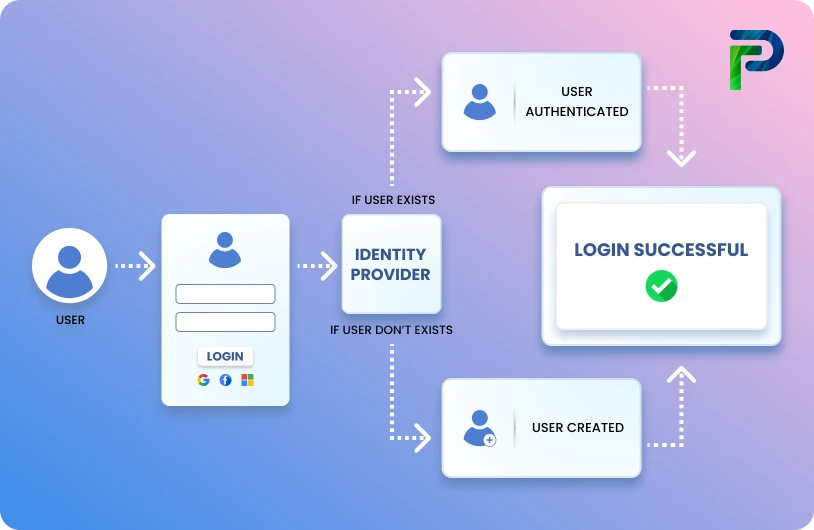
User Entitlement Review: Meaning, Process & Policy Template (2026 Guide)

User Entitlement Reviews (UERs) are essential to today's access governance. UERs are a systematic verification of whether individuals be it employees, contractors, or third-party partners, have access to the systems and data only in support of their current roles. By confirming access rights are in accordance to job duties, user entitlement reviews can create system security and compliance.
The problem? In fast-moving organizations, permissions often never catch up with changes in roles, rotations in projects, or departures. Employees change teams and retain entitlements from their prior team or project. Contractors finish contracts and retain access to the systems. Third-party vendors disengage, and their credentials are actively checked in. These situations create privilege creep, orphaned accounts, insider threats, and failed audits.
IBM's 2025 Cost of a Data Breach Report stated that the average global cost of a data breach fell to $4.44 million, a net reduction of 9% from the prior year. This decrease in cost was due to the faster identification and containment of data breach incidents, which suggests proactive security controls can be beneficial in a cost-effective manner. It is abundantly clear where poor entitlement governance can lead: to the exposure of sensitive data, regulatory non-compliance, and increased risks of data breaches. User Entitlement Reviews offer a structured method to detect, review, and certify entitlements so that access is congruent with the business objectives and security policies.
In this blog, we will discuss the value of entitlement reviews, the end-to-end workflow, best practices, and a simple-to-use policy template that you can leverage in your own organization.
Key Takeaways:
- The UER process helps protect against privilege creep by continually linking access rights to actual employment responsibilities.
- A regular entitlement review is a good way to ensure compliance with frameworks like SOX, HIPAA, GDPR, and ISO 27001.
- A predictable and structured workflow (inventory → classify → review → remediate → certify) ensures that access is managed consistently across any/all systems.
- Policy-based entitlement reviews bring accountability by defining a scope, frequency, ownership, and escalation paths.
- Automated entitlement reviews with a centralized IAM platform will not only make entitlement reviews faster and more accurate but also ensure they remain "audit-ready."
What Is a User Entitlement Review?
A User Entitlement Review (UER) iis a standardized, scheduled review of system and application permissions, authorizations, and access permissions assigned to the users within your systems/applications. The intention is to review these periodically and ensure that employees, contractors, vendors, or other third parties are only granted access to complete their job responsibilities. By conducting a regular entitlement review, organizations can limit excess right privileges, mitigate risk, and confirm compliance with internal policies and external audits or regulations.
This type of review answers four key questions:
- Who has access to what?
- What level of access does each of these users have?
- Does each of these users have a justified reason for access?
- How do I update these accounts?
But what does User Entitlement mean?
User Entitlements relate to a user's access rights or privileges to resources, applications, and data.
For example, an HR Manager may have entitlement to view employee records, but not entitlement to change payroll systems.
Entitlements are often assigned at the time of user provisioning, in which access is first granted. However, employees often acquire extra access rights over time due to employees changing roles, project types, and departments. Employees do not usually relinquish their rights, leading to privilege accumulation called Privilege Creep. Privilege creep is a major risk identified by User Entitlement Reviews. Also, Excess Privileges, permissions that are more than what is required for a user’s current role, may lead to unauthorized access, data leaks, or problems with compliance.
When an organization conducts reviews of entitlements, with certifications, regularly, they are:
- Compliance with the principle of least privilege.
- Preventing unauthorized or stale access continues.
- Complying with security frameworks and regulations.
- Mitigating risks related to insider threats and data breaches.
User Entitlement Review and User Access Review: Key Difference
While the terminology can overlap, there are distinct differences in the purpose of each term in the context of identity governance.
A user entitlement review (UER) evaluates the specific permissions, roles, and privileges assigned to a user to ensure they are necessary for their current job responsibilities. It helps prevent privilege creep, enforce least privilege, and maintain compliance with policies and regulations.
While on the other hand, a user access review (UAR) examines a user’s overall access across systems and applications to ensure it aligns with their role and responsibilities. It verifies that cumulative access is appropriate, supporting security, compliance, and operational efficiency.
| Aspect | User Entitlement Review (UER) | User Access Review (UAR) |
|---|---|---|
| Scope | Periodic evaluation of all user access rights, roles, and privileges across systems and applications. | Focused review of a specific user’s access to a particular resource, application, or system. |
| Frequency | Typically conducted annually or biannually. | Performed more frequently, e.g., monthly or quarterly, depending on risk and compliance requirements. |
| Purpose | Ensures users have access only to what is necessary for their job, enforcing least privilege across the organization. | Verifies that a user’s access to a specific resource is appropriate and aligned with their role and responsibilities. |
| Methodology | Often leverages automated tools and processes to streamline reviews across multiple systems. | May involve a combination of automated and manual reviews depending on the complexity of access. |
| Scope of Changes | Can result in broad adjustments to user permissions across multiple systems and applications. | Focuses on adjustments to a specific user’s access to the targeted resource. |
In practice, most organizations are utilizing both UERs and UARs within their Identity Governance and Administration (IGA) strategy. Utilizing UERs and UARs provides both detailed visibility of entitlements and overall visibility of user access as part of a more secure and compliant effort.
Why Are User Entitlement Reviews Important?
User Entitlement Reviews (UERs) are a critical component of access governance today. They provide compliance assurance and prevent excessive access by validating permissions and removing unnecessary and stale entitlements. They enable organizations to:
- Protect against insider threats by ensuring that no user has more access than they need.
- Be compliant with regulations such as SOX, HIPAA, and GDPR that require periodic access verification.
- Reduce organizational risk by eliminating attack exposure due to privilege creep, orphan accounts, and mismanaged entitlements.
- The financial impact, reputational damage, and failed audits are clear consequences of failing to conduct reviews.
Case Study: Real-World Breaches
1. Marriott Breach
Hackers broke into Marriott's systems over a long period of time, granting themselves persistent, long-term access to critical systems utilized by Marriott and its subsidiaries and affiliates. One of the primary enablers of this breach was entitlement and access reviews not being conducted properly. Attackers used unused and uncontrolled privileged permissions to undetectable lateral movement across multiple systems, gaining access to over 300 million guest records, payment card transactions, personal information, and even passport information. Marriott received almost $23.8 million in fines under GDPR and has incurred a number of losses (including reputation) that cannot be rectified. If Marriott had a strong UER program in place, it would have identified and removed those uncontrolled permissions much sooner.
2. GE Theft
At General Electric, there was a group of employees who exploited excessive entitlements to exit the company with confidential turbine design data. These entitlements were left intact from previous projects that had no governance or oversight to have those entitlements revoked. Once those employees left the company, the design data that they took with them ended up in the hands of foreign competitors, which has resulted in GE losing a huge amount of intellectual property, litigation, and legal exposure. If GE had a structured entitlement review process, it would have seen that there was a discrepancy between the employee's job and the entitlement they had, and would have found out about the theft sooner.
3. Cisco Sabotage
In Cisco’s case, a disgruntled ex-employee had retained cloud admin privileges, even after termination, and they deleted 456 virtual machines that supported key business functions. The damage caused in the millions in recovery costs, with downtime and loss of customers' trust. A robust approach to offboarding could establish a process with UERs to ensure that access and entitlement are fully revoked upon the employee exiting the door, eliminating any window for insider sabotage.
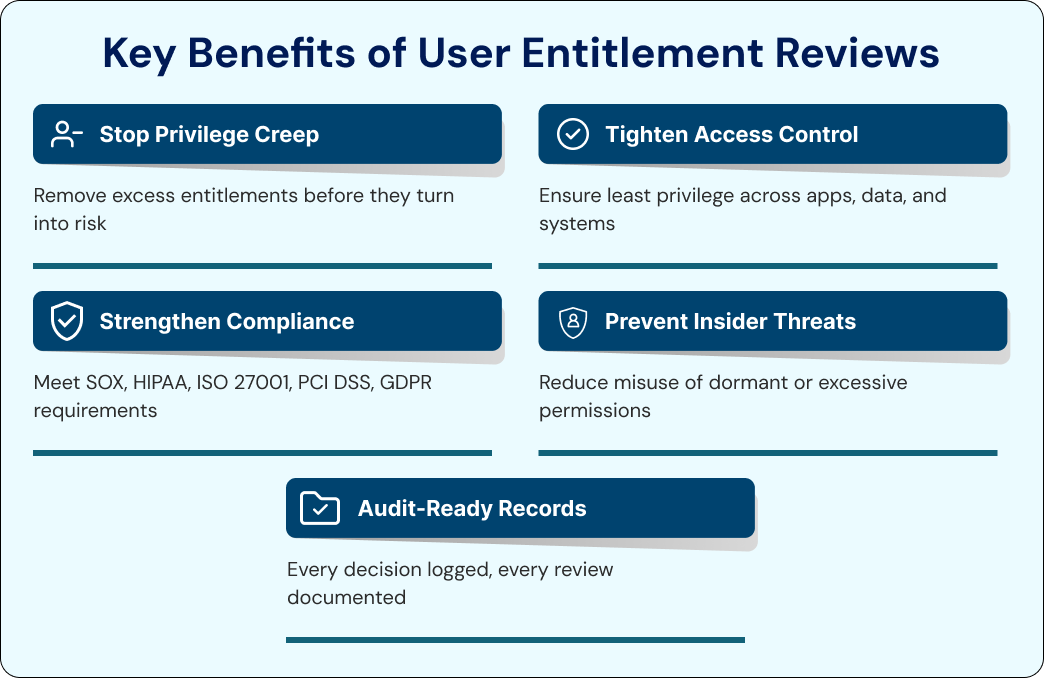
Key Benefits of User Entitlement Reviews
User entitlement reviews (UERs) are not merely a compliance check box, but are an important proactive security control that improves your organization's security posture while keeping your operational costs low and your organization audit-ready. By systematically reviewing entitlements periodically, you not only mitigate risk from excess entitlements, but you also gain visibility into what entitlements are available to users across all systems. Here are the most important advantages of performing UERs regularly:
1. Prevent Unauthorized Access
Unless you are conducting regular reviews, it is fairly common for employees, contractors, or third parties to carry forward permissions they no longer require. These "orphan" or "dead" entitlements represent high-risk access points for malicious insiders and attackers from the outside.
Why it matters: Restricting users to only the entitlements they require at their role level reduces exposure to sensitive data and applications.
Example: An employee moved from finance to marketing but has access to payroll data. A UER would have discovered and removed this access before harm could occur.
2. Meet Compliance Requirements
Most regulatory frameworks, including SOX, HIPAA, ISO 27001, and PCI DSS, specifically require organizations to conduct periodic entitlement or access recertifications to protect sensitive information. Non-compliance can lead to audit failures, penalties, and damage to the organization’s reputation.
Why it matters: UERs provide a defensible record of your continual compliance with industry standards and regulations.
Example: A financial institution can provide quarterly UER reports for each of the last three years during a SOX audit, demonstrating to the auditors that only authorized staff have access to accounting systems.
3. Enhance Security Posture
An organization that has too many outdated or over-privileged entitlements has a larger attack surface, which increases the risk exposure to bad actors who are trying to exploit a weakness. Entitlement reviews that apply the principle of least privilege (PoLP) are another way of finding and removing those types of risks, including over-privileged accounts or access, and can strengthen the overall security posture of an organization.
Why it matters: The smaller the attack surface, the less opportunity for attackers to move laterally or escalate privileges.
Example: An entitlement review discovered multiple cloud app admin rights that had not been used in more than 90 days. Removing these admin rights prevents an attacker from taking complete control or performing any administrative functions in the event the attacker compromises that cloud account.
4. Reduce SaaS License Costs
It’s common for organizations to pay for SaaS licenses related to entitlements that are not in use. Reviews can identify permissions not assigned to users and will enable IT teams to deprovision this entitlement for the user.
Why it matters: In addition to better security, entitlement reviews lead to extremely meaningful cost savings going forward, as they will help drive right-sized SaaS and software utilization costs.
Example: A review of entitlements identified that 40 inactive users had been assigned Salesforce licenses. Savings can amount to tens of thousands of dollars for the company in annual fees by removing these entitlements.
5. Improve Audit Readiness
Preparing for an audit can be stressful, especially if you do not have a clear view of your users’ entitlements. Regular entitlement reviews help keep a centralized audit trail that will be well-documented and easy for auditors to validate.
Why it matters: Rather than spend weeks collecting and compiling evidence, you will have evidence in a report suggesting you have sound access governance.
Example: A company preparing for an ISO 27001 audit was able to provide entitlement review logs downloaded and exported straight from their IAM platform, drastically shortening the audit duration by months.
Challenges Organisations Face with User Entitlement Reviews
Although entitlement reviews are important, many organizations find it difficult to perform them properly. They are forced to deal with manual processes, siloed systems, and poor visibility, which can be overwhelming. Here are the most common challenges that hinder effective entitlement reviews:
1. Resource Intensive
With manual reviews, the IT teams often have to collect entitlement data from multiple systems, format and document it, and submit it to managers for approval. This takes weeks of effort, especially for large organizations, leading to delays on entitlement review cycles or simply checking the box instead of treating it as a security control.
2. Complex Role Structures
Enterprises with thousands of employees are often managing many overlapping roles across departments, projects, or geographies. As users ultimately acquire entitlements for different roles, these users can be hard to evaluate as to whether their current access is warranted. This complexity only increases risk for privilege creep and possible security breaches.
3. Data Visibility Issues
When entitlement data lives in different SaaS platforms, legacy applications, on-premises databases, and even cloud environments, it creates a scenario where a reviewer has no single source of truth. Without visibility of everything, identifying too much or risky access is nearly impossible. This lack of visibility offers ample opportunities for malicious insiders or attackers who take advantage of overlooked entitlement.
4. Stakeholder Coordination Gaps
User entitlement reviews aren’t simply an IT function; they require some level of input from HR (to define employee roles), compliance (to address regulatory requirements), and business managers (for daily access requirements). All of this is subject to misalignment, which can add delays, misaligned priorities, or result in no review at all. When there is no alignment around entitlement reviews, they lose their effectiveness, and compliance requirements are not met.
User Entitlement Review Process: Step-by-Step
Having a clearly defined entitlement review process allows you to obtain an accurate account of access in relation to business requirements, bolster compliance posture, and minimize privilege abuse. Below, there is a framework organizations can utilize, which is structured to be audit-ready:
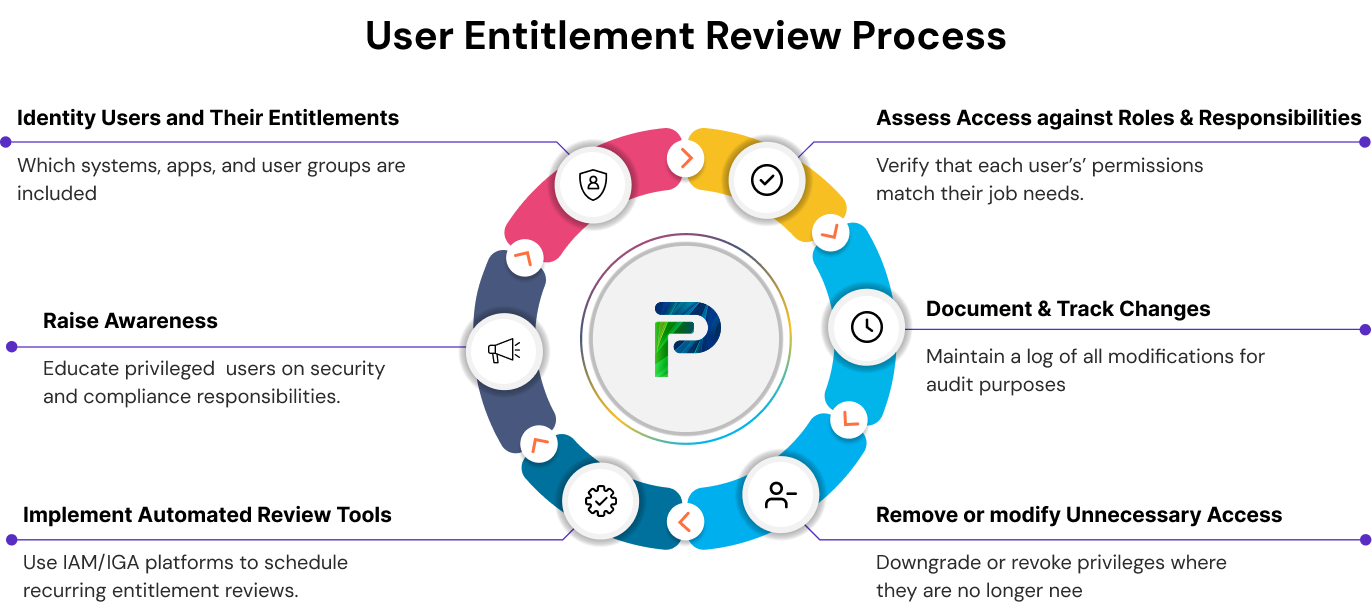
Step 1: Identify Users and Their Entitlements
Develop an inventory of users, systems, applications, and accounts. Map the entitlements by roles such as Finance, HR, or IT Admin to ensure those roles are clear and that there are no blind spots on critical systems. Accountability will be difficult without a complete inventory. It is impossible to assess if someone has excessive or old privileges without having an inventory to evaluate against.
Step 2: Assess the Entitlement against Roles and Responsibilities
Assess at a minimum if the entitlement is within the user's current accountabilities. Be aware of discrepancies such as an employee having unnecessary administrative rights or users that have switched departments yet still maintain access to former department rights, or contractors having excessive privileged access. This exercise seeks to manage privilege creep while keeping access in accordance with the least-privilege requirement.
Step 3: Document and Track Changes
It is important to maintain records of the entitlement reviews even if there are no changes to entitlement. Document all removals and approvals along with any exceptions that were noted. Documentation is a way to provide transparency and evidentiary support for regulators and compliance teams. It is common for auditors to want proof of reviews, and if documentation has not been maintained, staff may be required to search for evidence at the last moment.
Step 4: Remove or Modify Unnecessary Access
Revoke or downgrade access levels no longer needed, i.e., restrict inactive accounts, delete historical entitlements, and change access levels when someone’s role changes. Quick cleanup is a simple approach to also minimize unwanted insider threat risks and/or entry points for attacker access.
Step 5: Implement Automated Review Tools (IGA/IAM)
Consider incorporating an Identity Governance and Administration (IGA) and/or Identity and Access Management (IAM) solution, such as Tech Prescient’s Identity Confluence, to automate future periodic reviews/audits. These tools will automate the collection of entitlement data, issue reviews, and notify reviewers, and possibly even identify top entitlement risk items for quicker action. Using automated review tools makes it easier to ensure reviews happen on time and may lessen the load on IT teams tasked with completing compliance tasks.
Step 6: Raise Awareness Among Privileged Users
Educating privileged users (admin, superusers, managers) on access review policies and security requirements is essential. There are strict compliance requirements and specific obligations that must be met by organizations. Education can help limit mistakes and non-compliances, such as privileged users retaining unused accounts or over-provisioning their team members. Human error is consistently one of the leading causes of access-related breaches, and education plays a critical role in preventing such breaches.
Step 7: Continuous Monitoring
Don't only do entitlement reviews quarterly or annually. Ongoing monitoring of entitlement modifications made by privileged users across your systems allows security teams to identify risks in real-time (i.e., account privilege escalation on one system that has been made dormant and then activated repeatedly). This guidance transitions entitlement reviews from a compliance checklist exercise to a live and engaging security control.
Best Practices for Effective User Entitlement Reviews in 2025
User entitlement reviews (UER) are no longer merely compliance requirements but rather imperative to mitigating insider threats and enabling organizations to be more resilient against the risks of evolving cyber threats. However, as systems are scaled and identities proliferate, reviews can easily become unmanageable without a strategy to guide you.
"The best way to ensure entitlement reviews are successful is to find a happy medium between automation and human insight. It is important to automate wherever possible, but remember to always provide business context to ensure access is not just compliant, but also reasonable."
~ Sumod Tarkunde, Sr. Business Analyst
1. Clearly Establish the Review Scope
Develop a clear understanding of the systems, applications, and user populations included in the review. A clear scope leads to appropriate reviews, too much is wasted investigating non-impactful areas, and less chance that significant apps or sensitive data will be overlooked in reviews.
2. Use the Least Privilege Principle
Users should be given only the minimum permissions necessary to do the job at hand. Regular entitlement reviews should allow organizations to identify and remove excessive privileges, thereby shrinking the attack surface of the organization and limiting the impact of a breach, if it occurs.
3. Automate with IAM/IGA Tools
Use automation to assist in data collection, notifications for the review process, and help identify risk where applicable. Automated tools can identify anomalous activity, create audit-ready reports, help with reviewing access, and help accelerate the review cycles-instead of onboarding and training IT or security teams, focusing on their primary job responsibilities.
4. Revoke Access for Former Employees Promptly
Offboarding means the removal of access by revoking entitlements promptly. The longer someone has access, the greater the opportunity for insider threat or unauthorized access. Automated deprovisioning can assist in ensuring access is automatically removed upon the departure of an employee, contractor, or third-party.
5. Include All User Types
Do not restrict your reviews to just permanent employees. Contractors, vendors, privileged IT users, and service accounts all have potential risks that are often overlooked. A full review across types of users will guarantee that no entitlements are missed.
6. Maintain Audit Trails and Update Policies Regularly
Record every change, approval, and decision made in the entitlement review. Each updated policy can provide consistency, reflect changing systems and regulations, and can be a strong defensive evidence during audits to demonstrate compliance.
User Entitlement Review Policy Template Essentials
Having a well-documented policy is essential to a successful entitlement review. Without a clear policy, organizations will gravitate toward uneven practices, a patchwork of accountability, and non-compliance. A policy consolidates one's process and ensures that IT, security, HR, and business are unified in the correct allocation of entitlements.
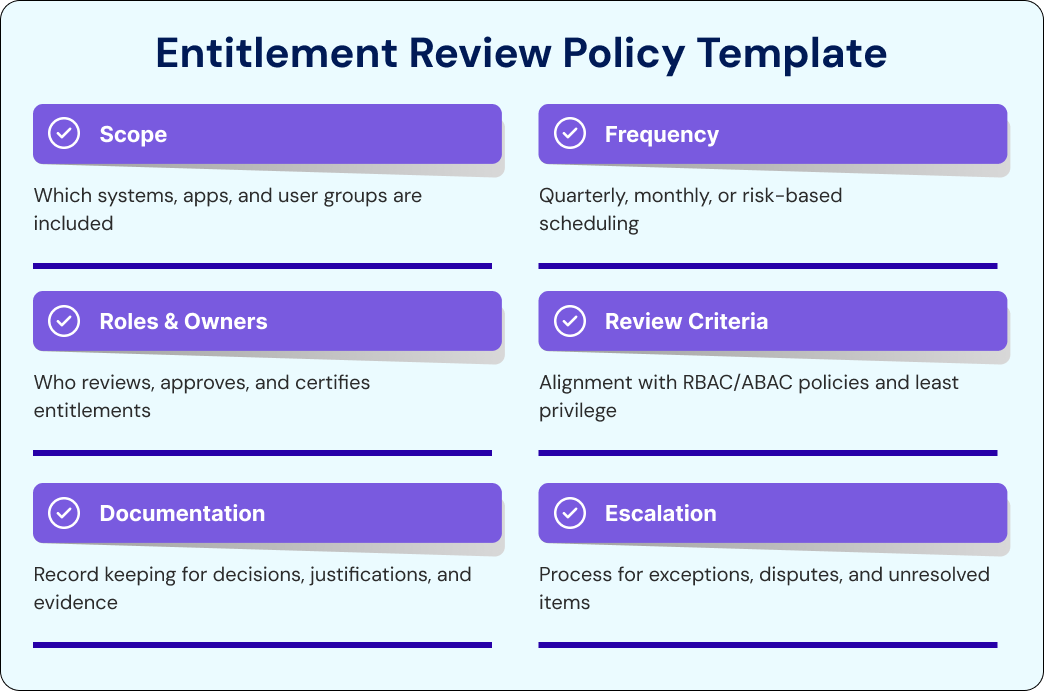
The following are important sections that your User Entitlement Review (UER) Policy should cover:
1. Purpose
Articulate the reason for the review process in the purpose section; it should list objectives for the process game plan, including avoiding unauthorized access, minimizing privilege creep, reducing compliance concerns (SOX, HIPAA, ISO 27001, PCI DSS), and securing mission-critical resources. Define business objectives that are parallel with the security objectives.
2. Scope
Explain what will be considered for the review. Identify systems, applications, databases, and user groups that will be addressed in the review, as well as an indication of whether external contractors, vendors, or privileged accounts are included in the scope. Clarity about what is addressed will reduce confusion and will allow reviewers to be thorough, followed by an iterative process.
3. Frequency
Establish review intervals based on risk and compliance considerations. For example:
Quarterly – When high risk (financial systems, administrative accounts).
Biannually/Annually – When risk is lower or less sensitive.
Documenting frequency ensures reviews are completed uniformly and can be defined for an audit.
4. Responsibilities
Assign accountability throughout the organization, virtually:
IT/security teams → Carries out entitlement discovery and technical review.
Managers → Oversee validating user access against job responsibilities.
Compliance → Assess that organizations are complying with regulatory obligations.
HR → Provides timely updates concerning updates to roles/departures.
Outlining layered responsibilities prevents inaction and accountability gaps.
5. Documentation Requirements
Identify what needs to be documented: entitlement access, changes (the action taken), rationale for approvals or denials, reviewer sign-offs, and audits. Documentation introduces transparency and provides evidence in an internal or external audit.
6. Automation Tools Used
Specify IAM/IGA Platforms or automation tools your organization utilizes (and approves) for entitlement reviews. For example, solutions that automate notifications, produce documents, and escalate anomalies. Standardizing on tools improves accuracy, eliminates manual work, and provides rapid compliance reporting.
Automating User Entitlement Reviews with IGA Tools
In today's identity-driven companies, automation is just not a choice; it’s a necessity. Employees use dozens of SaaS apps, cloud platforms, and internal systems, which means the volume and complexity of entitlements has moved beyond what any spreadsheets or human being can manage. Security teams are being asked to:
- Go faster – cyber threats are changing in real time, and reviews can't wait for quarterly cycles.
- Be accurate – just one missed privilege could lead to a breach that will cost us.
- Be compliant – auditors want to see clear, documented evidence of who has access to what.
This is where automation can deliver an improved user experience. Automating entitlement reviews through an Identity Governance and Administration (IGA) solution delivers speed, consistency, and transparency that manual reviews do not have. Automated entitlement reviews can change access governance from a reactive box-checking activity to doing something productive to advance the security posture.
Providing Real-Time Reporting
Automated platforms pull entitlement data from all the SaaS apps, cloud, and on-prem systems, and instantly tell you who has access to what, not by manually going into each tool, but all in one spot.
Identifying Anomalies
Automated anomaly detection identifies access misuse like inactive accounts, duplicate entitlements, or excessive admin access, all things that a person reviewing access may overlook.
Tracking Approvals and Revocations
Instead of a snarl of emails, automated workflows can route approval requests to proper managers and record revocation actions in one central location for planning and accountability.
Creating Audit-Friendly Logs
Workflow automation allows every approval, denial, and modification to be recorded, making replaceable records that are protected from change. This makes compliance audits more manageable than you can imagine.
💡 With TechPrescient’s Identity Confluence, security teams can automate the entire entitlement review process, from uncovering excessive privileges to enforcing policy-based deprovisioning and producing audit-ready reports, all in one single dashboard. Reducing mistakes from manual requests, accelerate the review, and improving compliance without burdening your team with overhead.
Final Thoughts
User entitlement reviews are not optional anymore; they are essential. In a rapidly evolving threat landscape, outdated or excessive access can quickly become a breach, compliance violation, or an expensive operational headache. Organizations that approach user entitlement reviews as a key security practice, rather than a simple tick-the-box task, will have a clear advantage: increased security, reduced risk, and fewer concerns at audit time.
If you are still using manual reviews, it's time to shift gears. By adopting an automated review mechanism, you can move from a tedious spreadsheet and endorsement process to continuous, audit-ready access governance. Effectively executing user entitlement reviews today decreases the risk for your business and secures it for the future.
Identity Confluence helps you automate reviews, generate audit-ready reports, and enforce least-privilege access with ease.
Get started faster → Learn more about Identity Confluence
Frequently Asked Questions (FAQs)
1. What is a user entitlement review, and why is it important?
A user entitlement review is the method of validating a user’s permissions, roles, and access to ensure alignment with current activities. It's significant because it reduces insider threats, improves oversight privilege creep and maintains compliance for the organisation.2. How is a user entitlement review different from a user access review?
A user entitlement review validates specific permissions and roles; a user access review looks at the appropriateness of overall access for each user. Together, they make a comprehensive user access governance strategy.3. How often should user entitlement reviews be conducted?
Most organisations do entitlement reviews quarterly or biannually, depending on compliance requirements in place like SOX, HIPAA, and PCI DSS, along with their internal risk tolerance.4. What are the biggest challenges of manual entitlement reviews?
Manual entitlement review is slow, often inaccurate, and can be a step-by-step process across IT, HR, and compliance teams. Missing records present challenges, as do incomplete records, which can delay the audit process.5. How can automation improve user entitlement reviews?
Automation, with integrated IGA tools, greatly reduces human error, provides more accurate up-to-the-minute visibility, flags excessive privileges, tracks user approvals, and provides audit-ready reports. This not only saves time but at the same time improves security posture.