What Is Session Hijacking?

Session Hijacking (TCP hijacking) occurs when attackers take control of a legitimate user’s active web session by capturing the session’s unique ID. Using that ID, attackers can impersonate the user to access sensitive information or perform actions on the user’s behalf, undermining session integrity and exposing personal and organizational data to serious risk.
After a session is compromised, the attacker can interact with the server without reauthenticating. Because the hijacked session was already validated, the attacker inherits the same permissions and access level as the original user for as long as the session remains active.
According to research by SpyCloud, session cookie theft via adversary-in-the-middle (AiTM) attacks accounts for about 15% of phishing attacks. With more people working remotely and using cloud apps, the risk is only growing. In this blog, let’s understand how session hijacking works, the common types of attacks, and what you can do to stay protected.
Key Takeaways:
- Learn how session hijacking lets attackers steal or predict session IDs to impersonate users.
- Understand the three main stages of a session hijacking attack from login to takeover.
- Explore common attack methods like sidejacking, XSS, session fixation, and token theft.
- Discover effective ways to detect and prevent session hijacking for developers, organizations, and users.
- See real-world examples that reveal how weak session management can lead to major breaches.
What is a Session?
A session is a short-lived, authenticated interaction that ties a user’s browser to a web server. It begins when the user signs in and ends when they sign out or when a configured inactivity window elapses. When a session ends, any user-specific data stored in the server’s allocated memory should be cleared to ensure no residual information is accessible.
To track a session, the server issues a session identifier, a long, randomly generated alphanumeric string that acts as a communication token between the client and the server. These identifiers are usually stored in cookies, embedded within URLs, or included as hidden fields in web forms. Because HTTP itself does not preserve state, the session ID is what lets the server recognize the same user across multiple pages and maintain things like authentication status and application state.
Secure session management is critical. Treat session IDs like secrets: deliver them over encrypted channels (HTTPS), store them with safe cookie attributes (e.g., Secure, HttpOnly, SameSite), set appropriate, short expiry times, and ensure server-side cleanup on termination. Proper handling of session lifecycle and storage reduces the risk that these tokens can be intercepted or reused.
Now that we understand what a session is and how it’s maintained, let’s explore how attackers can exploit sessions to hijack user access and evade security controls.
How Session Hijacking Works
Session hijacking is a cyberattack where an attacker takes over a user’s active web session to impersonate them and access their account. This happens when the attacker steals or predicts the session ID, a unique identifier that keeps the user logged in. Once they get hold of it, they can perform actions as if they were the legitimate user.
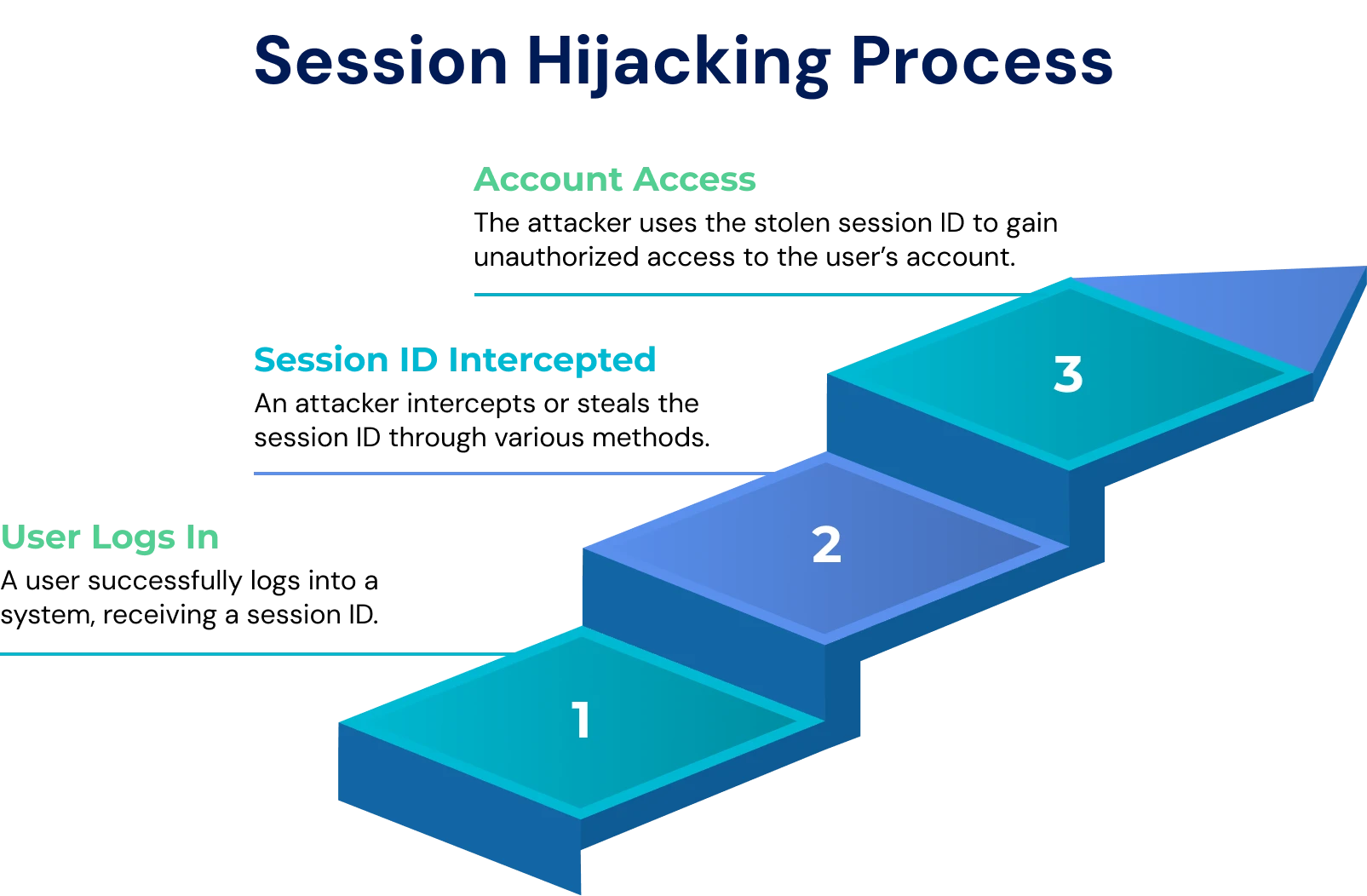
Below is a step-by-step walkthrough of how session hijacking unfolds, beginning with how a legitimate session is created so you can see exactly where attackers can intervene.
Session Hijacking Process Explained
Step 1: Establishing the Legitimate Session
When a user logs into a website or web application, the server creates a new session and generates a unique session token. The browser stores this token and automatically includes it with every request to the server. As long as the token remains valid, the server identifies the user as authenticated, allowing smooth and uninterrupted interaction without repeated logins.
Step 2: How Attackers Obtain the Session ID
Attackers use several techniques to steal or predict valid session tokens. Common methods include:
-
Session sniffing or sidejacking: One common application layer session hijacking technique is for attackers to deploy network sniffers, such as Wireshark, or use proxy tools like OWASP Zed to capture session data in transit between the client and the server. By extracting the session token from that intercepted traffic, they can hijack the session and impersonate the user.
-
Predictable session token ID: When websites generate session tokens using simple or guessable patterns, attackers can predict or calculate these IDs and gain unauthorized access to user accounts.
-
Man-in-the-Browser: This attack uses a Trojan or similar malware that infects the user’s browser. Once active, it waits for the victim to visit specific websites and can secretly change transactions or capture session data, making the activity look genuine.
-
Cross-Site Scripting (XSS): Attackers exploit weak points in a website to inject malicious scripts. When other users open those pages, the scripts run automatically and can steal session IDs or sensitive information.
-
Session sidejacking: In this type of attack, hackers intercept session data while it’s being sent over the network, especially if the connection isn’t properly encrypted, allowing them to hijack the session.
-
Session fixation: Attackers trick users into logging in with a session ID that the attacker already knows. Once the victim logs in, the attacker can use that same session ID to take control of the account.
-
Malware or infostealers: These are malicious programs installed on a device that collect stored cookies, session tokens, or fingerprints and send them to attackers, helping them take over user sessions.
Each of these methods allows the attacker to obtain a valid token that the server still trusts.
Step 3: Reusing the Token to Take Over the Session
Once an attacker possesses a valid session ID, they can impersonate the legitimate user by sending requests to the server that include the stolen token. These requests appear authentic because the session ID is valid. Attackers often use anti-detect browsers or session replay tools to mimic the victim’s device and environment. This gives them full access to the account, enabling them to perform actions such as viewing sensitive data, transferring funds, or spreading attacks across connected systems. The hijacked session usually ends when the token expires, the user logs out, or the server detects and invalidates the compromised token.
Session hijacking is especially attractive in high-traffic environments because many active sessions give attackers more targets and help them blend into normal activity. This abundance of simultaneous sessions increases the chances of a successful capture and can make the attack harder to spot.
Session hijacking remains one of the most effective ways to bypass authentication, even when MFA is in place. Understanding how these attacks unfold helps organizations identify weak points in their session management practices and strengthen defenses before an attacker can exploit them.
Real-World Session Hijacking Examples
Session hijacking is not just a theoretical threat; it has repeatedly made headlines across industries, from video conferencing to cloud collaboration tools. These incidents show how small oversights in session management can open doors to large-scale breaches, data theft, and reputational loss. Below are a few real-world cases that highlight the serious impact of weak session controls.
Example 1: Zoom Meeting Session Theft (Sidejacking)
During the remote work surge, attackers exploited weak meeting configurations and token-based links to infiltrate private video sessions. By intercepting or guessing session tokens, they joined confidential meetings and disrupted live discussions. The fallout included privacy concerns and reputational damage, prompting vendors to introduce mandatory passwords, waiting rooms, and better access controls.
Key takeaway: Even a single unsecured meeting link can expose an entire communication channel.
Example 2: GitLab OAuth Session Exposure
A major code hosting platform once leaked session tokens through URLs and used long-lived tokens without expiry. These tokens could be easily harvested from browser histories, logs, or shared links, giving attackers continuous access to repositories and CI pipelines. The company later redesigned its token management process, enforcing expiration and secure storage.
Key takeaway: Exposing tokens in URLs or logs gives attackers an easy backdoor into critical systems.
Example 3: Cloud App Takeover via Phishing Proxy (Adversary in the Middle)
In several recent breaches, phishing proxies were deployed between users and legitimate cloud services. These proxies intercepted real-time logins and captured active session cookies and authentication tokens, effectively bypassing MFA. With stolen tokens, attackers gained full account access and moved laterally across enterprise environments.
Key takeaway: MFA alone cannot stop Adversary in the Middle attacks; session token protection is equally vital.
Together, these examples reveal how weak session practices, even in well-established platforms, can lead to massive exploitation. Strengthening token management and real-time monitoring remains essential for preventing such breaches.
How to Detect and Prevent Session Hijacking
Protecting against session hijacking requires a coordinated effort between developers, organizations, and users. While attackers continually evolve their tactics, implementing strong encryption, disciplined session management, and real-time monitoring can drastically reduce risk. Below are key practices tailored for each group that plays a role in maintaining session security.
1. For Developers
Developers are the first line of defense against session hijacking. Secure coding and session handling practices ensure attackers can’t easily intercept or reuse tokens.
-
Use HTTPS and enforce HSTS: Encrypt all data exchanges with TLS to prevent session sniffing and enforce HSTS to ensure browsers always connect securely.
-
Regenerate session IDs on login: Create new session IDs after each authentication event or privilege change to prevent fixation attacks.
-
Set cookies with Secure, HttpOnly, and SameSite=Strict: Secure cookies prevent client-side scripts from accessing tokens and limit cross-site request risks.
-
Implement session timeouts and activity monitoring: End idle sessions automatically and track unusual activity patterns, such as unexpected IP or device changes.
-
Keep software and security tools up to date: Install reputable anti-malware or endpoint protection and apply updates regularly so devices and servers are less likely to be compromised by Trojans that can steal session tokens.
2. For Organizations
Organizations must build layered defenses that combine authentication, visibility, and proactive response.
-
Enable MFA and adaptive authentication: Add extra verification steps, especially for sensitive systems, and use adaptive policies that challenge suspicious behavior.
-
Monitor anomalies: Keep an eye on logins from new locations, devices, or multiple active sessions under one account. These may indicate session reuse.
-
Conduct regular penetration tests: Simulate attacks to uncover weak points in session management and validate that security patches and controls are effective.
-
Be cautious of phishing and scam links: Attackers often send deceptive emails with malicious links designed to install malware or redirect users to fake login pages. Always verify the sender before clicking any link, as these scams can lead to session token theft or compromise.
3. For Users
Users also play a critical role in preventing hijacks through safe online habits and security awareness.
-
Avoid public Wi-Fi without VPN: Public networks can expose session cookies to sniffing. A VPN encrypts traffic and hides user activity.
-
Log out after use: Always end sessions manually, especially on shared or public devices, to prevent others from reusing your credentials.
-
Keep browsers and antivirus updated: Regular updates patch known vulnerabilities and protect against malware that steals tokens or manipulates browsers.
By following these combined measures, developers can build secure systems, organizations can detect and stop hijacking attempts in real time, and users can maintain safer browsing habits. Together, these efforts form a strong defense against one of the most persistent web security threats.
Session Hijacking vs. Spoofing
The key distinction between session hijacking and spoofing lies in how and when the attack occurs. Session hijacking happens when an attacker takes control of an already active user session, while spoofing involves creating a fake identity or falsified communication from the start to trick a user or system into believing it’s legitimate.
Here are a few key differences to note before looking at them side by side:
-
Session hijacking happens after authentication, when an attacker steals or reuses a valid session token to take over a user’s active session.
-
Spoofing happens before authentication, where attackers falsify information like IP addresses, credentials, or device identities to trick systems into trusting them.
-
Both can lead to data theft or unauthorized access but require different mitigation strategies.
Key Differences Between Session Hijacking and Spoofing
| Sr. No | Aspect | Session Hijacking | Spoofing |
|---|---|---|---|
| 1 | Timing | Occurs after the user has logged in and an active session is in progress. | Occurs before a session is created as the user does not need to be logged in. |
| 2 | Execution | The attacker captures a valid session ID using sniffing, XSS, or malware and uses it to take control of the ongoing session. | The attacker forges identity or source details such as IP address, email, or website to make their communication appear legitimate. |
| 3 | Goal | To impersonate the authenticated user and carry out actions within their existing session. | To deceive the user or system into trusting the attacker and revealing access credentials or sensitive data. |
| 4 | User Awareness | The real user might notice unexpected logouts, errors, or unusual activity in their account. | The user usually remains unaware since they interact normally with what seems like a trusted interface. |
Incident Response Checklist
When a session hijacking incident is suspected, an immediate and structured response is critical. The goal is to contain the breach, secure affected accounts, and understand how the compromise occurred. Below is a step-by-step checklist that can help teams act quickly and effectively.
1. Invalidate all active session tokens
Begin by invalidating all active or suspected session tokens on the server side. This ensures that any attacker currently using a stolen session ID is instantly logged out. It also prevents reentry into the compromised session, effectively cutting off unauthorized access.
2. Reset user credentials and revoke persistent tokens
Force password resets for all affected accounts and revoke any persistent authentication tokens such as “remember me” sessions or API keys. This helps ensure that stolen credentials or tokens cannot be reused to regain access.
3. Collect and preserve forensic data
Gather server logs, IP addresses, browser fingerprints, and session history for forensic investigation. This data provides crucial insights into how the attack was carried out and helps trace the source or methods used by the attacker.
4. Identify and fix the root cause
Determine the origin of the attack, whether it was caused by cross-site scripting (XSS), a man-in-the-middle (MITM) attempt, malware infection, or a server misconfiguration. Once identified, apply necessary patches or configuration fixes to close the exploited vulnerability.
5. Notify users and enforce stronger authentication
Inform impacted users about the breach in a transparent and timely manner. Encourage them to reset passwords, verify account details, and enable multi-factor authentication (MFA) for added protection against future compromises.
Final Thoughts
Session hijacking remains one of the most critical threats to online security, capable of turning a trusted session into a weaponized entry point. By exploiting weak session management and unencrypted connections, attackers can impersonate legitimate users and gain unauthorized access to sensitive data.
However, with strong encryption, secure cookie practices, MFA, and vigilant monitoring, organizations can effectively prevent these attacks. As cybersecurity evolves toward Zero Trust and adaptive authentication, proactive defense and continuous awareness are key to safeguarding digital sessions.
To see how Tech Prescient helps enterprises build secure, resilient session management systems that defend against hijacking and ensure user trust,
Frequently Asked Questions (FAQs)
1. What is session hijacking?
Session hijacking is a cyberattack where a hacker takes control of a user’s active session by stealing or guessing their session ID. Once they have the valid ID, they can impersonate the user and access sensitive data or perform actions on their behalf. It’s one of the most common threats to web apps and online accounts.2. What is the best defense against session hijacking?
The best defense is strong session management. Use HTTPS to encrypt traffic, set cookies with Secure and HttpOnly flags, and always regenerate session IDs after login or privilege changes. These steps make it harder for attackers to steal or reuse valid session tokens.3. What is the difference between session hijacking and spoofing?
Session hijacking targets an active, authenticated session, while spoofing tricks systems by faking an identity or IP address. In short, hijacking steals an existing session, and spoofing pretends to be someone else from the start.4. Does HTTPS prevent session hijacking?
HTTPS definitely helps by encrypting the communication between browser and server, protecting session cookies from being intercepted. But HTTPS alone isn’t enough; you also need MFA, secure cookie settings, and regular session regeneration for full protection.5. How can I detect session hijacking?
Keep an eye on your system logs for unusual patterns like multiple logins from different locations, unexpected IP changes, or two sessions running at once for the same account. These red flags often point to a possible session takeover attempt.5. What are the benefits of Single Sign-On?
SSO simplifies the login experience, boosts productivity, and enhances security by minimizing password fatigue. It also reduces IT helpdesk requests for password resets, helping organizations save time and operational costs.