SOX User Access Review: Process, Checklist & Best Practices for 2026

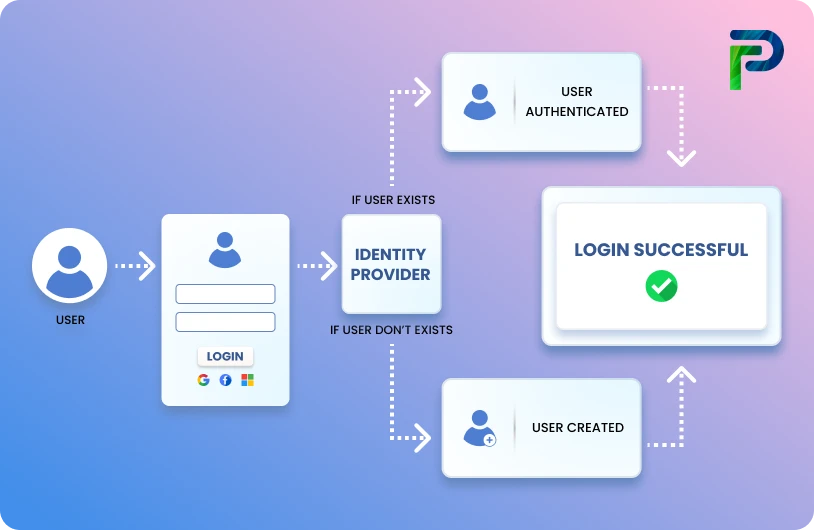
A SOX user access review enables organizations to verify continued data integrity and that only appropriate staff have new access. This guide documents the SOX user access review, including a step-by-step recommended practice and checklist which you can download to ensure that your user access reviews are audit-ready.
Businesses today are also up against increasing amounts of complexity in managing user access across multiple financial systems, while also being required to provide continual compliance and assurance to their auditors. With quarterly SOX certifications requiring documented evidence of effective access controls, organizations require not only a systematic way of accessing user permissions but design this activity to meet not only the organizations internal auditors but also the external compliance requirements to prevent unauthorized access, privilege creep, and insider threats.
Key takeaways:
- SOX reviews protect financial data integrity and reduce fraud risk
- Automation improves efficiency and audit readiness
- Quarterly reviews meet most compliance expectations
- Least privilege and SoD strengthen internal controls
What Is an SOX User Access Review?
The user access review for SOX is a formal process required by SOX Section 404 that validates who has access to financial systems and ensures those access rights are consistent with job roles and associated regulatory requirements. The Sarbanes-Oxley Act of 2002 user access reviews exist to ensure accuracy and reliability of financial reporting and to prevent financial fraud in public companies.
At its heart, identity governance is about ensuring the right people have the right access to the right resources at the right time, which is the broadest part of SOX 404 controls. The systematic review validates that user access is in line with business needs and regulatory and job responsibilities for financial systems access.
The SOX user access review process encompasses all systems that have a potential material impact on the accuracy of financial reporting, including Enterprise Resource Planning (ERP) systems (e.g., SAP, Oracle, NetSuite), general ledger and close management tools, accounts payable and accounts receivable systems, treasury and cash management, financial reporting and consolidation tools, and any customized applications that process financial transactions or hold accounting records.
Purpose:
- Required for public companies under SOX Section 404
- Ensures financial reporting systems are secure and audit-ready
- Part of internal controls for preventing fraud and data breaches
Section 404 requires management to develop and maintain sufficient internal controls over financial reporting, perform an assessment of the effectiveness of those controls annually, and provide attestation in its annual reports. User access reviews are a central component of security controls that provide critical detective controls to identify who has continued access to financial data. User access reviews provide a source of evidence to external auditors regarding management's commitment to maintaining effective controls throughout the year.
The user access review requirements in SOX require organizations to address four basic questions:
- Who has access to financial system information?
- What access rights do they have?
- Why do they need that access as part of their job?
- When were they last validated and by whom?
Organizations that are unable to answer those four questions face audit findings that could represent a potentially material weakness related to internal controls.
Why Are SOX User Access Reviews Important?
Prevent unauthorized changes to financial data
SOX user access reviews are the first line of defence to identify and prevent financial data manipulation, fraud, and misuse of the system. Financial systems contain extremely sensitive information, such as revenue, expenses, assets, and cash flows that drive market valuations. Without access review controls in place, organizations could potentially experience privilege abuse, misconfigurations, and fraudulent entries.
A good case in point is the ArthroCare fraud that occurred during the 2005-2009 timeframe. In that case, the senior executives exploited weak segregation of duties, insufficient reviews, and poor oversight to commit accounting fraud, which would artificially inflate revenue through improper "channel stuffing" with distributors. The internal controls and user access reviews enabled users to share admin credentials and work without oversight, allowing multiple fraudulent transactions to go undetected. The aftereffects were enormous: a $30 million fine to settle the DOJ investigation, executives sentenced to up to 20 years in prison , and shareholders lost hundreds of millions of dollars as a result of a $750 million securities fraud scheme leading to PCAOB disciplinary actions against auditors who failed to detect the issues.
Today, organizations need to be aware of the risks of not only intentionally committing fraud but also making accidental data changes and privilege escalation attacks, both of which can lead to significant damages to the corporation. These risks can be mitigated through SOX user access reviews by enforcing segregation of duties, confirming that only legitimate users have access to financial systems, adequately auditing and keeping reviews on file, etc. SOX user access reviews not only fulfill compliance requirements but can add confidence in financial reports and maintain integrity in an organization for the long term.
Support SOX compliance by providing strong internal controls
Section 404 requires firms to assess their internal controls over financial reporting, and user access reviews, as some of the base-level detective controls, show ongoing monitoring and validation of where users and privileged users can go. SOX user access review audits tangible evidence to external auditors that organizations maintain systematic oversight of financial systems, demonstrating their ongoing compliance with SOX.
Typically, a control environment includes three types of controls: preventive controls that stop problems before they happen, detective controls that recognize issues after they have happened, and corrective controls that fix identified problems. User access reviews serve both a detective control function and further support a preventive control function to enforce system access without identifying a fixation issue when potentially inappropriate access has been terminated before causing harm. Recent data through Graham Mudgway at Gartner tells us that 30 per cent of data breaches are a result of insider events, and that 63 per cent of those were a result of intentional errors or careless mistakes. User access reviews prove to be an important last line of defence to ensure access in those areas is performing as intended. So, while the common-mode failures will not lie just with insider threats, they do need to be considered as one of the common failure types.
Auditors assess SOX user access reviews from several perspectives: design effectiveness, whether the procedures sufficiently address risks; operational effectiveness, whether controls were operating reliably over the year; and adequate documentation, whether there is sufficient evidence to support the auditor's control conclusions.
Reduce security risks like privilege creep and insider threats
Privilege creep represents one of the most pervasive security risks in modern enterprises, occurring when employees accumulate access permissions over time without corresponding removal of previous access rights. This progressive accumulation of rights creates security vulnerabilities that can remain undetected without proper oversight. Research indicates that most organizations have employees who retain inappropriate access beyond their role requirements, while many former employees continue to maintain access to systems after termination.
The phenomenon accelerates in dynamic business environments where employees frequently change roles, take on temporary assignments, or receive emergency access for critical business needs. Without systematic SOX user access review best practices, these temporary access grants become permanent, creating a growing inventory of inappropriate permissions that expand the attack surface for both external threats and insider misuse.
Regular SOX reviews identify and remove unnecessary privileges, reducing the attack surface while maintaining necessary business functionality through proper SOX user access review process implementation.
Maintain data integrity for accurate financial reporting
The accuracy of financial reporting relies on data integrity throughout the entire information processing chain, from the initial transaction capture to the final preparation of statements. User access reviews support data integrity by limiting and controlling access to user accounts to only authorized users and ensuring that data may only be changed by those authorized with a change authority. This is vital because the user access reviews limit the risk of unauthorized individuals being able to change financial data, change configuration settings within the systems, or execute processes that could affect the accuracy of financial reporting.
In accounting, data integrity can be defined in four different ways: completeness - the recording of the entire transaction; accuracy - verifying the amounts and classifications are assigned correctly; validity - ensuring the transactions represent legitimate and authorized activities of the company; and authorization - ensuring that the sequence of approval workflows are followed. If an unknown or unauthorized user acts contrary to policies and procedures, it could violate any of these four concepts of data integrity, resulting in potential material misstatements that affect investors' decisions and commitment in compliance with regulations.
User access reviews provide corporate governance in the SOX environment to help maintaining the integrity of these data flows and essentially, the foundation of reliable financial statements that users of capital markets, regulatory agencies, and owners depend on.
SOX User Access Review vs General Access Review
Both processes provide verification of user permissions; SOX reviews are focused on financial systems and SOX compliance, while general access reviews encompass more IT resources as a whole. Understanding the variance to apply appropriate rigour as well as documenting a lot of what we do are critical for regulatory compliance.
Comparison Table:
| Feature | SOX User Access Review | General Access Review |
|---|---|---|
| Scope | Financial systems only | All IT systems |
| Compliance Tie | SOX Section 404 | Varies by org |
| Frequency | Quarterly recommended | Quarterly or annual |
| Controls Tested | SoD, least privilege | General access rights |
SOX reviews need to be an additional level of review due to their effect on the accuracy of financial reporting and the potential for failure of regulatory compliance obligations. Documentation requirements for SOX reviews are also beyond that of general IT reviews, requiring documented policies, documented "formal" procedures, documented evidence of management review, and complete documentation of the audit trail to substantiate that the review occurred and was thorough and effective.
Regulatory expectations regarding SOX user access review requirements change frequently but include specific segregation of duties tests to avoid conflicting combinations of access. They also require least privilege validation to ensure users have the least privileges necessary for their role. Business justification documentation for all access grants is also required, along with management certification that the review has been properly conducted, complete, and accurate.
Frequency requirements also differ greatly. General access reviews may only occur once a year or less. On the other hand, SOX reviews are typically aligned with quarterly reporting cycles to support Section 302 certifications. Many organizations have adopted quarterly SOX reviews in order to be in continuous compliance and to reduce the burden of the year-end audit.
SOX User Access Review Process
A structured process ensures consistent, audit-ready compliance. Organizations that follow systematic SOX user access review process approaches demonstrate greater control effectiveness and experience fewer audit findings than those relying on ad hoc procedures.
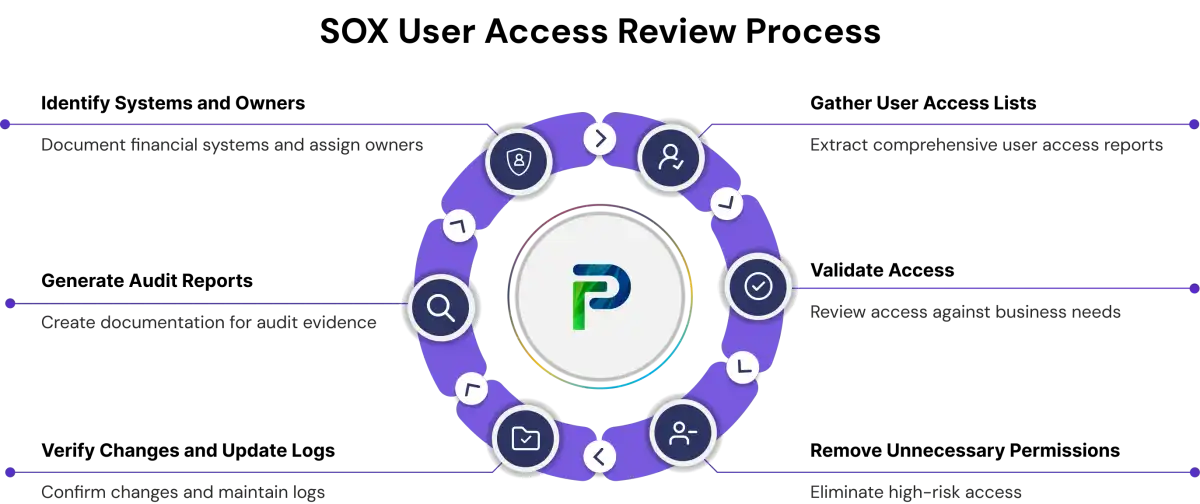
- Identify in-scope systems and owners- Identify and document every financial information system, application, and database that processes, stores, or transmits data impacting financial reporting. This explicitly includes systems such as ERP and general ledger systems, but also includes systems like procurement planning systems, treasury management systems, budgeting and forecasting systems, and the whole range of custom systems and applications that may have the potential to affect a financial report. Appoint system owners on a system-by-system basis, who will have the experienced business knowledge necessary to make access decisions while adhering to segregation of duties. Implement a formal periodic review schedule to assure on-going active review and to preempt any compliance insufficiencies.
- Gather current user access lists - Obtain thorough user access reports from all in-scope systems, to be comprehensive reports must address both active and inactive accounts. Identify the permission level for all the accounts, roles assigned to the accounts, last time the accounts logged in, and accounts with privileged access. The organizations should use an automated process to scan the accounts, generate report(s), and monitor access and their inheritance to user accounts. Leverage automation as it will increase efficiency and output. The organizations report experiencing difficulty with this process due to disparate systems with different access models, inconsistent reporting, and lack of center managed identity functionality.
- Validate access with system owners - System owners review access lists against current organizational charts, job descriptions, and business needs to validate the legitimate access needs of each user. This validation should include considering segregation of duties to ensure that no single individual has conflicting permissions that might otherwise enable them to execute a fraudulent act. Document business justifications for granting access in all instances, especially where there are elevated privileges or cross-functional access.
- Remove unnecessary or high-risk permissions - Taking access away from people who are separated, relinquished their duties, transferred, or have too much privilege to allow them to violate arrangements around least privilege. Following the steps on removing access takes away future access; future access we are trying to prevent from privilege creep (i.e. collecting rights). Take care to note generic accounts, shared credentials, and inactive accounts that might not have been evaluated in the past. Ensure that all changes to access privilege fall under the formal and approved change management policy and process to make sure access changes are approved, tested, and documented.
- Verify changes and update logs - Verify that all access changes are accurately reflected in the target systems, and keep a complete log of all access changes showing timestamps, responsible individual, and business justification. This step often identifies gaps in implementation where access changes approved by management were not implemented accurately, not implemented over a period of time, or implemented in an inadequate manner because of limitations of existing systems.
- Generate and store audit reports - Developing complete documentation that captures the review process, findings, remediation activities, and final access states for audit evidence. Reports should demonstrate management oversight, exception handling, and evidence of follow-up for identified issues. All access changes should have immutable records to establish an audit trail that, if properly managed, will satisfy internal and external auditors for periodic compliance reviews.
Types of SOX User Access Reviews
Distinct review types deliver distinct compliance purposes and risk scenarios, and organizations are able to adapt their strategy to their requirements and obligations.
- Periodic Reviews (quarterly, semi-annual, annual) - Scheduled reviews that assess all user access in a systematic fashion across time periods. Quarterly reviews align with SOX Section 302 certification requirements and provide the latest perspective on the appropriateness of access. Organizations engaged in quarterly reviews have reported fewer access-related security incidents than organizations that only take an annual review approach.
- Event-Driven Reviews (role change, termination) - Triggered reviews that happen when employees change positions or departments or leave the organization altogether. These reviews, which prevent orphaned accounts that expose security risks and ensure appropriate access rights as job responsibilities change.
- Ad-Hoc / Targeted Reviews (suspected fraud, failed audit findings) - These reviews are investigative in nature and focus on specific users, systems, or participants in distressed security incidents. These types of review measures allow for a fast turnaround on compliance issues and demonstrate management’s commitment to act quickly on known problems.
Role-Based Reviews
Assesses whether the access privileges assigned to the predefined roles are appropriate to the job functions and segregation of duties. This approach scales easily for larger organizations by assessing access profiles rather than on a user-by-user basis, while helping to ensure that role definitions are current and sensible from a business perspective.
Role-based reviews Assess the design and assignment of access roles, check that role definitions have the appropriate segregation of duties principles included, check the roles only have the required permissions required for the job functions, and check the assigned roles align with the real organizational structure and that there was periodic recertification for role appropriateness.
Emergency and Break-Glass Access Controls
SOX compliance requires special attention to emergency access procedures that bypass normal approval workflows. Organizations must implement:
- Documented break-glass procedures with specific approval requirements
- Real-time monitoring and alerting for emergency access activation
- Mandatory review and approval of all break-glass access within 24 hours
- Quarterly recertification of emergency access account inventories
- Automated revocation of temporary emergency privileges after predefined periods
Emergency access is a significant compliance risk because it lets you bypass normal segregation of duties controls. Proper documentation and monitoring of emergency access prompts make sure these needed exceptions do not become compliance vulnerabilities.
Quick Checklist for SOX Access Reviews
Use this SOX user access review checklist to streamline your review process and ensure comprehensive coverage of all critical elements.
- Document critical systems & owners
- Compile the current access list
- Review access needs per user
- Remove excess or outdated permissions
- Verify changes & log them
- Publish the review report
- Repeat at set intervals
This user access review template for Sox should be a useful resource for review coordinators and system owners with clear milestones and deliverables and valuable in providing an organized approach with similar operational outcomes across the multi-year review process. Organizations that use prepared checklist templates have reported improvements in review outcomes, have minimized mistakes from oversight and are much better prepared for audits than organizations who use informal processes.
Industry-Specific SOX User Access Review Requirements
Financial Services and Banking
Financial institutions face dual regulatory pressure from SOX and banking regulations like the Federal Financial Institutions Examination Council (FFIEC) guidelines. Banks must implement enhanced controls for core banking systems, trading platforms, and customer data repositories. Key considerations include real-time monitoring of privileged access to trading systems, segregation between front-office and back-office access, and quarterly reviews of wire transfer authorization capabilities.
Healthcare Organizations
Healthcare companies must align SOX user access reviews with HIPAA requirements, creating overlapping compliance obligations. Reviews must address access to financial systems containing protected health information (PHI), ensuring proper authorization workflows for billing systems, and maintaining audit trails that satisfy both SOX auditors and HHS compliance officers.
Technology and SaaS Companies
Technology companies face unique challenges with developer access to production systems that process financial data. SOX reviews must address code deployment privileges, database administration access, and API keys that could impact revenue recognition systems. Automated access reviews become critical for managing developer permissions across multiple environments.
Best Practices for SOX Access Reviews
Follow these SOX user access review best practices to improve efficiency, accuracy, and audit success based on industry leading approaches and regulatory guidance.
Document a formal SOX access review policy – Adopt written procedures detailing the frequency of review, the scope, the responsibilities of the reviewer, steps for escalation to management, and documentation requirements. Policy documentation should also include management review, exception notifications, and how the access review fits into the overall internal controls. Organizations with formal policies demonstrate a higher level of control maturity and fewer audit findings than organizations without formal policies or processes.
Automate reviews for speed and accuracy – Use the identity governance process to automate access discovery, review workflow, and reporting. Automating reviews will lead to fewer manual errors, quicker realizations in determining your compliance, and continuous and continual monitoring, rather than one review at a point in time. Moving forward with automated review processes leads to significant reductions of review processes while allowing for accuracy and audit preparedness.
Enforce SoD and least privilege – Implement segregation of duties controls to preclude combinations of conflicting access roles; for example, accounts payable has the ability to create vendors and approve payment, or a user can post a journal entry and then approve the entry without review. Enforce least privilege access by granting only access necessary for job functions. Document any business justification for these SoD violations and put compensating controls in place where segregation of duties is not possible.
Maintain thorough documentation for audits – It is vital to keep documentation for review activities, findings, remediating activities and management approvals. Documentation should show the rigor and completion of the SOX user access review process and should contain evidence of management oversight, resolution of exceptions, and actions taken for follow-up. Lack of appropriate documentation continues to be one of the most common audit findings associated with user access controls.
Educate reviewers on compliance requirements – make sure system owners and reviewers know SOX compliance requirements, segregation of duties principles, and the importance of thoroughly validating access for regulatory compliance. Training should include the business risk of improper access, documentation methods, and escalation processes for complicated access situations.
Challenges & Pitfalls in SOX User Access Reviews
Common obstacles can undermine compliance if not properly prevented. By understanding these challenges, organizations are able to take affirmative action, improve review effectiveness, and create a proactive culture.
Resource hungry manual reviews - Manual processes are expensive and can result in operating errors and mistakes that impact review quality and completeness. Organizations performing manual reviews often have challenges maintaining consistency in different review cycles , and struggle to remain scalable as business complexity increases, and demonstrate a systematic approach to auditors.
Tiered disparate systems - Financial operations are using multiple systems with different access models, authentication methods, and reporting capabilities. Not having centralized visibility makes it difficult to to be comprehensive in SOX reviews and increases the likelihood that systems, or data that has not been incrementally compiled, are missed in the review process.
Limited view into lives access - Many organizations do not know who has what access in their financial systems at any single time, and only rely on past approximations that need not reflect a snapshot of the current state. This blind spot about access, impacts the ability to assess risk, remediate in a timely way, and demonstrate continuous monitoring capabilities that are increasingly required by auditors.
Irregularity in reviews - Irregular or delayed reviews create compliance gaps while also allowing inappropriate access to persist longer than necessary. Organizations that conduct quarterly reviews report access-related incidents at a fraction of the rate as organizations that do them annually and/or inconsistently.
Neglecting shared accounts - Generic, service, or shared accounts typically fall outside of the traditional review process, but the risk associated with them is considerable due to broad access and the lack of individual accountability. Shared accounts require special treatment and additional controls including periodic password changes and usage monitoring and higher thresholds for approval.
Tools & Templates for SOX User Access Reviews
Using automation tools and pre-built templates has made compliance tasks easier and with higher accuracy and audit readiness. Modern identity governance capabilities take poor, manual processes and automate them into organized workflows with audit-ready visibility and control. Identity Confluence has all of the requirements for SOX compliance and, using an AI-based platform, enables and automates SOX user access reviews and provides end-to-end automated compliance capabilities. Tech Prescient’s Identity Confluence allows for on-demand visibility throughout the entire approval process across all financial applications, automated review workflow, automatic documentation from the legit reviewer at the snap of the fingers and continuous compliance monitoring for audit drift.
"With TechPrescient, automate every step of the SOX access review process from gathering user lists to generating audit-ready reports in one platform."
The platform solves common SOX review challenges via automated data extraction from hundreds of applications and systems, smart segregation of duties detection and alerts, policy-based access certification with customized approval workflows, real-time compliance dashboards showing review status and findings, and complete audit trails with evidence management capabilities.
Specific SOX features include automated quarterly review campaigns, segregation of duties rule configuration and monitoring, risk-based access prioritization that focuses attention on high-risk users and permissions, integration with HR systems to automate lifecycle management, and customizable reporting templates appeasing auditor requirements. Organizations leveraging Identity Confluence are reporting quicker onboarding, fewer IT support tickets, and significant improvements in audit efficiency and effectiveness.
SOX User Access Review Risk Assessment Framework
Effective SOX user access reviews require risk-based prioritization to focus efforts on the highest-impact areas. Use this framework to assess and categorize access risks:
Critical Risk (Quarterly Review Required):
- Administrative access to ERP systems (SAP, Oracle, NetSuite)
- Financial reporting and consolidation system access
- Treasury and cash management platform privileges
- Database administrator rights to financial databases
High Risk (Semi-Annual Review):
- Accounts payable and receivable system access
- Procurement and vendor management platforms
- Budget and forecasting application permissions
- Financial analytics and reporting tool access
Medium Risk (Annual Review):
- Read-only access to financial dashboards
- Standard user permissions in financial systems
- Temporary project-based access grants
- Service account permissions with limited scope
This risk-based approach ensures compliance resources focus on areas with the greatest potential impact on financial reporting accuracy and regulatory compliance.
Final Thoughts
In 2025, SOX user access reviews are essential for compliance, security, and audit readiness. Automation makes them faster, more accurate, and easier to maintain year-round.
The regulatory landscape continues evolving with increased expectations for real-time monitoring, automated controls, and continuous compliance demonstration. Organizations that continue relying on manual processes face mounting risks from regulatory scrutiny, operational inefficiency, security vulnerabilities, and competitive disadvantage in an increasingly digital business environment.
Leading organizations recognize that effective SOX user access review process implementation extends beyond mere compliance to provide strategic value through improved security posture, operational efficiency, and risk management capabilities.
Modern identity governance platforms like Tech Prescient’s Identity Confluence enable this transformation by providing the automation, visibility, and controls necessary to turn compliance requirements into competitive advantages.
Want to see how automation can cut review time significantly?
Frequently Asked Questions (FAQs)
1. What exactly is a SOX user access review?
A structured audit examining who has access to financial systems and what actions they can perform. These reviews verify proper segregation of duties, enforce least privilege, and prevent unauthorized access to financial data, directly supporting SOX compliance requirements for maintaining effective internal controls over financial reporting.2. How often should reviews be performed?
At a minimum, quarterly, with more frequent reviews for high-risk systems. Critical ERP components often require monthly reviews, while systems handling sensitive financial data may need bi-weekly monitoring. Additionally, trigger-based reviews should occur after major organizational changes like mergers, restructuring, or system implementations that could impact access controls.3. What's the difference between SOX and general access reviews?
SOX reviews target financial systems directly impacting financial reporting, require stringent documentation for external auditors, and focus heavily on segregation of duties. General reviews typically cover broader IT infrastructure, follow less rigorous documentation standards, and prioritize security rather than financial control objectives. SOX reviews carry regulatory consequences for non-compliance, including potential fines and executive liability.4. Can I automate access reviews?
Yes, through Identity Governance and Administration (IGA) tools that centralize user management, automate workflows, and maintain audit trails. These platforms can automatically identify segregation of duties conflicts, detect dormant accounts, flag excessive permissions, and generate compliance reports, reducing the 40+ hours typically spent on manual reviews by up to 75%.5. Which is better: manual or automated SOX reviews?
Automated reviews consistently outperform manual approaches by reducing review cycles from weeks to days, eliminating human error, analyzing all accounts rather than samples, and providing consistent, timestamped evidence. They enable continuous monitoring between formal reviews and generate real-time compliance metrics that give stakeholders visibility into control effectiveness before formal audit periods.6. What happens if a review fails an audit?
Immediately remediate by removing inappropriate access, enforcing proper segregation of duties, and documenting all actions. Conduct root cause analysis to identify control weaknesses, implement preventive measures like improved provisioning workflows, and develop a formal management response outlining remediation steps and timelines. A follow-up review should verify the effectiveness of corrective actions before the next audit cycle.