What Is Mandatory Access Control (MAC)?

Mandatory access control (MAC) is a type of access control in which the operating system grants users access depending on data confidentiality and user clearance levels. This paradigm grants access based on need-to-know: users must demonstrate their need for knowledge before getting access. MAC is also known as a non-discretionary access control paradigm, which indicates that control is not provided at the option of the user or file owner. The MAC model's control mechanisms enable businesses to apply zero-trust principles. MAC is regarded as one of the most secure access control methods. System administrators manually establish access rules under this paradigm, which are rigidly enforced by the operating system or security kernel.
However, choosing an access control model relevant to your organization can be tricky. This article discusses use cases for mandatory access control (MAC) and discretionary access control (DAC), explains the differences between MAC and DAC to help you decide which is the better fit, and provides tips on implementation.
In 2024, using valid but compromised credentials was the initial access vector in 22% of all data breaches, a clear sign that robust, centrally enforced access policies aren’t optional anymore. The good news? Organizations that put strict access controls in place have seen up to a 60% drop in unauthorized access incidents. That’s exactly where Mandatory Access Control (MAC) comes in. With its centrally managed, clearance-based enforcement, MAC is fast becoming a frontline defense in cybersecurity.
Key Takeaways:
- Learn what Mandatory Access Control (MAC) is and why it’s used in high-security systems
- Understand how MAC enforces access based on labels and clearance levels
- See real-world use cases across government, healthcare, and finance
- Compare MAC with DAC to grasp control, flexibility, and ownership differences
- Explore key MAC models and best practices for effective implementation
How Mandatory Access Control Works
Mandatory access control (MAC) is a centrally regulated access system that uses security labels. We label it "mandatory" because network users have limited ability to share access or alter access rights. This is how it works.
- Policy Definition
Start by establishing clear and detailed security policies that define who can access specific resources, under which conditions, and according to assigned roles and data sensitivity levels. These policies act as a definitive rulebook, leaving no room for ambiguity and preventing any user overrides. - Labeling System
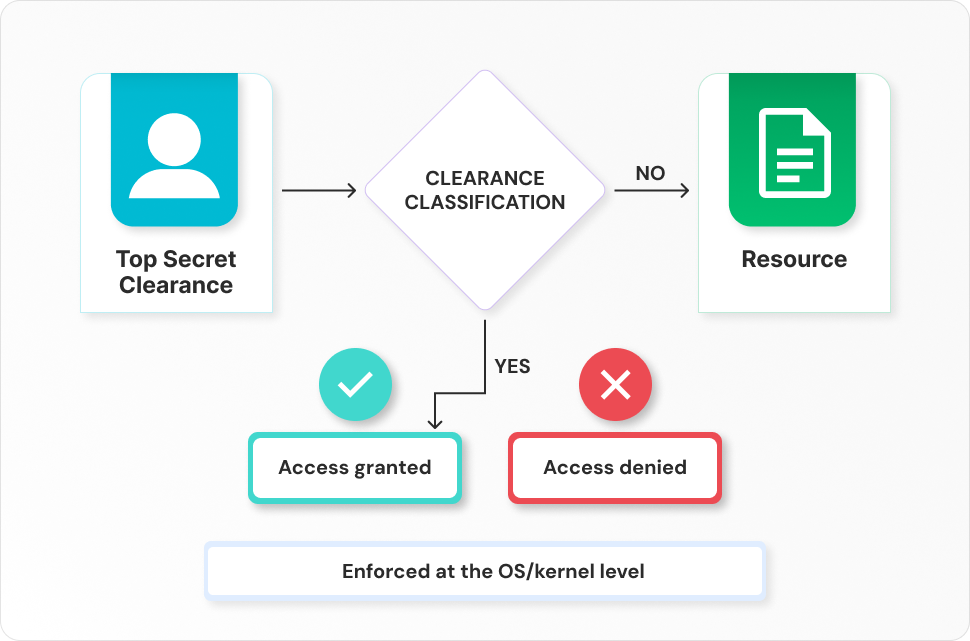
Mandatory access control, which is commonly used in government and military installations, assigns a classification label to each file system object (for example, "Restricted," "Confidential," or "Top Secret"). Similarly, every user is given a security or clearance level. They may only access the object or resource if their security level matches or exceeds the resource's categorization label. - Access decision logic
In MAC systems, security labels and policies maintain comprehensive records of permissions and access levels for every user and resource, guiding the enforcement mechanism in determining access rights. When a user attempts to access a resource, the system compares the security label of the user with that of the resource to verify whether the user’s label meets or exceeds the required classification level. - System enforcement
MAC is the most secure access control option available, but it needs careful planning and ongoing monitoring to maintain all resource item and user categories up to date. The administrator is responsible for creating and enforcing MAC's hierarchical architecture, regulating all user rights, and determining who has access to what. Because of this centralized management, non-admin users are unable to create their own permissions or access resources with higher security levels than their own.
Real-World Examples of MAC in Cybersecurity
Mandatory access controls work well in multilevel, hierarchical environments with tiers of users holding different clearances. This contrasts with multilateral systems like discretionary access control, which favor speed over data security. MAC is rare in small businesses or consumer applications, but it has important use cases.
- Government/military: Government, military, and intelligence institutions utilize required controls to impose stringent clearance levels. Government agencies handle massive amounts of sensitive information that must be kept secure. However, it must be available to employees. MAC allows for this by empowering administrators to define categories and securely link users to the secret information they require.
- Financial institutions: Large firms and banking sectors utilize MAC to protect client data. For example, MAC enables insurance and banking businesses to restrict the number of people who have access to financial data. This decreases the chances of potential data breaches and reputational harm. By implementing strict clearance-based access, these institutions can ensure only authorized users handle sensitive information. This not only safeguards customer trust but also helps meet strict regulatory and compliance requirements.
- Healthcare: In the healthcare sector, MAC is widely used to enforce HIPAA (Health Insurance Portability and Accountability Act) compliance by segmenting access to sensitive patient records. Each medical record is assigned a classification level, and only healthcare professionals with the appropriate clearance, such as a treating physician or authorized nurse, can access it. This prevents unauthorized staff from viewing or modifying patient data, reducing the risk of privacy breaches.
MAC vs DAC: What’s the Difference?
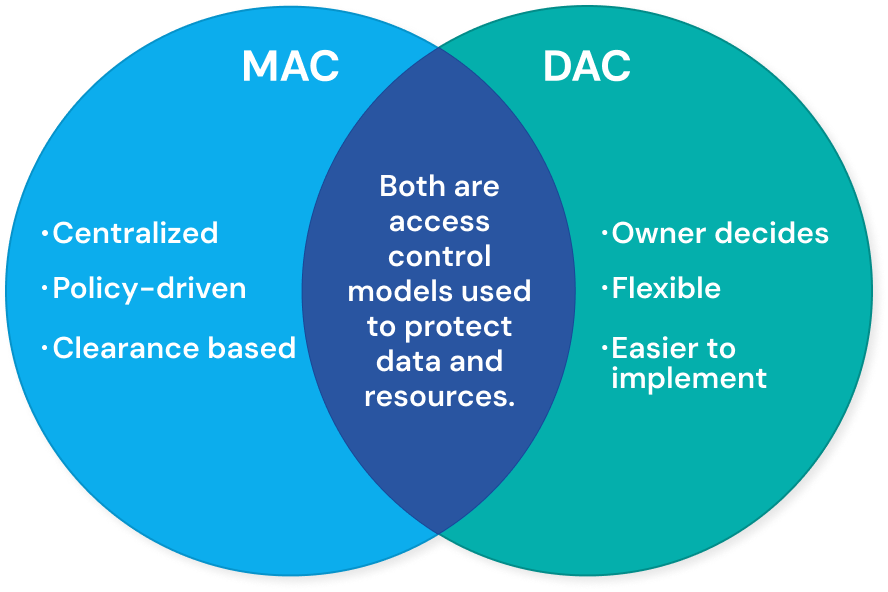
Mandatory Access Control (MAC) and Discretionary Access Control (DAC) differ in who controls permissions, how flexible they are, and where they’re most effective. MAC emphasizes strict, administrator-enforced security, while DAC offers user-level control with greater flexibility.
| Characteristic | MAC | DAC |
|---|---|---|
| User Control | Users cannot configure or change access parameters themselves. | Users can configure access parameters without involving administrators. |
| Access Management | Centralized access management defines and enforces all permissions. | No centralized access management; each access control list must be checked individually to find access parameters. |
| Security Level | Provides a high level of data protection because policies cannot be bypassed. | Offers a lower level of data protection because users can share data however they like. |
| Typical Use Case | MAC is typically used in government, military, law enforcement, and other high‑security sectors. | DAC is typically used in small and medium‑sized companies or trusted user environments. |
| Who Sets Access | In MAC, only administrators have the authority to set access permissions. | In DAC, both administrators and users can set access permissions. |
Benefits of Mandatory Access Control
There’s a reason government agencies and high-security environments trust MAC. Its stringent controls and rigorous enforcement make it the gold standard for access control, with benefits like:
- Strong centralized control
The system administrator can set access permissions for objects anywhere on the network. Users without the necessary clearance level cannot access these objects. There is also no scope to gain access by sharing credentials with others. Centrally managed policies grant access only to explicitly authorized users, preventing accidental permission sharing and enabling thorough vulnerability assessments. Multi-level security (MLS) rigorously classifies and labels data, protecting even the most sensitive information. - Ideal for compliance-heavy sectors
MAC is recommended by industry regulations like PCI-DSS. Companies handling financial data prefer mandatory controls to guard cardholder data environments or databases like insurance policyholders. Helps organizations meet regulations like GDPR, HIPAA, and PCI DSS through structured and auditable access control. Strict policy enforcement and detailed logging simplify compliance and reduce the risk of penalties. - Prevents insider threats via least privilege
Enforces a need-to-know basis for access, limiting insider threat risks. This aligns with the principle of least privilege (PoLP), which ensures users receive only the minimum access required to perform their tasks. Even system administrators cannot access sensitive information unless their security labels allow it, making it particularly valuable in finance and healthcare. - Enhances audit readiness with clear logs
MAC logs every access attempt and user action, creating comprehensive audit trails. These logs are crucial for forensic analysis and incident response, enabling organizations to trace breaches, understand their origins, and enhance accountability and transparency.
Challenges & Limitations of MAC
When choosing an access control system, security teams need to weigh up the pros and cons. Potential limitations of mandatory access control include:
- Complex policy management
- As user communities increase, administrators may have difficulty maintaining MAC systems. The administrator has the responsibility for configuring and managing all access, especially as the number of systems and users rises.
- Security teams must verify that user permissions are up to date and represent their roles. They must also quickly enroll new personnel and terminate those who have left. For the same reasons, MAC is unsuitable for applications with a large number of users, such as internet-based apps.
- Reduced flexibility for end-users
- Users must give their credentials every time they want to access data. This may be a serious issue when utilizing operating systems such as Linux or Windows, as users cannot update their access permissions, and only the system administrator may do so using the security kernel.
- Limiting access in this way slows down data flows and can reduce productivity. Clearing people to access one or more resource categories can be time-consuming and expensive. When several confidentiality levels or security domains must be applied to the same IT system, the expense and effort increase even more.
- Harder to implement in dynamic or agile environments
- Mandatory access control protects against many attacks, but it remains vulnerable to insider threats. Users with administrative privileges can bypass controls or grant access to outsiders.
- Clearance levels alone are not always enough to guard against such threats. For these reasons, the method is often avoided in budget-constrained corporate environments.
Common MAC Models: Bell-LaPadula & Biba
Consider adopting a structured framework of MAC models, such as Bell-LaPadula or Biba, for your security goals
1. Bell-LaPadula
The Bell-LaPadula (BLP) model is primarily focused on confidentiality, ensuring that sensitive data does not leak to unauthorized users. It operates on the principle of "no read up, no write down":
- No read up means a user cannot access information at a higher classification level than their own (e.g., a “Confidential” user cannot read “Secret” files).
- No write down means a user cannot write information to a lower classification level, preventing the accidental or intentional leakage of sensitive data to less secure areas.
This model is widely used in military, government, and classified systems where protecting data secrecy is critical. For example, in a defense network, this prevents a low-clearance soldier from reading top-secret orders or a high-clearance officer from accidentally saving classified reports into a publicly accessible folder.
2. Biba
The Biba model, on the other hand, focuses on integrity rather than secrecy. Its core rule is "no write up, no read down":
- No write up ensures that users cannot write to data at a higher integrity level, protecting critical information from being altered by less trustworthy sources.
- No read down prevents users from reading data from lower integrity levels, avoiding contamination by inaccurate or unverified sources.
This model is ideal for systems where accuracy and trustworthiness of data are more important than secrecy, such as financial systems, healthcare records, or safety-critical industrial controls, ensuring that decisions are based only on reliable and verified information.
Choose Bell-LaPadula when protecting confidentiality is the top priority, such as in defense or classified environments. Opt for Biba when safeguarding data integrity is critical, like in financial systems or safety-critical applications where accurate information drives decisions.
Best Practices for Implementing MAC
Implementing MAC effectively takes more than just turning it on; you need a well-structured approach that covers policies, automation, and ongoing oversight. Below are some proven best practices to help you set up a secure, efficient, and compliant MAC framework.
- Define clear policies and labels
Create precise and clear security policies to ensure consistent enforcement at all levels of access control. Policies should define data classification, access requirements, and organizational roles and responsibilities. Effective rules should also contain operational processes for dealing with exceptions and circumstances that necessitate policy changes. - Automate labeling and provisioning
To provide precise and prompt access control, automate the provisioning and deprovisioning of user accounts. Automated solutions such as Okta or Microsoft Azure Active Directory can swiftly provide new users the right amount of access and remove access as users exit or take on other responsibilities. By having this feature, security flaws related to manual onboarding, offboarding, or user role changes are avoided. - Enforce separation of duties
You may enforce separation of responsibilities (SoD) in your MAC framework by giving each user a unique role and set of access rights. For instance, MAC rules can be set up to allow one person to start financial transactions while requiring approval from another user with a higher security clearance and a different role. By preventing people from having complete authority over a crucial operation, this configuration lowers the possibility of fraud and mistakes. - Integrate with CI/CD pipelines, cloud environments, and IAM
Only authorized individuals and procedures are able to start, edit, or distribute code into CI/CD pipelines thanks to MAC. Code can only be started, changed, or deployed into CI/CD pipelines by authorized persons and processes, thanks to MAC. Every step of the pipeline can be given a security label, and by integrating these labels with identity and access management (IAM) systems, companies can implement policies that specify who may run builds, install applications, and access private data. - Classify Data with Sensitivity Labels
Establish a thorough categorization system to precisely categorize data according to its level of sensitivity and protection. An example of how you could categorize your data is as follows:- Confidential: Internal project documentation, personnel files, and memoranda are all considered confidential.
- Secret: Research and development data, financial reports, and strategic plans.
- Top Secret: high-level company trade secrets and important infrastructural specifics.
Automated technologies that update labels dynamically as data progresses through its lifespan can help preserve these categories.
- Regular Audits and Monitoring
Security audits and real-time monitoring can help quickly identify unwanted access attempts and automate incident detection. Automated compliance reports can also provide a clear view of your current security posture and highlight areas that need improvement.
Final Thoughts
A well-implemented Mandatory Access Control (MAC) framework doesn’t just lock down sensitive data; it enforces security at the very foundation of your systems.
By applying strict, centralized policies and clearance-based labels, organizations can safeguard high-value assets, prevent unauthorized access, and ensure compliance across regulated environments. The above best practices show how MAC, when combined with automation and continuous monitoring, shifts access control from a manual, error-prone process to a resilient, policy-driven security model.
If you’re considering MAC adoption or aiming to strengthen your existing access control strategy, Tech Prescient can help you design and implement a solution that’s both secure and scalable.
Get ready to elevate your access control to the highest standard.
Frequently Asked Questions (FAQs)
1. What is mandatory access control in cybersecurity?
Mandatory Access Control (MAC) is a system-enforced security model where access permissions are defined by a central authority based on predefined rules and security labels. It ensures users can only access data they’re cleared for, without exceptions.2. How does mandatory access control differ from discretionary access control?
Unlike Discretionary Access Control (DAC), where users can set permissions on their own resources, MAC is strictly controlled by administrators and cannot be overridden by users. This makes MAC much more rigid and secure.3. What are examples of mandatory access control in real life?
You’ll find MAC in government clearance systems where sensitive info is tightly controlled, and in healthcare environments compliant with HIPAA, ensuring only authorized personnel can access patient data.4. What are the benefits of using mandatory access control?
MAC boosts security by limiting insider threats and enforcing strict access policies. It also helps organizations meet compliance requirements for regulations like GDPR and PCI DSS.5. What challenges come with implementing MAC?
Implementing MAC can be complex due to detailed policy management; it offers less flexibility for users and requires more effort and oversight compared to other access control models.