Identity & Access Management Strategy: Complete 2026 Guide

Identity and Access Management (IAM) strategies are essential elements of modern cybersecurity. An IAM strategy outlines the principles for how your organization governs digital identities, authenticates users, and manages access to systems, applications, and even data. IAM comprises four distinct components, namely, identification, authentication, authorization, and monitoring. IAM is the foundation for initiating, capturing, recording, and managing users' identities and their respective access permissions through which it ensures access privileges are assigned in accordance with policy and that all users and services are authenticated, authorized, and audited appropriately.
The rapid adoption of cloud computing, hybrid/remote work arrangements, and complex threat environments necessitate a holistic IAM strategy to protect systems, enable compliance, and deliver a consistent, seamless experience for users. A strong IAM strategy includes more than simply whether or not a user is allowed to access information resources; it provides the foundation for a unified access framework that protects your organization's most sensitive assets, insists on least privilege, automates identity life cycle management, and requires close adherence to Zero Trust. In a multi-cloud environment, this means it is focused on reducing risk while enabling agility and productivity.
Key Takeaways:
- An IAM strategy mitigates data breaches by mandating strong identification, least privileged access, and active monitoring.
- It helps organizations to comply with regulations, such as GDPR, HIPAA, and SOX, by following policies and audit requirements.
- It improves productivity by automating identity lifecycle processes, which include onboarding, offboarding, and access requests.
- It embraces Zero Trust security in that it continuously verifies every user, device, and access request -- not just the traditional perimeter.
What is an Identity and Access Management Strategy?
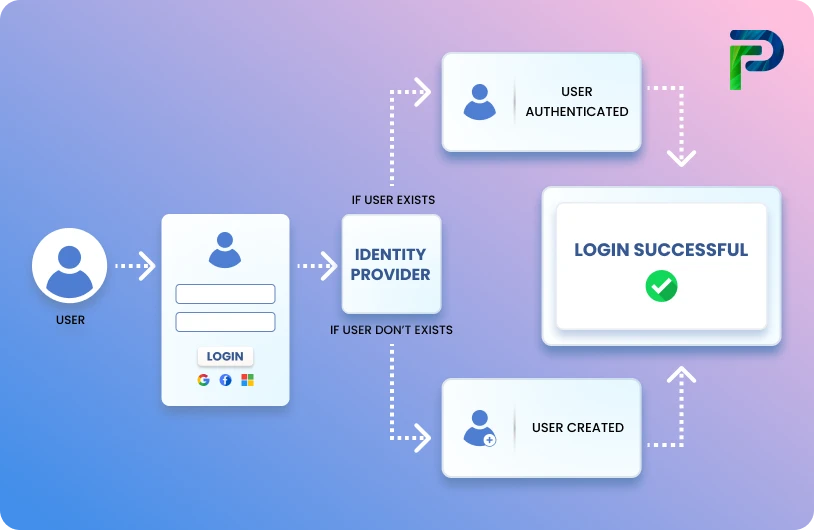
Identity and Access Management (IAM) strategy refers to a set of cybersecurity practices incorporating policies, procedures, and technology that establish and manage digital identities while controlling access. The purpose of an IAM solution is to ensure that only authorized persons, whether employees, partners, or devices, can access the organization's applications, data, and systems, and to avoid accessing those resources by anyone unauthorized from doing so thereby avoiding security breaches to happen. An IAM strategy is more than just a set of disconnected tools; an effective IAM strategy formalizes an enterprise's processes to establish a consistent, secure, compliant, and scalable access across the enterprise, while aligning people with technology.
An IAM strategy fundamentally encompasses five core functions:
1. Identity Provisioning – This refers to the creation, modification, and removal of the digital identity. The provisioning function ensures seamless creation of accounts and roles when onboarding a new employee, and it ensures that accounts are quickly removed when the person leaves. Automated provisioning can reduce human errors and prevent orphaned accounts, which attackers look to compromise.
2. Authentication – Authentication assures that a user, system, or device is truly who they say they are. Authentication can be everything from simple passwords to more complex mechanisms like multi-factor authentication (MFA), biometric scanning, or adaptive MFA, which considers factors like device, location, and time of access. Good authentication mechanisms are the first line of defence against credential theft.
3. Authorization – Authorization is the process of determining what an authenticated identity can do in systems, applications, or data environments; it enforces rights and permissions based on organization policy, allowing users access only to the allowable actions or resources for their role or context. As organizations attempt to enforce the least-privilege access, authorization can use mitigating factors found in role-based access controls (RBAC), attribute-based access controls (ABAC), and/or Just-In -Time (JIT) access, to grant the minimum permissions only when the user requires.
4. Governance - Governance is the control layer of an IAM strategy. It assures access controls are enforced according to business policies, regulatory compliance, and risk appetite. Governance takes the oversight form of planning Segregation of Duties (SoD) rules, completing periodic access reviews, and managing privileged access accounts that could be misused. Policy enforcement is a critical component of governance and seeks to define and enforce both organizational and regulatory policies with respect to user access. Policies aim to ensure permissions are suitable, have an auditable presence, and comply with regulations. Governance converts IAM from a technical control into a compliance enabler.
5. Auditing & Monitoring - Continuous monitoring and auditing track who accessed what, as well as when and how. These functionalities can provide security and accountability through anomaly detection, alerts for suspicious behavior, and auditing and reporting for regulatory purposes. Monitoring completes the IAM lifecycle loop by delivering visibility and continual improvement.
Together, governance, auditing, and monitoring form the foundation of an IAM strategy, allowing the organization to govern access ergonomically while supporting the business's needs and compliance.

Why is an IAM Strategy Important in 2025?
In 2025, an IAM strategy is no longer an option but a requirement because cloud adoption, hybrid work, and insider threats have widened the attack surface. Reports state that compromised credentials rose 160% in 2025, now responsible for one in five data breaches. Security is still the pressing issue: unauthorized access is still one of the top 3 causes of breaches, and compromised credentials made up nearly 50% of breaches in many reports. A good IAM strategy will implement strong authentication options (MFA and adaptive to access), least privilege will prevent over-permissioning, and centralized monitoring for capturing anomalies and possible breaches.
- Regulatory Compliance
Even in a normal business environment, IAM strategies not only protect data, they drive compliance in an era of increased regulation, including GDPR, SOX, and HIPAA, among others. Regulators expect organizations to account not only for access being controlled but also for access being periodically reviewed, documented, and auditable. IAM supports the compliance process and achieves this by providing audit trails, access certifications, and creating governance workflows like a role-based access review process, while helping to lower compliance expenses and enhance compliance with a lower risk of being levied a penalty. - Efficiency
IAM strategies can enable organizations to identify tangible efficiencies by automating the onboarding and offboarding process with provisioning and deprovisioning processes that streamline the onboarding and offboarding of employees, contractors, and third parties. Instead of allowing IT groups to manually onboard dozens of apps, users get access on the first week of their employment first day, old and irrelevant accounts are retired quicker, reducing friction and risk to the organization. - Business Alignment
Finally, IAM strategies tie into business transformation strategies that support the secure adoption of cloud services, SaaS, and hybrid infrastructure. By employing an IAM strategy with zero-trust principles, organizations can support their innovation economy and fast-track innovation without compromising security. This is a crucial balance in today's digital-first economy.
Key Components of a Robust IAM Strategy
Developing an efficient Identity and Access Management (IAM) strategy is all about defining security, compliance, and usability. Each area plays its role, but together they provide a framework to govern how sensitive information is protected - compliance, enforceability, and business continuity planning.
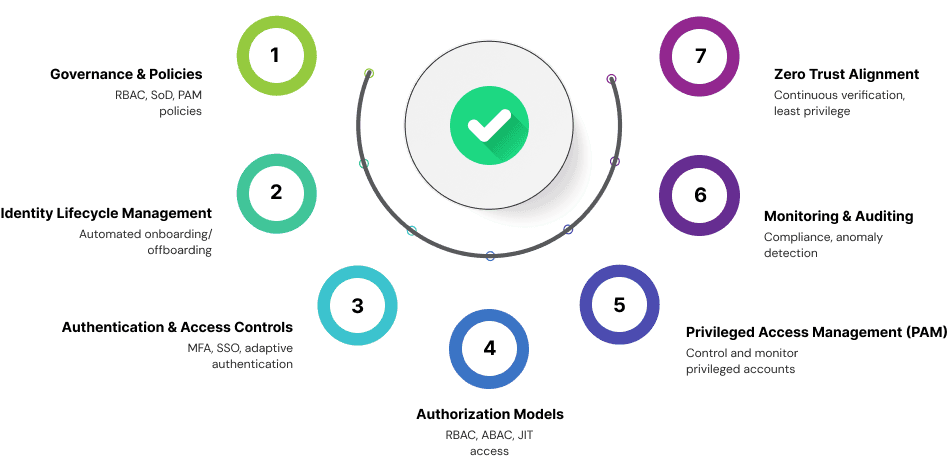
1. Governance & Policies
Governance is the basis for building strong IAM policies. Governance covers policies around Role-Based Access Control (RBAC) as the basis for ensuring that access is based on job function and not a blank check; Segregation of Duties (SoD) to mitigate the conflict of interest from sensitive tasks being divided among varying users; Privileged Access Management (PAM) policy either defines a segregation of duties master policy or high-level admin rights. If you clearly define governance, you begin the process of making IAM not just a technical implementation but an organizational decision.
2. Identity Lifecycle Management
An Identity needs to be managed constantly as it transitions in the organization. Identity management covers onboarding to off-boarding. Automated provisioning allows new employees or contractors to gain timely access to the tools they need, while automated de-provisioning allows organizations to limit "orphaned accounts" that attackers exploit. Lifecycles also include moving employees within an organization, so identify management has the capacity to prevent the "carryover" of entitlements.
3. Authentication & Access Controls
Authentication is your first layer of defense. A solid IAM (Identity and Access Management) strategy does not rely solely on passwords or even passwords plus MFA (Multi-Factor Authentication) - other factors in your strategy may include Single Sign-On (SSO) and a more adaptive stream of authentication. Adaptive authentication uses multiple contextual factors in the logon process, like device, location, and time of access, to validate the logon attempt, which minimizes credential theft and operational friction of a secure experience.
4. Authorization Models
Now that identity is authenticated, you must consider the authorization process, which determines what a user can do. IAM strategies will commonly use Role-Based Access Control (RBAC) as the base level for identity and access management deployment, with consideration of finer grained control with Attribute-Based Access Control (ABAC) which takes into consideration an contextual factors that may inform a decision on whether a user is granted access, to Just-In-Time (JIT) access which enables elevated rights for a limited timeframe, to mitigate remaining standing privileges. Operating in a controlled manner simplifies the management of rights that allow users to have access to only the identity and resources for which they are empowered.
5. Privileged Access Management (PAM)
Privileged accounts such as administrator, root, or service accounts have elevated access levels that are potentially catastrophic if compromised. PAM offers more control over privileged accounts through elevated security: requiring step-up authentication, multi-approvals, and justifications before access. A majority of today's PAM solutions are very capable of enforcing time-bound and task-specific privileged accounts (Just-in-Time access). This assures that users do not have elevated rights indefinitely. Session recordings and command logging enable IT/security teams to see exactly how they are used, making it easier to detect misuse and compliant evidence.
6. Monitoring & Auditing
IAM strategies that do not employ robust monitoring capabilities are blind to account misuse. Continuous monitoring records data on information like log-on attempts, access requests, and user activity, and allows security teams to see anomalies like large spikes in downloading data or a user accessing a resource from suspicious geographies. Automated alerting and the ability to have things like Splunk or Microsoft Sentinel plug-ins allow real-time notifications and action. Auditing goes hand-in-hand with monitoring and creates immutable records of what users accessed, when, and how. Audit logging is important for compliance frameworks like GDPR, HIPAA, SOX, and ISO 27001; however, architecture compliance may require immutable logs that could provide forensic evidence for incidents.
7. Zero Trust Alignment
Zero Trust is not a choice anymore; it is a baseline assumption for modern IAM. Every request is verified continuously, regardless of the origin (inside/outside). IAM accomplishes this through adaptive authentication (checking device, location, and all risk signals) and least privilege. For example, an employee who accesses HR systems on their office laptop may be granted direct access, while an access request on the same user from a personal device from another country may prompt MFA or complete blocking. By implementing IAM in a Zero Trust model, organizations can limit the attack surface further and make identity the strongest part of the security perimeter.
Steps to Build an Effective IAM Strategy
Establishing an IAM strategy isn't simply a technical development exercise; it is a systematic development process that balances security, compliance, and user experience. A successful strategy develops in phases. This goes from assessing the current state, to development, and then to ongoing evaluation and improvement. The following are the key steps to be followed by any organization that aims to develop an effective IAM strategy.
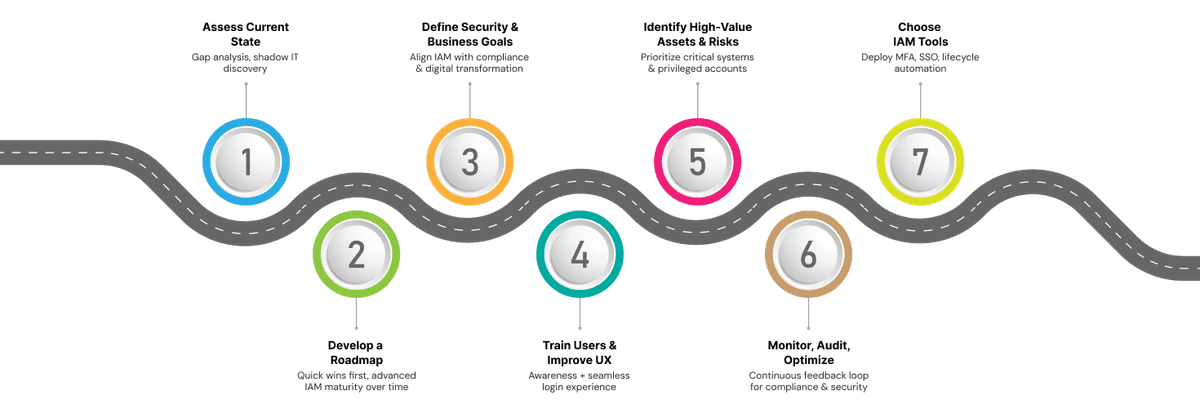
Step 1 - Analyze the Current State
To start, evaluate the identity landscape across the organization. This includes the IT infrastructure, applications, data, and users to see what needs to be protected, and who needs to access it. A baseline assessment will highlight gaps with authentication, provisioning and deprovisioning, and compliance posture. It may also identify shadow IT, which is unsanctioned apps or services that employees adopted without IT approval and allow for risk by being outside of the governance and monitoring process. Identifying over-permissioned accounts and non-integrable systems in this step allows your IAM program to start with a clear and unique view of vulnerabilities.
Step 2 - Define Security & Business Goals
Creating an IAM strategy is not simply about limiting unauthorized access; it must clearly state what an organization intends to achieve. The directories for those goals will vary, and could include security improvements through reduced likelihood of credential misuse, compliance with certain frameworks (e.g., GDPR, HIPAA, or SOX) increased user experience through fast, low-friction access, etc. These goals may also include operational efficiencies too, like lessening onboarding time through automated provisioning, or even secure support for cloud utilization. Establishing IAM objectives that lead to both security outcomes and business-driven suitability value ensures that your IAM strategy has measurable value that supports effective risk reduction, compliance readiness, and workforce performance.
Step 3 - Identify High-Value Assets and Threats
Not every system has the same level of threat value. Develop a map of the critical applications, sensitive data elements (customer records, intellectual property, etc), and privileged accounts, which are often among the first targets an attacker will go after, because of the level of access those have. Knowing what your threats are and how they relate to the business will allow you to implement IAM controls in a prioritized way, govern where it matters, and spend on security as efficiently as possible.
Step 4 - Select IAM Tools
The tools you select will help with automation, efficiency, scalability, and improve security posture. Look for IAM platforms that include features like multiple factor authentication (MFA), single sign-on (SSO), facilitate and manage role-based access, and integrate with human resource management systems, as well as cloud or third-party tools. At TechPrescient, we help organizations understand their IAM needs and risks, and connect your access management in a business context while using IAM for Zero Trust and compliance.
Step 5 - Develop Roadmap
A successful IAM roadmap should find the right balance between quick wins and long-term projects. The initial steps are to implement basic functionalities such as multi-factor authentication (MFA),** single sign-on (SSO)**, and privileged access management (PAM) that will better establish a security baseline. If your environment is complex or hybrid, your second step (there's no clear sequence of steps) would be to develop an identity fabric to create a unified access management framework across your cloud and on-premise systems. Equally important to align IAM with your organisation, is to ensure that the IAM solutions you select are fully compatible with your existing human resource (HR) platform and integration with other primary business applications, to enable scalable and sustainable IAM.
Step 6 - Train Users and Improve UX
Everyone in your organization needs to adopt IAM if it is going to move the needle. Start with security awareness training, simplify user login experiences using SSO, and when implementing MFA, ensure that user experience does not become friction-laden. Balancing security and usability reduces the resistance to adoption and ultimately generates higher levels of compliance throughout the employee workforce.
Step 7 - Monitor, Audit, and Optimize Continuously
IAM is not "set and forget". IAM is not a "set and forget" capability. A matured strategy is going to require continuous monitoring of authentication events, access requests, and privileged activity to identify abnormal behavior in real-time. Regular audits also validate compliance regulations such as GDPR or SOX, while performance reviews can show bottlenecks in onboarding, access provisioning or integrations. Thinking of IAM more like a living program means it evolves with new threats, user needs, and business goals.
Common IAM Strategy Mistakes to Avoid
Even the most successful Identity and Access Management strategy can fall short if it overlooks common missteps that organizations repeatedly make. Most mistakes occur when organizations consider IAM a standalone IT project rather than an enabling factor of security and governance for the enterprise. If they can address these upfront, they should instill confidence that their IAM will be resilient, compliant, and be able to align with the business objectives.
1. Treating IAM as Only IT’s Responsibility
One of the biggest missteps is establishing IAM to only reside in the IT department. While, of course, the IT function will implement and maintain the platform, IAM is an activity that the IT function does not own entirely. IAM extends across the entire organization, from HR onboarding, compliance reporting to day-to-day productivity. Excluding all relevant business units, risk teams, and compliance from the IAM conversation ensures all access policies are technical and not business-driven. Technical access policies create unwanted friction for end users, blind eyes for audit, and added risk for user-generated events. A quality IAM strategy should involve cross-functional ownership and governance committees across the business, IT, and security teams.
2. Over-Permissioning and Absence of Least Privilege Enforcement
It is typical for employees to gain access privileges over time without undergoing any type of review. Users are typically granted broad entitlements "just in case" or do not lose any old permissions when they transition into a new position. Over-permissioning is commonly known as privilege creep, and the risk of escalating the attack surface posed by insider threats and external attackers who have access to the accounts is considerable. IAM strategies that do not enforce least privilege and/or periodic access reviews leave an organization exposed to these types of compliance violations and data breaches. Just-in-time (JIT) access and automated entitlement reviews provide greater confidence to organizations that access permissions will remain closely aligned with business needs.
3. Poor Integration with HR or Cloud-based Systems
IAM does not operate in a silo. Poorly integrated HR systems result in redundant access not being provisioned or deprovisioned promptly, resulting in onboarding delay or orphaned accounts created when employees exit an organization. And cloud-based application access is not integrated, creating blind spots since sensitive SaaS-centric environments are uncontrolled yet centrally governed. A lack of integration creates finger-pointing for security teams when fragmented identity needs to be managed. While it takes time and presents challenges, security teams want to avoid having duplicate effort when quickly addressing the disconnect of a fragmented identity. Seamless connectors to HR systems, Enterprise Resource Planning (ERP)systems, and cloud systems are a must for seamless end-to-end identity lifecycle management.
4. Disregarding Governance and Compliance Obligations
Organizations typically include the IAM program in authentication (SSO, MFA) consideration, but do not incorporate all of the governance capabilities that IAM supports: segregation of duties (SoD), entitlement certifications, and audit-ready reporting- to name a few. The intent here is not to find fault, but to highlight that this can be costly, particularly for organizations in regulated industries where the organization is expected to demonstrate proper controls over access. Yes, an organization can pass a simple security exam; however, that does not mean the organization is compliant, particularly with all of the possible ramifications, such as penalties or reputational risk when attempting to complete a compliance audit. When you layer all of the governance elements into the IAM program, you synchronize the access with the operational requirements, and the external regulations such as GDPR, HIPAA, and SOX, so security and compliance both operate in lockstep.
📌Note: That's where Identity Governance is so important, by including some governance elements into your IAM program, you can ensure that access aligns with business process and regulation elements. At TechPrescient, we help organizations extend IAM with governance, thus creating a state of continuous compliance, audit readiness, and risk-aware identity decisions.
IAM Strategy Roadmap for 2025 and Beyond
Identity and Access Management has graduated from overseeing logins and is establishing itself as thought leadership for enterprise security in a cloud-first and AI-accelerated world. As threats proliferate and regulations mount, enterprises must look ahead and design IAM strategies that are fundamentally resilient today and stand resilient to future risks. Here are some of the key trends impacting IAM strategy for 2025 and beyond.
- Role of AI & Automation in IAM
AI and machine learning are helping to shift IAM from enforcement-based reactive security to proactive security through defense-based IAM strategies. Automated anomaly detection enables the continuous monitoring of user behaviour and flags suspicious activities such as logging from high-risk geographies, privilege escalations, and bulk downloading of data (even if they normally wouldn't be considered problematic from a compliance perspective). AI-driven IAM platforms can eliminate static rules in favour of dynamically adaptive policies and automate real-time alerts to security teams. Identity becomes the first line of defense against APT and other advanced threat actors. - Cloud Infrastructure Entitlement Management (CIEM)
The world of cloud adoption has made it one of the hardest challenges for IAM to manage entitlements across AWS, Azure, and GCP. Traditional IAM tools cannot handle the complexity of cloud-native permissions that can number in the thousands. Solutions for CIEM help security teams get transparency into cloud entitlements, identify excessive permissions, and enforce least privilege across multi-cloud. In 2025, CIEM will be a critical component of any IAM roadmap to reduce the risk of misconfigurations and shadow admins in the cloud. - Continuous Authentication & Behavioral Biometrics MFA and passwords don't cut it anymore for sensitive systems. IAM is heading toward continuous authentication, meaning that access does not end at login, but is continuously reassessed throughout a session. Behavioral biometrics like typing speed, cursor movements, or mobile sensor data allow IAM systems to verify a user's identity silently behind the scenes. If some form of anomaly occurs, the IAM system can raise the bar for authentication and/or terminate access altogether in real time.
- Zero Trust Maturity Alignment
Zero Trust has gone from buzzword to baseline strategy, but a number of organizations remain early in their adoption. IAM is integral in establishing the Zero Trust maturity path by enforcing least privilege, verifying every request by context, and integrating with endpoint, network, and data security tools. An IAM strategy aligned to 2025 is much more than just implementing MFA and SSO. It's about continuous validation of trust and aligning identity with business risk, while closing the gap between access and governance. Effectively, IAM becomes a control plane to operationalize Zero Trust and identity management across the enterprise.
Final Thoughts
Identity Access Management no longer represents a background IT function, but rather is a strategic pillar of risk management. An IAM approach is about much more than keeping attackers out; it is about compliance, user productivity, and establishing the foundation for ultimately applying a Zero Trust model. With digital transformation accelerating, IAM must change to accommodate hybrid environments and multi-cloud workloads, as well as the ongoing AI-enabled threat landscape.
At Tech Prescient, we help companies avoid IAM tool implementations and instead help design an IAM strategy that leverages IGA and automation and the tenet of Zero Trust principles to ensure your security is resilient and future-proof. If you want to increase your identity security posture for 2025 and beyond, we would be happy to be a guide for you on this journey.
NEXT STEPS
IAM is the foundation, but IAM + IGA unlocks true identity security.
With Tech Prescient’s Identity Confluence, you can unify access, automate reviews, and stay audit-ready
- Get started faster → Learn more about Identity Confluence
- See it in action.
Frequently Asked Questions (FAQs)
1. What is an IAM strategy?
An IAM strategy is a structured approach to securely managing digital identities and authentication, and providing secure access to systems and resources. An IAM strategy defines the policies, processes, and technology that will define who is allowed access to what resources, who has the correct permissions, and when.IAM is all about defining who can use what one to ensure that the right users access the right resources at the right time.
2. What are the 4 pillars of IAM?
The four pillars of IAM are Authentication (verifying identity), Authorization (providing appropriate access), Administration (maintaining user accounts and roles), and Auditing (monitoring access and ensuring compliance). Those four pillars create the basic elements of secure identity.3. What is the difference between IAM & IGA?
IAM is about enabling and controlling access to resources (governance and compliance); meanwhile, IGA (identity governance & administration) has additional oversight, governance, and compliance requirements. IGA is about ensuring that access is appropriate, and the access is kept in accordance with organizational policies and regulatory standards.4. What are IAM strategy best practices?
Best practices can include the use of multi-factor authentication (MFA), adopting Zero Trust concepts, enforcing least privilege access, and implementing ongoing audits to identify anomalies or misuse of policy. These points will also help with security overall, but also operational efficiency.5. Is there an IAM strategy template or PDF?
Yes, many organizations do use IAM strategy templates or PDFs to document their roadmap and define their policies for compliance. These templates and guidance documents help to provide a structured approach to implement and manage IAM effectively across the enterprise.