MAC vs DAC vs RBAC: Access Control Models Compared (2026)

Access control models are the gatekeepers of your digital environment, as the rights to access a particular resource, what actions can be performed, and how much control one has over it are defined by them. Selecting the right model for your business isn’t just about ease of use; it is crucial for protecting sensitive data, being audit-ready, and minimizing cyber threats. Even the most advanced technologies can fall short if access policies do not align perfectly with their security and compliance standards.
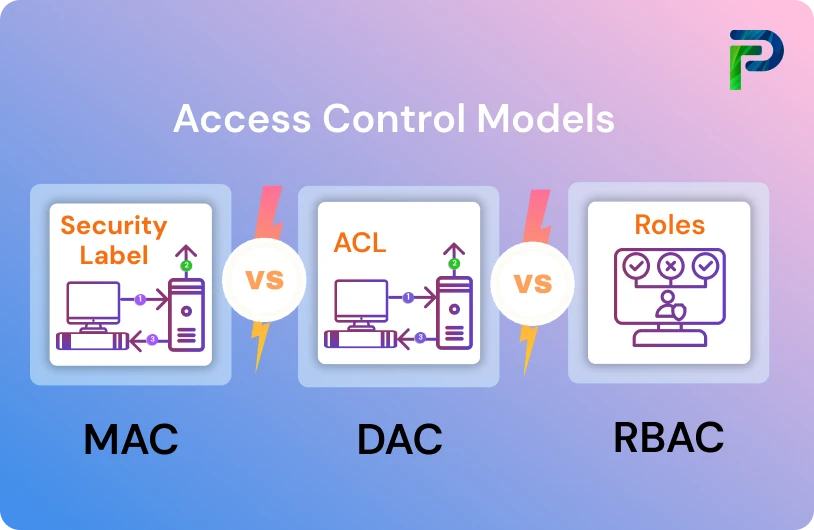
Let us have a look at the three most common access control models, MAC, DAC, and RBAC, and understand how they differ from each other.
- Mandatory Access Control (MAC) is the strictest model, where the system sets all access rules using security labels and clearance, and users cannot change them, keeping everything tightly controlled. It’s commonly seen in highly sensitive environments like government or military systems where data classification is critical.
- Discretionary Access Control (DAC) is the most flexible model because the resource owner decides who can access their files or applications, usually using ACLs (access control lists), which puts control in the owner’s hands. This approach is typical in operating systems like Windows, where a file owner can grant or deny access to others.
- Role-Based Access Control (RBAC) organizes access by grouping permissions into roles like ‘Admin’ or ‘Editor’ and gives users access based on their role, making it easier to manage access for larger teams. Large enterprises often use RBAC in applications such as ERP systems, where employees are assigned roles with predefined permissions.
MAC is strict and centrally controlled, making it ideal for environments like government or defense where data classification cannot be compromised. DAC offers greater flexibility by enabling resource owners to control who can access their files or applications, making it well-suited for business settings and collaborative environments. RBAC offers a balance between the two, providing a structured, scalable system tied to organizational roles, though it depends on clearly defined roles to work effectively.
The access control model you choose plays a key role in managing risk and ensuring compliance. According to Frontegg, RBAC (Role-Based Access Control) is the most widely used model because it offers a good balance between security and usability. 94.7% of companies have implemented it, and 86.6% still rely on it. On the other hand, choosing MAC (Mandatory Access Control) instead of DAC (Discretionary Access Control) ensures stricter, system-enforced rules that help maintain compliance. In contrast, relying on DAC when stronger controls are needed can increase the risk of compliance gaps and costly penalties.
Key Takeaways:
- Understand how MAC, DAC, and RBAC differ in control, flexibility, and security
- Learn the strengths, weaknesses, and real-world use cases of each model
- See a side-by-side comparison table for quick decision-making
- Discover how to choose the right access control model for your organization’s security and compliance needs
- Explore real-world industry examples to see how MAC, DAC, and RBAC work in practice
What Are Access Control Models? Access Control Models Explained
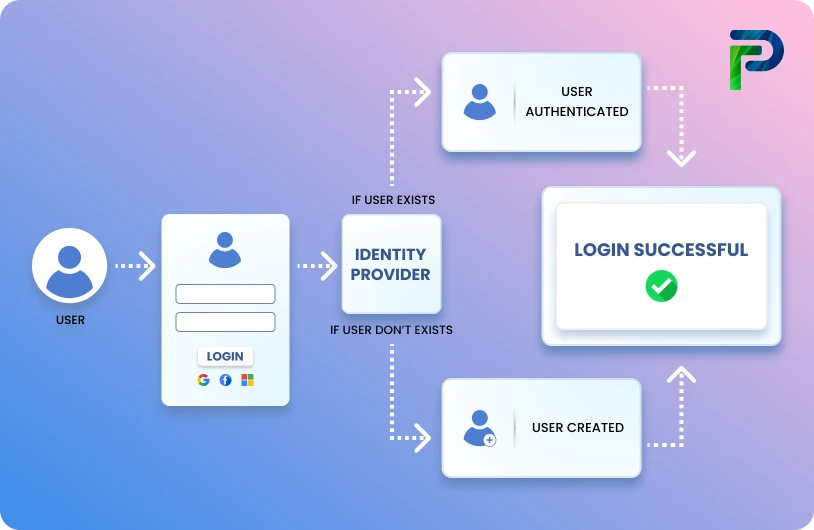
Access control refers to the policies and technologies that determine which authenticated users are allowed to access specific systems, data, or resources. It's a cornerstone of cybersecurity, ensuring that only authorized parties gain access, thereby protecting the confidentiality, integrity, and availability of critical assets.
In the broader landscape of identity security, Access Control is a vital component within Identity & Access Management (IAM) frameworks. IAM systems handle authentication, authorization, and account lifecycle processes to manage access securely across environments. Meanwhile, Identity Governance & Administration (IGA) overlays IAM with governance, policy enforcement, compliance visibility, and auditing capabilities, ensuring access rights are appropriate and aligned with regulations.
Together, access control, IAM, and IGA form a layered defense: access control enforces who gets in and what they can do; IAM provides the operational mechanisms to authenticate and authorize; and IGA ensures governance, policy compliance, and oversight over those access decisions.
What Is Mandatory Access Control (MAC)?
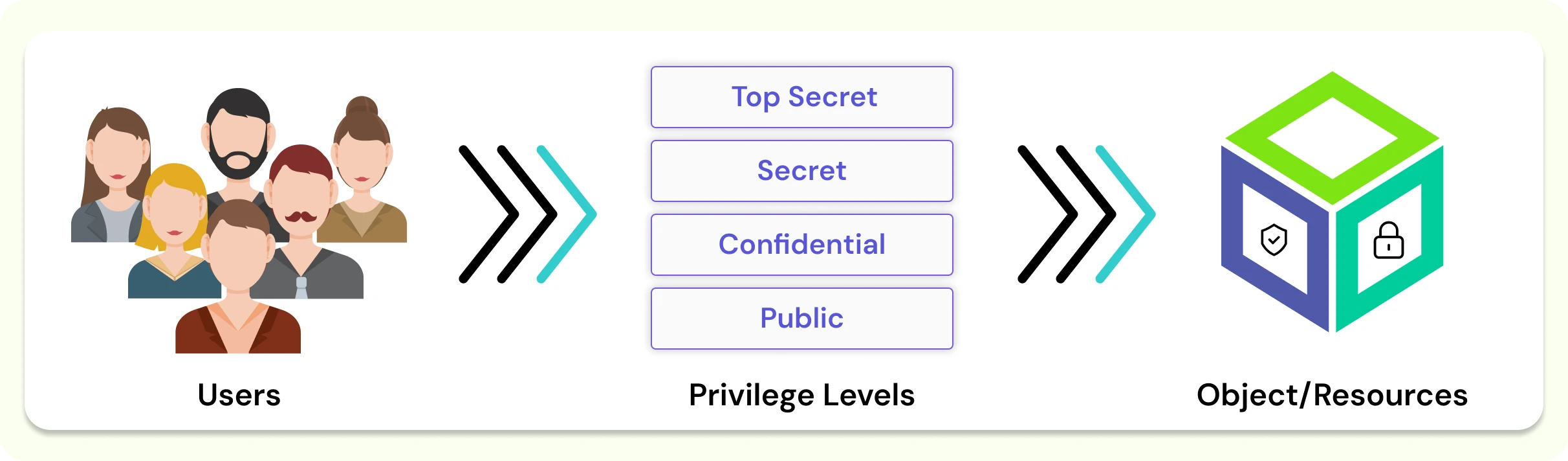
Mandatory Access Control (MAC) is an access control model where the operating system regulates access according to the confidentiality level of data and the clearance level of the user. It follows a strict need-to-know principle, meaning users can only gain access if their clearance matches the sensitivity of the information they require.
Mandatory Access Control (MAC) is a centrally managed, non-discretionary security model designed to deliver the highest level of protection. In MAC, access policies are strictly governed by a centralized security administration rather than individual resource owners. This model applies security labels to both resources and users, which determine access eligibility.
- Classification and Clearance: Resources are assigned classifications (e.g., restricted, secret, top-secret) that reflect their sensitivity level. Users are granted clearances that define what classifications they are authorized to access.
- Compartment: Each resource is also assigned a compartment, such as a department or project group, while users are assigned to one or more compartments. Access is permitted only when both the user’s clearance and compartment match those of the resource.
MAC is the highest level of access control, originally developed for military and government environments. It uses classification levels such as Classified, Secret, and Unclassified instead of a simple numbering system to enforce strict security policies. While it was first designed for defense and intelligence sectors, MAC is also used in industries like banking and insurance to protect highly sensitive data, such as customer account information.
Benefits of MAC
When security cannot be compromised, organizations turn to MAC. Its rigid controls make it the most trusted access control model in sensitive environments.
- Centralized Policy Enforcement
In MAC, the system administrator defines access policies across the network. Users without the required clearance cannot bypass restrictions, even with shared credentials. Centrally managed rules enforce strict authorization, prevent accidental permission leaks, and support multi-level security (MLS) by classifying and labeling data for maximum protection. - Classification and Clearance
In MAC, every resource is assigned a classification level (such as Restricted, Secret, Top-Secret) to indicate its sensitivity. Users are granted security clearances, which determine the classification levels they are authorized to access. - Compartment
Each resource can also belong to a compartment, which specifies the group of people, such as a department or project team, who can access it. Similarly, a user’s compartment membership defines which groups they belong to and, therefore, what additional resources they can access.
Limitations of MAC
Security teams must balance benefits with constraints. Here are the primary limitations of mandatory access control:
- Complex Policy Administration
As user communities scale, maintaining MAC becomes challenging since administrators must configure and manage all access centrally. Security teams need to continuously validate permissions, handle rapid onboarding and offboarding, and ensure roles remain accurate, making MAC impractical for large, internet-facing applications. - Limited User Flexibility
In MAC, users must repeatedly authenticate with credentials, and only the system administrator, via the security kernel, can update permissions. This strict control slows data flow, reduces productivity, and makes managing multiple confidentiality levels or security domains both time-consuming and costly. - Clearing users is an expensive process
Granting and managing security clearances for users can be costly and time-consuming. It also requires ongoing maintenance to keep access rights updated, which can place a significant burden on administrative teams. - Complex implementation
The process of assigning classification labels to every resource and user can be overwhelming, often slowing down operations and reducing productivity. Additionally, MAC’s rigid structure is not always compatible with certain applications or operating systems, making integration challenging in diverse IT environments.
Examples of MAC
MAC is best suited for multilevel, hierarchical environments where users hold different clearance levels. MAC emphasizes strict data security. While uncommon in small businesses or consumer apps, it remains highly valuable in specialized high-security use cases.
-
Government Institutions
Government, military, and intelligence agencies rely on MAC to enforce strict clearance levels for sensitive data. These institutions manage vast volumes of classified information that must remain secure yet accessible to authorized staff. With MAC, administrators can assign categories and map users to the specific classified resources they need, ensuring both security and controlled availability. -
Banking Sectors
In banking and large enterprises, MAC is used to safeguard sensitive client and financial data. By enforcing clearance-based access, institutions like insurance companies and banks can tightly restrict who handles critical records. This reduces the risk of breaches, protects customer trust, and ensures compliance with strict regulatory frameworks such as PCI-DSS and GDPR. -
Healthcare
Healthcare organizations apply MAC to meet HIPAA compliance by restricting access to sensitive patient records. Medical data is classified by sensitivity, and only cleared professionals, such as treating physicians or authorized nurses, can access or update it. This ensures patient confidentiality, prevents unauthorized access, and minimizes the risk of privacy breaches.
What Is Discretionary Access Control (DAC)?
Discretionary Access Control (DAC) is a security model where the owner of a resource determines who is allowed to access it and what actions, such as read, write, or execute, they can perform. These permissions are typically managed through access control lists (ACLs) or configured directly within application settings.
DAC is particularly well-suited for corporate offices, small businesses, and collaborative environments, as it gives resource owners the flexibility to grant or revoke access based on real-time requirements. Its simpler structure allows faster implementation with minimal administrative overhead, making it a practical choice for organizations seeking convenience and efficiency.
In Discretionary Access Control (DAC), the resource owner, whether a file, folder, or database, determines who can access the resource and what actions (read, write, modify, share) they can perform. When a user requests access, the system verifies their credentials (username, password, or cryptographic keys) and enforces the permissions set by the owner. Because control is “discretionary,” owners can grant, adjust, or revoke access at any time. This flexibility makes DAC highly user-driven but also introduces security risks, as protection depends on how responsibly owners manage and distribute permissions.
Benefits of DAC
When it comes to controlling access to resources, Discretionary Access Control (DAC) offers several advantages that make it a widely adopted model. While every access control approach has trade-offs, DAC strikes a balance between usability and control, empowering resource owners to manage access with minimal administrative overhead.
Key benefits of DAC include:
- Granular Permission Control: DAC allows owners to assign permissions at a granular level, whether to individuals or groups, enabling precise control over who can read, write, modify, or share resources. Unlike mandatory access control (MAC), this adaptability provides users with more autonomy.
- Faster Collaboration: Permissions can be granted or modified quickly, often with just a few clicks. This eliminates the need to create complex clearance levels or extensive user profiles, making onboarding and collaboration faster.
- Lower Administrative Overhead: Because access decisions are decentralized, object owners, not central administrators, control permissions. This lightens the burden on IT teams and allows users to manage access to information as needed.
- Simplified Policy Management: With the right Access Control List (ACL) management tools, DAC is simple to implement. Administrators only need to grant baseline object rights, while resource owners handle ongoing permission adjustments.
Limitations of DAC
While Discretionary Access Control (DAC) offers flexibility, it also introduces certain limitations that organizations must be mindful of.
Key drawbacks of DAC include:
-
Weaker Security Posture
Compared to Mandatory Access Control (MAC), DAC is inherently less secure. Since access decisions rest with users, attackers may exploit these permissions to spread malware or escalate privileges. Risks like privilege creep, over-sharing of resources, or users unknowingly granting access can expose systems to vulnerabilities. -
Limited Administrative Visibility
Because DAC is decentralized, IT and security teams may struggle to maintain clear visibility into who has access to sensitive resources. This lack of centralized oversight can lead to compliance challenges, hidden security gaps, and difficulty in enforcing consistent governance. -
Ongoing Maintenance Burden
DAC relies on object owners to keep Access Control Lists (ACLs) updated and relevant. As networks and roles evolve, ACLs may become outdated, granting permissions to former employees or failing to reflect role changes, ultimately reducing the effectiveness of access management.
Examples of DAC
Discretionary Access Control (DAC) is widely embedded in both consumer and enterprise systems. Most users engage with it daily, often without realizing it.
- Smartphone App Permissions
When installing or using apps, users are prompted to allow or deny access to resources such as the camera, contacts, or GPS. This is DAC at work: the resource owner (the user) decides which apps can interact with sensitive functions, and can later revoke or adjust these permissions. - Collaborative Document Sharing
Platforms like Google Workspace (Docs, Sheets, etc.) rely on DAC to manage sharing. Document owners control access control lists (ACLs), assigning privileges such as view-only, comment, or edit. They also retain the right to revoke access, delete the file, or restrict sharing entirely.
What Is Role-Based Access Control (RBAC)?
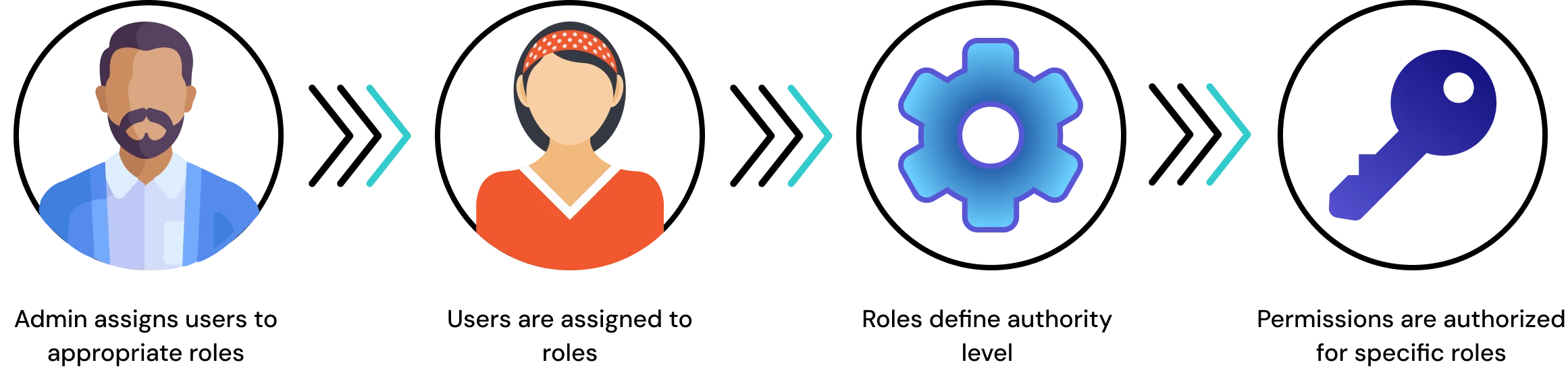
Role-Based Access Control (RBAC) is an approach to managing access to systems and data by linking permissions to specific job roles within an organization. Instead of assigning permissions to each user individually, Role-Based Access Control (RBAC) uses roles to manage access. In this model, access permissions are tied to specific roles, such as Manager, HR, or IT Administrator, rather than to individual users. Once roles are defined with their associated permissions, users are assigned to the appropriate roles, ensuring they only access the resources necessary for their responsibilities.
With Role-Based Access Control (RBAC), each user gets only the permissions they need, no more, no less. For example, an HR recruiter can update employee records, while others may have view-only access. This eliminates confusion, reduces the need for constant checks, and ensures secure, seamless access as teams expand. In today’s environment of hybrid work, rapid scaling, and rising insider risks, RBAC is essential for keeping systems compliant, secure, and manageable as your business grows.
Benefits of RBAC
RBAC isn’t just about restriction; it’s about making access smarter, safer, and easier to manage as your business scales. Here’s how it delivers real-world value:
- Implements the Principle of Least Privilege
With RBAC, employees get only the access necessary for their role. Think of it as handing out the right key for the right door, not the entire building. This minimizes potential damage if an account is compromised and keeps security aligned with modern best practices. - Automates Role-Based Onboarding
Instead of manually configuring access for every new hire, RBAC lets you assign a predefined role, like a developer or an intern. All required permissions come bundled, cutting down setup time, avoiding mistakes, and ensuring new team members are productive from day one. - Minimizes Human Error in Provisioning
Manual access assignment often results in either over-provisioning or under-provisioning. RBAC removes this uncertainty by standardizing roles across the organization, reducing errors, and keeping security consistent without constant admin intervention. - Simplifies Compliance & Audit Readiness
RBAC makes it easier to meet compliance demands like GDPR or HIPAA. With roles clearly defined and access logs readily available, audits turn into a streamlined process, no scrambling, no guesswork, just transparent reporting of who has access to what. - Ensures Flexibility Across Environments
From AWS to Salesforce to on-premises systems, RBAC scales across your entire ecosystem. Roles are created once and applied everywhere, cloud, SaaS, and legacy environments, so you don’t need to rebuild permissions every time your tech stack evolves.
Limitations of RBAC
While Role-Based Access Control (RBAC) offers strong security and scalability, it isn’t without its challenges. Implementing and managing RBAC in real-world environments, especially within large enterprises, can become complex. Here are some of the key drawbacks organizations often face:
- Complex deployment and role engineering
Defining roles isn’t always straightforward, particularly in large enterprises with diverse teams, overlapping responsibilities, and constantly evolving job functions. This difficulty has even given rise to its own discipline: role engineering. Without careful planning, the process can become lengthy and resource-intensive, sometimes delaying RBAC adoption. - Striking the balance between security and usability
The more granular the roles, the tighter the security, but this comes at a cost. If a system has dozens of overlapping or highly specific roles, administration becomes cumbersome and harder to maintain. On the other hand, oversimplified roles can compromise security by giving users broader access than they need. Finding the right balance is an ongoing challenge. - Overlapping roles and risk of over-privileging
As organizations grow, it’s common for employees to accumulate multiple roles over time. When roles and permissions overlap, users may end up with over-privileged access, meaning they can perform actions beyond their responsibilities. This not only increases the security risk but also creates compliance issues if access rights aren’t regularly reviewed and pruned.
Examples of RBAC
Role-Based Access Control (RBAC) streamlines permission management by assigning access based on organizational roles. This ensures employees only get the access required to perform their responsibilities, helping reduce unauthorized access and safeguard sensitive data. Here are some practical scenarios where RBAC plays a key role:
- Access to HR Platforms
In HRMS tools, HR managers can handle confidential functions such as salary updates, performance evaluations, and onboarding records. Regular staff, on the other hand, are limited to viewing personal details like payslips, leave balances, or tax forms. This separation preserves data privacy while keeping workflows efficient. - Controlled Access in IT & DevOps
In DevOps ecosystems, permissions are tightly aligned to technical roles. Developers and engineers are granted access to testing environments, CI/CD pipelines, and server logs, while non-technical teams such as HR or Finance are restricted entirely. By limiting visibility and actions, RBAC prevents misconfigurations and strengthens system security. - Role Segmentation in Finance Systems
Financial applications like ERP platforms use RBAC to differentiate access. Finance managers can approve transactions, update payment records, and generate reports. Meanwhile, auditors are restricted to read-only access, allowing oversight without the ability to alter data. This balance ensures compliance, security, and a transparent audit trail.
MAC vs DAC vs RBAC: Side-by-Side Comparison
When choosing the right access control model, it helps to see how they differ side by side. The table below highlights the key distinctions between MAC vs DAC vs RBAC across control, flexibility, security, and usage, making it easier to understand which model best fits different environments.
| Sr. No | Feature | MAC (Mandatory Access Control) | DAC (Discretionary Access Control) | RBAC (Role-Based Access Control) |
|---|---|---|---|---|
| 1 | Who controls access | Access is strictly controlled by system policies. | Access is controlled by the resource owner. | Access is managed through roles defined by administrators. |
| 2 | Who sets permissions | Permissions are enforced only by the system administrator. | Permissions are granted or revoked by the resource owner. | Permissions are assigned through role configurations by admins. |
| 3 | Can users change access | Users cannot alter their own permissions. | Users can freely change permissions on their resources. | Permissions change when a user’s role is updated. |
| 4 | How flexible it is | Very rigid with almost no flexibility. | Highly flexible as owners can adjust access anytime. | Moderately flexible through role-based adjustments. |
| 5 | Security level | Highest level of security, ensuring strict data confidentiality. | Lowest level of security. Permissions can be carelessly managed by end-users, leading to risks like privilege escalation or accidental data exposure. | Offers a strong balance of security and usability by following the principle of least privilege, which reduces the risk of excessive permissions. |
| 6 | What access is based on | Determined by security labels and classifications. | Determined by ownership and sharing preferences. | Determined by organizational roles and responsibilities. |
| 7 | Use case | Military, intelligence, and government systems where data confidentiality is paramount. | Typical user-centric operating systems like Windows and Linux, and collaborative platforms like Google Docs. | Enterprise-level applications and systems, such as banks and hospitals, where managing access for a large number of employees. |
How to Choose the Right Access Control to Implement in Your Organization
Selecting the right access control model isn’t a one-size-fits-all decision. It depends heavily on your organization’s size, industry, compliance needs, and available resources.
-
Small and Medium Businesses (SMBs):
SMBs often lack dedicated IT teams and resources, making them more vulnerable to cyber threats. In fact, 43% of cyberattacks target SMEs (Accenture). For such businesses, DAC or MAC, or RBAC is often more practical since these models are easier to configure and manage without large IT overhead. However, strict policy enforcement is key to preventing accidental over-permissioning. -
Enterprises:
Larger organizations manage thousands of employees, departments, and external vendors. For them, RBAC works best as it provides structure and scalability. In highly sensitive environments (like defense or finance), MAC is often implemented to meet compliance and ensure the highest level of security. -
Industry-Specific Scenarios:
Defense contractors may require MAC for end-to-end operations due to the sensitivity of classified information. Retail and restaurant chains often benefit from RBAC, allowing secure access for employees, suppliers, and partners while protecting sensitive customer data.
At the end of the day, there’s no single winner among DAC vs MAC, vs RBAC. Instead, organizations often adopt a hybrid approach, deploying MAC for mission-critical systems, RBAC for structured workforce access, and DAC for less sensitive, collaborative environments.
Questions to ask before choosing
Selecting the right access control approach isn’t just a technical decision; it’s a strategic one that affects security, compliance, and user productivity. Before committing to MAC or DAC, or RBAC, organizations should ask themselves:
- What level of security is required?
If your environment handles highly sensitive or classified data, strict system-enforced policies (MAC) may be necessary. For less sensitive contexts, DAC or RBAC could strike a better balance. - Who should control permissions?
Do you need system administrators to enforce every rule (MAC)? Or should resource owners have the flexibility to grant access (DAC)? If role-based consistency is key, RBAC offers centralized governance with less administrative overhead. - How dynamic are user roles and responsibilities?
In fast-moving organizations where roles evolve frequently, RBAC can simplify updates by assigning access through roles instead of individuals. - What compliance standards must be met?
Some industries, like defense, healthcare, and finance, demand strict adherence to regulatory frameworks. Matching your model to compliance obligations is crucial to avoid risk. - How important is scalability and ease of management?
As teams grow, individually managing permissions (DAC) becomes impractical. RBAC provides scalability, while MAC ensures uniform security across the system. - Is collaboration or strict control more important?
DAC supports collaboration and user-driven sharing, but at a higher risk. MAC enforces rigid boundaries, while RBAC balances governance with efficiency.
Consult with our IAM experts to find the best fit for your organization. Whether you prioritize airtight security, flexible collaboration, or scalable governance, we help you design and implement an access control strategy that aligns with your unique needs.
Best Use Cases for MAC, DAC, and RBAC
Each access control model is designed with specific strengths, making it suitable for different organizational needs. While all three approaches aim to secure data and systems, their effectiveness depends on the level of security required, the size of the organization, and how permissions need to be managed. Here’s when each model works best:
-
Choose DAC when you want maximum flexibility and control at the user/resource-owner level
Discretionary Access Control puts the reins in the hands of the resource owner. This model relies on access control lists, making it easy for document creators or department leads to grant and manage privileges quickly. It is conceptually simple and highly responsive to evolving business needs, allowing owners to adjust permissions without involving administrators. However, this flexibility comes with trade-offs: the potential for over-privileged users and ambiguous sharing pathways can introduce security risks. -
Choose RBAC for small teams with stable, well-defined roles
Role-Based Access Control streamlines permission management by binding access rights to roles rather than individual users. It’s ideal for organizations where responsibilities and structures are clear, grant access by role, and everyone aligned with that role automatically inherits the correct permissions. This not only supports scalability but also ensures consistency across teams, reducing error and overhead. Although a robust internal hierarchy is needed, RBAC balances governance with efficiency effectively. -
Choose MAC when your organization operates in the military, government, or defense sectors
Mandatory Access Control enforces centralized, policy-driven access rules that users cannot override, perfect for environments where strict classification, compartmentalization, and auditability are non-negotiable. With security labels and kernel-level enforcement, MAC prevents unauthorized sharing and keeps boundaries airtight. Though less flexible and heavier to manage, its rigid structure is invaluable for safeguarding high-impact, sensitive data in regulated contexts.
Real-World Examples of Access Control Models
Access control models are applied differently across industries depending on security needs, collaboration requirements, and compliance demands. Understanding real-world use cases can help organizations choose the right model for their environment.
- Finance
In financial institutions, access control is a cornerstone of data protection. RBAC helps segment roles, account managers, auditors, and compliance officers, and each gets access tailored to their responsibilities. For critical systems like trading platforms or payment gateways, MAC ensures only cleared personnel can execute or approve high-value transactions. This dual use strengthens compliance with regulations like PCI-DSS while minimizing fraud risks. - Education
Academic environments often rely on DAC for collaborative flexibility. Faculty members and students can share lecture materials, research files, or project documents while controlling who can view, comment, or edit. At the same time, RBAC supports Learning Management Systems (LMS), where administrators, teachers, and students each get role-specific access. This ensures efficiency in managing coursework while protecting sensitive student data. - Cloud/SaaS
Modern cloud and SaaS platforms leverage RBAC to manage large user bases across multi-tenant environments. Customers, admins, and support teams are assigned role-specific permissions, ensuring streamlined operations without overexposure of data. For highly sensitive functions, such as system configuration or master admin controls, MAC is layered in to restrict access to only a handful of authorized users. This hybrid model balances usability with robust security.
Final Thoughts: Which Is Right for You?
MAC vs DAC vs RBAC models each bring distinct advantages. MAC delivers maximum security for highly sensitive environments, DAC offers flexibility for collaborative teams, and RBAC ensures scalable, structured access for growing organizations. The key is matching the model, or a hybrid approach, to your organization’s security needs, compliance obligations, and operational realities.
At Tech Prescient, we help businesses design and implement access control strategies that balance security, usability, and compliance.
Get secure, efficient, and compliant access for your team, every time.
Talk to our access control specialists and see how Tech Prescient can optimize your access management strategy:
Frequently Asked Questions (FAQs)
1. What are the main differences between MAC, DAC, and RBAC?
MAC enforces access through strict, system-defined policies, leaving no room for user overrides. DAC gives resource owners control to decide who can access files or applications. RBAC organizes permissions around predefined roles, making access easier to manage across teams.2. Which access control model is most secure?
MAC is the most secure because it enforces centralized, non-discretionary policies. RBAC also offers strong security by standardizing permissions across roles. DAC is the least secure since it relies on individual owners to manage access, which can lead to mistakes.3. When should I use MAC vs DAC vs RBAC?
Use MAC in environments where protecting high-security or classified data is critical. DAC works well for teams that need flexibility and quick sharing. RBAC is ideal for enterprises that want structured, scalable access based on roles.4. Can you combine MAC, DAC, and RBAC?
Absolutely! Many organizations adopt hybrid models to get the best of all worlds. You can enforce strict security with MAC, allow flexibility with DAC, and manage large teams efficiently using RBAC.5. How does RBAC improve compliance?
RBAC ties permissions to roles instead of individuals, making audits faster and easier. It reduces human error by standardizing access across the organization. This approach helps meet GDPR, HIPAA, SOX, and other compliance requirements.6. Is DAC less secure than MAC and RBAC?
Yes, because DAC puts access control in the hands of owners. While this is flexible, it can lead to over-permissioning or accidental exposure of sensitive data. Proper oversight is needed to keep DAC secure.7. Which is better: MAC, DAC, or RBAC?
It depends on your priorities. Choose MAC for maximum security, DAC for flexibility and user-driven control, and RBAC for scalable, role-based access in enterprise environments.