What Is Discretionary Access Control (DAC)?

Discretionary Access Control (DAC) is a decentralized model where the resource owner determines who can access it and what level of access they have. In this approach, the subject controlling a file, document, or system object can grant or revoke permissions, share it with others, and even define attributes for newly created objects, all without requiring central administrator approval. Practical examples of DAC appear in tools like Google Docs, where you decide who can view or edit a document, in smartphone applications, and in common operating systems.
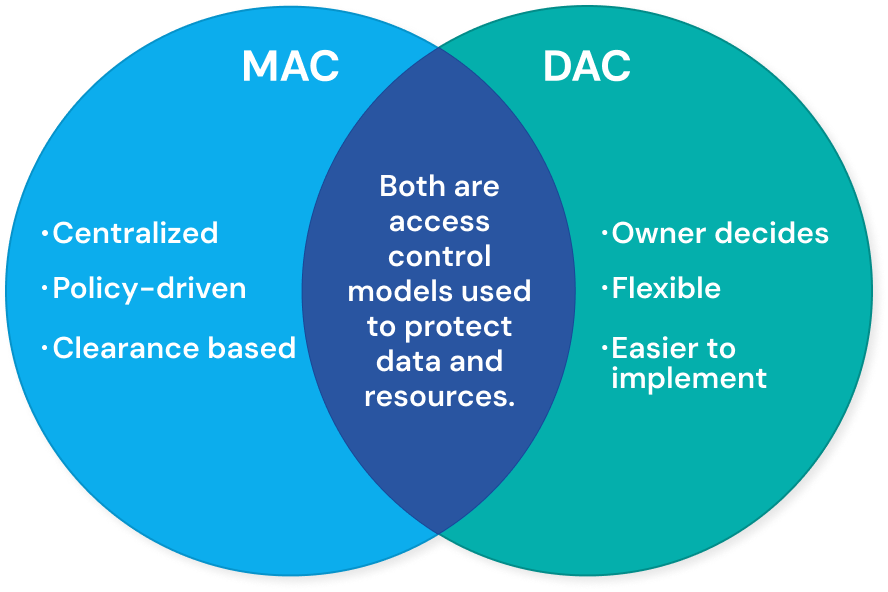
Unlike Mandatory Access Control (MAC), which enforces strict policies through a central authority, Discretionary Access Control (DAC) gives resource owners flexibility and autonomy. In DAC systems, subjects can share information, grant privileges, modify object attributes, or define attributes for new objects, all without central authorization. This allows quick adjustments and different forms of access control that are generally not possible in MAC. While MAC sets policies centrally via clearance levels, DAC lets object owners decide who can access and modify their resources. The trade-off, however, is that such freedom can create security risks if permissions are not carefully managed.
A 2025 market analysis shows that while Role-Based Access Control (RBAC) leads the access control market, Discretionary Access Control (DAC) is a favorite among environments where teamwork and flexibility matter. It’s especially common among small and mid-size organizations and makes up a big part of the USD 12.01 billion global access control market, which is expected to reach USD 25.15 billion by 2034. This mix of autonomy and flexibility is why DAC works so well for user-driven collaboration. Up next, we’ll look at how it works, where it shines, where it can pose risks, and how it stacks up against more rigid models like MAC.
Key Takeaways:
- DAC puts resource owners in control, enabling identity-based permissions
- It’s highly flexible and promotes collaboration, but can introduce security vulnerabilities
- Common in everyday tools, including OS file systems, enterprise cloud platforms, and mobile apps
- Ideal for agile, low-regulation settings; less suited for strictly controlled or highly sensitive environments
- Often supplemented by structured models like RBAC within IAM frameworks for better governance
What Is Discretionary Access Control (DAC)?
In Discretionary Access Control (DAC), the security model allows the resource owner to define who can access the resource and specify the actions they are permitted to take, such as read, write, or execute. Control over these permissions is generally maintained through access control lists (ACLs) or configured within application settings. To see how DAC compares with another model, check out our MAC vs DAC comparison guide.
DAC operates on the principle that the resource owner has full discretion over who is granted access. First introduced in the Orange Book by the Trusted Computer System Evaluation Criteria (TCSEC), DAC is widely implemented in operating systems and network resources. Most discretionary access control examples incorporate accountability features, such as logging user access and tracking resource modifications. Overall, DAC provides granular control over access to sensitive information, helping safeguard critical data from unauthorized individuals. You can perform the following types of discretionary access control:
- Create user roles to control which users can perform operations on which database objects. Control who can create databases.
- Prevent unauthorized users from registering user-defined routines.
- See Security for external routines (UDRs).
- Control whether other users besides the DBSA can view executing SQL statements.
How Does Discretionary Access Control Work?
In Discretionary Access Control (DAC), the resource owner, whether it’s a file, folder, or database, decides who can access the resource and what actions they are allowed to perform. When a user requests access, the system validates their credentials (such as a username, password, or cryptographic keys) to confirm identity and then grants the appropriate permissions defined by the owner. Because control is “discretionary” the owner can grant, adjust, or revoke permissions at any time, determining not only who can access the resource but also the extent of their privileges, such as read, write, modify, or share. This makes DAC highly flexible and user-driven, though it also introduces potential security risks since protection largely depends on how carefully owners manage and distribute credentials.
For example, in personal computer operating systems, file access can be limited by granting certain privileges to specific users. These rights often include Read (R), which allows you to examine a resource without making any changes; Write (W), which allows you to create or edit material; and Execute (X), which allows you to run files, programs, or applications. To observe DAC in action, it's necessary to understand how such rights are granted and maintained.
- Permissions set by owner, not system admin
In any discretionary access control example, access regulations are defined by the resource's owner, who determines access terms. It all comes down to user identity, which is validated using the credentials provided during the login procedure. Whoever provided credentials would be permitted access. The owner may establish a username and password that will let the user in, and they can choose who will receive these credentials. - Control via ACLs, file permissions, or sharing panels
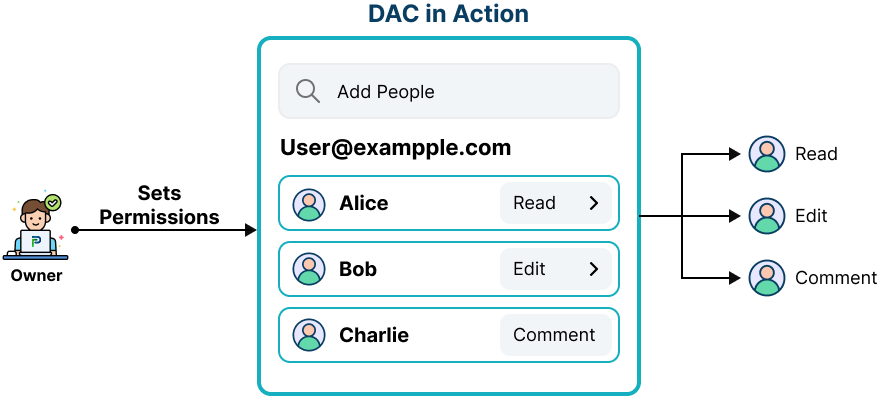
Discretionary access control is an identity-based access control mechanism that allows users to govern their data. Data owners can set access rights for single users or groups of users. An Access Control List (ACL) stores the access rights for each piece of data. When a user provides access, the administrator generates this list, which can also be created automatically. An ACL lists the people and organizations who have permission to access data, as well as their access levels. A system administrator can also use an ACL as a security policy to prohibit normal users from changing it. - Easy grant/revoke with immediate effect
DAC is considered discretionary since the resource owner can give or revoke access to the information in issue. It is more than just allowing access; the owner may specify the type of access the user has and what they can do with it. Because not all employees require the same degree of access, separate user profiles with particular credentials can be developed to provide for changing access types as needed.
A practical example of DAC is Google Docs sharing, in which the document author determines who may access, comment on, or change the file, or Unix chmod commands, in which the file owner grants read, write, and execute rights to certain users or groups. In both circumstances, the resource owner has complete discretion over granting or denying access at any time.
Advantages and Disadvantages of DAC
When it comes to managing who can access specific resources, discretionary access control provides a range of advantages worth considering.
The main benefits of DAC systems include:
While every access control model has its strengths and limitations, DAC stands out for balancing usability with control. Its design makes it easier for resource owners to manage access without heavy administrative effort, offering practical advantages such as:
1. Flexibility: With DAC, users may specify rights for specific items. Object owners can divide users into groups, allowing for more precise control over access settings, and mandatory access control systems do not allow for this.
2. Speed and efficiency: Discretionary controls allow data to flow freely over networks. Users can provide access to objects by clicking a button. There is no need to build complicated user profiles or clearance levels for new personnel.
3. Low burden on administration: Decentralization means that object owners govern access, which reduces administrative burden. Administrators are not required to manage access control profiles for each user and each resource. Instead, consumers decide how they want to obtain information when they need it.
4. Simple policy management: administrators only need to provide users with object access rights. Discretionary access technology is very easy to utilize with the correct ACL management solutions.
When speed and ease of use are top concerns, these advantages make a discretionary security system alluring. Smaller businesses or organizations that handle less sensitive data are frequently a suitable fit for DAC.
Disadvantages of DAC
Discretionary access control has drawbacks despite its advantages. These are the key points to remember.
1. Security: Above all, it is acknowledged that mandatory access control is more secure than DAC. Attackers may use discretionary access to infect target access points with malware. Users may be given undue access due to privilege creep. Users may provide too much access. Or they could not be aware of what they are consenting to.
2. Absence of visibility: Decentralization may result in a lack of administrative visibility and confusion. Security personnel must be aware of who is using private resources. Discretionary controls can result in security flaws and problems with compliance since they are difficult to monitor and manage.
3. Maintenance: Object owners are responsible for keeping ACLs up to current and relevant. As ACLs and networks develop, they may lose effectiveness. For example, access control lists may include access privileges for former workers. Alternatively, it may fail to update with user roles.
DAC vs MAC: What’s the Difference?
MAC and DAC handle security, flexibility, and user control in different ways. Knowing these differences helps you choose the model that best fits your company’s needs.
| Feature | DAC | MAC |
|---|---|---|
| Control | Access is managed by the resource owner, who decides who can view, edit, or execute the resource. | Access control is managed and enforced by system administrators and the operating system. |
| Flexibility | Highly flexible, allowing owners to grant, modify, or revoke permissions at any time. | Very limited flexibility, as permissions are fixed according to strict security classifications. |
| Security | Provides low security, with risk depending on how carefully the owner manages access. | Provides very high security, as policies are centrally controlled and difficult to bypass. |
| Use Case | Works best for environments that prioritize collaboration and general office work. | Works best for sectors like government, military, or regulated industries where strict control is essential. |
| Example | In Google Docs, the file owner can choose who to share the document with and decide whether they can view, comment, or edit it, giving the owner direct control over access. | In a military clearance system, access to classified documents is based on security clearance levels. For example, only personnel with “Top Secret” clearance can open certain files, regardless of who created them. |
Real-World Examples of DAC in Use
DAC is a common feature in both consumer and enterprise applications. In many cases, users interact with discretionary access systems without even realizing it. Here are some practical examples:
- Smartphone app permission prompts (contacts, camera): When installing or using smartphone apps, owners decide which applications can access functions such as the contacts directory, GPS, or camera. These permissions reflect DAC in action, as the user chooses when to allow or restrict potentially insecure operations.
- Unix/Linux file commands (chmod, chown): Most operating systems rely on DAC for file management. In UNIX or Linux, commands like chmod and chown let object owners set read, write, or execute privileges. Owners can also hide file attributes or deny access without proper authentication.
- Google Workspace document sharing: Platforms like Google Docs apply DAC by letting document owners create access control lists (ACLs). Some users may be given write permissions, while others have view-only access. The owner can also delete the document or close the project at any time.
- Dropbox, Slack, and similar collaboration platforms: Collaboration tools often use DAC to manage shared resources. Owners determine who can view, edit, or share files, ensuring the right people have the right level of access while keeping control over the content.
When Should You Use DAC?
While discretionary access control isn’t ideal for organizations handling extremely sensitive or regulated data, it works well in environments where collaboration, speed, and adaptability matter more than rigid security rules. Its ability to let resource owners control permissions on the fly makes it practical for smaller or less-regulated setups.
- Small businesses with ad-hoc projects
For companies with around 10–20 employees and limited IT staff, DAC reduces complexity. It allows owners to share files, tools, and databases without constant admin intervention, keeping operations smooth and costs low. - Academic and research teams
Universities, research labs, and project-based study groups benefit from DAC’s flexibility. Team leads can quickly grant or adjust access to datasets, papers, or experimental results as needs change. - Low-regulation environments
In industries without heavy compliance requirements, DAC offers the freedom to share information without getting bogged down in strict approval processes. This is ideal for creative agencies, startups, and small service providers. - Collaborative Projects:
In team environments where documents, code, or other resources must be shared, Discretionary Access Control (DAC) makes it simple to grant, adjust, or revoke permissions, enabling smooth and efficient collaboration. - Personal Computing:
In operating systems such as Windows and Linux, Discretionary Access Control (DAC) governs file and folder permissions, giving users the ability to decide who can access their personal data and how it can be used. - Specific Applications:
Discretionary Access Control (DAC) is widely used in applications that require content sharing, such as Google Docs or Facebook groups, where the creator manages who can view, edit, or comment. It also supports cross-functional teams working on shared content, from collaboration platforms like Google Docs to shared drives in Dropbox, by enabling users to co-edit documents, upload files, and modify permissions in real time, while ensuring the content owner maintains final control.
How DAC Fits Into the Cybersecurity Landscape
Discretionary Access Control (DAC) offers flexibility, granting resource owners the ability to manage permissions directly, but it should not stand alone. In the modern DAC cybersecurity landscape, DAC must be integrated into Identity Governance and Administration (IGA) and IAM systems to deliver both usability and governance.
- Fits alongside RBAC for structured access.
DAC complements Role-Based Access Control (RBAC) by allowing resource owners to fine-tune permissions within the structure of roles. While RBAC defines who needs what access broadly, DAC access control lets owners adjust permissions at the object level, creating a balance between structure and flexibility. - Works within IAM/IGA frameworks.
When embedded in IAM or IGA platforms, DAC becomes part of a governed workflow. Access decisions made by owners are tracked, reviewed, and audited, ensuring that discretionary decisions remain transparent and controlled. - Not suited for regulated or sensitive data without additional controls.
While DAC allows rapid collaboration, it lacks centralized enforcement and oversight, making it unsuitable on its own for regulated or high-sensitivity environments. Without complementary controls, DAC cybersecurity can lead to overprovisioning and unchecked privilege escalation. - Combine with access reviews to prevent privilege creep.
Embedding DAC within governance processes like periodic access reviews, certification campaigns, and automated entitlement reporting helps catch and correct privilege creep, strengthening overall security posture.
Final Thoughts
Discretionary Access Control is widely used for its flexibility, speed, and user-driven nature, making it ideal for agile environments like small teams and research groups. However, to avoid security risks, it should be balanced with governance by integrating it into IAM/IGA frameworks, supplementing with RBAC, and conducting regular access reviews.
At Tech Prescient, we help businesses design and implement access control strategies that balance collaboration with compliance, so you can share confidently without compromising security.
Get the right access to the right people, every time.
Talk to our access control experts and see how DAC can work for your organization:
Frequently Asked Questions (FAQs)
1. What is discretionary access control in cybersecurity?
Discretionary Access Control (DAC) is a model where the owner of the data decides who gets access and what they can do with it, like read, edit, or share. Think of it as giving someone the keys to your room because it’s your room, and you decide the rules.2. How does DAC differ from MAC and RBAC?
The difference lies in who makes the decisions. In DAC, the data owner controls permissions. In Mandatory Access Control (MAC), the system or a central authority sets the rules, and no one can override them. Role-Based Access Control (RBAC) assigns access based on predefined job roles, so permissions change automatically when a person’s role changes.3. Is DAC a secure model for sensitive data?
Not always. While DAC offers flexibility, it can also cause accidental over-permissioning, where users get more access than they actually need. That’s why it’s usually better for less sensitive environments or used alongside stricter access control models.4. What are some real-world examples of DAC?
You’ve probably used DAC without realizing it. When you share a Google Doc and choose who can view or edit it, that’s DAC in action. The same goes for smartphone app permission prompts or Unix/Linux file commands like chmod and chown.5. Can DAC be combined with other access control methods?
Yes, and that’s often the best approach. Many organizations pair DAC with IAM systems or RBAC to balance flexibility with governance, ensuring that permissions are both user-friendly and compliant with security policies.