Identity and Access Management Framework: A Complete Guide

Introduction
An Identity and Access Management (IAM) Framework represents a combination of policies, processes, and technologies in order to provide controlled access to the right resources to authorized users while preventing access to unauthorized users. This digital identity governance framework takes into account security threats, compliance obligations, and operational efficiencies all at the same time.
The challenge of accessing what resources, by whom, has become an increasingly critical issue for security, compliance, and operations. Organizations encounter these issues at the same time they are managing more and more sensitive data in support of their missions across a growing number of disparate systems (e.g., cloud services, enterprise systems). An identity and access management governance framework provides an overall construct to help manage access controls across the enterprise.
Key takeaways:
- 5 foundational elements from identification to security compliance
- Upgraded security, compliance, cost savings, and user satisfaction
- End-to-end identity lifecycle management from onboarding to deprovisioning processes
- IAM policy framework, Zero Trust IAM application, and automated provisioning
- AI/ML anomaly detection, blockchain identity, and contextual access
What is Identity and Access Management?
Identity and Access Management (IAM) is a security framework that determines who gets access to what resources, under what conditions, and for what duration. IAM is an approach to digital identity security that is made up of policies, technologies, and processes that ensure the proper access by an individual to systems, applications, and data. Identity management framework, or ID management, or IdM, ensures only validated users, whether they are individuals or devices, can access specific applications, components, and systems for which they are authorized to do so.
IAM frameworks do this by managing digital identities for all entities within an organization. Users (i.e., human users, employees, and contractors), devices, applications, bots, and automated systems. When considering the various types of identities that enterprise IAM solutions manage, it is important to think of an identity access management framework that would allow for the proper authentication, authorization, and auditing of every access, whether the access request is from a person or a machine.
IAM security frameworks will first adhere to and second maintain core security principles. The principle of least privilege allows users only the access they need for the job they are in. Newer identity governance framework solutions use a centralized identity database to store all information in a single solution, making user identity management much easier to manage, allowing users to have consistent access across all systems of the organization.
Why Organizations Need an IAM Framework
Without a strong identity management framework for compliance, organizations risk unauthorized access, data breaches, and compliance failures. An identity and access governance framework addresses four critical business challenges:
1. Enhanced Security - Protects against identity-based breaches and insider misuse
According to Secureframe's 2025 Data Breach Statistics report, 46% of all breaches are associated with personal customer information. IAM security is the first line of defence. The framework establishes several levels of security with multi-factor authentication, behavioural analytics, and continuous IAM risk management.
For example, if a nurse is attempting to access patient records at an unusual pairing (i.e. location) at 2 AM, the access control framework will recognize this incident differently, and would typically ask for another verification, and notify the security teams for possible investigation—not allowing the patient data access with just 1 or 2 pieces of identity proof, mitigating risk while allowing access for legitimate emergencies.
Advanced analytics identify atypical user behaviour, which allows security teams to act quickly before incidents can escalate. The IAM governance model also applies segregation of duties controls to ensure no one user can complete high-risk transactions on their own.
2. Compliance Assurance – Meets regulatory requirements with proper access governance
IIAM frameworks allow organizations to follow essential regulatory standards. Identity and access management policy frameworks provide the appropriate structural controls, auditing processes, and access governance that regulators require. Today's compliance and access control regulations even go so far as to monitor who accesses sensitive data, how access to sensitive information is granted and monitored, and how organizations can prove they are protecting personal information. Digital identity governance frameworks address all these regulatory requirements through automated policy enforcement, comprehensive auditing of user activity, and regular access governance review.
The most common regulatory standards include:
HIPAA (Health Insurance Portability and Accountability Act): Implements appropriate safeguards for patient data, controlling access to sensitive health information with detailed audit trails required for healthcare compliance.
ISO 27001 (Information Security Management): Supports certification by establishing comprehensive identity governance framework policies and systematic access control documentation.
SOX (Sarbanes-Oxley Act): Enables compliance by establishing proper controls over financial systems access, ensuring segregation of duties, and maintaining accurate records of user activities.
Additional Regulatory Alignment:
- GDPR: Enforces data protection through controlled access and comprehensive audit trails
- PCI DSS: Secures payment card data with role-based access controls
- FISMA: Meets federal information security standards with robust authentication and access management
- NIST Framework: Aligns with cybersecurity best practices for comprehensive risk management
Enterprise IAM solutions provide automated compliance reporting and continuous monitoring capabilities, helping organizations avoid regulatory fines, pass audits more efficiently, and demonstrate adherence to industry standards through detailed access governance documentation.
3. Cost Optimization - Automates provisioning and reduces admin overhead
IAM implementation provides substantial savings through automation and intelligent automation. By removing manual, time-intensive IT tasks that routinely require the involvement of IT staff or personnel, automated tasks save money in spending on operational overages and minimize mistakes made by humans. Identity and access management framework self-service capabilities minimize cost by having users accomplish routine tasks in place of higher-cost help desk capabilities.
Key areas of cost reduction include:
- Automated Provisioning & Deprovisioning: Avoid the need for a manual onboarding process (like our process that takes about 3-5 hours per new employee). For example, when a new sales representative joins the sales team, IAM will provision access to CRM, email, and collaboration tools, taking into account the project they will work on.
- Automate Access Controls: Solutions use machine learning to facilitate access request approvals while enforcing security standards.
- Reduced Administrative Burden: Using self-service/self-help reduces help desk calls for password resets and access requests; it is estimated that 40% of all help desk calls are password resets.
According to the Gartner report, organizations achieve a return on investment of up to 300% over three years through eliminating duplicate access rights, achieving optimized software licensing, and reducing the risk of compliance violations.
4. User Convenience - Offers smoother access via Single Sign-On (SSO) and self-service features
IAM frameworks eliminate common access friction points. Single Sign-On allows users to authenticate once and access multiple applications seamlessly, reducing password fatigue while maintaining security.
For example, a marketing manager logs in once and immediately accesses their email, project management tools, social media platforms, and analytics dashboards without additional authentication prompts. Self-service portals enable users to request new access, reset passwords, and manage profiles without IT intervention.
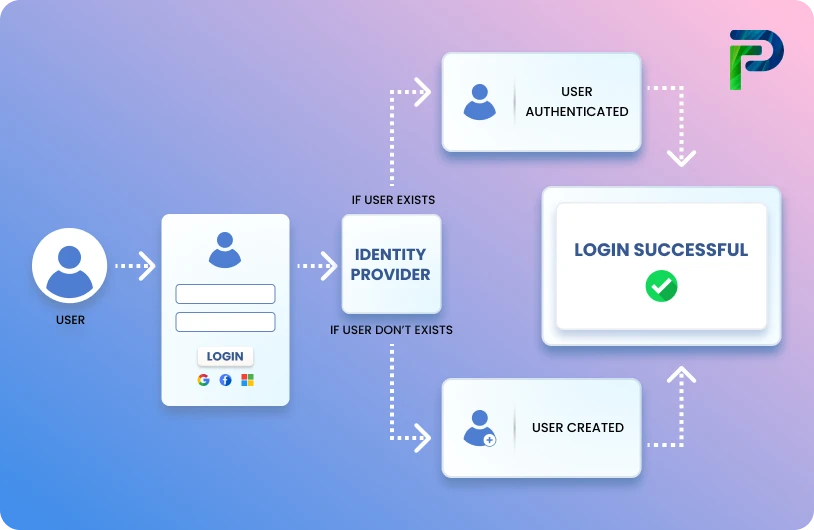
How Does the IAM Framework Work?
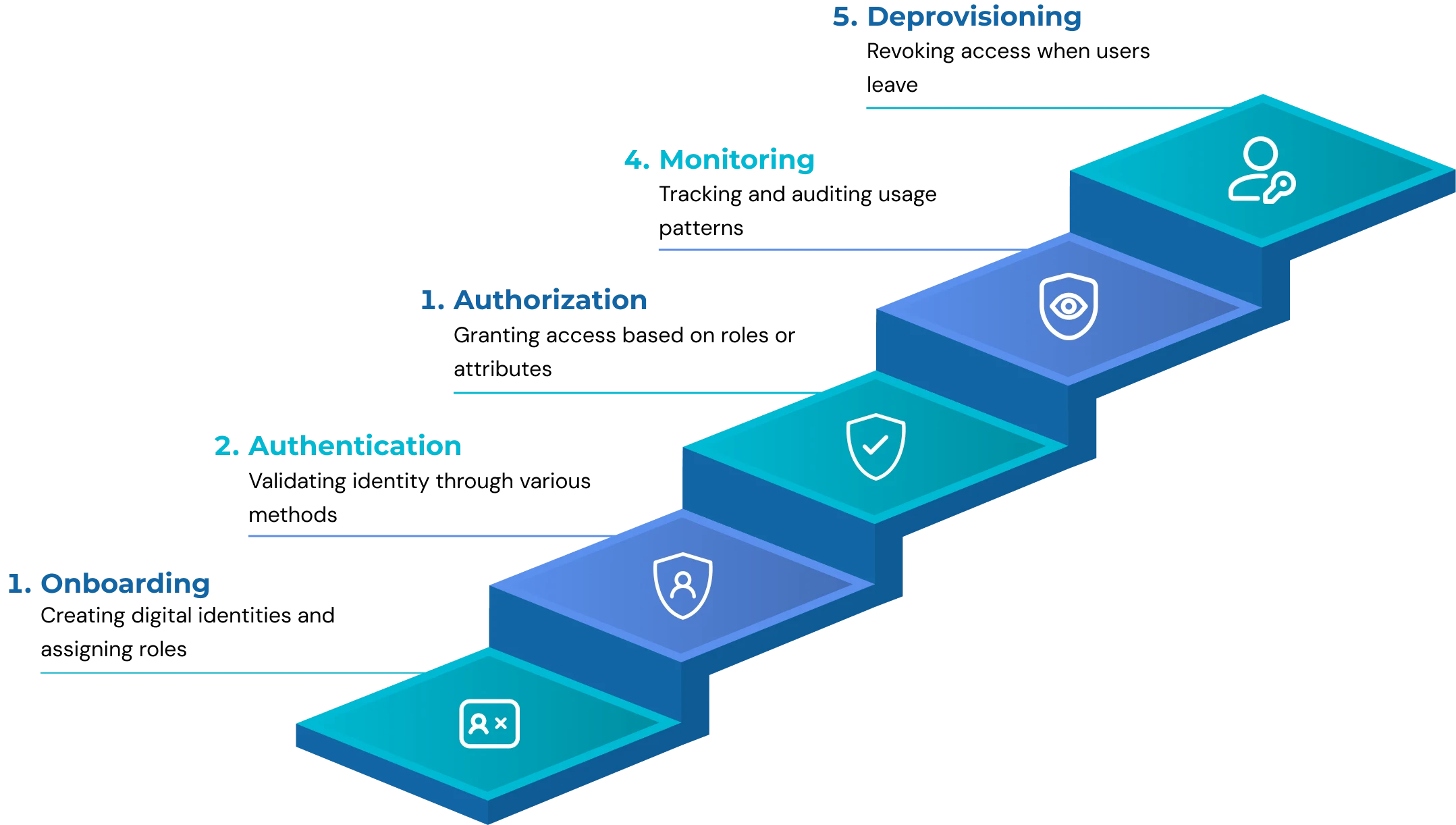
The IAM framework operates through five distinct lifecycle stages, as illustrated in the accompanying diagram. Each stage builds upon the previous one to create comprehensive identity governance:
Step 1. Onboarding: Creating digital identities and assigning roles
The identity lifecycle management begins when new users join the organization. IAM frameworks create unique digital identities, including employee ID, department, job function, and manager relationships. Role assignment occurs through predefined templates that align with job functions.
For instance, when a new financial analyst is hired, User Lifecycle Management automatically ingests HR data from systems like Workday, creates their digital identity, and provisions access to financial reporting tools, spreadsheet applications, and compliance databases based on their role template.
Step 2. Authentication: Validating identity through passwords, biometrics, or MFA
Authentication is the confirmation of user identity prior to gaining access to a system. Modern digital identity frameworks support a variety of mechanisms, including:
Multi-Factor Authentication (MFA): MFA generally requires multiple factors to confirm identity before granting system access. For example, a bank teller typically enters their PIN, has their fingerprint scanned, and receives a push notification to their mobile device.
Risk-based authentication: Risk-based authentication takes contextual considerations into account when adjusting authentication requirements. For example, accessing email from the office may need the simple authentication mechanism, and then a request for even more verification may be triggered when accessing the same system from a foreign country.
MFA provides a stronger baseline of security, often through the use of more than one factor. Risk-based authentication is basically making MFA smarter by only requiring multiple verification items when necessary, so it weighs security against convenience for the user.
Step 3. Authorization: Granting access as per role or attributes (RBAC/ABAC)
Once identity is verified, authorization determines resource access permissions:
Role-Based Access Control (RBAC) is a security model that limits access to systems through the assignment of permissions to predetermined roles instead of to individual users. Users are assigned a role, or roles, and the permissions that comprise a role grant the user specific access. The security model bolsters security, requires the user to utilize a role, and applies the principle of least privilege to assign the user only access that is necessary to perform their job role/functions. For example, all accounting managers access the financial reporting systems, the budgeting tools, and the audit databases with the same permissions as determined by their "Accounting Manager" role. When an accounting manager is hired by the company, instead of configuring the permissions specific to them, they'll simply be assigned the role of "Accounting Manager". The corporate world generally embraces consistency by having many employees fill similar roles within the organization, so this benefits them to the extent they can utilize roles to easily manage the category of roles or group of employees when a role has changed or if new employees are added.
Attribute-Based Access Control (ABAC) provides a flexible approach to access control decisions that can be based on a range of attributes, which may incorporate user characteristics, resource properties, environmental conditions, and contextual information. Whereas role-based access controls are based on roles, ABAC evaluates attributes at runtime to inform the permission status on the object.
For example, a consultant can access client information only during business hours (time attribute), on company devices (device attribute), and for projects assigned (resource attribute). If any of these attributes are violated – e.g., trying to connect at midnight or from a personal laptop – the ABAC system would automatically deny access.
Tech Prescient brings it all together with Identity Confluence and makes RBAC and ABAC easy through Business Role & Policy Management. Teams use visual, low-code policy builders to create rules and automate/apply rules for clear guidance and enforcement. Tech Prescient automatically updates access and privileges as roles and project-level changes happen or attributes change. This means organizations reduce over-provisioning of access, the least privilege is ensured, and there is good, clear auditability that enables governance and makes security as business-friendly as possible.
Step 4. Monitoring: Tracking and auditing usage patterns
Continuous monitoring tracks authentication attempts, access grants, and user activities. Advanced capabilities include real-time anomaly detection and automated alerting for policy violations.
Identity Analytics & Risk Insights leverage machine learning to score user risk and highlight anomalies. When a user suddenly accesses sensitive data they've never touched before, the system flags this for security review.
Step 5. Deprovisioning: Revoking access when users leave the system
The lifecycle concludes with immediate access revocation when users leave or change roles. Automated Provisioning & Deprovisioning integrates with HR systems to disable accounts across systems, including Salesforce, Azure AD, and Google Workspace when employment status changes.
This prevents orphaned accounts, a major security risk in organizations where former employees retain system access.
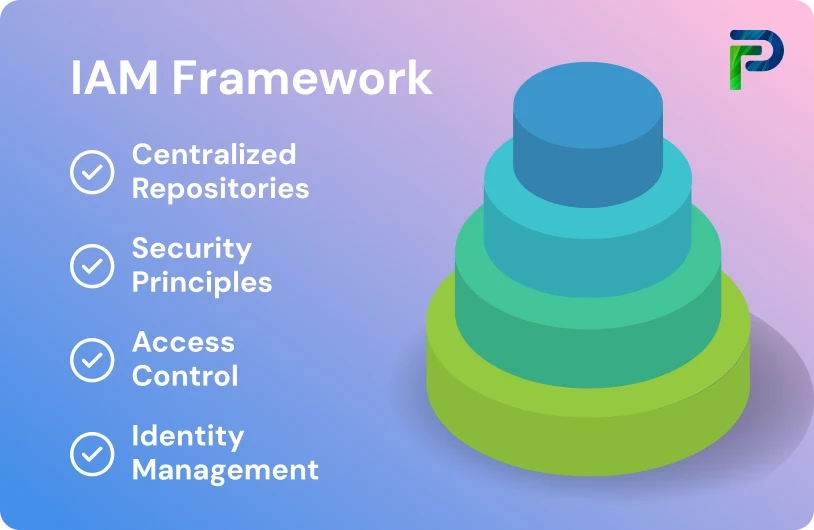
5 Key Components of an IAM Framework
The IAM framework, as shown in the centralized architecture diagram, rests on four fundamental pillars that work together to provide comprehensive identity security:
1. Identification
Identification is the basis of every IAM function, as it creates a unique identity for every entity that requires access to a system. Each of these entities has a distinct digital identity in the real world, the digital world, or both. An identity can be for a user, device, application, or automated system.
- For Users, Identification will generally involve attributes like employee ID, email address, department, job title, and relationships to managers. Each of these identifiers will be unique to each user and across every connected system.
- For Devices, Identification will involve using hardware characteristics such as MAC addresses, device certificates, or unique device identifiers. All of these hardware identifiers operate the same way every time they connect to a network so that the device can be uniquely identified on the network. This ensures the device is authorized and can access organization resources.
- For biometric identification, this involves recognizing a unique identifier by collecting and analyzing: fingerprints, facial features, voice block patterns, or behaviour characteristics. These methods are proving to be one of the most granular pieces of identity establishment that is not easy to copy (or transfer) from one person to another. Biometric identification is proving to be the most prevalent, accepted, and reliable method for establishing Identification, which explains its area's focus on which approaches to take in highly secure environments or mobile access.
- Federated identification allows users to take advantage of existing and accepted identities from trusted external providers, with the organization still having control over the security and audibility facets of Identification in support of modern collaboration scenarios.
2. Authentication
- Single Sign-On (SSO) streamlines the authentication process, so users only have to authenticate once with a trusted identity provider, and then they securely receive tokens granting them access to systems, apps, and websites without additional sign-on prompts. This reduces password fatigue as SSO applications always identify who you are as a user, while enabling centralized enforcement of security policies.
- Multi-Factor Authentication (MFA) adds important layers of security through requiring multiple verification factors. Modern Multi-Factor Authentication often uses push notifications to mobile devices, codes sent through SMS or voice, hardware tokens, mobile authenticator applications, and biometric verification (fingerprint or voice).
- Adaptive Authentication changes the security that is required, with extra verification when suspicious actions or conditions are known, requiring the user to respond, thus retaining strong security while allowing low friction for daily access.
- Certificate-based Authentication provides the greatest level of security for privileged access and system integrations. Authentication based on certificates uses cryptographic certificates to establish an identity with mathematical certainty.
- Combined Security Framework: Once SSO and MFA are in place, you have built a strong security framework that supports a level of convenience and protection from possible security issues. As businesses strive to find their way through the complexities of the digital world, layering approaches using multiple authentications ensures unique and reliable protection against complex and evolving cyber risks. The layering security approach allows organizations to provide seamless and productive access for users while managing strong security controls where it matter.
3. Authorization
Authorization governs what authenticated users can access and what actions they can perform within Organizational Access Management Systems:
- Role-Based Access Control (RBAC) simplifies authorization by grouping permissions into organization specific roles. For instance, if a user requires authorization to a set of applications and/or data to perform their job function, those permissions are aggregated into one or more roles in conjunction with the users' job responsibilities. This role-based hierarchy can rapidly scale with the growth of the organization.
- Least Privilege Principles provide users with only the minimum amount of access required to perform their job functions. Least Privilege helps minimize the scope of impact by limiting a user's access to only the access required in the event of account compromise or insider threats. Access reviews also assist in identifying excessive permissions that may be granted to users over time in order to remediate any excessive permissions.
- Attribute-Based Access Control (ABAC) is the most granular means of access decisions, and permits a decision based on multiple attributes including user attributes, resource sensitivity, environmental context, and business rules. ABAC enables the organization to use dynamic policies in complex scenarios while maintaining a manageable policy environment.
- Just-In-Time (JIT) Access provides temporary escalated permissions only when needed, and has the automatic ability to revoke access after the period of time has expired or the task has been completed. JIT Access also further minimizes the amount of standing privileges provided to users.
4. Monitoring & Auditing
Monitoring and auditing provide the visibility and accountability to maintain security posture and demonstrate compliance with regulatory obligations.
- Activity Logging captures detailed records of authentication attempts, access grants, permission change events, and other administrative actions. Activity logging must be tamper-proof, searchable, and retained according to organizational and regulatory obligations.
- Real-time Monitoring can immediately point out security incidents and policy violations enabled by behavioural analytics and machine learning algorithms identifying abnormal activities. More advanced products can even identify subtle changes in user behaviour that may indicate a compromised account or insider threat.
- Compliance Reporting generates the documentation needed for regulatory audits and internal governance. The ability to customize reports according to specific compliance frameworks is important, and reports should be generated automatically on a routine basis to reduce administrative effort.
- Anomaly Detection uses advanced analytics to look for unusual access pattern recognition, including out-of-hours behaviours, unexpected applications being used, and unauthorized resource access attempts. This pre-emptive form of security will alert security teams prior to runaway incidents.
5. Security & Compliance
Security and compliance capabilities help ensure you can implement IAM that doesn't exceed your organization’s appropriate levels of risk for sensitive data and systems and is compliant with organizational operational obligations:
- Encryption Protection secures identity data while in flight and at rest with standard industry best practices for cryptography that protect authentication credentials, personal information, and access control data against unauthorized disclosure.
- Regulatory Alignment ensures that IAM implementations address specific regulatory compliance mandates such as GDPR data protection, HIPAA healthcare privacy, SOX financial controls, PCI DSS payment protection, and industry compliance matters.
- Insider Threat Monitoring utilizes predictive analytics to effectively identify behavioural traits over time that could signal malicious insider behaviour or compromised account activity. This includes flagging activities for unusual data access requests, activity outside normal operational hours, and something considered a privilege escalation.
- Third-party Access Control extends the entities' security governance to external sources who are gaining limited (contractor, vendor, partner) access to organizational resources. This encompasses time-limited access, more enhanced monitoring, and robust segregation from the organizations internal organizational systems.
Benefits of an Identity and Access Management Framework
1. Risk Mitigation – Prevents unauthorized access and insider threats
Comprehensive identity governance mitigates organizational risks with several layers of security. The real-time risk assessments allow organizations to identify potential threats, even before they manifest as an incident. Advanced analytics can identify unusual behaviour patterns which can indicate when accounts are compromised or when there is an insider threat where the organization may be at risk.
A pharmaceutical company leverages IAM, for instance, to identify when a researcher accesses competitive intelligence databases they had never previously accessed, to initiate automatic security reviews.
2. Cost-Effectiveness – Automates provisioning and reduces overhead
Automation removes the manual processes that take up a lot of an organizations' IT resources. With automated provisioning, new users get the access they need right away, and automated deprovisioning makes sure that there are no security risks that could come from an old, inactive account.
Self-service is part of an automated process that removes the administrative burden of the tasks that can easily be done on their own. This improves the user's productivity and lowers the help desk costs, but it also frees up the IT group's time, allowing them to focus on critical issues like corporate initiatives.
3. Enhanced Incident Response – Faster detection and remediation
Detailed audit trails provided by the IAM system facilitate the ability to rapidly vet security incidents. When a security incident does occur, detailed logs allow teams to quickly assess the scope of a breach or compromise and perform the necessary remediation actions.
Connection to SIEM systems provides aggregated and correlated threat intelligence that enhances the enablement of incident analysis and response.
4. Improved User Experience – Seamless access with strong security
Modern frameworks remove user frustrations while providing satisfactory security measures. Single Sign-On minimizes password fatigue and enhances productivity in the workplace. The self-service capabilities allow users to manage their accounts through easy-to-use, self-service portals that reduce dependency on IT.
The mobile-friendly interface allows users to access resources from any device and location and work flexibly without sacrificing security.
Implementation Strategy & Best Practices
Define clear Identity and Access Management Policy Frameworks
Tech Prescient's Identity Confluence provides Business Role & Policy Management with visual RBAC/ABAC policy builders that simplify large-scale access control. The platform seamlessly alters access bundles when roles or departments change, allowing for worry-free policy compliance.
Good policies provide sound rules concerning access provisioning, authentication obligations, and review activities in accordance with business requirements and compliance obligations.
Automate provisioning and deprovisioning to eliminate ghost accounts
User Lifecycle Management is a process that automates joiner, mover and leaver processes by ingesting HR events from systems like Workday and SAP. Automated Provisioning & Deprovisioning provides access across systems at the time of hire and removes access at the time of termination using pre-built connectors and just-in-time provisioning.
It removes security risks from orphaned accounts and helps reduce the direct cost on administration while keeping access rights in line with organizational changes.
Implement Zero Trust principles with continuous verification
Identity Analytics & Risk Insights use machine learning to score user risk, flag anomalies, and identify unused entitlements. This supports Zero Trust principles and allows for continuous verification, as it is capable of identifying potential breaches before they even occur.
As a foundational element of Zero Trust, assume you trust nothing implicitly - and that every access request must be verified - no matter whether the user is within your network or their access has previously been approved. This means strong identity verification with continual monitoring.
Align with compliance standards through integrated architecture
Integration-Ready Architecture includes SCIM, REST APIs, SAML, and OAuth, so it can easily integrate with any HRMS, IdP, or custom applications. Identity Confluence's unique, integration-ready features provide flexibility with regard to deployment models (SaaS, on-premise or hybrid), are designed for compliance and can be provisioned quickly.
Access Reviews & Certifications (a planned feature) will provide one-click attestation and exportable reports for SOX, GDPR, and HIPAA compliance to help auditors streamline the audit process.
Future of IAM Frameworks
AI/ML-driven anomaly detection
User behavior patterns are analyzed by machine learning algorithms to look for anomalies that indicate potential security threats. Advanced analytics examines elements of subtle behavioural change that other technologies may miss, such as changes in access patterns over time that indicate a potential compromise of an account.
Predictive analytics aids in the ability to be preventive by identifying users who require an increased level of scrutiny, based on risks and behavioural patterns.
Contextual & Just-In-Time Access
Just-In-Time provisioning provides temporary elevated permissions on an as-needed basis and then automatically revokes any access after task completion. This approach reduces standing privileges and the attack surface.
Contextual controls consider the relevant criteria of location, device trust, network trust, and business context in making access decisions, allowing organizations to create complex/advanced security policies while keeping usability intact.
Cloud Infrastructure Entitlement Management (CIEM) Integration
CIEM takes IAM one step further by extending it to maintain visibility and control over permissions for cloud resources across multi-cloud environments. This integration is critical as organizations are relying more on cloud services to conduct their missions.
By integrating traditional IAM and CIEM, we can have a unified identity governance capability in both on-premise and cloud environments, while ensuring identity security policies are consistently enforced for all resources, regardless of where they reside.
Real-World Applications by Industry
Healthcare Sector
A regional hospital system employs IAM to ensure immediate physician access to patient records during emergencies and compliance with HIPAA. The use of break-glass access procedures provides multifactor emergency access and allows for all emergency access attempts to be logged within the IAM system, with a full post-event review process. The system will always log an attempt to access patient records in an emergency, but will require a justification within 24 hours to ensure accountability, while never compromising patient care. The IAM approach reduces emergency response time and provides for the full patient record audit trail required for the various healthcare compliance and regulatory inspections.
Financial Services
A community bank employs IAM for SOX-compliant access controls with appropriate segregation of duties. The loan approval process calls for multiple approvers, and no single employee can both initiate and approve a large transaction. The system routes large loan applications to the appropriate approvals based on the amount and risk level. The automated workflow extends to regulatory compliance, decreasing processing and turnaround times, and eliminating any opportunity for an unauthorised transaction, which would impose huge financial and regulatory penalties.
Manufacturing
An automotive company has broadened IAM to general Internet of Things devices on the factory floor, treating sensors and automated supervising systems as identities that require authorization and authentication to avoid the possibility of industrial espionage or sabotage. For every connected device, there is a unique digital certificate, and for every device, there are boundaries under which the device will have access to certain networks and data systems. This model protects proprietary manufacturing processes and guarantees that only authorized systems can communicate with relevant production equipment, preserving security and business continuity while maximizing productivity.
Conclusion
An established Identity and Access Management Framework builds trust, enhances productivity, and assures regulatory compliance. When organizations are focused on Governance, Automation and Security, they can safeguard their digital ecosystem while providing a seamless user experience.
A modern IAM framework manages complex identity management demands presented by Hybrid and Multi-Cloud environments, and meets regulatory compliance and security best practices. As it relates to information systems Security ROI, the strategic benefits provided by IAM are not limited to security; operational efficiencies, user satisfaction, and business enablement are equally attractive outcomes.
Start with a solid governance framework, choose IAM solutions that can scale, and continue to monitor access to remain proactive against threats. IAM is both a process and a product, and commitment is needed to implement technology and organizational change management, but full identity governance will provide improved security, decreased costs, and increased operational efficiencies.
Ready to get started?
See how our AI-powered platform, Identity Confluence, can automate your identity governance by implementing these components with visual policy builders and automated workflows.
Frequently Asked Questions (FAQs)
1. What are the 5 key components of IAM?
Identification, Authentication, Authorization, Monitoring & Auditing, and Security & Compliance. These components function together to provide end-to-end identity security, from the creation of distinct identities through security monitoring and regulatory compliance.2. What is an Identity and Access Management Governance Framework?
It ensures IAM processes are aligned with business policies, compliance requirements, and risk management objectives. Governance frameworks provide strategic governance to build and confirm that implementations align with organizational goals while maintaining appropriate security controls.3. What is an example of IAM in action?
A financial organization using privileged access management to restrict admin-level permissions. When a database administrator needs elevated access, the system verifies identity, checks risk factors, grants temporary access with full logging, and automatically revokes access after the maintenance window.4. How long does IAM implementation take?
Modern cloud-based solutions can also be rolled out quickly, much faster than traditional enterprise solutions. The project delivery time varies depending on the complexity of the organization and the degree of integration required. Standard applications will enable fairly simple deployment, which can be completed in weeks. Complex enterprises with many legacy systems are likely to take several months.5. What ROI can organizations expect?
Organizations generally experience a 300% return on investment in 3 years based on the decreased operational costs, improved security posture, and lowered compliance risks. This ROI is driven by automating manual processes, reducing help desk tickets, and avoiding expensive security breaches.