Benefits of Identity Lifecycle Management (ILM): Why It Matters


As enterprises scale rapidly and adopt more SaaS tools, Cloud platforms, and enable hybrid/remote working models, managing access becomes a serious challenge. The stakes rise as weak identity controls cause security breaches, compliance failures, and operational slumps. Identity Lifecycle Management ensures increased operational efficiency, security, compliance, and better user experience.
In fact, according to Gartner, organizations with 10,000 employees or more can save over $3.5 million and achieve a 300% ROI in 3 years by modernizing their identity lifecycle processes.
Identity Lifecycle Management streamlines the entire journey of a user’s digital identity, right from onboarding and changing roles to secure offboarding. ILM reduces manual errors, strengthens access controls, and ensures that identity governance stays scalable and compliant.
So, whether you are dealing with rapid hiring, mergers, or even new compliance mandates, ILM gives you the visibility and agility required to secure your organization without hindering your growth.
Key Takeaways:
- ILM automates the entire identity journey, reducing any manual errors and delays.
- Strengthens security posture by implementing least privilege and withdrawing unnecessary access in real-time.
- Ensures regulatory compliance with external and internal regulations through access reviews.
- Reduces IT costs by eliminating manual effort in provisioning/deprovisioning tasks.
- Improves user experience with faster access, self-service features, and fewer login issues.
- Provides centralized visibility into user access across systems, cloud apps, and endpoints.
Top 10 Benefits of Identity Lifecycle Management (ILM)
A well-implemented Identity Lifecycle Management (ILM) strategy simplifies the lives of IT teams and end users by streamlining user access, mitigating risks, and enhancing compliance.
1. Enhanced Security through Automated Access Controls
Identity Lifecycle Management notably reduces the risk of security breaches by ensuring that only the right people have access to the right systems. It also eliminates the manual error and subsequent lag that are a part of the manual access management process by integrating ILM with core systems like HRMS, HCM systems, and directories such as Active Directory to automate provisioning and de-provisioning.
For example, let’s say a new employee joins your company. Their access to necessary tools and resources is provisioned immediately with ILM. And even more importantly, their access is updated or removed automatically when the employee switches roles or leaves the organization.
Because without this automated access control, the risk of insider threats and privilege creep increases due to retained access with old employees or systems. Organizations today need stricter boundaries and security, which ILM provides seamlessly.
2. Improved Operational Efficiency
Manual identity processes are slow, costly, and risky. But with Identity Lifecycle Management, automation can turn weeks of provisioning/deprovisioning work into minutes. Organizations that make use of automated ILM show up to a 50% reduction in their onboarding processes, which not only frees up time for IT teams but also helps new hires start as early as possible.
With Identity Lifecycle Management, as soon as a new hire joins your organization, access is automatically provisioned via Role-Based Access Control (RBAC). And when that person leaves or switches roles, this provisioning is updated or removed as necessary, eliminating any security gaps or delays.
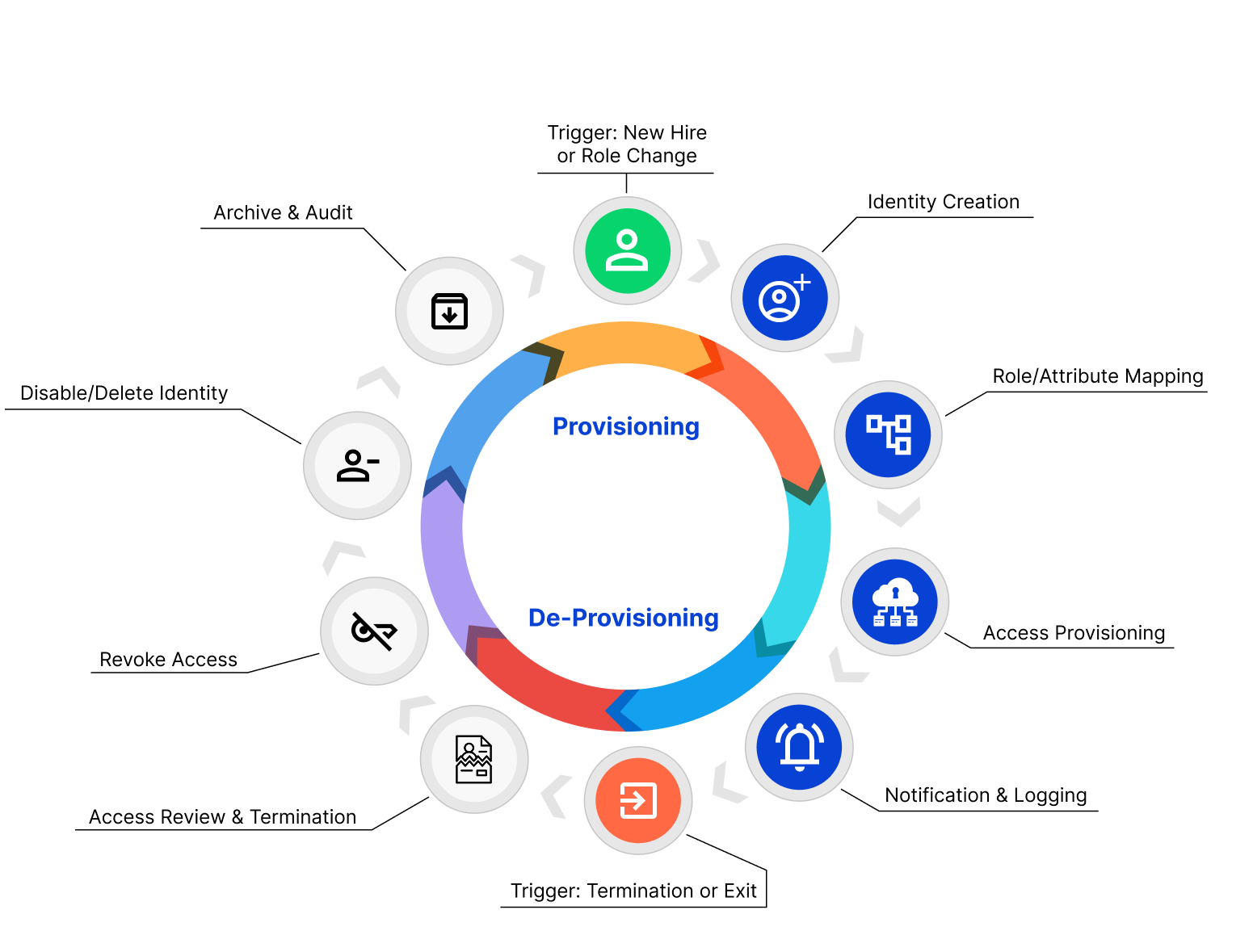
3. Simplified Regulatory Compliance
Compliance is a constant and evolving responsibility. It is not just a checkbox to be ticked. Identity Lifecycle Management (ILM) helps you meet evolving regulatory requirements like GDPR, SOX, HIPAA, and stay compliant by maintaining detailed audit logs, automating access controls, and enforcing role & policy-based access control.
Manual compliance efforts are no more sustainable with increased scrutiny on access governance and data privacy. Identity Lifecycle Management ensures that only authorized people can access sensitive data; it reduces the risk of human error and supports segregation of duties (SoD), all with complete visibility. It also saves hours of time by generating real-time reports instantly during audits and keeps your organization audit-ready always.
4. Reduced IT Costs
Identity Lifecycle Management (ILM) reduces operational costs by automating all identity-related tasks such as permission management, role changes, and assigning access. This eases the burden on IT teams by reducing manual effort and ticket volume, making more time for the necessary strategic projects. Simultaneously, ILM constantly eliminates orphaned accounts and ensures users only have the right access to the right resources, minimizing the risk of costly security breaches.
IBM reported that the average cost of a data breach reached $4.45 million, and the most common factor in the initial attack was compromised credentials. ILM automates access clean up and enforces periodic deprovisioning that significantly reduces this risk.
Identity Lifecycle Management also enables faster risk detection and response to insider threats, lateral movements, and policy violations by enforcing least privilege access and entitlement reviews. This tightens your cybersecurity posture and also results in long-term cost savings.
5. Insider Threat Mitigation
Not all threats are external. In fact, one of the most difficult risks to detect and restrain is an insider threat, which can be either malicious or accidental. Identity Lifecycle Management (ILM) addresses this by enforcing the principle of least privilege access. ILM ensures that privilege creep doesn’t go unnoticed by constantly monitoring permissions, access rights, and managing roles throughout the user lifecycle.
What does ILM do to curb insider threats?
- Supports Segregation of Duties (SoD)
- Automates access reviews to catch risky entitlements
- Tracks user roles or employment status changes
- Revokes access immediately when user status changes
6. Improves User Experience with Faster, Self-Service Access
Delayed access provision causes loss of productivity and increased user frustration. Identity Lifecycle Management makes this employee experience better by automating routine tasks like onboarding, role-based access provisioning, and authentication without having to wait on IT teams. ILM also enables self-service access requests and automated approvals, ensuring users get the resources they need quicker with well-defined policies.
What are the user experience benefits of ILM?
- Self-service access lessens IT dependency
- Faster day-one access when onboarding
- Fewer support tickets for access problems
- Smooth transitions during role changes
7. Centralized Visibility and Control Across the Identity Lifecycle
Identity Lifecycle Management(ILM) provides a unified view of users, their roles, access rights, and activity across your organization. Without this centralized visibility, IT teams have to depend on guesswork and fragmented data to understand who has access to what. With ILM’s centralized dashboards and identity repositories, organizations can spot anomalies, access patterns, and implement policies all in one place.
Why centralized visibility matters:
- Easy implementation of SoD (Segregation of Duties) and least privilege
- Simplified reporting for compliance and audits
- Real-time insight into user access
- Flagging of dormant or over-provisioned accounts
8. Efficient Password Management
Weak, reused, or forgotten credentials are one of the top causes of security breaches or IT support overhead. Identity Lifecycle Management has features such as password synchronization, self-service password resets (SSPR), and single-sign-on (SSO) systems that streamline the password management process. These features lessen authentication friction and remove password sprawl by offering users secure and convenient access across systems.
With this, users gain access quickly without needing IT support, while IT teams don’t have to deal with as many password-related tickets. Identity lifecycle management fortifies your complete security posture and increases productivity by enforcing unified password policies across cloud and on-prem environments and reducing irrelevant logins. It’s a win-win situation for organizations as users spend less time locked out and IT focuses on more important tasks.
9. Adaptability to Change in Dynamic Business Landscapes
The one thing constant in all organizations is change. New hires, role changes, mergers, or organizational restructuring, and without a flexible and dynamic Identity Management system, these shifts can cause security gaps, disarrayed access, and delays that cost organizations.
ILM allows your identity infrastructure to grow and scale with your business. For example, when a finance manager is promoted to a senior manager role, ILM automatically updates their permissions, removing any outdated access and provisioning new ones based on defined policies.
With ILM, you can automate user access based on role changes, take care of bulk provisioning (for instance, during mergers and acquisitions), and even ensure compliance with evolving regulations.
10. Audit Readiness Made Easy
Regulatory audits are stressful, time-consuming, and very important to maintain compliance. But when identity records are ill-maintained or outdated without clear access trails, it can cause harm to your organization’s reputation. Identity Lifecycle Management makes your organization audit-ready by maintaining automated, timestamped details of user access, approvals, and changes across the identity lifecycle.
This guarantees that you always have a real-time view of who has access to what, when, and why. ILM enables your organization to build trusted relationships with customers, investors, and partners while showing strong governance.
Identity Confluence helps you build a strong and secure process right from onboarding to offboarding while staying compliant.
- Learn more about Identity Confluence
- See Identity Confluence in action.
Frequently Asked Questions (FAQs)
Q: How does ILM improve compliance?
A: It automates your access reviews, maintains all audit trails, and implements policy-based control. This makes it easy for you to comply with standards like HIPAA, SOX, and GDPR by decreasing human error and providing clear documentation to auditors.Q: How is ILM different from traditional IAM?
A: IAM focuses on authentication and real-time authorization, while ILM focuses on governing the full identity lifecycle using automation and oversight. ILM goes beyond just giving the login access and takes care of who, when, and why they got access.Q: Is ILM only for large companies?
A: No, not at all. If you are a mid-sized company or a start-up up you can also benefit from ILM. As your business scales, manual identity processes become very time-consuming and risky.Q: What systems does ILM integrate with?
A: Modern ILM tools can integrate with HR systems, directories, cloud apps, and IAM platforms.