity challenges today don’t come from having too few tools, but rather from having too many disconnected ones. You juggle multiple identity providers, cloud platforms, and legacy apps that all speak different languages. Stitching them together is expensive, fragile, and doesn’t scale.
Identity-related breaches are very common. A report from the Identity Defined Security Alliance shows that 90% of organizations faced at least one identity-related incident in the past year; 84% of those organizations said that the incident had a direct business impact, such as company disruption, reputational impact, or financial impact.
That’s where identity orchestration enters the picture. It sits above all of your IAM stack at the service level and organizes/creates order out of the chaos. Instead of hard-coding access flows into each application, you define policies once, and the orchestration layer dynamically enforces those policies securely without custom code.
It’s not meant to replace your current tools. It’s what connects them. And in a world moving toward Zero Trust and hybrid everything, that connection is no longer optional.
Key Takeaways
- Identity orchestration acts as the control layer that unifies identity tools, clouds, and applications.
- It separates identity logic from applications, with no need for custom code or brittle integrations.
- Enables real-time policy enforcement, centralized governance, and secure access flows.
- Critical for hybrid and multi-cloud environments, especially during M&A or IDP transitions.
- Works alongside IAM, SSO, and IDPs. Doesn’t replace them, but makes them work better together.
- Key benefit: flexibility to modernize identity without disrupting existing systems.
What is Identity Orchestration?
Identity orchestration is the control layer that interconnects and orchestrates all your identity infrastructure across clouds, platforms, and applications. Rather than build custom integrations to every system, it enables you to define identity policies in one place and apply them consistently in unison everywhere, without ever having to change application code.
Identity orchestration allows you to define access flows consistently without having to modify code or create custom integrations for every tool and environment. Whether your users authenticate using Okta, Azure AD, or something older, our orchestration will guarantee that users experience the same policies and approach to adapting identity, securely and in real time. This is especially valuable in today’s hybrid and multi-cloud environments, where identity is often fragmented and hard to manage.
Ultimately, it helps you respond to complexity. It integrates cloud and on-prem systems, manages authentication across apps, and offers you a single programmatic way to manage how individuals are granted, verified, and revoked access, while not relying on your teams to manually piece everything together.
Key Functions:
- Unifies identity silos between next-gen modern, cloud, on-premise, and legacy systems.
- Orchestrates authentication and authorization without requiring custom code.
- Integrates flows between cloud, hybrid, and on-premise identity systems.
- Responds in real time to changes in the user, device, or session context.
How Identity Orchestration Works
Identity orchestration platforms operate as a control plane that sits above your identity systems, giving you centralized control and visibility over the full identity journey. You can design and automate flows from user registration to authentication, policy checks, risk signals, and session management. Orchestration allows you to design and automate flows to govern how identities engage with your applications.
Rather than embedding identity rules inside every app, orchestration decouples that logic. You define access policies once, and the orchestrator dynamically enforces those policies in real time, regardless of which cloud, app, or identity provider is involved.
This abstracted layer allows you to deliver secure access experiences that are consistent and seamless without having to rewrite application code or build custom point-to-point integrations. Rather, orchestration quickly streamlines identity in the increasingly complex environments we find ourselves in and in a way that allows for many disparate things to work as one solution, even if they were never designed to be.
Here is how a typical orchestration flow comes together:
- Define your flow objective: Start with what you want the user journey to achieve, for example, onboarding a new employee or logging in with a risk-aware authentication.
- Determine authentication requirements: Determine whether Multi-factor Authentication (MFA) is necessary or biometric or passwordless options, based on the level of sensitivity in the process or the industry (e.g., financial services, healthcare).
- Build the flow: Using a no-code or low-code interface, you actually drag-and-drop nodes that represent the steps you want to take, such as email capture, device check, MFA prompt, etc. Each node is powered by an underlying connection to your identity tools or identity providers.
- Add logic and conditions: Link together the steps using logical operators (e.g., like "if user is external, route to IdP X") so that you can make real-time decisions based on users, the devices they're connecting with, their location, or risk level.
- Test and launch: Test your flow in a sandbox to validate the user experience and security logic before you put it into live production.
Identity Orchestration Platforms: Core Features
Identity orchestration platforms serve as the connective tissue across fragmented IAM environments. They do not replace your IAM tools but bring them together, allowing for unified access management across many system environments, clouds, and user types. Their value is their ability to centralize control without friction or having to rewrite code in your IAM tools.
Have a closer look at the key capabilities that make them so important:
- Integrates with Multiple IdPs (e.g., Okta, Azure AD, Google)
Most modern enterprises do not use only one identity provider. Perhaps you use Okta for workforce, use Azure AD for internal IT, and then Google or legacy LDAP for some specialized apps. The orchestration platform can integrate all of them into one unified control layer and allow consistent policies and access decisions across all IdPs. - No-Code Policy Automation
For traditional IAM, defining access logic usually involves custom scripting or modifying each application. With orchestration platforms, that model is flipped. They have visual or declarative policy builders allowing you to define authentication flows, access rules, and exception handling easily, often without having to write a single line of code. Therefore, it is much quicker to implement policies on an identity orchestration platform and is able to be audited, tested, and modified more quickly as business requirements shift. - Multi-cloud and Hybrid Support
Many of today's identity issues arise from hybrid situations: a cloud-first strategy coexisting with on-prem infrastructure. Identity orchestration platform solutions are built to address this complexity. Orchestration allows consistent access decision-making, regardless of whether you are securing a cloud-native application on AWS or a legacy application in your data center.
Authentication Orchestration Explained
Authentication is no longer simply logging in to allow access to resources. Authentication is now more about making real-time decisions about context, including who the user is, what resource they are accessing, where they are coming from, and is their behavior is as expected. This is where authentication orchestration takes place.
You can think of orchestration as the logic engine for modern access. Because it orchestrates every step in the authentication flow, across devices, identity providers, and risk signals, and enables you to deploy adaptive policies into all your applications without the burden of writing rules in each and every application.
With an orchestration engine, you only define your adaptive policies once, and with respect to real-time information, the orchestration engine decides on whether to allow, request more authentication, or deny access.
Key Capabilities:
- Adaptive MFA and passwordless authentication
Not every login requires the same degree of scrutiny. Authentication orchestration applies just the right level of authentication appropriate to the risk. It can trigger MFA for high-risk access (e.g., accessing sensitive data with an unmanaged device) or allow for passwordless login for low-risk, verified circumstances. - Real-time identity signal processing
Orchestration platforms gather and assess a variety of signals like geolocation, device posture, IP reputation, behavioral anomalies, and session context. All of these signals provide input to an organization's access decision-making on an ongoing basis and not just at the time of login. - Dynamic session and risk management
Authentication does not stop once a user is in. Orchestration enables risk management and access enforcement at run-time. For example, an organization can revoke access to resources if a device becomes non-compliant or unusual behavior is observed mid-session. - Cross-application consistency
Instead of enforcing authentication policies separately in each application or identity provider, orchestration enforces them holistically, giving users a consistent experience and solutions across services, while ensuring that those experiences are secure.
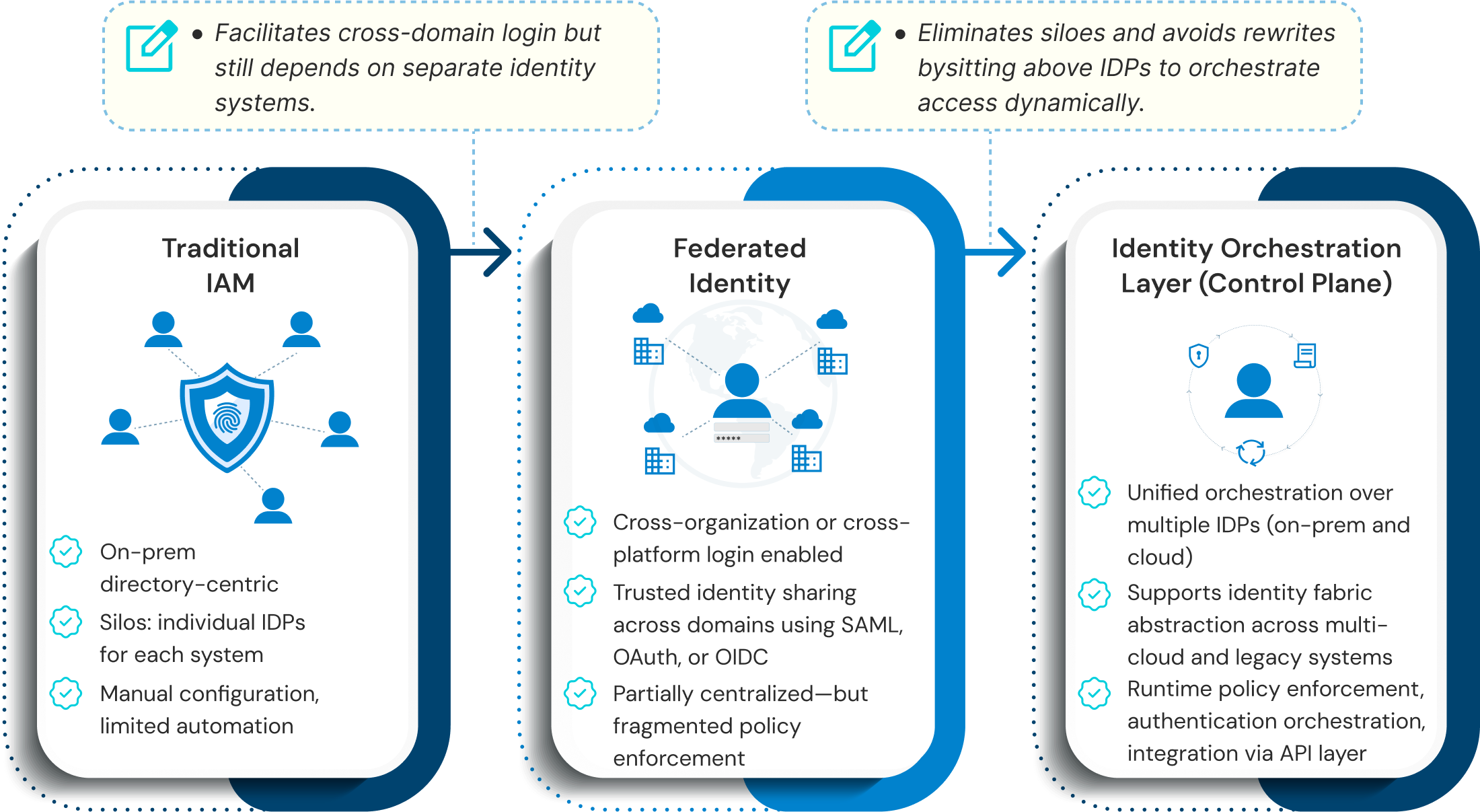
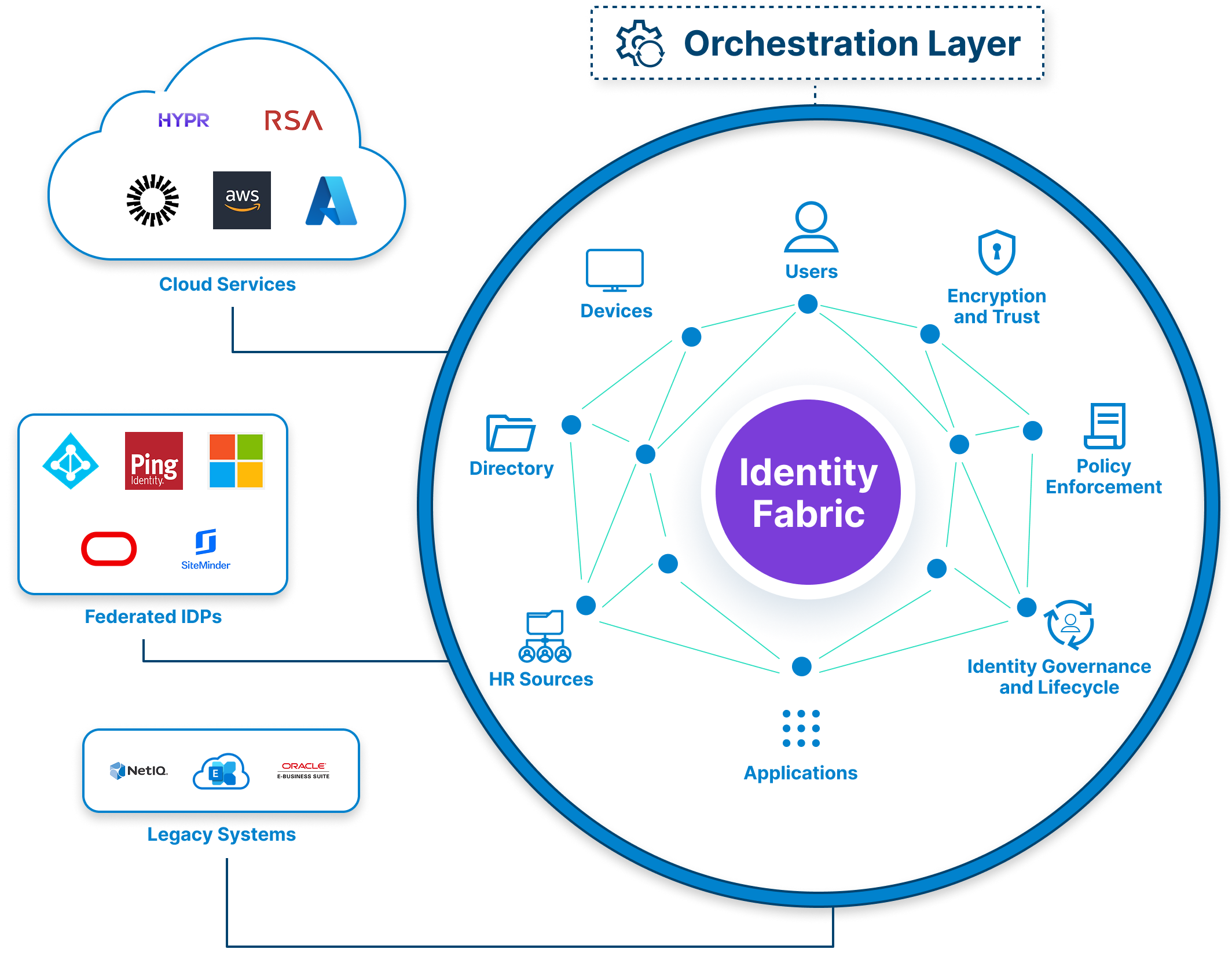
Identity Fabric vs. Identity Orchestration
Identity fabric and identity orchestration are often used synonymously, but still play distinct roles in contemporary IAM architectures.
Identity fabric is an architectural environment that connects and integrates different IAM tools and identity providers, and services within your organization’s IT landscape. You may visualize it as a flexible mesh that connects identity for all users, such as employees and partners, devices, in cloud or on-prem constructs. Identity fabric abstracts complexity and provides the environment for consistent authentication, authorization, and governance.
Identity orchestration, on the other hand, is the operational engine that drives this fabric, which automates identity flows like authentication flows, policy enforcement, access decisions, etc., in real-time. Identity orchestration illustrates how the identities move across the system, and does not require changes to apps or code.
When combined, identity fabric and orchestration allow organizations to have scalable, secure identity capabilities across hybrid, multi-cloud, and legacy environments.
Comparison: Identity Fabric vs. Identity Orchestration vs. Identity Provider
| Feature/Aspect | Identity Fabric | Identity Orchestration | Identity Provider (IdP) |
|---|---|---|---|
| Role | An architectural layer that connects identity tools | Operational layer that automates identity flows | A system that authenticates and manages users |
| Primary Function | Abstracts and unifies identity systems | Automates and coordinates identity workflows | Authenticates and authorizes identities |
| Scope | Cross-cloud, cross-IDP, and multi-domain | Policy execution across all identity systems | Single source of identity (e.g., Azure Active Directory, Okta, Auth0) |
| Custom Code Required? | No (via abstraction and orchestration) | No (uses no-code/low-code orchestration tools) | Sometimes (esp. for integrations) |
| Flexibility | Highly adaptable across environments | Dynamic execution based on real-time context | Often limited to the ecosystem it's built for |
| Key Benefit | Consistent identity architecture | Adaptive access control without hardcoding | Centralized identity management |
How Identity Fabric Works
An identity fabric is the abstraction layer in a distributed identity architecture. Think of it as the connective tissue between all of your identity systems, be it legacy and modern, on-premises and cloud, and how they can work together seamlessly. An identity fabric itself isn't something you buy. It's something you build using identity orchestration to connect and coordinate multiple identity domains, tools, and policies within your ecosystem.
Here’s how it works:
- Integrates separate identity systems
The fabric integrates separate identity silos—now you have one unified identity layer that apps and users interact with instead of MFA tools, directories, cloud IDPs, databases, and legacy authentication systems. - Reduces complexity with one unified API
Rather than writing custom integration logic for every app or cloud environment, developers can just make calls on one abstracted API that talks to all of the identity systems below. Fewer lines of code, reduced access complexity, and faster deployment. - Creates uniform policy enforcement across environments
By maintaining access and authentication paradigms in one layer, developing identity policies (conditional access, risk scoring, session control), and having consistent policy enforcement across SaaS apps, IaaS platforms, and hybrid models becomes natural. - Provides no-code orchestration
With orchestration, the fabric can automate authentication, authorization, and identity transitions, without the developers needing to put security custom logic in each individual app. Instant value, particularly when managing user journeys like passwordless login, MFA escalation, or just-in-time provisioning.
Common Use Cases Across Industries
Identity orchestration is not just a concept. It's already addressing complicated, cross-platform identity challenges today. Below are what we found to be the most impactful use cases from various industries:
- M&A Identity Merging
When companies merge or acquire an entity, the IT departments of the two companies must merge the identity systems from the two companies, often leveraging multiple clouds and vendors. Identity orchestration can mitigate this complexity by correlating disparate IdPs and policies, eliminating the need to "rinse and repeat" the technology and related infrastructure already in place. Oftentimes, effectively implementing identity orchestration allows members of both entities to access shared applications, using their own unified policies without any downtime. - Securing Legacy Apps Without Code Changes
The majority of applications that support core business functions in various organizations are still legacy systems, especially in industry segments like healthcare, finance, and manufacturing. These applications often require native support for modern authentication mechanisms like SSO or MFA, both of which are critical for ensuring compliant access, and have no means of advancing authentication strategies. Orchestration allows you to establish security layers, such as adaptive MFA or risk-based access, and apply them externally to legacy apps, without modifying any existing code. - Automating User Onboarding/Offboarding
Provisioning or deprovisioning users in 20+ SaaS applications manually is inefficient and error-prone. Orchestration platforms automate these workflows based on lifecycle events such as employee hire or exit events from your HR application. This provides timely access provisioning and revocations, and offloads the burden from IT. - Auditable Access for Compliance (HIPAA, SOX)
Regulated industries like healthcare, finance, and government must demonstrate access controls during the audit process and deny access after employees have left. Orchestration guarantees that every access policy is consistently enforced across environments, and it captures every step along the way, making it easier to prove compliance with HIPAA, SOX, and GDPR.
Key Capabilities of Identity Orchestration
What's the big deal about orchestration platforms?
Identity orchestration platforms are not just integrations; they are blunt-cutting capabilities that simplify and strengthen your identity strategy across multi-cloud and hybrid environments. Here are some of the key capabilities:
Policy Automation:
Usually, orchestration platforms provide the ability to centrally define access policies and apply them dynamically across all your systems (cloud, on-prem, or hybrid). Policies can be triggered by user attributes, risk signals, time-of-day rules, or business logic. No-code interfaces provide the capability for teams to create rich workflows without touching application code, enabling consistent enforcement and quick turnaround for change management.
Federated Identity Management:
Have to manage multiple identity providers (IdPs) between regions, business units, or partners? Orchestration provides a single control layer to unify them. Support for federated SSO across multiple disparate IdPs (e.g., Okta, Azure AD, Ping, and much more) allows users to authenticate once and access everything they need, regardless of their credential repository. This is critical for M&A, multi-org architectures, or physical and ecosystem integrations.
Passwordless and MFA Integration
The use of identity orchestration makes it easier to modernize your authentication stack. You can harness adaptive MFA, biometrics, and passwordless login flows to add features to any application without rebuilding it. Whether derived from contextual signals such as location, device risk, or behavior, the orchestration layer dynamically enables stronger or weaker auth mechanisms.
Runtime Access Flows
Instead of relying on static access decisions at login, using identity orchestration, you can make access decisions in real-time throughout the duration of a session. This is helpful for contextually enforcing policy for direct access in a continuous fashion, particularly in Zero Trust scenarios. If a user's risk profile changes mid-session, their access can be adjusted or revoked in real time without re-authentication.
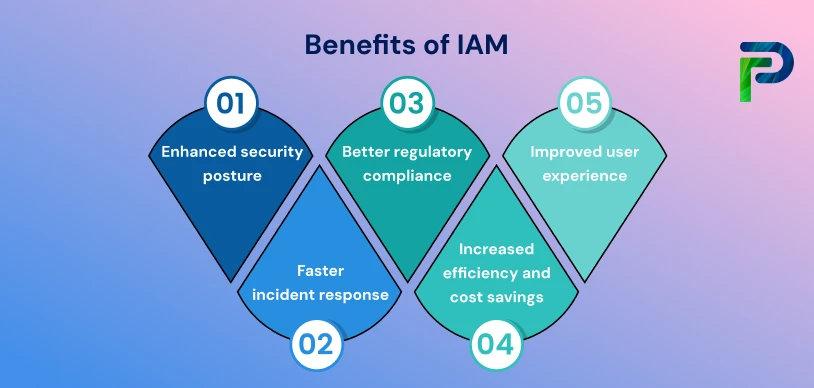
Benefits of Identity Orchestration
Security, efficiency, and modernization are no longer separate objectives. Identity orchestration offers all these benefits in one simple manner, acting above your existing identity and access infrastructure. Whether you are enforcing Zero Trust or trying to simplify access across hybrid environments, orchestration can help you do that more quickly.
Consistent Policy Enforcement
It's impossible to enforce consistent identity policies across environments, from SaaS applications through to legacy systems, with conventional IAM approaches. Orchestration removes these challenges by making policy enforcement declarative, as well as centralized.
It enables dynamic enforcement of policies (such as access rules and MFA requirements) that are set once at rule definition time, for wherever the application may ultimately reside. With its no-code policy, builders allow security teams to update rules on the fly, without turning to developers or having a formal change window. And audits become easy, since the orchestration system will provide a single point of truth for the access decision, as well as logs and trails of the decision information.
It supports consistent access governance, even if it has to be governed across heterogeneous underlying systems.
Modernization without Code Rewrites
Orchestration decouples identity logic from applications, critical for organizations that are bound by their legacy applications that weren't built using modern identity protocols like SAML, OIDC, or SCIM. It wraps old applications with orchestration flows, allowing you to inject modern capabilities like SSO, MFA, or just-in-time provisioning without touching the application itself.
Orchestration also provides protocol translation, which can allow a modern IdP like Okta to authenticate users to a legacy application that only speaks LDAP. When migrating to cloud apps, orchestration can provide a bridge so that apps can migrate without breaking user access. This helps you rethink and modernize identity at the speed of infrastructure, not at the speed of application development.
Reduced Admin Overhead
Provisioning and deprovisioning users manually is a time-consuming process and often loaded with errors. Orchestration provides organizations with identity lifecycle events that can be automated based on business triggers (HRIS updates or an AD group change).
Users can be onboarded, provisioned with role-based access, and deprovisioned automatically, resulting in reduced IT tickets and fewer missed revocations. Workflows weave across systems, for example, provisioning an app in Azure, a SaaS tool (like Salesforce), and a VPN in a single workflow. And admins no longer need to write and maintain fragile scripts or one-off connectors.
This automation leads to faster access delivery, fewer helpdesk tickets, and better compliance with least privilege.
Improved User Experience and Productivity
Inconsistent identity flows are detrimental to end-user productivity. With orchestration, users can switch between applications with seamless SSO even if the apps live in different clouds or use different identity providers. Users can also have adaptive MFA, based on risk signals including: device posture, geolocation, or time of access, improving both usability and security. Organizations can create self-service access portals or approvals through the orchestration layer to streamline access requests. Providing a better balance of usability with security, especially for hybrid and remote teams.
Resilience in Hybrid Environments
Orchestration provides architectural resilience by abstracting identity from infrastructure dependencies. It acts like a middleware layer that allows for consistent identity flows across public clouds (AWS, Azure, GCP), private data centers, and SaaS apps. Since orchestration is loosely coupled from the underlying systems, any changes (IdP switch, M&A, moving to cloud, etc.) do not require a significant rewrite. You also gain agility to bring in new technology stacks or identity providers without impacting the application-level access.

How to Choose the Right Orchestration Platform
Identity orchestration is a must-have, not a feature. Selecting the right platform is about choosing what will best accommodate your existing ecosystem, but also the capabilities to further evolve within your architecture. Selecting the wrong platform will lock you into another silo; the right platform will abstract away unnecessary ecosystems and eliminate optional silos.
Here are some thoughts worth consideration when evaluating orchestration platforms:
Key Criteria
- Vendor-neutral architecture
You do not want a solution that works perfectly well, just in its ecosystem. You want a platform that is neutral to multiple IdP possibilities (Okta, Azure AD, Google Workspace, etc.). Avoid vendor lock-in. Real orchestration platforms abstract identity, not create additional silo's. - Real-time, policy-based controls
Does the platform modify access policies at run time, dynamically? This is essential for Zero Trust, adaptive MFA, or session-level restrictions. Ideally, the platform will give you the ability to define policies from one central location and immediately enforce them regardless of whether the user is accessing apps, regardless if in the cloud or on-prem. - Cloud and Hybrid Compatibility
A contemporary orchestration layer must support multi-cloud (AWS, Azure, GCP), hybrid infrastructure, and legacy on-prem applications, to provide a consistent identity experience across all, without requiring custom code per environment. - No-code or low-code orchestration
There should be no need for you to write Python scripts and manage fragile XML policies. Rather, you should look for platforms that offer visual workflows, drag-and-drop policy builders, and declarative configuration for the teams to operate autonomously, providing a reliable platform with less reliance on engineering. - Protocol translation and identity bridging
The platform must translate and bridge identity between modern and legacy protocols (e.g., OAuth to LDAP or SAML to OIDC). This is critical if you have applications you can’t modernize, but still need to integrate into new access patterns.
Challenges Solved by Identity Orchestration
Identity orchestration isn't just a convenience layer but a tactical response to some of the biggest IAM aggregators, issues, and challenges that enterprises face today. As organizations drive warranted speed across clouds, applications, and geographies, traditional IAM implementations, approaches, and efforts cannot scale. Here is where orchestration comes in:
Multi-cloud Complexity
Identity management across AWS, Azure, GCP, and on-prem may often mean having separate access policies, authentication flows, and integrations for each stack. Identity orchestration resolves this by:
- Designating a single layer to handle and implement identities across all environments
- Providing a consistent access policy for identity regardless of cloud provider
- Supporting federated and governance authentication across clouds
Vendor Lock-in
The majority of IAM tools work best when used together, or in the expected eco-system, meaning it suddenly becomes very difficult to implement a new tool, switch vendors, without complete rewrites, and disruption to access. Identity orchestration overcomes vendor lock-in by:
- Abstracting and detangling identity flows away from the underlying IdP
- Allowing you to integrate with as many identity providers as needed without hardcoding
- Enabling easier modernization when, or if it works for you, rather than your vendor.
Lack of Skilled Identity Engineers
It is difficult to find identity engineers who have the skills and experience to do a good job. To train existing teams to build and maintain brittle, custom identity integrations? It is even worse. Orchestration platforms can provide help by:
- Providing no-code or low-code policy designing
- Decreasing reliance on scripting, or custom integration code
- Facilitating security and IAM teams that want to build workflows without needing advanced developers
Legacy End-of-Life IdPs
Organizations are often using on-prem IdPs like CA SiteMinder, Oracle, or IBM Tivoli, many of which are nearing or at end-of-life, but can’t be pulled out overnight. Identity orchestration can help with this situation by:
- Connecting legacy protocols to modern authentication (SAML to OIDC)
- Helping applications transition to modern identity flows without having to rewrite applications
- Supports co-existence in phased migrations from legacy systems to modern systems
Identity Orchestration vs. IAM, SSO, and IdPs
Identity Orchestration does not replace IAM tools, but it connects them and coordinates them. Most organizations already have foundational identity infrastructure in the form of IAM systems, SSO products, and IDPs. These identity tools allow for important functionality, but as identity ecosystems get more fragmented in multi-clouds, legacy apps, and several user types, they cannot work well together. That’s where identity orchestration comes in.
You can think of it as the control plane that stitches all of your identity tools together, coordinates access flows in real-time, and eliminates the need for brittle, custom code. Orchestration lives above your existing stack and supports flexibility, abstraction, and dynamic policy enforcement across any environment, without necessitating you to rip and replace what you already have.
Comparison matrix of Identity Orchestration, SSO, and IdP
| Feature / Capability | Identity Orchestration | SSO Solutions | Identity Providers (IdPs) |
|---|---|---|---|
| Purpose | Coordinate identity workflows across tools | Provides single sign-on across apps | Authenticates users |
| Scope | Cross-environment, multi-vendor, multi-cloud | App-focused | User-focused |
| Flexibility | Highly adaptable to hybrid, multi-cloud setups | Low. Requires tight integration | Low. Specific to vendor or platform |
| No-Code Policy Management | Built-in | Manual or scripted | Not applicable |
| Integrates Legacy + Modern Apps | Without rewriting code | Often requires custom connectors | Limited |
| Vendor Neutral | Works across vendors | Often tied to a vendor | By definition, tied to a vendor |
| Dynamic Runtime Policy Enforcement | Supports adaptive flows | Session-based only | Authentication-only |
| Multi-Cloud Support | Native support | Complex to scale | Limited |
| Supports Zero Trust Architecture | Core use case | Limited context awareness | Only handles authentication |
Final Thoughts
Identity orchestration is a game changer in today's hybrid and multi-cloud world with its disparate identities. It doesn't replace your IAM, SSO, or IDPs; it brings them together and extends them. Identity orchestration centralizes identity flows and deploys policies in real time, delivering secure, scalable access without the custom code or complication of multiple integrations.
Whether you're merging identities due to an M&A, securing legacy apps, or modernizing your stack to have ZT, identity orchestration will afford you the flexibility that you need to operate flexibly and securely in any environment!
Ultimately, identity orchestration isn’t just a tool. It’s the architectural glue that connects your identity strategy to your business goals securely, efficiently, and without compromise.
Ready to future-proof your identity strategy?
Frequently Asked Questions (FAQs)
1. What is identity orchestration in IAM?
It is a centralized control layer that automates and orchestrates identity workflows—such as authentication, access, and policy enforcement—in multiple applications, systems, and cloud environments.2. How is identity orchestration different from SSO?
SSO provides the convenience of a single sign-on to access multiple applications, using a single login credential. Identity orchestration provides a similar capability, but extends into the management of the entire identity lifecycle, including access logic, policy enforcement, and integration into different platforms.3. What are common identity orchestration tools?
Some examples include TechPrescient, Strata Identity, Ping Identity, Auth0, and Microsoft Entra—all of which provide orchestration capabilities to unify and automate identity lifecycle in complex hybrid environments.4. Can identity orchestration replace legacy IDPs?
No, identity orchestration does not replace an older identity provider. Instead, orchestration sits on top of the identity provider in order to unify, modernize, and automate access without disrupting the infrastructure already built.5. Why is identity orchestration critical for zero trust?
Identity orchestration provides a mechanism for applying continuous identity assurance and adaptive access policies across all environments, without relying on static trust. Orchestration is an essential component of supporting dynamic, risk-based access decisions on the fly as part of a Zero Trust architecture.