How to Implement Role-Based Access Control (RBAC) in 5 Simple Steps

Role Based Access Control (RBAC) implementation is the most systematic approach to boost enterprise security and streamline access management. You can ensure that users interact with the right data and systems they actually need for their work, by assigning access based on their job roles. Whether you're developing applications or managing cloud environments, a well-executed RBAC strategy can help enforce consistent access based on the principle of least privilege and strengthen compliance standards.
Companies with a structured RBAC implementation, can reduce prohibited access by up to 60% according to Sprinto, which is a huge win for lowering security-related risks. Getting RBAC right means defining roles that match the job responsibilities, mapping the users properly, and enforcing policies through your IAM platform, while running regular audits. These steps not only ensure role-based access but also help follow RBAC best practices and boost operational agility. To make it clear, this blog walks through a step-by-step RBAC implementation framework, complete with real-world examples and practical tips designed for enterprise environments.
Key takeaways:
- Define roles and permissions aligned with job functions
- Understand how to assign permissions using the principle of least privilege
- Discover methods to automate user-role mapping and reduce manual errors
- Explore tools and techniques to enforce and maintain RBAC policies effectively
- See real-world RBAC implementation examples that ensure compliance and audit readiness
What Is Role-Based Access Control?
Role-Based Access Control (RBAC) is an access management approach that assigns only the minimum necessary permissions to individuals based on their job roles, limiting access to predefined role privileges. By doing so, RBAC helps streamline access management and reduces the risk of security breaches and insider threats.
RBAC is essential for large enterprises as it simplifies access provisioning and monitoring, which allows IT teams to manage access permissions, thus reducing human error and administrative workload. It makes access management simpler by letting IT teams enable faster onboarding through reusable roles. RBAC also strengthens compliance by supporting the principle of least privilege, segregation of duties (SOD), and audit trails, which makes it easier to meet regulatory standards like GDPR, SOX, and HIPAA.
For example, in a content management system (CMS), an Author may only create or edit their content, while an Editor can review and approve content from multiple authors. An Admin, on the other hand, would have full access to manage content, users, and settings. This hierarchy ensures clear separation of responsibilities and reduces the potential for unauthorized actions.
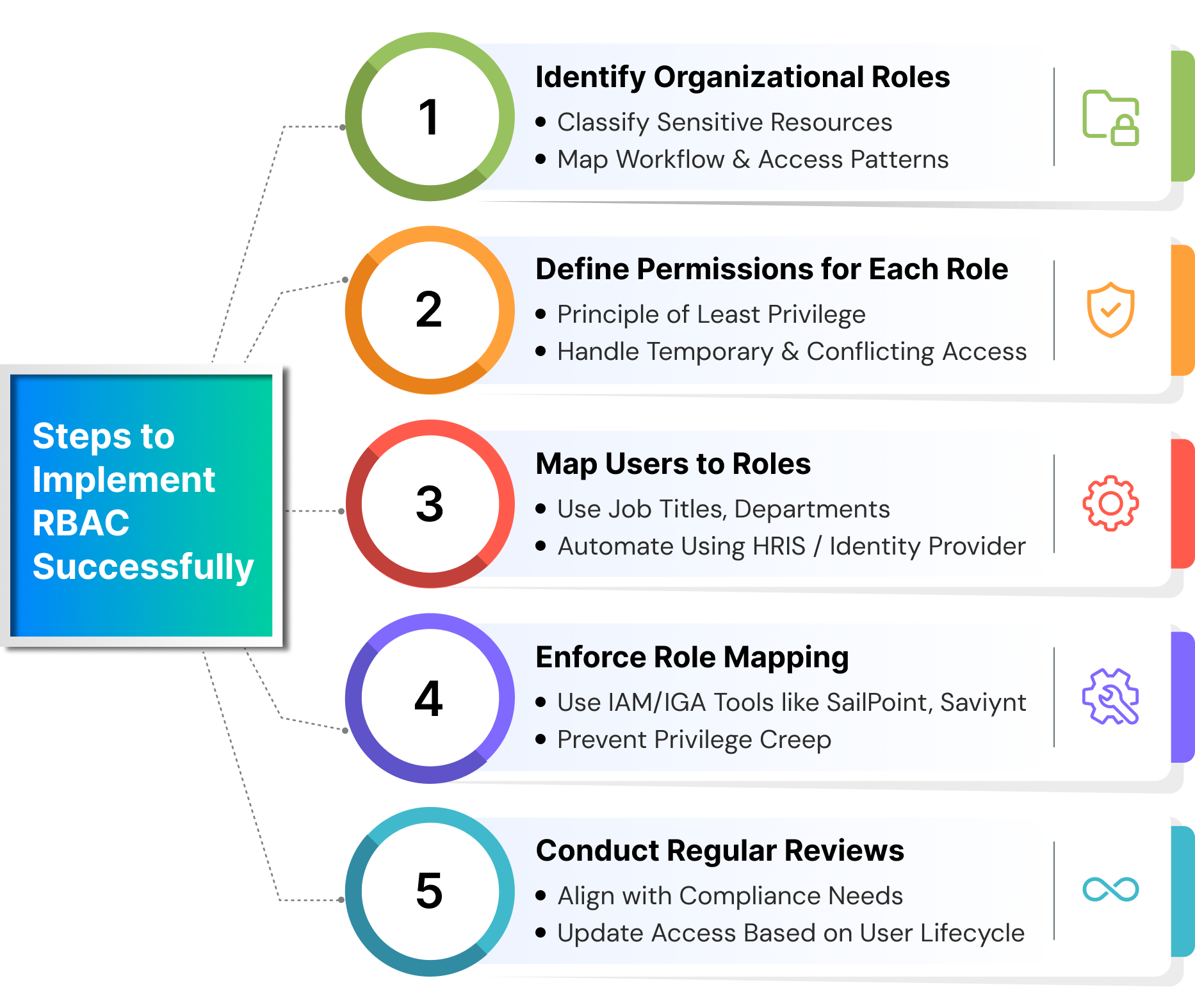
Key Steps for RBAC Implementation
Implementing Role-Based Access Control isn’t just about restricting access; it’s about structuring it smartly. A well-executed RBAC model reduces human error, improves security hygiene, and simplifies scaling access across departments. Here’s how to do it in six practical steps:
Step 1. Identify Organizational Roles
RBAC implementation begins with viewing the present technique of managing access control and is done in two separate processes. The first step is to classify significant organizational resources according to their criticality, which includes sensitive files, databases, specific datasets, and views, as well as unique functionality or operations that require privilege to access. This stage allows you to inventory data and data classes in order to determine which permissions to allocate to users. It also identifies the domains covered by RBAC implementation.
The process is to undertake a review of procedures and workflows, as well as how your users access and interact with the resources within them. You should consider assessing existing security procedures and policies to evaluate if they are in line with compliance standards. Finally, review how users are currently organized or managed, as well as how user accounts are provisioned and de-provisioned.
Step 2. Define Permissions for Each Role
This step begins with an analysis of the organizational structure and the division of roles according to the level of access, just like data classification. Once done, identify the roles that have not been created yet and map permissions to each role. While doing so, be sure to apply the principle of least privilege, ensuring that each role only gets the minimum access necessary to perform its tasks. At this point, it's also critical to consider constraints and nuances like temporary access, additional access, and conflicting roles. This is a critical phase that will require meticulous attention to detail. It also makes it easier to assign group responsibilities that require similar access.
For instance, a Finance Analyst may need access to budgeting and reporting tools, an IT Admin would require control over infrastructure and configurations, while a Support Rep would handle customer queries and access support-related platforms. Identifying such roles lays the groundwork for more precise access control and smoother RBAC implementation.
Step 3. Map Users to Roles
With roles and permissions in place, it’s time to link users to the roles that match their job function. Use existing organizational data like titles, departments, or job levels to guide these assignments. Where possible, integrate your RBAC model with your Human Resource Information System (HRIS) or identity provider to automate this mapping. Manual user-role assignment doesn’t scale well and is prone to inconsistencies, especially in large organizations.
Step 4. Integrate RBAC
With the basic structure in place, the next step is to integrate RBAC into your existing infrastructure. RBAC can be applied at multiple levels, and you can enforce a combination of rules depending on your security and operational needs.
- RBAC Implementation at the Query Level:
A query-level implementation defines varying degrees of access and permissions within an application. This can be achieved in two primary ways:
- Granting specific functional access related to individual databases to designated roles.
- Assigning custom query types to particular roles for controlled execution.
- RBAC Implementation at the Interface Level:
An interface-level RBAC implementation manages the specific views, interfaces, or screens that each user role can access. It ensures that users interact only with views or screens relevant to their core responsibilities, in alignment with the principle of least privilege. - RBAC Implementation at the Component Level:
A component-level implementation is especially effective when the differences between two roles are minimal. It controls the visibility of specific attributes based on the role accessing them. This approach not only simplifies the user experience by reducing the number of screens but can also selectively display certain options to roles that have the necessary access rights.
The decision on which implementation type to adopt depends on the required granularity of control and the organization’s overall security objectives.
Step 5. Implement & Enforce Role Mapping
Now, enforce role assignments using Identity and Access Management (IAM) or Identity Governance and Administration (IGA) tools like Tech Prescient and SailPoint. These platforms help apply policy-based access enforcement and ensure that users can’t override their assigned boundaries. RBAC enforcement also ensures that privilege creep doesn’t occur as users change departments or take on new responsibilities.
Step 6. Conduct Regular Reviews
RBAC is not a one-time exercise; it requires regular evaluations. Access within the organization is constantly changing for a variety of reasons, including compliance updates, workflow changes, shifts in roles and responsibilities, and so on. As a result, it must be continuously monitored and improved through a reporting mechanism. Access control is also an important function in the onboarding and offboarding process workflows, and must be reviewed when employees join or leave the organization. As a result, these periodic reviews will need to assess RBAC policies and how the system aligns with them.
Real-World RBAC Implementation Examples
To truly understand the effectiveness of Role-Based Access Control (RBAC), let’s look at a real-world scenario that showcases how role definitions and access restrictions come together to improve operational security, reduce risk, and support compliance.
Scenario: A mid-sized financial services firm implements an Identity Governance and Administration (IGA) platform to streamline and automate access control across departments like HR, Finance, and IT. Facing increasing data sensitivity and evolving compliance requirements, the organization adopts RBAC to establish granular control over user permissions, reduce manual provisioning, and create a scalable access management strategy.
Roles & Access Mappings
With the RBAC framework in place, each department is assigned roles that align with their specific job responsibilities, ensuring that access is customized, secure, and role-appropriate. Below are three core roles and how access is structured for each:
- HR Specialist
The HR Specialist is granted access to view and manage employee records within the HRMS (Human Resource Management System). Their role includes onboarding new hires, updating personal information, and managing internal HR documentation. However, access to payroll, compensation data, or financial records is explicitly denied. This separation reinforces data confidentiality and minimizes the risk of sensitive salary information being mishandled. - Finance Manager
The Finance Manager has access to the organization’s ERP system, where they are responsible for approving expenses, managing budgets, and overseeing financial workflows. They are completely restricted from accessing HR or employee-related data. This clear division ensures that financial operations remain isolated from personnel management, preventing any unintentional crossover or data exposure between departments. - IT Administrator
The IT Administrator has full control over system infrastructure, including managing user identities, setting access controls, and maintaining security configurations. Their role is technical, with no involvement in business functions like financial approvals or HR operations. By restricting access to sensitive business data, this role respects the principle of segregation of duties (SoD), ensuring IT has the tools to support without overstepping into operational or confidential areas.
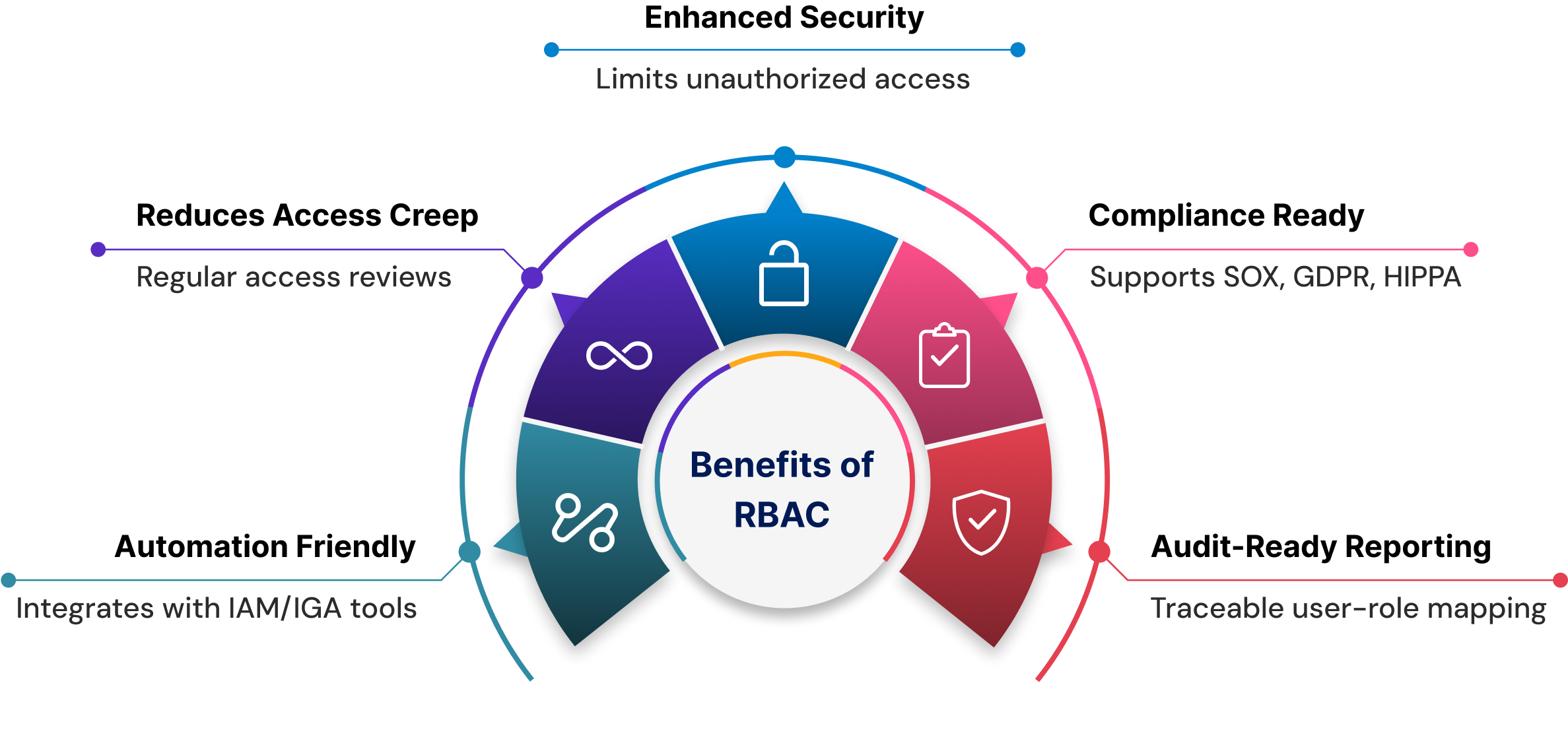
Why It Matters?
RBAC delivers more than just structured access control; it enforces security best practices, supports regulatory compliance, and adapts to evolving business needs. Here’s why a well-implemented RBAC model can be a game-changer for your organization.
- Supports Least Privilege and SoD Principles
RBAC ensures that each user receives only the access required to perform their job, no more and no less. This implementation of the least privilege principle reduces the risk of unauthorized access, human error, and insider threats. At the same time, Segregation of Duties (SoD) is inherently built into the system. For example, an IT admin cannot both provision and approve financial access, and a finance manager cannot access HR records, eliminating toxic permission combinations that could lead to compliance failures or fraud. - Enables Compliance & Audit Readiness By clearly defining roles and permissions, RBAC makes it easier to meet regulatory standards like SOX, GDPR, and HIPAA. Each user’s access can be traced back to their role, and those roles can be audited for scope and relevance. Access logs, user-role mappings, and policy enforcement become straightforward to generate and review. This not only shortens the time required for audits but also ensures that the organization maintains continuous compliance without scrambling to gather evidence when required.
- Automates Access Reviews with IGA Tools Using an IGA platform, the organization automates periodic access reviews, critical for maintaining RBAC hygiene. Managers are regularly prompted to verify whether users still need the access they’ve been assigned, and any outdated or unnecessary permissions can be quickly revoked. This automated certification process keeps the access environment lean, minimizes over-provisioning, and ensures the RBAC model evolves with organizational changes. It also eliminates the overhead of manual reviews, saving both time and effort.
Final Thoughts
A well-executed RBAC model doesn’t just enhance access security; it operationalizes governance. By assigning entitlements based on roles and enforcing strict boundaries between job functions, organizations can proactively meet compliance mandates, reduce identity-related risks, and scale secure access as business needs evolve. The above real-world example illustrates how RBAC, when paired with an IGA platform, transforms access control from a reactive IT task to a strategic enabler of enterprise security and agility. If you’re exploring RBAC implementation or looking to optimize your access governance strategy, Tech Prescient can help you get there faster and smarter. Our team has deep expertise in building secure, scalable identity solutions tailored to your business needs.
Ready to see how it works in action?
Frequently Asked Questions (FAQs)
1. What are the steps to implement RBAC?
To implement RBAC, start by clearly defining organizational roles based on job functions. Then, set specific permissions for each role, assign users accordingly, and enforce access through IAM or IGA tools. Don’t forget to regularly audit and review role mappings to keep your system secure and up to date.2. What is an example of RBAC in action?
A common example is in a content management system (CMS). Here, authors can only create or edit their own posts, editors can modify content from all authors, and admins have full access to manage content, users, and settings. Each role gets access aligned with their responsibilities.3. What’s the difference between RBAC and ABAC?
RBAC (Role-Based Access Control) assigns access based on a user’s role within the organization. ABAC (Attribute-Based Access Control), on the other hand, grants access using dynamic attributes like time, device type, location, or user status—offering more contextual and fine-grained control.4. Can RBAC be used in cloud applications?
Absolutely. RBAC is widely supported in cloud environments. Major platforms like Microsoft Azure Active Directory, AWS IAM, and Google Cloud IAM all offer robust RBAC features to help manage user access securely and efficiently.5. What tools support RBAC implementation?
RBAC is supported by many IAM and IGA tools, including Azure AD, AWS IAM, SailPoint, Okta, and Saviynt. These platforms help automate role assignments, enforce access policies, and maintain compliance with audit-ready access controls.