What Is Onboarding Automation? Benefits & Best Practices

Welcoming a new employee isn’t just about sending out a welcome email and handing them a laptop. It’s the beginning of a critical phase that shapes how connected, productive, and committed they feel to your organization. Yet in many companies, the entire process to this date consists of scattered checklists, endless paperwork, and a lot of back-and-forth communication within departments. As a result of all this, there are delayed start dates, frustrated employees, and an overwhelmed HR team.
Here is where onboarding automation steps in. Instead of managing tasks manually, organizations are now turning to automated onboarding tools to simplify, formalize, and speed up the process. Whether it’s assigning role-based access to IT systems or making sure all the documents are signed on time, employee onboarding automation removes the guesswork and delivers a smooth, structured experience for everyone involved.
Organizations that are investing in these onboarding automation tools are seeing measurable impact. According to Forbes, nearly 87 percent of organizations using automation report a faster time-to-productivity for new hires. From improving accuracy and onboarding compliance to delivering employee satisfaction, automating the onboarding process has become a strategic must. In this blog, we’ll explore what makes automated onboarding so powerful, how modern IGA software plays a key role in identity provisioning, and the best practices to follow when you decide to automate your onboarding process.
Key Takeaways
- Learn how IAM secures user access and forms the core of identity security.
- Understand why IAM best practices are vital in 2025 for threat defense, remote access, and compliance.
- Explore key principles like Least Privilege, RBAC vs ABAC, and centralized IAM.
- Discover 6 best practices, including MFA, automated provisioning, access reviews, PAM, Just-in-Time access, and monitoring.
- Identify common mistakes like over-permissioning and weak system integration—and how to avoid them.
- Get insights on creating a scalable, compliant IAM strategy aligned with business growth.
- Understand how IGA complements IAM for deeper governance and lifecycle control.
What Is Onboarding Automation?
Onboarding automation is the use of technology to streamline and simplify the process of integrating new employees, vendors, or clients into an organization. It replaces manual, repetitive tasks with digital workflows that ensure every step from paperwork to provisioning is handled accurately and efficiently.
At its core, it digitally transforms traditional HR and IT onboarding processes. Instead of manually coordinating between departments or chasing down updates, teams can rely on automation to trigger the right actions at the right time. Tasks like assigning devices, granting access, sharing welcome kits, or scheduling orientation meetings are all managed through predefined workflows, removing bottlenecks and reducing room for error.
This approach brings clear value across departments:
- HR teams can focus more on engagement and culture instead of administrative back-and-forth.
- IT teams benefit from streamlined identity provisioning and faster setup of system access.
- Compliance teams gain better visibility and control over onboarding steps for onboarding compliance.
- Even client and vendor onboarding can be automated, offering the same consistency and accountability as internal onboarding.
To enable all this, organizations often use a combination of RPA (Robotic Process Automation), AI, and HRIS integrations, creating a connected ecosystem that runs with minimal manual intervention. Whether it’s employee onboarding automation or scaling the onboarding journey for partners, automating the onboarding process ensures a faster, more structured, and scalable experience across the board.
Where IGA Fits Into Onboarding Automation
While onboarding automation takes care of streamlining the process, Identity Governance and Administration (IGA) adds the critical layer of control, compliance, and security right from day one.
Think of IGA as the system that ensures new hires don’t just get access quickly, but get the right access, for the right reasons, and for only as long as they need it.
Here’s how IGA strengthens employee onboarding automation:
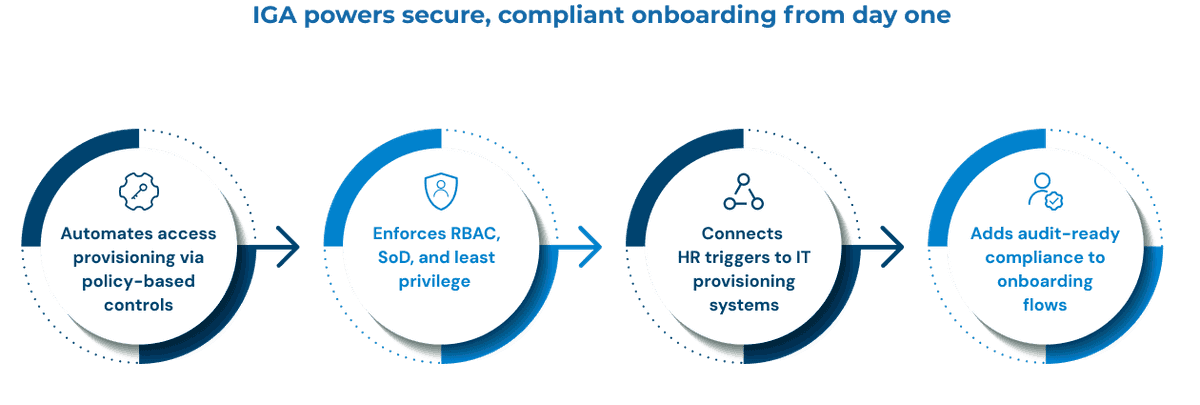
- Automated access provisioning: IGA solutions use policy-based controls to automatically assign the correct permissions based on an employee’s role, department, or location. This removes the need for manual ticketing and ensures access is granted immediately, without delays or missteps.
- Role-based access control (RBAC), segregation of duties (SoD), and least privilege enforcement: With these guardrails in place, IGA ensures no employee ends up with excessive or conflicting access that could pose a security or compliance risk.
- HR-triggered IT provisioning: IGA connects directly with HRIS systems, so the moment a new hire is added or a role changes, the right provisioning workflows kick in automatically. There’s no need for manual updates or follow-ups between HR and IT.
- Audit-ready compliance: Every access decision, assignment, and change is tracked—creating a clear, reviewable trail. This is essential for meeting regulatory requirements and staying ready for audits at all times.
Types of Onboarding Automation
Onboarding automation isn’t limited to just new employees. In fact, organizations today are automating onboarding journeys across multiple touchpoints from team members and clients to vendors and suppliers. Let’s break down how automation works in each of these scenarios.
1. Employee Onboarding
This is the most widely adopted use case, and for good reason. With employee onboarding automation, HR and IT teams can eliminate repetitive tasks and ensure every new hire gets what they need without delays or confusion. Automation handles everything from sending out welcome emails and gathering documentation to assigning devices and scheduling orientation meetings. But more importantly, IGA onboarding plays a central role here.
Through identity provisioning, IGA ensures that new employees are given access based on their role, department, or seniority level and nothing more. It enforces policy-based access, keeps permissions aligned with security protocols, and ensures onboarding compliance from day one.
Pro tip
At Tech Prescient, our IGA tools help automate role assignments and enforce RBAC so every new hire walks in with the right access and nothing slips through the cracks.
2. Customer Onboarding
For B2B and SaaS businesses, the onboarding experience can make or break customer engagement. Customer onboarding automation uses digital workflows to guide users through product walk-throughs, tutorials, and knowledge base resources. From sending welcome emails and syncing CRM data to triggering optional identity workflows for secure access, automation ensures that customers get a personalized, value-driven experience without manual intervention. Automated tracking and feedback loops help your team understand where customers are getting stuck and what actions lead to better activation, making the onboarding experience smarter over time.
3. Vendor/Supplier Onboarding
Bringing on new vendors and partners? That process can also be automated.
Vendor onboarding automation ensures that compliance checks, documentation, and access provisioning are completed quickly and consistently. Workflows can guide vendors through contract acknowledgment, policy acceptance, and background verification. Meanwhile, IGA verifies what level of access each vendor requires, provisions it accordingly, and most importantly, sets expiry timelines. This ensures vendors only have access while they’re actively working with you, helping reduce unnecessary exposure and security risk.
Whether it’s a short-term contractor or a long-term supplier, automated onboarding ensures the process is quick, compliant, and traceable from start to finish.
Benefits of Combining IGA with Onboarding Automation
While onboarding automation brings speed and efficiency to the table, combining it with Identity Governance and Administration (IGA) takes things several steps further. IGA doesn’t just help automate the process; it ensures that every onboarding decision is secure, policy-aligned, and scalable for the long term.
Here’s how this combination delivers real, tangible benefits:
- Access Accuracy Through Role Mapping
Not every employee needs access to everything, and that’s where IGA makes all the difference. By mapping access to roles, departments, or responsibilities, it ensures new hires get exactly what they need nothing more, nothing less. This eliminates the guesswork for IT and prevents over-provisioning that can lead to security gaps. - Just-in-Time (JIT) Access for Faster Provisioning
Need access right away? IGA supports Just-in-Time provisioning, meaning permissions can be granted exactly when they’re needed and revoked automatically once the task or project is done. This speeds up access without compromising control, ideal for dynamic teams or contract-based roles. - Continuous Audit Trails for Compliance
Every access request, approval, and change is automatically logged, creating a clear audit trail. This is especially valuable in industries with strict compliance requirements. With IGA in place, your onboarding compliance becomes seamless and audit-ready from day one. - Scalable Security for Hybrid and Remote Teams
As organizations move toward hybrid and remote models, managing access securely across locations becomes more complex. IGA solves this by centralizing control and allowing organizations to scale employee onboarding automation securely no matter where users are located.
Workflow Examples with IGA Integration
Now that we’ve explored the benefits, let’s take a look at how IGA actually fits into real-world onboarding workflows. These examples show how Identity Governance doesn’t just run in the background—it actively powers key stages of the onboarding journey.
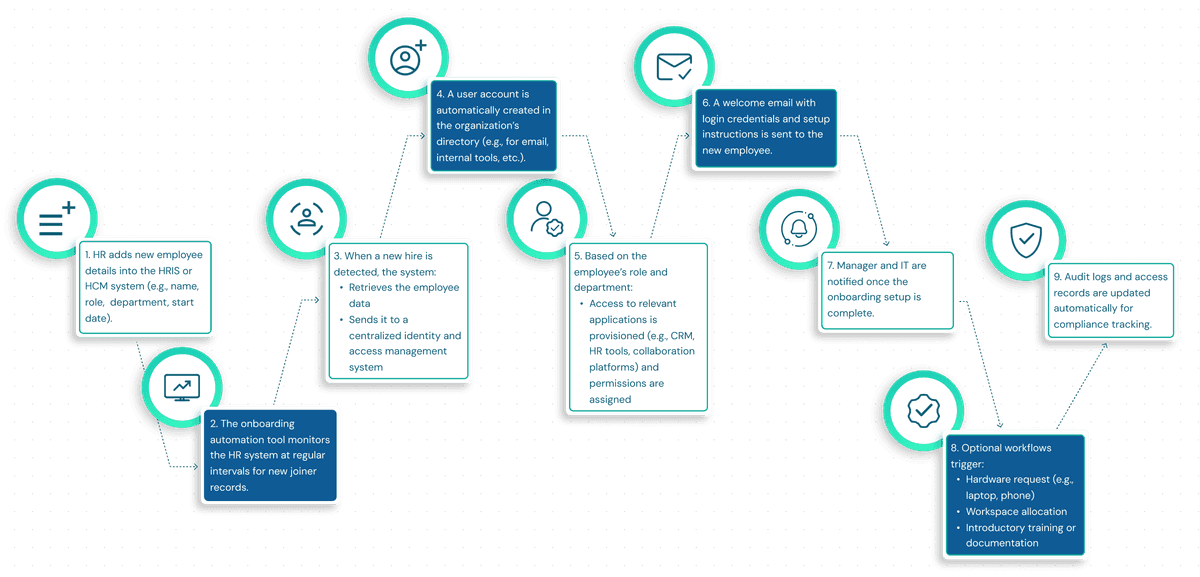
1. Preboarding
Before the employee even steps in, the onboarding process has already begun. As soon as HR adds a new hire into the HRIS system, IGA picks up that trigger and automatically initiates provisioning workflows.
That means:
- A user identity is created
- Role-based access policies are applied
- Initial access to email, communication tools, or shared drives is granted — even before day one
This ensures a ready-to-go experience for new hires and eliminates first-day delays.
2. Identity and Access Setup
Once onboarding is in motion, IGA software handles the next critical piece — assigning the right access to the right people.
Here’s how:
- It routes access requests through automated approval chains
- Enforces RBAC (Role-Based Access Control) based on department or job title
- Prevents risky access combinations through SoD (Segregation of Duties) policies
- Logs every access action for audit visibility
This step ensures that security, productivity, and compliance are all working together from the start.
3. Compliance and Policy Alignment
Onboarding isn’t just about access — it’s also about accountability. IGA supports this by assigning relevant compliance tasks based on the employee’s role.
For example:
- New hires are automatically enrolled in mandatory security awareness or data privacy courses
- Digital acknowledgements for policy documents are tracked and recorded
- Reminders and deadlines are automated to avoid missed sign-offs
Choosing the Right Onboarding + IGA Tools
Not all onboarding platforms are built the same especially when it comes to integrating governance and automation. To truly secure and streamline the onboarding journey, your tools need to do more than just assign tasks and send emails. They need to be intelligent, connected, and policy-aware from the start.
Here’s what to look for when choosing a solution that brings together onboarding automation and IGA capabilities:
1. Seamless IGA Integration
Look for platforms that support integration via SCIM, APIs, or direct HRIS connectors. This ensures real-time synchronization between your HR systems and identity governance layer, so provisioning workflows kick off the moment a new hire is registered.
2. Policy-Based Provisioning and SoD Controls
Your tool should allow access provisioning to follow predefined rules based on role, department, or location. Support for segregation of duties (SoD) policies is also key to preventing conflicts and minimizing risk.
3. Built-in Audit-Ready Reporting
Automated logging of every access event, approval, and policy acknowledgment helps you stay onboarding compliant without extra effort. Reporting features should support internal audits and help meet regulatory requirements like GDPR, HIPAA, or SOX.
4. Platform Compatibility and Extensibility
Choose a solution that integrates easily with the tools you already use. TechPrescient’s IGA platform, for instance, is built to work with a variety of HR systems, cloud platforms, and business apps, enabling a unified approach to automate onboarding processes at scale.
Best Practices for IGA-Driven Onboarding Automation
Blending IGA software with onboarding automation isn’t just about setting it up it’s about doing it right. When done well, it brings together security, compliance, and efficiency in one seamless flow.
Here are some best practices to keep in mind when building a governance-first onboarding strategy:
1. Map Roles and Least Privilege During Preboarding
Don’t wait until day one to think about access. During preboarding, define roles clearly and assign permissions based on the principle of least privilege. This helps prevent over-provisioning and ensures new hires only get what they truly need to start.
2. Integrate IGA with HR and IT Systems
Your IGA platform should be tightly connected to your HRIS, ITSM tools, and directory services. This ensures smooth identity provisioning, real-time updates, and consistent access control as soon as HR flags a new hire.
3. Schedule Access Recertification from Day One
Governance doesn’t stop after onboarding. Build in automated access recertification cycles right from the beginning. This means managers will be prompted at regular intervals to review and confirm if access is still relevant—helping reduce risk over time.
4. Monitor Lifecycle Triggers Continuously
Use IGA to track employee lifecycle changes such as role transitions, departmental shifts, or exits. Every change should automatically trigger a review or update of access permissions. This keeps your onboarding—and offboarding—secure and compliant.
Real-World Use Cases
Let’s take a look at how different industries are using IGA-enhanced onboarding automation to solve real business challenges. From compliance-heavy sectors to fast-scaling tech companies, IGA is helping organizations onboard smarter, safer, and faster.
1. Finance
In the finance industry, compliance and risk management are non-negotiable. During employee onboarding, IGA plays a vital role in enforcing segregation of duties (SoD) ensuring no employee is granted conflicting access rights that could lead to fraud or misuse.
With automated role mapping and access workflows, financial institutions can onboard new hires without delay while keeping strict governance controls in place. Every access decision is logged and review-ready, which simplifies audits and regulatory checks.
2. Healthcare
Healthcare organizations operate under strict regulatory frameworks like HIPAA, making access governance critical from day one.
With IGA software, HIPAA-related access reviews and policy acknowledgments are triggered automatically during onboarding. IGA ensures that healthcare staff only receive access to the patient data and systems relevant to their role, and nothing more. Continuous access monitoring and recertification further help these organizations maintain security and compliance over time.
3. SaaS
For SaaS companies, agility is everything and so is visibility into software usage.
IGA helps streamline just-in-time onboarding for employees, contractors, or customers by provisioning access only when needed. It also offers license visibility across platforms, helping teams avoid overspending on unused tools and keeping access tightly controlled.
In a fast-moving environment, IGA ensures onboarding is not only fast but also cost-efficient and secure across every app and user type.
Measuring IGA-Onboarding Success
Implementing IGA-driven onboarding automation is a great start but how do you know it’s actually working? Measuring the right metrics can help you track both the efficiency of your automation and the strength of your security controls.
Here are key success indicators to focus on:
Time to Productive Access
How quickly can a new hire log in, access the tools they need, and start contributing? With IGA software in place, you should see a significant reduction in time to first access — a clear sign of streamlined provisioning.
Access Request Turnaround
Track how long it takes for access requests to be approved and fulfilled. Faster, policy-driven approvals show that your onboarding automation is working as intended without sacrificing control or compliance.
Compliance Checklist Completion
Whether it’s security training, policy acknowledgments, or audit logs, IGA ensures that all onboarding-related compliance tasks are automatically assigned and completed. Monitoring these rates can reveal gaps and help you stay ahead of regulatory requirements.
Onboarding Satisfaction Feedback
At the end of the day, the new hire’s experience matters. Gathering feedback through automated surveys helps assess how smooth and structured their onboarding felt giving you insights to refine the process further.
Next Steps
Tech Prescient unifies identity and access management across cloud apps, on-prem systems, HR platforms, and more built for IT, security, and compliance teams.
- Learn how Tech Prescient IAM works
- Book a personalized demo
Frequently Asked Questions (FAQs)
Q. How does IGA enhance onboarding automation?
A. IGA streamlines onboarding by automatically assigning users the appropriate access based on their roles and organizational policies. By integrating with HR systems, it ensures access is granted securely and in compliance with company and regulatory requirements from the first day.Q. Can IGA automate access provisioning during onboarding?
A. Yes. IGA platforms automate the entire provisioning process by assigning user roles, enforcing security policies, and syncing with HRIS and directory services. This reduces manual effort and errors, providing users with timely and appropriate access.Q. Is onboarding automation secure without identity governance?
A. No. While automation speeds up access provisioning, without identity governance, there is a higher risk of overprovisioning and non-compliance. IGA ensures security by continuously enforcing least-privilege principles, access reviews, and compliance monitoring.Q. What tools support both IGA and onboarding automation?
A. Solutions such as TechPrescient offer integrated capabilities that connect with HRIS and other identity sources, enabling automated onboarding workflows combined with governance features like access certification and policy enforcement.Q. How do I measure onboarding automation success with IGA?
A. Success can be measured by tracking the time taken to provision access after onboarding, the percentage of compliant access assignments, readiness for audits through clear access documentation, and feedback from new hires regarding access availability and usability.