What Is User Provisioning? Full Guide for 2025

User provisioning is the process of setting up, managing, and maintaining user accounts and their access across various systems and applications within an organization. It ensures each user gets the right level of access based on their role, so they can do their job efficiently, while keeping security and compliance in check.
According to Gartner, 50% of help desk calls are permission-related, and human error is responsible for over 80% of access misconfigurations. That’s why automated user provisioning has become a security and compliance imperative. Modern provisioning strengthens your IAM strategy while supporting agility at scale. But how does it work? And why does it matter more than ever in 2025? Let’s break it all down.
Key Takeaways:
- User provisioning is central to secure identity and access management (IAM).
- Automation boosts efficiency, cuts security risks, and supports compliance.
- Provisioning methods include manual, automated, SCIM, RBAC, and self-service.
- A strong lifecycle covers onboarding, access control, updates, and deprovisioning.
- Best practices: least privilege, automation, access reviews, and MFA.
What Is User Provisioning?
User provisioning is the process of controlling and maintaining user access across an organization. It includes creating, updating, and removing user accounts and access rights across various systems and applications. This process typically involves several steps: setting up new user accounts, assigning appropriate roles and permissions based on job responsibilities, and managing identities throughout their lifecycle, from onboarding to offboarding. Effective identity management ensures that access levels are consistently aligned with organizational policies and employee roles.
A well-structured user provisioning system ensures that employees have timely and appropriate access to the tools, applications, and data they need to perform their jobs efficiently, while maintaining strict security and compliance standards. By automating this process, organizations can reduce manual effort, minimize errors, and significantly lower the risk of unauthorized access or identity misuse. Think of it like handing out keys to different rooms in your building. You wouldn’t give someone a key to every room just because they walked in, right? It’s the same idea here. With good provisioning, you’re making sure the right people get access to the right things at the right time, and that they lose that access when they’re done. Without it? Well, it’s like leaving the doors unlocked and hoping for the best. And that’s where the real risk creeps in.
“Provisioning ensures that access is timely, appropriate, and revocable, just as security should be.”
Definition of User Provisioning
User provisioning refers to automating the creation, updating, and deletion of user accounts and access permissions in an organization’s systems, typically as part of identity and access management (IAM).
In simple terms, it is the smart way to make sure people get the access they need, nothing more, nothing less, without the headache of doing it all manually. When you bring automation into the user provisioning process, everything just flows. New employees get what they need from day one, no waiting around. When someone leaves, their access disappears; no lingering “zombie accounts” lurking around. And say goodbye to tracking everything in messy spreadsheets. Instead, you get streamlined workflows that grow with your business.
- No more bottlenecks during onboarding
- No more “zombie accounts” post-exit
- And no more manual spreadsheet chaos
It’s security, efficiency, and compliance rolled into one process.
Why Is User Provisioning Important?
User provisioning extends far beyond simply setting up accounts; it’s crucial to running a secure and efficient business. When done right, it protects your data, keeps teams productive, and helps you stay compliant. In a digital world where access needs are constantly evolving, getting it right matters more than ever. Let’s take a look at why it’s so important:
1. Security
Proper user provisioning makes sure the right people have the right access. That means less chance of insider threats or someone stumbling into something they shouldn’t. It also helps avoid old or overly-permissioned accounts turning into easy targets for hackers. And in today’s world of hybrid and remote work, real-time provisioning is a must to keep identities secure across all your apps, devices, and cloud systems.
2. Operational Efficiency
Automated user provisioning gets new hires instant access to the tools they need, so they’re productive from day one. It also quickly removes access when someone leaves, cutting down IT work and closing security gaps. No delays, no confusion, just smooth, efficient transitions. The result? Happier teams and seamless operations across departments.
3. Compliance
Regulatory compliance refers to an organization’s ability to meet legal and industry-specific standards such as GDPR, HIPAA, SOX, and PCI DSS, each of which mandates strict control over user access to sensitive data. User provisioning plays a critical role in helping organizations meet these requirements by enforcing the principle of least privilege, maintaining comprehensive access logs, and ensuring that user access is granted, modified, or revoked on time.
Identity Lifecycle Management (ILM) supports compliance by automating access controls. It ensures accurate provisioning and deprovisioning, maintains up-to-date audit trails, and simplifies access reviews. By embedding these controls into daily operations, ILM not only strengthens security but also streamlines audits, making it easier for organizations to demonstrate compliance and reduce the risk of violations or costly penalties.
4. Risk Reduction
Automated user provisioning helps prevent privilege creep and the presence of orphaned accounts by promptly revoking access rights when users exit the organization or transition to new roles. By utilizing role-based access control (RBAC) and implementing policy-driven provisioning, organizations can consistently apply the principle of least privilege, ensuring that users are granted access only to the resources necessary for their responsibilities. Furthermore, conducting regular access reviews and certification campaigns enables organizations to validate and update user entitlements, thereby reducing the overall attack surface and enhancing the organization's security posture.
“A single unrevoked account can be a breach waiting to happen.”
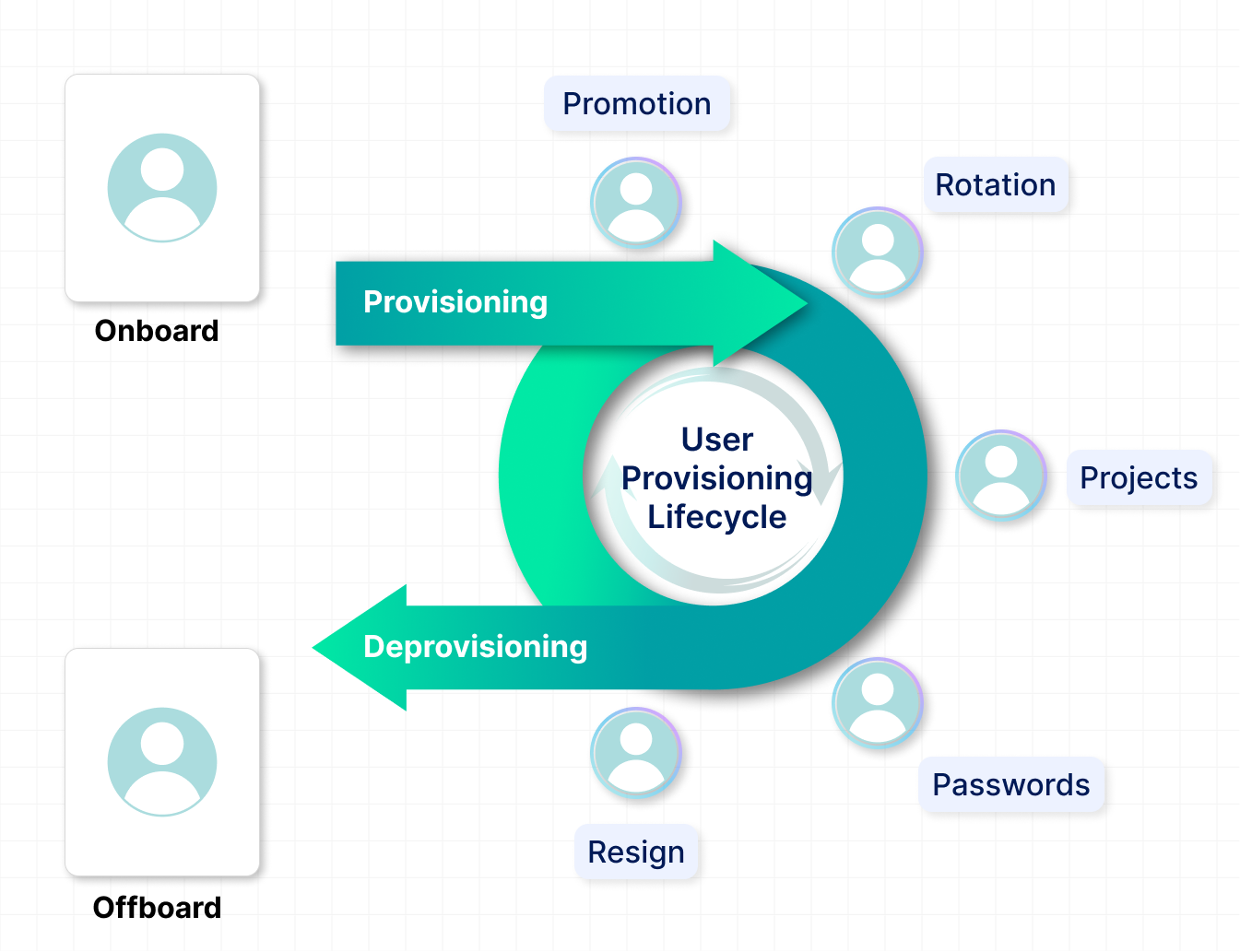
User Provisioning Lifecycle: From Onboarding to Offboarding
The user provisioning lifecycle covers every stage of a user’s access journey, from their first day to their last. It ensures the right access is granted, adjusted, and revoked as needed. Getting this lifecycle right is key to security, compliance, and operational efficiency. Here’s how it typically unfolds:
1. Account Creation
The user provisioning process starts when an HR or onboarding system sends a signal to create a new account. This automatically sets up the user in all the necessary systems, eliminating the need for manual work. It ensures every new user is set up properly and consistently. The result? Faster onboarding with fewer errors or duplicate accounts.
2. Role Assignment & Access Granting
After the account is created, access is given based on the person’s role, department, or other key details. This is done using RBAC or ABAC models, which help assign the right permissions automatically. It follows the “least privilege” rule: just enough access to do the job, nothing extra. That way, users get exactly what they need, keeping things secure and simple.
3. Modification During Role Changes
As people change roles, switch teams, or take on new projects, their access needs to change too. This part of the user provisioning process keeps permissions up to date in real time. Without it, someone might lose access they need, or keep access they shouldn’t have. Both can cause security risks and slow down productivity.
4. Deprovisioning
When a user exits the organization or no longer requires access, the final stage in the user provisioning lifecycle is deprovisioning. This process leverages automation to revoke permissions, terminate active sessions, and disable user accounts across all integrated systems. By preventing orphaned accounts and unauthorized access, deprovisioning strengthens security posture and supports regulatory compliance, particularly critical in enterprise environments.
“Provisioning is not just about giving access; it’s about taking it away at the right time.”
What Are the Types of User Provisioning?
The user provisioning lifecycle can take many forms depending on your organization’s size, tools, and security needs. From manual setups to fully automated and role-based models, each approach offers different levels of efficiency and control. Understanding the types of user provisioning helps you choose the right method for scaling securely and effectively.
1. Manual Provisioning
Admins have to set up user accounts and give access to one system at a time, doable for small teams, but a real hassle as things grow. It’s slow, easy to mess up, and not great for security. Without automation, tracking changes or staying compliant gets tough. The more users you have, the bigger the headache.
2. Automated Provisioning
With automated provisioning workflows, users are granted access to applications based on predefined roles. When someone is assigned a role, like Sales, the system automatically creates their account and provisions access to all associated apps, such as Salesforce, Office 365, and G Suite. This eliminates manual setup, reduces errors, and ensures consistent, role-based access across your environment.
3. Role-Based Access Control (RBAC)
With RBAC (Role-Based Access Control), users get access based on their job role, like HR Manager or Developer. Instead of assigning permissions one by one, roles come with set access rules. It’s consistent, easy to manage, and helps avoid giving too much access. This way, everyone gets just what they need, nothing more.
4. Self-Service Provisioning
Self-service provisioning lets users request access to tools or apps through a simple portal. Requests go through automated approval steps, so users get what they need faster, without IT losing control. It cuts down wait times and avoids the back-and-forth of manual tickets. Everyone wins with faster, smoother access.
5. SCIM Provisioning
SCIM (System for Cross-domain Identity Management) is an open standard that automates the exchange of user identity data between identity providers and cloud apps. It handles provisioning, updates, and deprovisioning in real time using standardized REST APIs. This reduces manual effort, keeps identities in sync across systems, and is ideal for managing access in multi-cloud environments.
How Does User Provisioning Work?
User provisioning involves several coordinated steps to ensure users have the right access at the right time. From onboarding to deprovisioning, each stage plays a critical role in maintaining security, efficiency, and compliance. Here’s how the user provisioning workflow typically unfolds behind the scenes.
1. Trigger
The process begins when a new hire is added to the HR system, like Workday or BambooHR. That update sends a signal to identity systems to start setting up accounts. Since it all starts with HR, the source of truth, everything stays accurate and in sync. It’s a simple, automated way to launch the user lifecycle.
2. Identity Sync
The IAM system keeps user info synced across all platforms, apps, directories, and services. That means no more entering the same details in multiple places. If something changes, like a job title or department, it updates everywhere automatically. It’s a smooth way to keep identity data accurate and up to date.
3. Role Mapping
Access is given based on a person’s job role or other details, using models like RBAC or ABAC. This makes sure users only get access to what they need for their work. It helps avoid giving too much access by mistake. The result? Better security and fewer manual errors.
4. Access Provisioning
Once access is mapped, the right permissions are automatically given for the tools a user needs, like email, collaboration apps, or finance systems. Everything is tracked for auditing, so there’s a clear record. The best part? The user gets instant access without waiting on IT. It’s fast, secure, and hassle-free.
5. Deprovisioning
Deprovisioning refers to the process of modifying or removing user access when an individual leaves the organization or transitions to a different role. This ensures that access permissions are updated to reflect the user’s current status, helping prevent the existence of unused or orphaned accounts. Proper deprovisioning is critical for maintaining system security, minimizing the risk of unauthorized access, and ensuring that identity and access data remains accurate and up to date. Even routine updates like these play a significant role in reducing security vulnerabilities and strengthening overall access governance.
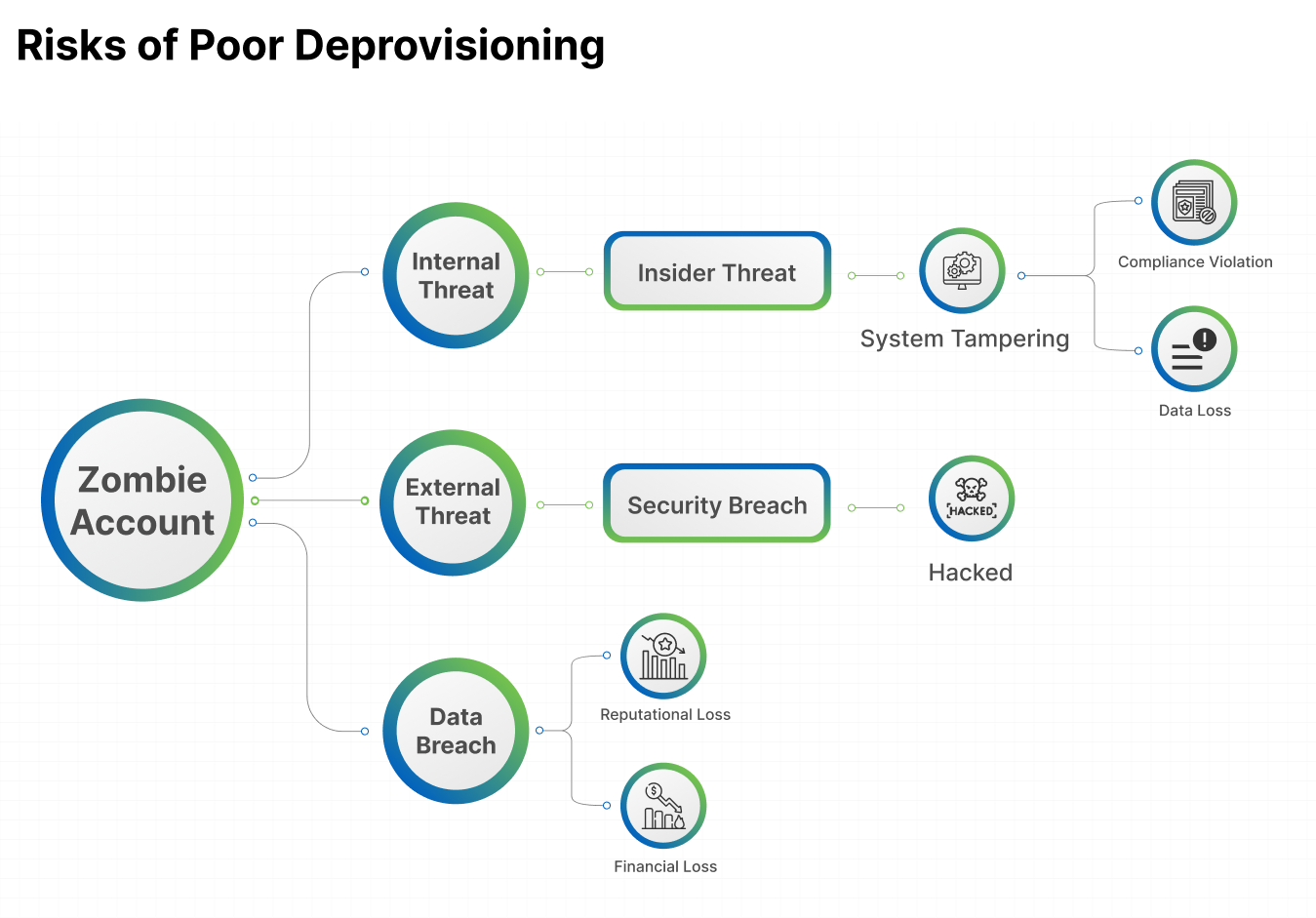
Provisioning vs. Deprovisioning
Provisioning is the process of granting users access to systems, applications, and data based on their role, department, or other identity attributes. It ensures that employees are equipped with the necessary resources from day one, enabling immediate productivity and reducing onboarding delays. Provisioning typically includes account creation, role-based permission assignment, and application access setup, automated through IAM systems to minimize manual intervention and reduce the risk of errors. An effective provisioning process not only accelerates user onboarding but also enforces consistent access policies and centralizes control.
Deprovisioning refers to the timely removal or adjustment of access rights when a user leaves the organization or no longer requires specific resources. It is a critical component of access lifecycle management, playing a key role in maintaining security and regulatory compliance. By revoking access promptly, organizations can prevent potential data breaches, eliminate orphaned accounts, and reduce their overall attack surface. Automated deprovisioning ensures that user access is terminated across all connected systems, helping to close security gaps and complete the user lifecycle in a controlled and compliant manner. Together, provisioning and deprovisioning form the foundation of secure and policy-driven identity management.
What Are the Benefits of User Provisioning?
Implementing user provisioning brings measurable benefits across security, efficiency, and compliance. By automating access management and aligning it with business roles, organizations can reduce risk, streamline operations, and maintain better control over user activity. Let’s explore the key advantages it offers.
1. Improved Security
No more giving users too much access or letting old permissions linger. Provisioning follows the “least privilege” rule: just enough access to do the job. This keeps things tighter and more secure. It helps prevent insider threats and limits damage if something goes wrong.
2. Faster Onboarding/Offboarding
New users get instant access to the tools they need, no waiting or chasing IT for help. When someone leaves, their permissions are removed right away, keeping things secure. It prevents gaps and forgotten access. The whole process is smooth, with no lost time or added risk.
3. Reduced IT Workload
Provisioning takes care of the repetitive stuff, like creating accounts and managing access, automatically. That means IT teams don’t have to do it all by hand anymore. It saves time and cuts down on busywork. Now, admins can focus on bigger things like security, compliance, and improving systems.
4. Enhanced Compliance
Automated provisioning systems generate comprehensive audit logs for all access-related activities, such as account creation, role assignments, and deprovisioning, ensuring complete traceability for compliance audits under standards like GDPR, HIPAA, and SOX. By applying policy-driven access controls and aligning provisioning workflows with regulatory requirements, these systems ensure that access is consistently granted and removed as needed. This not only minimizes the risk of human error or policy violations but also simplifies audit preparation and reduces the operational burden on IT teams.
5. Centralized Access Control
A centralized view lets admins see exactly who has access to what, across every system and team. This makes it easier to spot anything unusual and run regular access checks. It also helps apply the same security rules everywhere. Clear visibility means better control and fewer surprises.
6. Streamlined User Management Across Systems
User provisioning simplifies management by automatically syncing user data from sources like Active Directory (AD), LDAP, and other integrated applications. It ensures user profiles stay current across all connected systems, reducing manual updates and keeping information accurate at all times. This improves consistency and minimizes the risk of outdated or incomplete user data.
Challenges in Scaling Provisioning
Scaling user provisioning isn’t always straightforward, especially as organizations grow, adopt new tools, or integrate with external systems. Inconsistent policies, outdated processes, and messy data can create real friction. Here are some of the biggest challenges businesses face when trying to scale provisioning effectively.
1. Inconsistent policies across tools
As companies use more SaaS and cloud tools, access rules can get scattered across different systems. That leads to messy setups, like duplicate roles and gaps in security. Things start slipping through the cracks. A unified provisioning strategy keeps everything consistent, secure, and easy to manage.
2. Growing pains during mergers or hypergrowth
When companies go through mergers, acquisitions, or fast growth, provisioning systems can get overwhelmed. There’s a rush to add new users, systems, and domains quickly. That’s why automation and clear policies are so important. Without them, delays and mistakes can slow everything down.
3. Manual errors in legacy systems
Older IAM setups often rely on manual provisioning, which can be slow and full of mistakes. A simple typo or outdated script can open the door to security risks. It’s also tough to track and audit everything properly. As the company grows, these issues only get bigger.
4. Keeping identity data clean and current
Provisioning works best when your user data is clean and accurate. If records are old, duplicated, or missing info, things can break or go wrong. That’s why it’s important to keep identity data in sync across HR, IT, and IAM systems. Good data means smooth, reliable provisioning.
Best Practices for User Provisioning
To ensure secure, efficient, and scalable user provisioning, it's essential to follow structured best practices. From automating access management to enforcing least privilege and regular audits, these strategies help reduce risk, improve compliance, and streamline operations across the user lifecycle.
1. Automate Whenever Possible
Leverage IAM tools with built-in automation to efficiently handle user onboarding, access modifications, and timely deprovisioning. Automated workflows reduce manual errors, improve consistency, and ease the administrative burden on IT teams. These solutions are designed to scale seamlessly with complex IT environments, accommodating the addition of new systems, applications, and user roles without compromising control or performance. It’s a reliable, efficient, and scalable approach to identity and access management.
2. Apply Least Privilege
Give users just the access they need to do their jobs, nothing more. Avoid permission sprawl by linking access to roles or key details, and remove it when it’s no longer needed. This keeps things clean and secure. Least privilege is a core part of smart access management.
3. Standardize Onboarding/Offboarding
Use templates, workflows, and checklists to make sure provisioning and deprovisioning are done the same way every time. This keeps things consistent and reduces the chance of something being missed. It also creates a clear record for audits. Standardizing the process helps with both security and smooth operations.
4. Conduct Regular Access Reviews
Over time, people often end up with more access than they need. Regular access reviews help catch this “access creep” and keep permissions in check. The best way to do it? Set clear policies and automate the process when you can. It keeps your systems secure and your access clean.
5. Use MFA & Risk-Based Authentication
To enhance identity and access security, Identity and Access Management (IAM) systems utilize Multi-Factor Authentication (MFA) along with risk-based adaptive authentication. MFA requires users to authenticate their identity using multiple independent factors, commonly including something they know (like a password), something they have (such as a hardware token or mobile authenticator), and something they are (biometric identifiers).
Risk-based authentication strengthens security by dynamically analyzing contextual risk factors, such as device type, geolocation, IP address reputation, time of access, and user behavior, during each login attempt. Based on the level of assessed risk, the IAM system can apply adaptive access controls in real time, which may include prompting for additional authentication steps, restricting access privileges, or completely blocking access when suspicious or high-risk activity is detected.
This method helps maintain a strong security posture by lowering the chances of unauthorized access while also ensuring a seamless experience for legitimate users through intelligent, context-aware access management.
Real-World Examples & Use Cases
Axos took control of over 200,000 permissions by centralizing their IAM processes across both cloud and on-prem systems. This made managing user access much simpler and more consistent. It also helped them get audit-ready faster. Plus, it cut down the mess of permission sprawl across departments.
CO2 AI used RBAC to automate access provisioning for their sustainability teams around the world. By setting up predefined roles linked to their climate work, they made access fast and secure. This way, teams got what they needed without delay. At the same time, sensitive environmental data stayed tightly protected.
User Provisioning in IAM vs. IGA
IAM systems are primarily responsible for managing the operational components of user provisioning. This includes automating the creation, modification, and oversight of user accounts and their associated permissions across integrated applications and systems. IAM platforms connect with authoritative data sources, such as HR systems, corporate directories, and SaaS platforms, to synchronize identity attributes and enforce access policies in real time. By automating standard processes like account provisioning and access assignment based on predefined roles or group memberships, IAM significantly reduces manual effort, speeds up onboarding and role transitions, and ensures timely offboarding, enabling streamlined and efficient access lifecycle management.
IGA goes beyond the operational tasks of provisioning by emphasizing governance, oversight, and compliance posture related to user access. It establishes a framework for evaluating who has access to which resources, the justification for that access, and whether it complies with internal policies and external regulatory standards. IGA capabilities include access risk scoring, approval workflows, periodic access certifications, and enforcement of segregation of duties (SoD) policies. While IAM handles the execution, creating and managing access, IGA addresses the reasoning and validation behind it, ensuring that all access rights are reviewed, certified, and governed in alignment with organizational risk management and compliance objectives.
Choosing the Right User Provisioning Tool
Choosing the right user provisioning solution is a strategic move, not just a technical one. It should support your growth, integrate with your IAM ecosystem, and scale across cloud and hybrid environments. At Tech Prescient, we build secure, scalable, and future-ready provisioning systems tailored to your business. From IAM to full IGA, our cybersecurity consulting ensures seamless onboarding, role-based access, and policy compliance.
Ready to simplify provisioning and strengthen your identity perimeter?
Frequently Asked Questions (FAQs)
Q. What is user provisioning in identity management?
A. User provisioning is basically how organizations give employees access to the tools and systems they need, like email, apps, or databases, based on their role. It also covers removing that access when someone changes roles or leaves the company.Q. How does automated user provisioning work?
A. Think of it as a smart system that handles access behind the scenes. When someone joins the company, their info from the HR system kicks off a process that assigns the right permissions automatically, no manual setup needed. It also pulls access when they leave, keeping things secure.Q. Why is role-based access control important in provisioning?
A. RBAC saves a ton of time and reduces mistakes. Instead of granting access one-by-one, users are grouped by roles, like “Marketing” or “IT,” and each role comes with the right permissions built in. Easy to manage, easy to audit.Q. What’s the difference between IAM and IGA in user provisioning?
A. IAM (Identity and Access Management) handles the basics: who can access what. IGA (Identity Governance and Administration) takes it a step further with compliance, policies, and deeper visibility into who's doing what and why.