What Is Cybersecurity Posture? (Definition & Importance)


The capability of your organisation to withstand the fast-paced growing impact of cyber threats today relies on more than just the correct tools. It relies on your cybersecurity posture, the overall health and preparedness of your defenses. A strong posture shows how well your policies, technologies, processes, and people work together to mitigate, identify, and respond to threats.
This year, global spending for cybersecurity is estimated to reach $458.9 billion gross, showing organisations must make security investments a priority. Indeed, recent research from the physical security industry reports that 43% of organisations are planning to invest in cybersecurity tools this year to fortify their physical security posture.
In the current landscape of continual attacks and ever-expanding compliance obligations, evaluating and improving your cybersecurity posture is no longer an option. It's a direct proof of the business's resilience, trust, and sustainability for the future. This blog will break down what a cybersecurity posture means, why it matters in 2025, how to assess your posture, and provide a realistic action plan to fortify it.
Key Takeaways
- Cybersecurity posture = the state of overall defense.
- It indicates how well your policies or procedures, processes, people and technologies work to prevent, detect and respond to threats.
- Conducting regular assessments and monitoring to help identify gaps in the posture, benchmark readiness and help with future improvements.
- A stronger posture = lower risk and increased trust. Organisations with a strong posture can reduce breaches or respond faster and continue business as usual in the face of threats.
Cybersecurity Posture Definition Explained
Cybersecurity posture denotes the general condition of an organization’s security posture, the combination of policies, controls, processes, and technology for protecting its data, applications, and IT infrastructure. It reflects how prepared an organization is to prevent, detect, respond to, and recover from cyberattacks, data breaches, or other security incidents.
A strong posture means fewer vulnerabilities, stronger defenses, and greater operational resilience. A weak posture means greater exposure to risk, slower response times, and increased financial and reputational risk.
Cybersecurity posture has an inverse relationship with risk: the stronger the cybersecurity posture, the lower the likelihood of unauthorized access, data loss, or service disruption. Cybersecurity risk refers to the potential for harm to confidentiality, integrity, and availability (CIA) of IT systems and data.
In addition to security, organizations need to maintain a strong posture for compliance purpose with privacy and security frameworks including, but not limited to, GDPR, LGPD, PIPEDA, CCPA, GLBA, FISMA, CPS 234, NYDFS Cybersecurity Regulation, HIPAA. A strong posture indicates that technical and operational controls are working together to mitigate risk, identify anomalies, and facilitate timely, coordinated response to security incidents.
Components that define cybersecurity posture are:
- Policies & Procedures: Governance framework and compliance requirements, along with still internal security policies for managing secure behaviour.
- Technology & Tools: Firewalls, endpoint protection, SIEM, cloud security tools, and encryption are your frontline technologies.
- Employee Awareness: Security awareness training and security culture that reduces human error and lower insider risk.
- Incident Response & Recovery: Existing process to identify, contain, and remedy breaches rapidly.
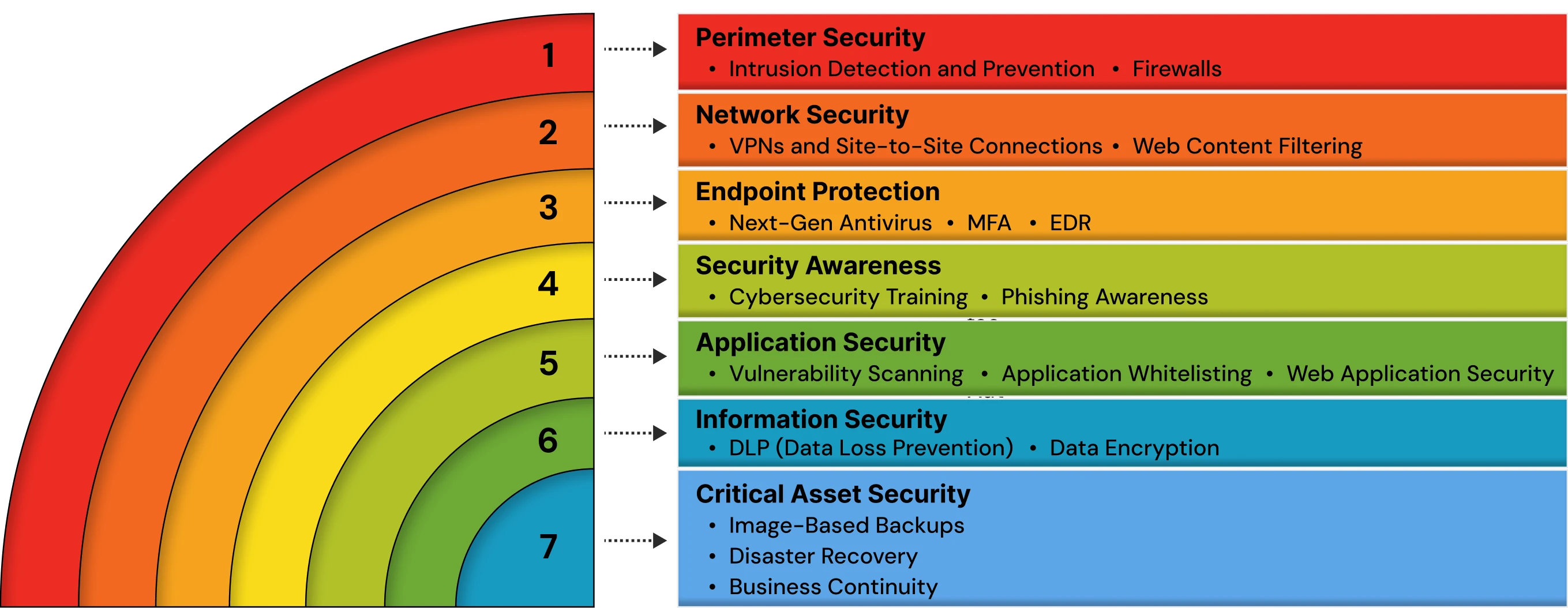
Why is Cybersecurity Posture Important?
A strong cybersecurity posture is the basis for an organisation’s capability of effectively defending against, detecting, and responding to threats. Organizations with a mature posture are better equipped to deal with evolving risks, regulatory pressures, and operational challenges. In the current threat environment, where attacks are more advanced and occur continuously, reactive measures are not enough; proactive defense is required.
Key reasons why cybersecurity posture matters in 2025:
-
Decreases Breach Risks
Companies with a strong posture can identify weaknesses before an incident occurs. For example, continuous automated monitoring of a system and regularly scheduled assessments of system security would identify configuration errors or unpatched systems, all of which would reduce the potential for incidents such as ransomware attacks or data breaches. Organizations that utilize a robust cybersecurity posture framework are less likely to encounter incidents and have fewer and less severe incidents than an organization that relies on ad-hoc security practices. -
Builds Trust and Reputation
As customers, partners, and stakeholders evaluate organizations against security reliability. With a strong cybersecurity posture, organizations can show their ability to protect sensitive information, maintain operations, and preserve privacy. On the other hand, when breaches occur, trust is lost, and reputation can take a long time to repair and restore.
Example- Breach in Okta Customer Support: Okta announced in 2023 that it suffered a breach of its customer support platform, during which the names and email addresses of some users and employees were exposed. Although only a small subset of customers were affected, the breach startled clients and demonstrated how quickly trust can disintegrate when security controls are viewed to be lacking. -
Ensures Compliance Readiness
Cybersecurity posture is closely correlated with regulatory and industry compliance, including ISO 27001, NIST CSF, HIPAA, and GDPR. Having defined policies, processes, and security controls allows organizations to demonstrate compliance, reducing the pressure of an audit and mitigating potential fines. Continuous monitoring of the controls will make compliance more effective and less stressful as the regulatory state evolves. -
Strengthens business continuity
A strong posture does more than simply prevent breaches. It supports detection and response capabilities, promotes rapid ecosystem recovery from cyberattacks, system failures, or insider incidents, and ensures the organization can continue with its business, all while minimising downtime and impacts on revenue. -
Facilitates Risk-Based Decision Making
For leaders evaluating the organization’s security posture over time, ongoing assessments allow them to prioritise resources for the components most vulnerable to risk. This focused effort in identifying risk means a formal investment in tools, processes, or training is supported by measurable improvements in preparedness.
Key Components of a Strong Cybersecurity Posture
An effective cybersecurity stance is comprised of four key elements: governance, technology, people and processes. Each of the components of the posture enhances an organisation's resilience, preparedness, and capability to prevent, detect and/or respond to threats.
1. Policies and Procedures
Policies and procedures are the backbone of a cybersecurity governance posture. The policies and procedures establish roles, responsibilities, access controls, and other checks for frameworks, such as SOC 2, HIPAA, PCI DSS, etc. Policies and procedures create the framework for risk assessments, incident management, and periodic review, establishing an expectation of consistency and accountability across the organization.
2. Technology and Tools
A layered technology architecture is essential for proactive defense. Tools like firewalls, security information and event management (SIEM), endpoint protection, encryption, intrusion detection, and access controls work together to detect, block, and respond to threats. Each layer strengthens the next, reducing single points of failure and enabling continuous monitoring of security events.
3. Employee Awareness and Training
The human component of the organisation is still among the top attack vectors. Continuous training programs, phishing simulations, and clear reporting channels equip employees to recognize and respond to threats. Awareness initiatives also enforce secure password practices, multi-factor authentication, and proper handling of sensitive data, reducing insider and accidental risks.
4. Vulnerability & Risk Management
Preventive measures such as scanning for vulnerabilities, penetration testing, and risk assessments help identify and reduce the attack surface. Most organizations will follow a structured vulnerability management process, including vulnerability scanning, pen testing, and risk assessments, all with some prioritized matrix for risk to high-value assets, then proceed with patching or configuration monitoring to remediate that known risk.
5. Incident Response & Recovery
The strength of defenses will not completely prevent breaches. Documented incident response is clear about who is doing what with respect to threat detection, containment, and remediation. A good incident response plan will also be considered with a valid communications plan, evidence collection and forensic process, recovery, and any lessons learned for future mitigation.
6. Data Security & Cloud Posture
Data security and cloud posture ensure that sensitive information is protected, wherever it resides, on-premises, hybrid, or in multi-cloud environments. Techniques like encryption, strict access control, and identity-based policies limit unauthorised access. Continuous monitoring of cloud configurations detects misconfigurations, excessive permissions, or compliance gaps so they can be promptly remediated.
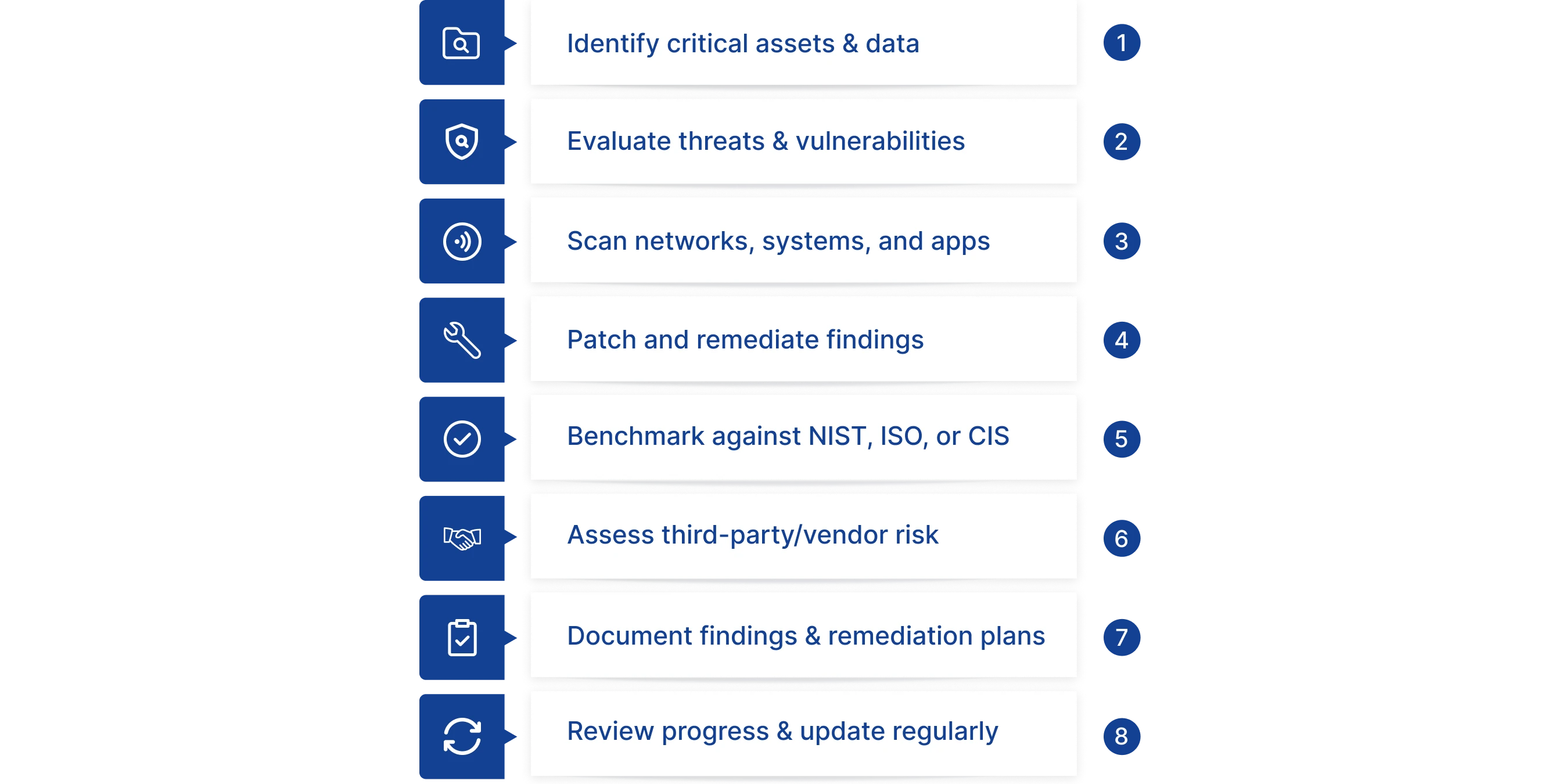
How to Assess Your Cybersecurity Posture
A cybersecurity posture assessment is a structured evaluation of an organisation’s strengths, weaknesses, and overall resilience to threats. It identifies gaps in policies, processes, technology, and employee behaviour, and lays out a path to remediation and risk reduction.
Steps to Assess Cybersecurity Posture Include:
- Conduct Risk Assessments
- Identify critical assets, sensitive data, and systems.
- Assess threats, vulnerabilities, and impact to determine an order for remediation.
- Run Vulnerability Scans
- Run scans on the network, system, and application to discover misconfiguration, unpatched software, or exploitable gaps.
- Document the remediation, and verify that the vulnerabilities were fixed.
- Benchmark to a Framework
- Compare existing security controls against established frameworks such as CIS Controls, SOC 2, COBIT, or PCI DSS, depending on industry requirements.
- Use scores against a framework to assess coverage and maturity across policies, processes, and technology.
- Third-Party/Vendor Risk Review
- Assess the cybersecurity posture of vendors and cloud providers by reviewing SOC 2 Type II reports, ISO 27001 certifications, penetration test results, or compliance attestations relevant to your industry (e.g., HIPAA, PCI DSS).
- Review contracts, certifications, and audit documentation to provide evidence that your third-party is compliant with your security requirements.
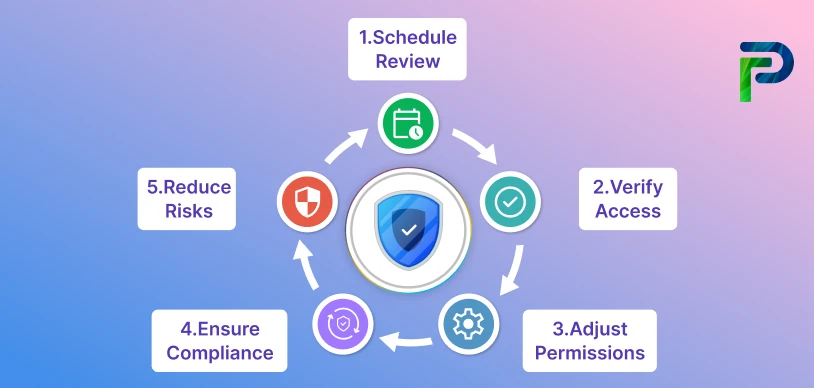
Ways to Improve Cybersecurity Posture
Enhancing your cybersecurity stance is not a singular task. Protecting your organisation requires ongoing improvement through people, processes and technology. The following areas can assist organisations in improving their defenses and staying resilient against changing cyber risks:
1. Automate Patching and Software Updates
Unpatched devices remain one of the most frequent paths to successfully target organizations by cyber criminals. Automating patching, which means the process of using tools to detect, download, test, and install security updates without manual intervention, ensures vulnerabilities are addressed on time and will reduce lingering risks. For example, when organizations deploy automated patching tools, remediation timelines are substantially reduced, going from weeks to hours, which reduces the likelihood of successfully utilizing the exploit in question.
2. Strengthen Password and Identity Policies.
Identity continues to be one of the most targeted objectives of criminals as they victimise organisations. Enforcing stronger password requirements, enabling multi-factor authentication (MFA), and adopting modern identity governance practices help secure user accounts. This is compounded with the use of [role-based access control RBAC, as well as periodic user access reviews, which ensure that users possess no more access than is required to accomplish their tasks within the least-privilege model.
3. Invest in Ongoing Employee Training
Employees serve as both the first line of defense and the most prevalent point of breach. Routinely scheduled training on common threats such as phishing, social engineering, and proper data handling procedures will significantly limit human error. Simulation-based training exercises, such as phishing tests, serve as measuring tools for employees' awareness of threats while establishing a culture of accountability.
4. Implement Continuous Monitoring & Metrics
Cyber threats very seldom operate strictly “9 to 5,” and in the same respect, defenses should also never be “9 to 5.” Continuously monitoring your networks, endpoints, and cloud environments will allow for early notice of anomalies. In addition to continuous monitoring, metrics (e.g., mean time to detect/respond rates, patch compliance and incident trending) allow you to demonstrate your performance, track the progress of your pending resolutions, and make adjustments to your ongoing defenses.
5. Adopt Zero Trust & Cloud Posture Management
With the hybrid and cloud-first environments carried out in organizations today, perimeter defenses are no longer sufficient. In a Zero Trust model, nothing is trusted based solely on identity. Continuous verification of access allows for real-time context to support access, such as location, IP address, device health assessment, and behavior analysis. Cloud Security Posture Management (CSPM) can be used to resolve misconfigurations, properly enforce compliance policies, and secure data in multi-cloud environments.
Cybersecurity Posture vs Compliance: Key Differences
Cybersecurity posture and compliance are interconnected, yet distinct. Compliance measures whether an organization meets the regulatory requirements, while posture measures the organizational level of cyber risk and readiness. An organization can be compliant, but if its posture is weak, it will be vulnerable.
| Aspect | Cybersecurity Posture | Compliance |
|---|---|---|
| Definition | Overall strength, resilience, and readiness to defend against cyber threats | Adherence to specific regulations, standards, or frameworks (e.g., GDPR, HIPAA, SOX) |
| Focus | Security, health, risk reduction, and operational resilience | Meeting legal/industry requirements |
| Measurement | Risk assessments, vulnerability scans, monitoring, and incident response capabilities | Audits, certifications, regulatory reporting |
| Approach | Continuous, proactive improvement | Periodic, checklist-driven |
| Outcome | Reduced risk of breaches, faster detection & recovery | Regulatory approval, reduced penalties, and trust with regulators |
| Example | Deploying Zero Trust, continuous monitoring, and employee awareness training | Passing a HIPAA or ISO 27001 audit |
Types & Levels of Cybersecurity Posture
A strong cybersecurity posture can be assessed over a range of different areas. Each concentrates on a specific aspect of protection, from cloud environments to identity management, while maturity levels indicate how far along the organization is with respect to its overall posture.
Types of Cybersecurity Posture:
1. Cloud Security Posture
Cloud environments present risks related to misconfigurations, insecure APIs, and shadow IT (unauthorized apps or services used without IT approval). Cloud Security Posture Management (CSPM) allows organizations to continually monitor configurations, enforce policies, and discover vulnerabilities throughout hybrid and multi-cloud environments. A strong cloud posture ensures that sensitive workloads remain secure during the business growth phase.
2. Data Security Posture
Data security posture refers to an organization's ability to safeguard sensitive data at rest, in transit, or in use. This will encompass options such as encryption, access control, data loss prevention (DLP), and controls that detect unauthorised activity. With an increase in regulation (GDPR, CCPA), a strong data posture is a vital component of limiting breaches and incident-based penalties.
3. Identity Security Posture
Identity remains the most frequently targeted attack surface, generally remaining the single most effective point of attack for adversaries. A positive identity security posture will include multi-factor strong authentication, privileged access management (PAM), and regular access assessments for all users. Every organisation should remain an advocate for Zero Trust concepts, where all high-risk identities, whether human or machine-based, must be continuously verified before allowing access.
4. Network Security Posture
An organization's network security posture encompasses the means, processes, and policies that best protect the organization's network infrastructure, which includes routers, switches, servers, and endpoints. There are firewalls, IDS/IPS technology, continuous monitoring, network segmentation, etc. A strong network security posture limits lateral movement by a malicious attacker in the organization's environment.
5. Application Security Posture
Application vulnerabilities represent one of the most common attack vectors for malicious attackers. An application security posture assesses the degree to which the organizational software ecosystem is resilient to application risks such as SQL injection, cross-site scripting, etc., and insecure APIs (application programming interfaces). Application security posture includes secure SDLC practices, penetration testing, Software Composition Analysis (SCA), etc., to reduce risks within the organization's software ecosystem, including applications that are custom-developed or from third parties.
Levels of Cybersecurity Posture
Levels illustrate the maturity of an organization's security program as it matures from responsive /ad-hoc to integrated and adaptive.
Level 1 - Basic Cyber Hygiene:
In this stage, security is responsive and has little to no planning effort. Controls are ad hoc in nature, and any incidents the organization responds to are done on a case-by-case basis. Security is not integrated into operational practices.
Level 2 - Intermediate Cyber Hygiene:
The organization begins to implement some documented policies and basic standard practices. Security responsibilities are defined, and a consistent approach is applied to protection across IT operations. The organisation may still lack visibility or automation around security in practice.
Level 3 - Good Cyber Hygiene:
You have a proactive program, and processes are implemented to monitor, detect and respond to incidents in place. Periodic audits, vulnerability scans and training of employees are accomplished regularly as part of the culture.
Level 4 - Proactive:
Your organization has implemented advanced monitoring, automated detection, and integrated risk management of the overall security program. Your security processes are dynamic, with continuous assessments, improvements, and forward thinking to stay in front of evolving threat landscapes.
Level 5 - Advanced/Progressive:
The organization can demonstrate industry-leading practices. The advanced level is seen as one that utilizes threat intelligence, automation and innovation into a highly adaptive "security environment" culture of cyber risk posture. Security has matured to a place of several examples of its implementation into culture and overall approach to organizational practices and governance. An advanced organization influences industry standards.
Final Thoughts
Cybersecurity posture is not a box to check, but it’s a continuous journey. Threats develop, technologies develop, and compliance needs get tougher every year. A company that treats its posture as a one-time event will fall behind and have a gap in its defenses.
Companies that consider their cybersecurity posture to be evaluated, enhanced, and monitored continuously over time will increase resilience and stay one step ahead of adversaries. Companies that continually assess and invest proactively in people and technology and maintain a security culture build defensible positions that change as quickly as the threat landscape does.
The key is the regularity and consistency of measuring the state of your security posture. The more often you measure and improve the state of your security posture, the more prepared you will be to protect critical assets and sustain trust with your customers, partners, and regulators.
NEXT STEPS
Strengthening cybersecurity posture requires the right mix of strategy, automation, and continuous oversight. With Tech Prescient’s Identity Confluence, you can gain the visibility and control needed to reduce risk and stay audit-ready.
- Get started faster → Explore now
- See it in action.
Frequently Asked Questions (FAQs)
1. What is cybersecurity posture in simple terms?
Cybersecurity posture is similar to a health check for your company's defenses. It shows how well your people, processes, and technology are prepared to prevent, detect, and respond to cyber threats. A stronger posture indicates fewer vulnerabilities and quicker restoration when incidents occur.2. What are the three components of security posture?
1. Policies and procedures that inform governance and compliance.2. Technologies and tools like firewalls, encryption, and endpoint protection.
3. Employee awareness that aims to reduce human error, which is still one of the leading reasons for breaches.
3. How do you measure cybersecurity posture?
You can assess it with structured assessments like risk assessments, internal audits, vulnerability scans, and penetration testing. Many organisations use benchmarks like NIST CSF or ISO 27001 to assist with identifying gaps and assessing improvements over time.4. What’s the difference between security posture and compliance?
Cybersecurity posture is focused on your overall defensive capabilities, as well as your overall resilience against breaches. Compliance is about adhering to regulations, such as SOC 2, HIPAA, or GDPR. A strong security posture can support compliance, but being compliant does not equate to a strong security posture.5. What are examples of improving security posture?
Some practical examples of improving your security posture include regular employee training, strong password and identity policies, automating updates and patching, continuous monitoring, and adopting Zero Trust and cloud security posture management to mitigate risks in today's modern IT environment.