RBAC vs ABAC: Which Access Control Model Fits Your Organization?

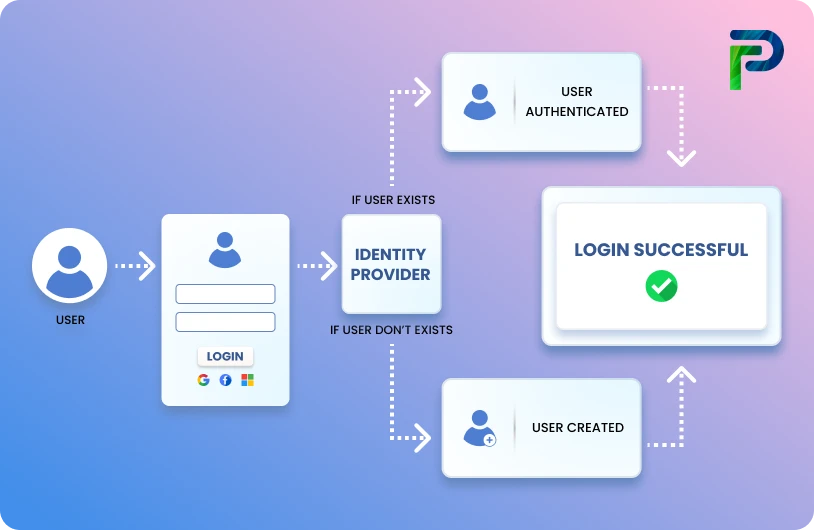
Organizations today face the challenge of securing access across a complex mix of cloud platforms, on-premises systems, remote teams, and third-party vendors. You can imagine the results when you have no clear access control strategy: overprovisioned accounts, access sprawl, compliance holes, and a constant risk of access incidents.
There are two approaches that organizations are most familiar with: Role-Based Access Control (RBAC), where permissions are granted based on a user role, and Attribute-Based Access Control (ABAC), where permissions are based on the context of the user from attributes like department, location, device type, and time. RBAC has traditional characteristics like simplicity and predictability, whereas ABAC has features that drive adaptability/flexibility and granularity. The major difference between the two approaches is the way they each grant access.
Yet, in practice, we find many enterprise organizations are transitioning to more hybrid models by leveraging the structured RBAC model with disciplinary, context-aware policies in the ABAC model to balance least privilege with the demands of Zero Trust and hybrid environments.
In this blog, we will cover RBAC vs ABAC, how use cases shine for each, and most importantly, show you whether a hybrid or single model is more appropriate for your organization.
Key Takeaways
- RBAC is role-focused and supports traditional organizations with their role and responsibilities.
- ABAC allows for the adaptability and real-time access decision based on attributes such as location, time, or device.
- RBAC and ABAC both provide the basics to enforce least privilege and identity governance.
- Hybrid access management models that include RBAC and ABAC provide the dexterity needed to accommodate sellers in modern and dynamic environments.
- The best model for your access management requirements is based on organizational scale, compliance requirements, and infrastructure complexity.
- Understanding the distinctions of these access practices ensures establishing a secure and scalable cybersecurity program.
What is Role-Based Access Control (RBAC)?
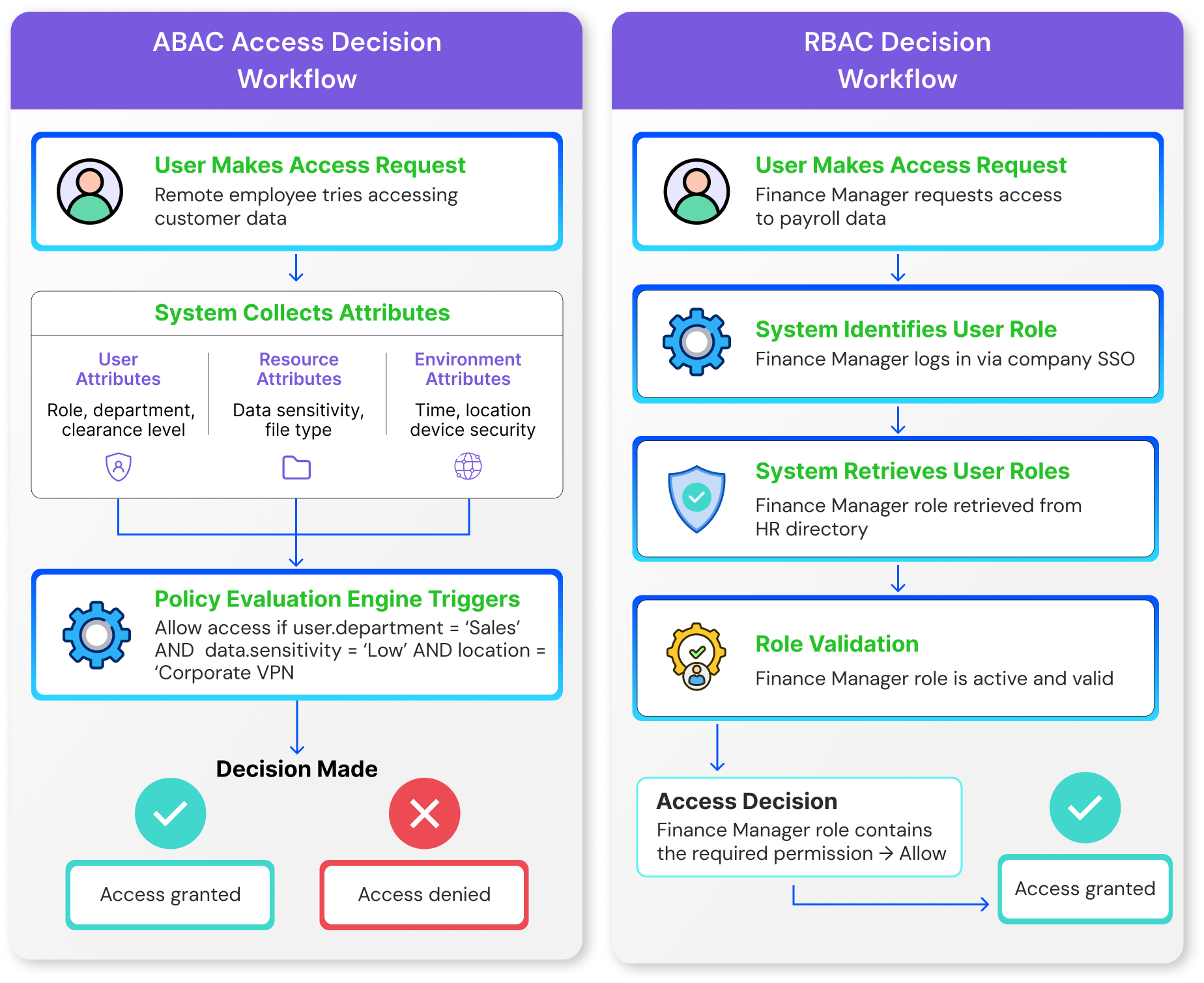
Role-Based Access Control (RBAC) is one of the most adopted approaches for governing access in enterprise environments. With RBAC, access is granted according to the user’s role in the organization, which generally corresponds with their job function. Each role includes a set of permissions that help you easily provide users access so that they can perform their jobs.
For example:
- Admin - Has full control over systems, application configurations, and user management.
- HR - Has access to employee records, payroll applications, and recruiting and hiring platforms.
- Sales - Has access to a customer relationship management (CRM) tool, sales dashboards, and customer data.
- IT Support - Has permission to troubleshoot system issues, reset user passwords, and manage help desk tickets.
This model typically works best in a structured organization with clear job responsibilities. Additionally, it can be implemented easily, audited easily, and aligns well with governance requirements like SOX, HIPAA, or GDPR.
RBAC can be complicated at scale, commonly called "role explosion." It is magnified by organizations with nuanced user needs and growth that allows for tens of thousands of roles. In practice, onboarding hundreds (or thousands) of unique roles and maintaining them becomes a problem, introducing unintuitive permissions leading to role overlap and redundancy, which can introduce more risk of over-permissioned users.
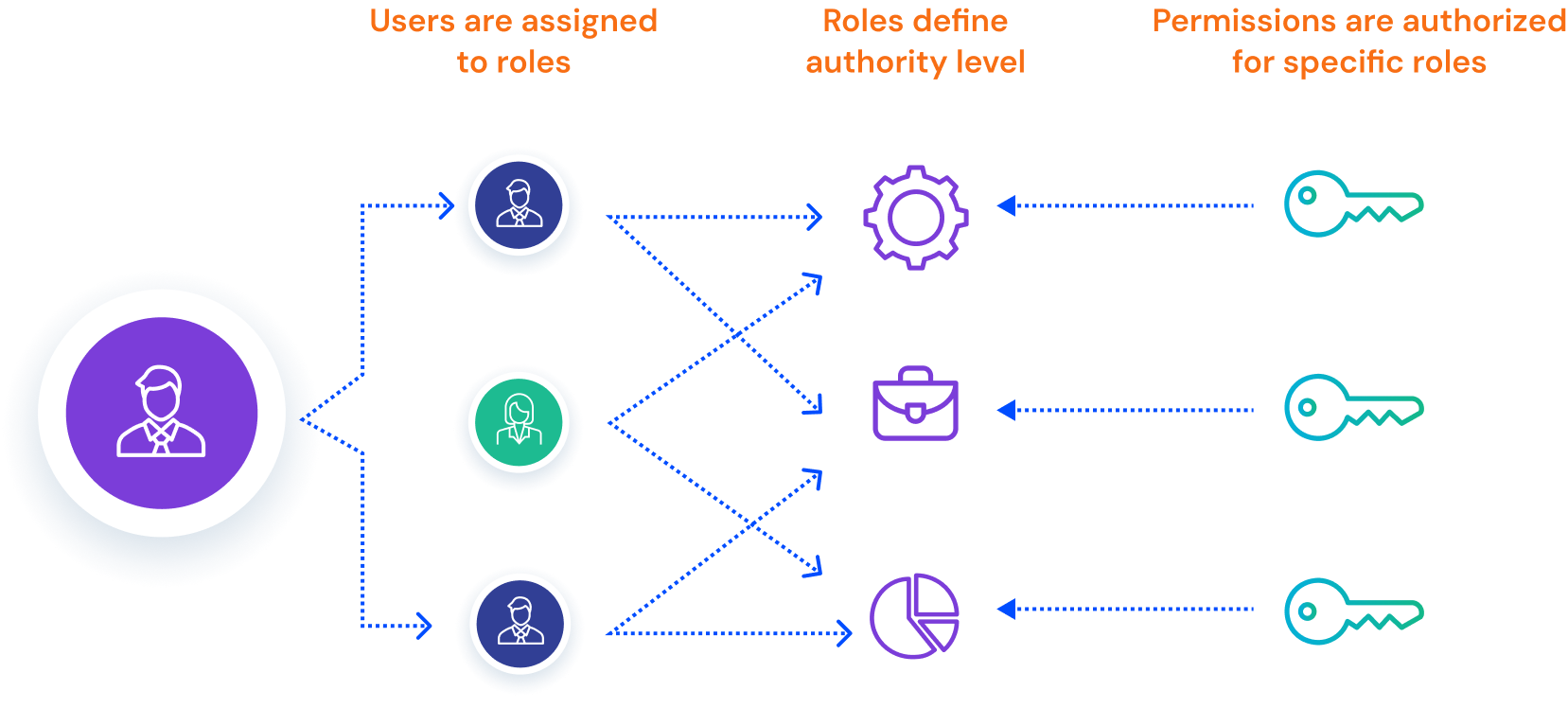
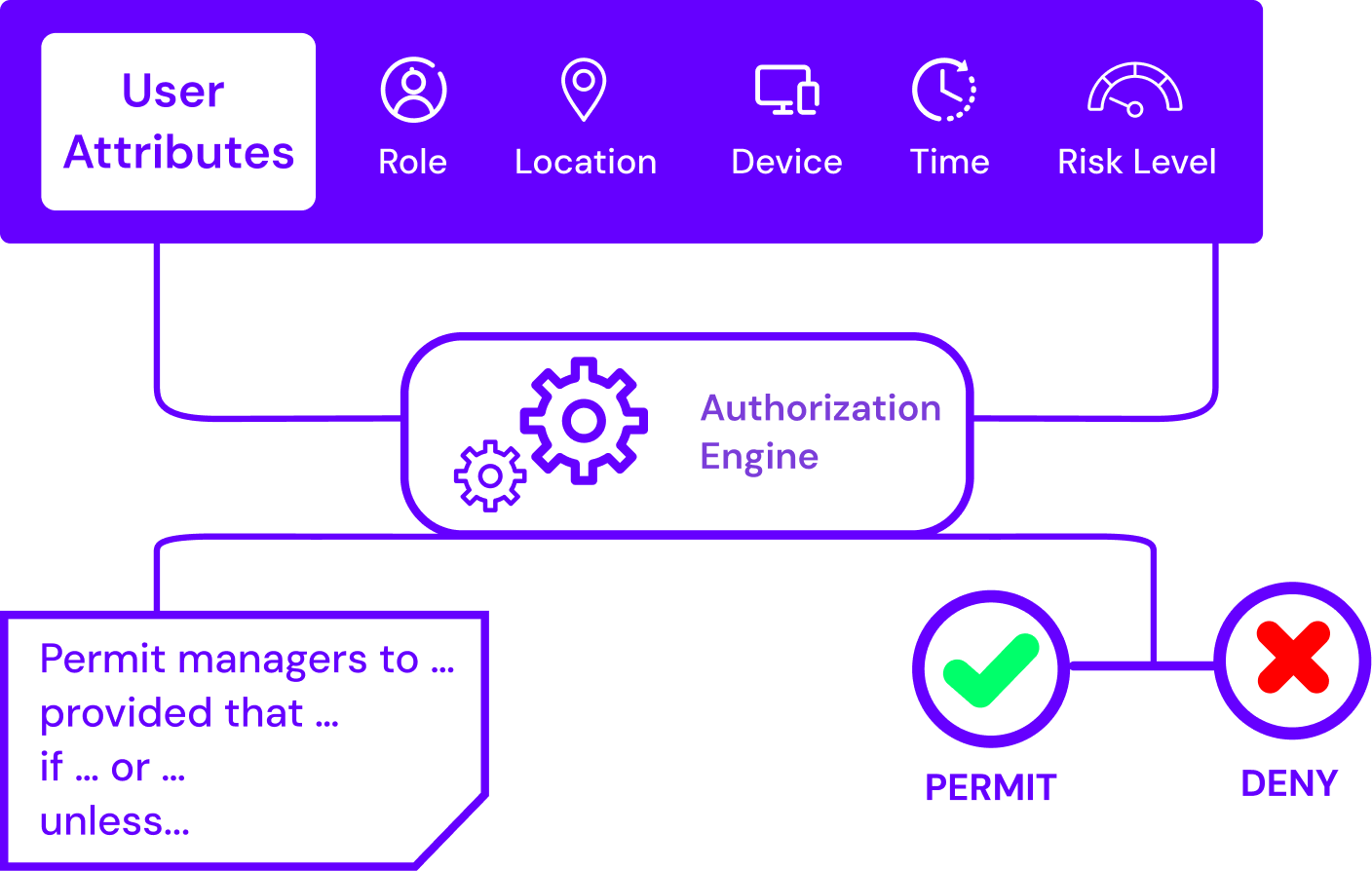
What is Attribute-Based Access Control (ABAC)?
Attribute-Based Access Control (ABAC) is more dynamic and context-aware when it comes to permission settings. Instead of just assigning access based on roles, ABAC evaluates multiple attributes, which are properties or characteristics, when granting or denying access.
These attributes can be broken down into:
- User attributes - Department, security clearance level, job title
- Environmental attributes - Time of day, location, type of device
- Resource attributes - Document classification, data sensitivity, system type
For example, a policy may state, “Allow access to Financial records only if the user is from the Finance department, connecting from the corporate network during business hours, and document sensitivity level matches user security clearance.”
Since ABAC takes real-time context into account, it allows highly granular and flexible policies, well-suited for Zero Trust, hybrid, or multi-cloud environments. It can enforce policies that change as each situation unfolds, such as denying access if a login attempt is made from an unusual location or outside of business hours.
The downside? Complexity. To be successful, you need a strong understanding of the attributes used in the policy, trusted data sources to provide the attributes, and clearly defined policies. While ABAC is more flexible than RBAC, it requires a higher level of governance maturity and often more capable tooling to implement successfully at scale.
How RBAC and ABAC Support Zero Trust Architecture
Zero Trust Architecture (ZTA) embraces the principle that one should never trust, but always verify. This means granting permission only based on least privilege and always verifying that the identity and context have not changed. Role-based access control (RBAC) and attribute-based access control (ABAC) are two key methods to support ZTA.
RBAC is used to provide the minimum baseline of trusted access by assigning permissions based on the user’s role. This provides a new user starting out with a minimum baseline of controls, thus limiting the number of excessive permissions a user can be given on day one.
ABAC method continually verifies context based on variables such as geolocation, device health, and data sensitivity, thus ensuring that each user stands on a solid footing before being granted access. This approach allows a strong verification of a user, but also allows that verification to happen again if the context changes.
The hybrid RBAC–ABAC model is becoming the most common and effective way to operationalize Zero Trust within organizations. Positioning RBAC as the foundational model provides structure to access, while ABAC layers and adds flexibility to how policies can be managed and operationalized in a true cloud, hybrid, or remote-first world where security is paramount but flexibility is equally as important.
Role-Based Access Control vs Attribute-Based Access Control: A Side-by-Side Comparison
Both RBAC and ABAC are security and access control mechanisms, but their approaches to security differ significantly. The table below examines these models against important criteria to help you determine which model or models may be best suited for your organization.
| Criteria | RBAC (Role-Based Access Control) | ABAC (Attribute-Based Access Control) |
|---|---|---|
| Access Mechanism | Based on predefined roles (e.g., Admin, HR, Sales) mapped to specific permissions. | Based on attributes such as user role, department, device type, location, time, and data sensitivity. |
| Flexibility | Moderate as changes require updating role definitions. | High as policies adapt dynamically to changing attributes and contexts. |
| Granularity | Coarse-grained — permissions are tied to broad roles. | Fine-grained — policies can apply to individual resources and contexts. |
| Ease of Implementation | Easier to set up in structured organizations with stable roles. | More complex to design and maintain due to the number of attributes and policy rules. |
| Dynamic Access Capabilities | Access is limited — roles don’t automatically adapt to context changes. | Strong — ABAC evaluates access in real time based on the current context. |
| Scalability | Can suffer from “role explosion” as organizations grow. | Scales better by avoiding role proliferation and focusing on attribute combinations. |
When to Use RBAC vs ABAC
The correct access control model for your organization will depend on various factors, including the size, complexity, and security needs of your organization.
- Use RBAC when:
You have a relatively small number of employees, predictable or stable job functions, and well-understood roles. RBAC is best where permission can and will remain infrequent, and you are seeking an easy-to-manage and maintain access model. - Use ABAC when:
You are in a complex and rapidly changing environment (multinational enterprise, regulated industry, or cloud-native organization) where compliance, dynamic environments, and requirements for context-aware policies are the norm. ABAC under these conditions is particularly well suited where permissions need to be enabled in a real-time manner on a fine-grained level. - Use a Hybrid RBAC+ABAC model when:
You want the ease of use of role-based assignments of access items and the flexibility of attribute-based policies. The current breadth of modern identity systems typically supports blended RBAC with ABAC as a role-driven assignment system for access to resources access but independent contextual markers (e.g., time, device, location) to offer a Zero Trust-like security posture.
The bottom line is that RBAC provides clarity, ABAC provides adaptability, and the Hybrid model provides both, while supporting the demands of modern, hybrid, and multi-cloud environments.
💡 Pro Tip
Don’t pick RBAC or ABAC in isolation. Design your access strategy around your business risk and scalability needs. The best-performing security teams evolve from static role models to dynamic, attribute-driven policies without ripping out existing systems.
Real World Examples of RBAC and ABAC
Access control models become easier to understand when you see how they are used. Here are three examples from the industry of how RBAC and ABAC can function alone or together to drive security.
- Finance
RBAC: Access is granted based on predefined roles, such as Manager or Analyst. For example, a Manager can approve high-value transactions, while an Analyst can only review them.
ABAC: Access adds conditions. For instance, loan files over $250,000 can only be opened by a Manager in the Corporate Lending department and only during business hours, ensuring sensitive data is protected by both role and context. - Healthcare
RBAC: Medical staff, like doctors and nurses, are assigned roles in the Electronic Medical Record (EMR) system, determining what patient information they can view or update.
ABAC: Adds patient-specific and environmental conditions. For example, only the patient’s assigned care team can access their records, and only when using devices connected to the hospital’s secure network. - SaaS
RBAC: New hires are assigned an Onboarding role that automatically provides them with standard access to features they need to start working.
ABAC: Access is fine-tuned based on attributes like subscription tier, geographic location, or active license count, so certain premium features are only available to customers who meet those specific criteria.
Benefits and Challenges of Each Model
Both Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) have positive attributes and weaknesses. Knowing the advantages and disadvantages of each model allows you to choose the one that will best meet your organization’s need for security, compliance, and scalability.
Role-Based Access Control: Pros and Cons
| Pros | Cons |
|---|---|
|
|
|
|
|
|
Attribute-Based Access Control: Pros and Cons
| Pros | Cons |
|---|---|
|
|
|
|
|
|
|
|
Hybrid Model Benefits
The hybrid model leverages the benefits of both RBAC and ABAC:
- Simplicity: Using RBAC allows for a base level of ability that`s easy to assign.
- Flexibility: ABAC rules can be layered on top of RBAC to enforce context-based permissions in real-time.
- Future-proofing: The hybrid model can facilitate static role-driven governance (RBAC), along with enabling dynamic governance based on attributes (ABAC).
- Stronger Zero Trust alignment: The hybrid model can help support least privilege while verifying entitlements.
Final Thoughts: Which Is Right For You?
Choose ABAC if you:
- Operate in a complex, compliance-heavy, or highly regulated industry.
- Require flexibility and context-aware access that adapts to changing business needs.
- Need fine-grained, real-time control over who can access resources based on multiple dynamic factors.
- Work in hybrid or multi-cloud environments where user attributes and environmental conditions frequently change.
Choose RBAC if you:
- Are a smaller organization with well-structured and relatively static roles.
- Do not require real-time, context-based access decisions.
- Want a simple, cost-effective model that is easier to design, implement, and audit.
- Have stable business processes that don’t require frequent role or policy changes.
Hybrid Approach
- Many organizations are adopting a hybrid RBAC + ABAC model, leveraging the ease and manageability of RBAC for broad permissions while using ABAC for situational, real-time access decisions.
- This approach reduces operational friction while meeting the contextual, adaptive security needs of today’s Zero Trust environments.
For a more holistic look at how access control fits into your identity security landscape, take a look at our guide to Identity Governance and Administration (IGA) that highlights how access control models, including RBAC and ABAC, fit into identity governance across the enterprise.
💡 Here’s What Our Expert Suggests
In fast-paced, compliance-driven environments, relying solely on RBAC can be limiting, while ABAC can often be more than teams can handle. Our experts suggest a dual approach: RBAC to provide baseline role assignments and ABAC for contextual, real-time enforcement. Using Identity Confluence, your team will make this balancing act look easy, as you centralize policy management, enforce Zero Trust, and maintain your entire IAM stack without any reengineering.
- Learn more about Identity Confluence
- See Identity Confluence in action.
Frequently Asked Questions (FAQs)
1. What’s the key difference between RBAC and ABAC?
RBAC grants access based on their role, which has a defined set of permissions. ABAC makes access decisions in the moment based on attributes such as the user’s department, the resource’s classification, and some other contextual factors such as location or time.2. Which model offers greater flexibility?
ABAC is a more flexible method for managing access control because it uses context-aware and dynamic rules, as opposed to the static roles that RBAC employs. ABAC is ideal for those environments that require access under certain conditional circumstances, such as work location or time of day.3. Can RBAC and ABAC be used together?
Absolutely! Many organizations may use RBAC to assign broad permissions while utilizing ABAC to specify finer, conditional access. This hybrid model allows the convenience of managing access control while adding an extra layer of contextual security.4. Is ABAC more complex to implement than RBAC?
Typically, yes, it is more complex to implement because ABAC requires the initial planning and defining of policies and attributes across separate systems, whereas RBAC reads access from user roles. That said, once configured and defined, ABAC is less complex than RBAC because it can adapt to changes to both the context of the security needs and the business.5. What’s a real-world example of ABAC?
An example of ABAC in practice could be an HR employee with the clearance to access, view, or download payroll data only during normal business hours, from a corporate network, and only as long as the document is at the same or lower classification than they have security clearance for.