4 Types of Access Control: Explained with Examples & Use Cases

Access control, also known as Access Management, is the cornerstone of cybersecurity in today's enterprises. Access control determines who can access what systems, data, and assets and under what circumstances. Moreover, as digital ecosystems become increasingly dynamic and hybrid, Choosing the right access control approach isn’t optional anymore. It’s a strategic decision with real consequences for security, compliance, and efficiency and has significant ramifications for security, compliance, and operational efficiency. This blog will review the four core access control types: Discretionary, Mandatory, Role-Based, and Attribute-Based, along with examples, use cases, and how Identity Governance Administration (IGA) solutions, such as Identity Confluence, can govern and optimize these models at scale, regardless of your objectives. Access control is typically foundational in identity-first organizations, whether you are securing sensitive customer data, managing access to critical cloud infrastructure, or adhering to increasingly rigorous compliance regulations.
What Is Access Control in Cybersecurity?
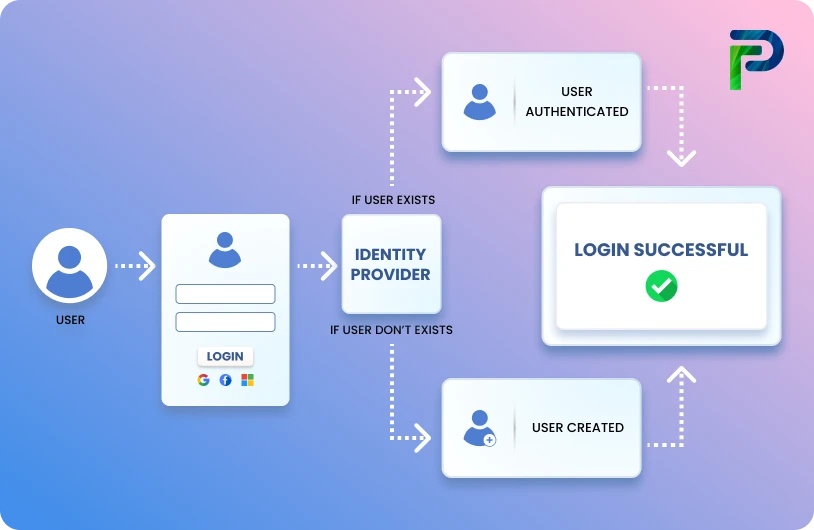
Access control is an essential security construct that specifies who can access the organization's digital and physical assets and under which conditions. It ensures that only individuals or processes that are authorized and authenticated to interact with an organization's managed assets, ensuring that sensitive information is secured and the confidentiality, integrity, and availability of enterprise environments are maintained.
Access control may be defined as a combination of identification, authentication, and authorization processes designed to grant or restrict permissions to users to align their privileges with their business role and the organization's policies. In contemporary machine-to-machine interactions, access control and user identity verification can be further augmented to include features such as biometric validation or utilization of multi-factor authentication (MFA) messages and hardware. Architecture is also enhanced by by using a policy-based access framework to define permissions logically and enforce secure, adaptive access across all environments.
Importantly, access control forms the basis for the Zero Trust security model ("never trust, always verify") and regulatory compliance with standards such as HIPAA, SOX, and ISO 27001. And by practicing least privilege, it assists in an organization's efforts to assess insider threat issues and improve operational risk management.
Access control is broadly categorised into two types:
- Physical Access Control: This includes physical access controls such as locks, biometric scanners, and key cards used as restrictions to access a physical space such as offices, data centres, or secured labs.
- Logical Access Control: This includes digital access controls such as file permissions, software restrictions, and operating system access controls to restrict access to data, applications, or network resources based on their login credentials (user levels, credentials) based on user roles. Together, these two forms of access controls create comprehensive access restrictions for both physical and cyber environments to enable modern enterprises to operate in a highly agile manner while ensuring adequate access and protection measures, including governance mechanisms.
4 Major Types of Access Control
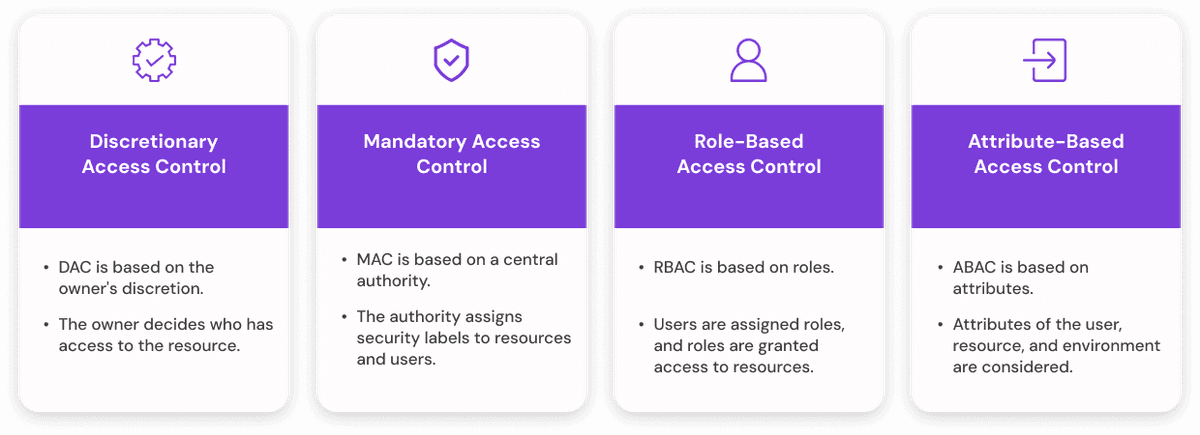
1. Discretionary Access Control (DAC)
DAC is a flexible model, where the owner of the data has total control over which users can access resources and what level of permissions they receive. They can freely add or remove users and set permissions for users at their discretion, similar to the user responsibility seen in consumer file sharing services, including Google Drive and Dropbox. While DAC allows the ability for collaboration and is active in user autonomy, DAC brings a higher risk of potentially unauthorized access to data while allowing individuals within the organization to own the permissions, as there may not be any mandatory governance follow-up with data using DAC. DAC works in environments that are highly creative or collaborative, but it should be closely monitored in organizational or enterprise settings.
2. Mandatory Access Control (MAC)
In MAC, any access decisions are based on established security labels (e.g. Confidential, Secret, Top Secret) that are assigned to both users and resources. Once the user logins they are tagged into the system with a digital (security) profile - a combination of access attributes that determines, based on the level of classification, what data they can access. Security labels must align with or match in order to grant access, making for highly controlled, traceable data flows.
Because the permissions are not adjustable (non-negotiable) and centrally controlled, MAC limits the possibility for insider threats or accidental exposures of sensitive data. The price of this inflexibility, even for a very high-trust environment, is that it is not easily adaptable to fast-paced business types of environments that require operational flexibility.
3. Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is one of the most common access models used within enterprises. It provides access based on an individual’s user role in the enterprise (e.g., HR manager, IT administrator, Sales associate, etc.). Each role has a defined set of permissions that an enterprise maps to an individual’s user account, enabling scalable management of permissions and easier auditing. From an operational standpoint, RBAC enhances efficiency and supports simplified onboarding/offboarding workflows. However, understudied RBAC governance processes can result in role explosion with resultant over-permissioning with roles.
4. Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) is a dynamic, context-aware access control model that grants users permission based on attributes such as department; job title; device type; geographic location; time of day; etc. Attributes overall represent a user's digital profile, and access is granted when user attributes meet the conditions of a policy. For instance, a doctor may not be allowed to access electronic health records except when logged in from a device issued by the hospital during working hours, which ABAC could administer in seconds. ABAC is not RBAC, which relies upon static assignments of roles. ABAC allows more nuanced, risk-intelligent, fine-grained decisions which are always contextualised.
ABAC systems are particularly valuable in cloud-native and hybrid IT environments, where users, devices, and data are constantly shifting across environments. ABAC allows for policies that apply automatically to those shifts, allowing for better security while not disrupting user productivity. ABAC policies are a form of policy enforcement, organizations create separate policies to evaluate with logical conditions based on attributes, the evaluation is continuously updated in real time. These attributes can also come from external systems like HR databases, marketing CRMs (e.g. Salesforce) or even identity provisioners. The link between the external context of the user and the internal hierarchy, adds additional semantic context as to what we want and how risk is articulated.
While ABAC has great potential, strong policy governance and oversight are needed for it to be utilized fully. When rules are defined correctly, but with conflicting attributes, organizations may grant over-permissions or, alternately, deny access. Documentation, testing, and validating ABAC are crucial.
| Model | Definition | Key Characteristics | Example Use Case |
|---|---|---|---|
| DAC | Access is granted by the data owner at their discretion | User-centric, flexible, but less secure, prone to inconsistent enforcement | A member of the group shares a folder in Google Drive with a few selected collaborators. |
| MAC | Access is enforced based on system-classified security labels | System-controlled, non-negotiable; ideal for highly classified data | Access to "Top Secret" forms of documents with military-grade levels of clearance, by user clearance. |
| RBAC | Access is assigned based on user roles within an organization | Scalable, easy to manage and audit; widely adopted in enterprise environments | HR managers access the payroll systems using pre-assigned HR roles. |
| ABAC | Access is determined by evaluating attributes (e.g., user, device, location, time) | Context-aware, flexible, supports fine-grained policy enforcement | Doctors access electronic health records from only hospital IPs while they are on duty/working. |
Other Access Control Models to Know
In addition to the four foundational models, several emerging or complementary models enhance modern access control strategies. Understanding these helps organizations adapt to evolving security needs:
- Policy-Based Access Control (PBAC): PBAC extends the principles of RBAC and ABAC by incorporating business logic and compliance policies directly into access decisions. For example, access might only be granted if a specific workflow step is completed or during a defined audit period. It’s particularly useful for highly regulated industries that require dynamic access governance.
- Risk-Adaptive Access Control (RAdAC): RAdAC takes access control a step further by integrating real-time risk signals such as threat intelligence or user behavior analytics into the decision-making process. If a user logs in from an unusual location or attempts to access sensitive data outside normal hours, RAdAC can restrict or deny access dynamically.
- Identity-Based Access Control (IBAC): This model grants access based solely on the authenticated identity of a user. It's straightforward and commonly seen in legacy systems but lacks the contextual awareness of modern models. IBAC often serves as a foundational layer that can be enhanced by adding roles or attributes.
- Access Control Lists (ACLs): At the object level, ACLs describe permissions on UNIX-like operating systems, which in this case are folders or files. Each object has a list of users or systems who can read, write, or execute that object. In smaller, scoped environments ACLs work great, as they allow precise management of resources. However, in larger environments, oversight can be tedious and cumbersome if ACLs are not centrally managed.
- Principle of Least Privilege (PoLP): Rather than a model, PoLP is a philosophy that supports all access control systems, which says the user should only have access to the resources they absolutely need to perform their job. By implementing PoLP to limit access, you can limit your exposure and reduce the operational impact of a breach and to an organization, it is good practice for compliance audits.
Real-World Use Cases by Access Control Type
It's important to recognize how each access control model operates in a real-world situation. This is crucial in considering the favorable/detrimental aspects of an access control model to determine if it is the right access control strategy for a given organization's particular needs. Here is an outline of industries/scenarios mapped against these models:
| Type | Use Case | Example |
|---|---|---|
| DAC | File sharing | Google Drive folder permissions |
| MAC | Military data | Access labeled “Classified” |
| RBAC | HR systems | Payroll access for HR team |
| ABAC | Healthcare | Access only from verified hospital IP during work hours |
These practical examples demonstrate that good model selection positively impacts security, operational efficiency, and compliance posture across diverse industries.
To Conclude
Selecting the appropriate access control model is not a one-size-fits-all process. While DAC, MAC, RBAC, and ABAC are all able to meet different security requirements, the challenge lies in getting them operational in multiple, complicated, hybrid environments. That's where Identity Governance tools such as Identity Confluence come in, allowing enterprises to define, manage, enforce, and monitor access changes dynamically, while creating consistent policy enforceability, maintaining strong audits, and are always audit-ready.If you want to see how models can be seen in a practical sense in your organization, consider scheduling a specific demo. Sometimes the best way to see access control is to actually see it.
Frequently Asked Questions (FAQs)
- What are the 3 types of access control?
The traditional core three types are Discretionary Access Control (DAC), Mandatory Access Control (MAC) and Role-Based Access Control (RBAC). Attribute-Based Access Control (ABAC) has surfaced as a fourth and is also a very valuable model. - What’s the difference between RBAC and ABAC?
Role-Based Access Control (RBAC) is associated with a user's organizational role which makes RBAC relatively static. Attribute-Based access Control (ABAC) implements access control based on real-time attributes, such as time, location, or the device being used, thus allowing for dynamic enforcement, which includes finer granularity. - Which type of access control offers the strongest security?
Due to its systematic, regulation-based rules and access granted by classification, MAC has the highest level of security and is useful for environments with highly sensitive data. - How does IGA help with access control?
IGA solutions, such as Identity Confluence, extends all access models--including RBAC, ABAC, ACL, and MAC-- by automating provisioning, performing access reviews, enforcing governance policies, and producing compliance-ready audit history and audit trails reports from a centralized dashboard while providing an update, secure, and scalable access process across both on-premise and cloud resources. - Can access control models be combined in a single enterprise environment?
Yes, most enterprises today operate in hybrid environments where multiple access control or permission models exist, including be
- RBAC for intended structured access based on pre-determined internal roles,
- ABAC for contextual and conditional-based decisions in cloud systems,
- ACLs for older and often legacy applications or databases,
- MAC for datasets that may need regulatory role or restriction (i.e., lessons learned with sensitive data such as financial, and healthcare).
- How does access control support Zero Trust architecture?
In zero trust as a concept access control is a fundamental requirement. The zero trust model states that there is no implicit trust zero trust even from within the perimeter.
- There are three unique ways that can support this within an access control context:
- ABAC policies can enforce contextual parameters of trust (i.e., time, device, location, etc.)
- RBAC is predefined access minimum for end-users
- Identity Confluence is an IGA tool that will provide continuous monitoring, policy violation detection, and real-time access reviews
- Zero Trust is more than just verifying "who" is making the access request, it is the ongoing verification of the "context" and "justification" for that access, every time.
- What’s the role of access certification in strengthening access control?
Access certification helps to ensure that access permissions stay current over time - especially after role changes, project completions, or user exits.
Key Elements:- Managers and application owners regularly review and assess who has access to what.
- Identity Confluence enables automated campaign-based access reviews at scale, which enables audit-friendly access reviews.
- Certifications ensure access continues to support the needs of the business, helps manage privilege creep which is a major risk to meeting compliance requirements.
- What are signs your access control model is failing?
Some common signs that access may be a problem include:
- Users with access to applications that they don't use any more (inactive access)
- Delays in the revocation of access upon the offboarding of a user
- Incidental role transitions, which lead to bloated roles (what we are labelled role sprawl)
- Lack of auditing ability has led to unknown approvals in known time frames
- Missing log access or inaccessible permissions have led to failed audits