What Is Automated Provisioning? Benefits, Tools, and Use Cases

Automated provisioning, also known as automated identity provisioning or automated user provisioning, is the process of using software to automatically create, update, and revoke user accounts and access privileges across an organization’s systems, applications, and data, without manual intervention. As a foundational principle of Identity and Access Management (IAM), it streamlines user access management while improving operational efficiency, enhancing security, and ensuring compliance across the user lifecycle.
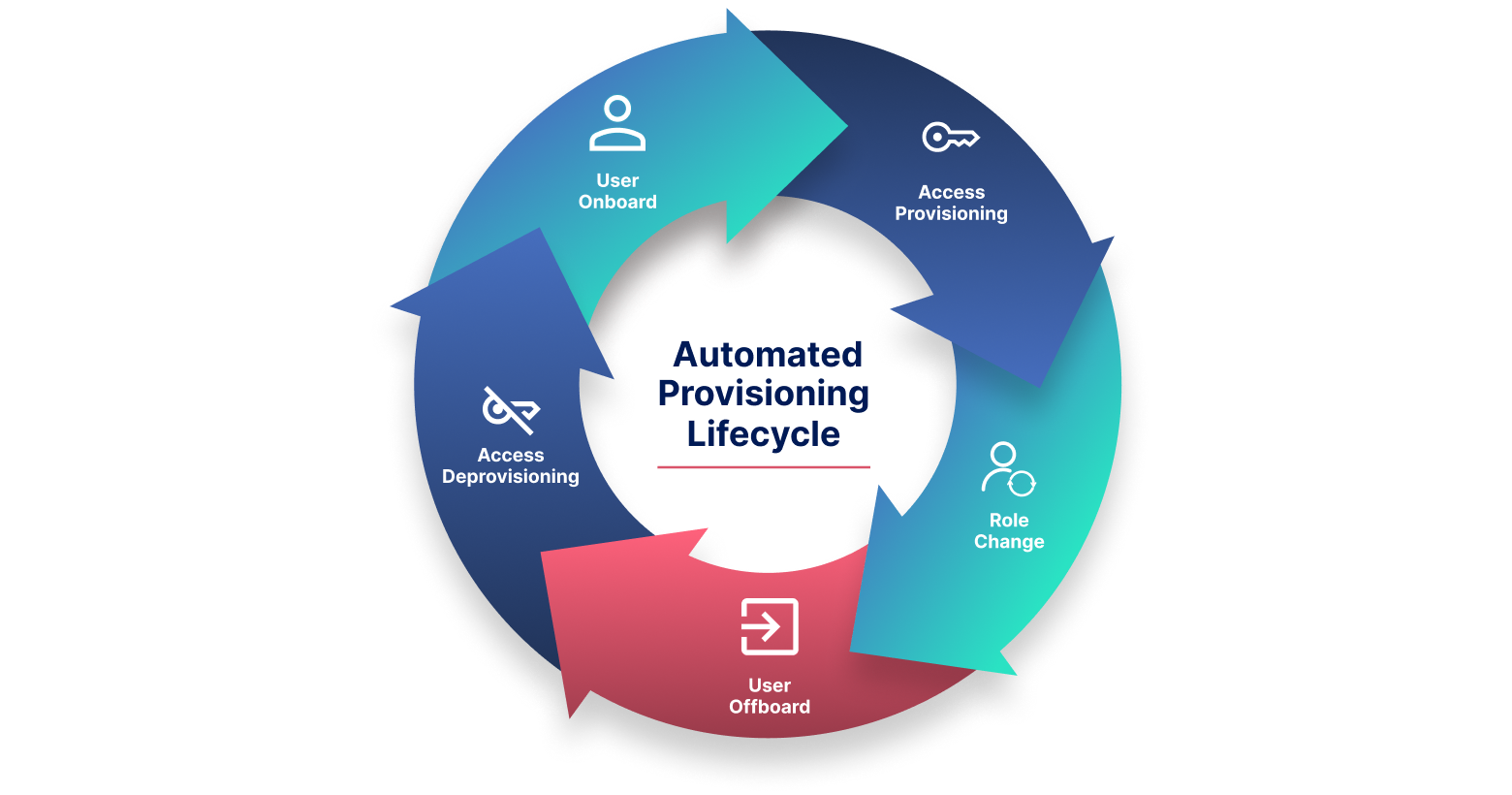
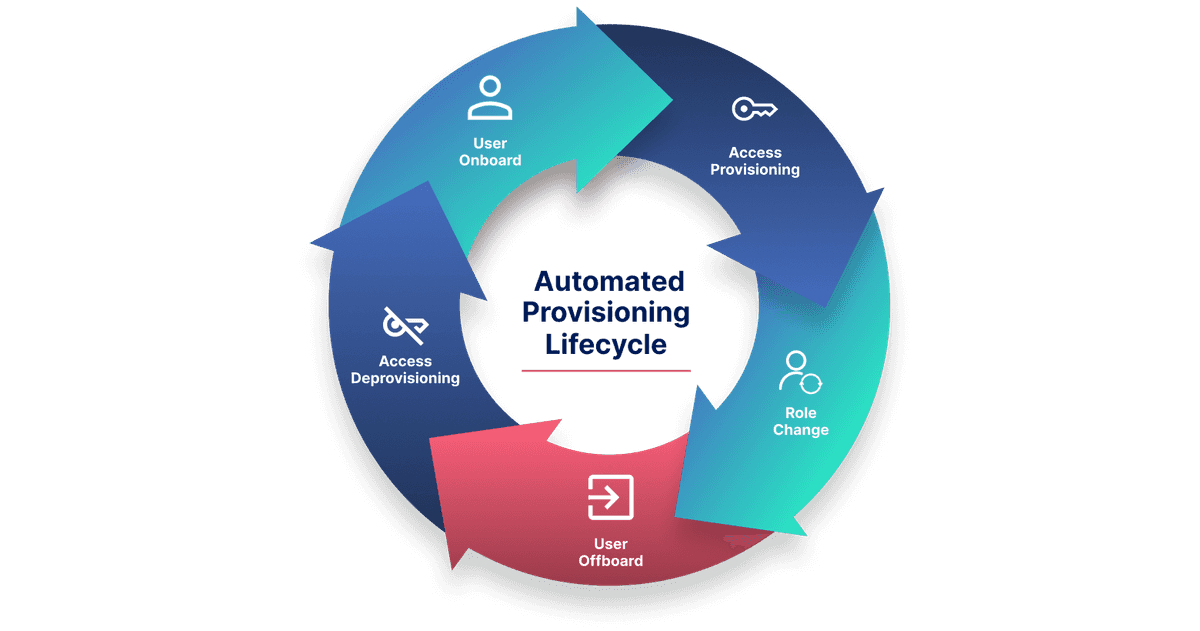
However, just as automated provisioning may deploy and activate services for users, it can also disable user access to systems, apps, and data. This is known as automatic deprovisioning, or deprovisioning. The act of providing and deprovisioning user access is a type of lifecycle management used to onboard and offboard people when an organization's needs change.
But more than just streamlining access, automated provisioning helps you stay in control, strengthen security, and stay compliant across the entire user lifecycle. Companies using automated access management report up to 80% fewer permission-related security issues. It keeps a clear log of access changes and helps you stay compliant. With hybrid work and growing SaaS adoption, this kind of automation is no longer optional.
In this blog, we’ll break down what automated provisioning is, how it works, the benefits it offers, and the tools that make it possible.
Key Takeaways
- Learn what automated provisioning is and why it's central to IAM.
- Understand how it connects HR, IAM, and apps to automate access in real time.
- Explore real-world use cases like onboarding, role changes, and offboarding.
- Discover how it boosts security, reduces errors, and ensures compliance.
- Get a practical step-by-step guide to implement provisioning at scale.
What is Automated Provisioning?
Automated provisioning is a solution for managing user access and privileges for organizational applications, websites, data, and other systems. Rather than manually assigning rights for each user and system, automated provisioning enables access to be automatically granted based on preset rules allocated to predefined roles or groups.
Unlike manual provisioning, where IT teams handle access requests through spreadsheets or ticketing systems, automated provisioning responds instantly to identity lifecycle events such as new hires, internal transfers, or exits, updating access across systems without manual input. But automated provisioning isn’t just about streamlining administrative tasks; it also enhances security and ensures compliance, which is critical in today’s business environment where cyber threats are an ever-present risk. At its core, automated provisioning leverages software to manage user identities and their access rights throughout their lifecycle within the organization.
This end-to-end automation includes:
- Creating new user accounts: When a new employee is onboarded, their profile is added to the HR system, which automatically initiates the creation of user accounts across all relevant applications and IT systems.
- Modifying access rights: As employees transition to new roles or take on additional responsibilities, their access permissions are automatically adjusted based on predefined rules and workflow policies.
- Revoking access: When an employee leaves the organization, their access to all systems and applications is automatically revoked, minimizing the risk of unauthorized access.
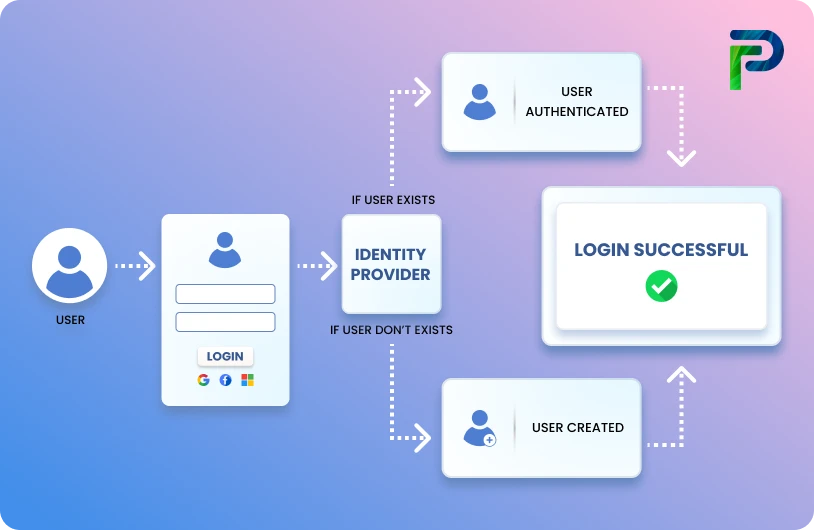
In the IAM (Identity and Access Management) context, provisioning is triggered by systems like your HRIS (Human Resource Information System) or ITSM (IT Service Management), while the IGA (Identity Governance and Administration) layer ensures policy enforcement, audit trails, and compliance with regulations like SOX or HIPAA. Manual provisioning is slow and inconsistent. Automated provisioning is fast, scalable, and secure.
How Does Automated Provisioning Work?
Automated provisioning connects your HR systems to identity platforms and business applications, enabling real-time, policy-based access control across the user lifecycle. This process, also known as automatic provisioning, helps organizations reduce manual effort, eliminate errors, and enforce consistent access policies. Here’s how the process works, step by step:
- Step 1. HRMS Integration → IAM/IGA → Apps
Automated user provisioning begins with a connection between your Human Resource Management System (HRMS) and your IAM/IGA platform. When a user is added, modified, or removed in the HRMS, this event acts as a trigger. The IAM or IGA system uses predefined rules to determine what access the user should receive, automatically assigning permissions to applications, tools, or systems according to their role and company policies. This seamless flow ensures every identity update is reflected instantly across connected systems. - Step 2. Role-Based Access Control (RBAC) and Policy Enforcement
Consider a scenario where new sales representatives are being onboarded. When the HR team assigns them the “sales” role in the HRMS, the IAM platform automatically provisions access: a CRM account with standard permissions, a shared cloud folder with sales documents, and a commission tracking tool login. These assignments are driven by Role-Based Access Control (RBAC), which maps user roles to access rights. All provisioning follows company-defined policies, eliminating manual intervention while maintaining consistency and control through intelligent provisioning tools. - Step 3. Real-Time Sync and Revocation
Automated provisioning also handles changes and departures with equal efficiency. If a sales rep exits the organization, an update in the HRMS immediately triggers the IAM platform to revoke access across all systems, ensuring no former employee retains entry. Similarly, if an employee is promoted, the system automatically adjusts their access levels to reflect their new responsibilities. This real-time synchronization, powered by automatic provisioning, ensures security, prevents privilege creep, and supports compliance through complete, auditable access trails.

Main Benefits of Automated Provisioning
From faster onboarding to better compliance, automated provisioning improves security, reduces risk, and optimizes IT resources across the organization. Here's how provisioning automation delivers value:
1. Speeds Up Onboarding & Offboarding
With provisioning automation in place, new hires and contractors receive access to the tools they need from day one, without IT manually setting up each account. It gathers necessary data from identity sources such as Human Resources systems or Active Directory and uses that to automatically create user accounts across relevant applications.
More than just account creation, it also assigns appropriate access privileges based on predetermined rules and role-based policies. This efficient, policy-driven action accelerates the onboarding process, ensuring that each user gets the right access from the start. Likewise, when employees exit or change roles, automated deprovisioning instantly revokes outdated access, streamlining the entire provisioning and deprovisioning lifecycle and boosting overall productivity.
2. Strengthens Organizational Security
Automated provisioning strengthens organizational security by enforcing company-defined policies, ideally based on the principle of least privilege. This ensures users are granted only the specific system permissions and granular access to resources required for their roles. By limiting access in this controlled manner, organizations reduce the risk of underqualified or negligent employees compromising the integrity or confidentiality of sensitive data systems, resulting in a more robust and resilient security posture.
3. Supports Compliance (e.g., SOX, HIPAA)
By standardizing how access is assigned and revoked, provisioning automation plays a critical role in ensuring compliance. Whether you're aligning with SOX, HIPAA, or other regulatory frameworks, automated workflows help enforce consistent access rules and generate auditable logs for every action. This not only simplifies audit readiness but also reduces the risk of non-compliance, which can lead to failed audits, financial penalties, and reputational damage. With provisioning automation in place, organizations can stay prepared for both internal and external audits while maintaining continuous compliance.
4. Lowers Operational Costs
Manual provisioning is time-intensive and resource-draining. With automation, IT and HR teams spend less time managing access and more time focusing on strategic initiatives. By eliminating repetitive tasks and reducing errors, provisioning automation not only increases operational efficiency but also helps reduce onboarding costs and improve ROI across departments.
“Provisioning automation isn't just about efficiency; it’s about reducing exposure.”
Common Use Cases for Provisioning Automation
Automated provisioning ensures that users receive (or lose) access the moment their role or status changes, boosting productivity, improving security, and minimizing IT overhead. Here are some common real-world scenarios where provisioning automation plays a critical role:
- New Hire Account Setup When a new employee joins, automated provisioning instantly sets up access across all required tools like Slack, Salesforce, Microsoft 365, and project management systems, based on their job title, location, and department. This ensures new hires are productive from day one, without waiting on manual account creation or IT intervention.
- Role or Department Change As employees shift departments or get promoted, their access needs change. Provisioning tools automatically update access to reflect new responsibilities, granting access to new systems while revoking those no longer relevant. This helps prevent privilege creep and enforces role-based access control (RBAC) at scale.
- Contractor Offboarding For temporary or third-party workers, access needs to be both timely and limited. Automated deprovisioning ensures that once a contract ends, all access to sensitive systems and data is revoked immediately, without relying on manual follow-up. This reduces the risk of orphaned accounts and ensures consistent access governance.
- M&A Onboarding or Mass Updates During mergers, acquisitions, or internal restructuring, organizations must provision or update access for large groups of users quickly and securely. Automated provisioning simplifies this process by applying centralized policies that scale across systems, ensuring access is consistent, compliant, and aligned with organizational goals.
These scenarios highlight the need for provisioning automation that can quickly react to identity lifecycle changes without compromising security or compliance.
Automated Provisioning vs. Deprovisioning
Both provisioning and deprovisioning are essential to identity lifecycle management. While automated provisioning grants access based on user roles, automatic deprovisioning ensures access is revoked when it’s no longer needed, reducing risks like orphan accounts, insider threats, and failed audits.
| Function | Automated Provisioning | Automated Deprovisioning |
|---|---|---|
| Purpose | Grants users access based on their role and identity attributes. | Revokes access when users leave the organization or switch roles. |
| Triggered by | Happens during hiring, promotions, or internal role changes. | Triggered by employee exit, contract end, or long periods of inactivity. |
| Benefits | Automated provisioning drives operational agility by updating roles instantly, streamlining access control, and supporting evolving business needs. | Reduces compliance risks by revoking access quickly and removing orphan accounts when users exit or shift roles. |
| Security Role | Secures initial access by assigning the right permissions early. | Blocks unauthorized access after a user leaves or changes positions. |
| Audit & Compliance | Keeps a record of who gets access and when for compliance checks. | Maintains clean logs to meet audit and regulatory requirements. |
| Risk Reduction | Minimizes errors and delays in assigning access rights. | Prevents insider threats and misuse of old credentials. |
Think of provisioning and deprovisioning as two sides of the same security coin; one opens the door responsibly, and the other ensures it’s locked when no longer in use.
“You can’t govern access if you don’t revoke it when needed.”
Best Tools for Automated Provisioning
When evaluating automated provisioning tools, the most critical factor is how well they integrate with your existing identity ecosystem, from HR systems and Active Directory to cloud apps and governance layers. A reliable tool should automate access decisions in real time, ensure policy compliance, and reduce the burden on IT teams. The following components are essential for an effective provisioning setup:
1. Importance of SCIM, APIs, and HR Connectors
Provisioning systems rely on strong integration capabilities to work efficiently. Here are the key components that enable real-time, secure, and policy-based access automation:
- SCIM Support SCIM (System for Cross-domain Identity Management) enables consistent and secure provisioning across modern cloud apps. Tools with SCIM support eliminate the need for custom scripts and enable faster onboarding and offboarding. Additionally, SCIM 2.0 support ensures compatibility with most modern SaaS apps like Slack, Zoom, and Salesforce, making it easier to scale identity management across diverse platforms.
- Robust APIs APIs allow provisioning tools to communicate with a wide range of internal and third-party systems. Strong API support ensures real-time updates, flexible integrations, and workflow customization across apps, directories, and identity platforms.
- HR Connectors HR systems like Workday, SAP SuccessFactors, or BambooHR serve as the source of truth for user identity, driving automated provisioning across the organization. With native connectors in place, any change in employment status, such as a hire, promotion, or exit, automatically updates access rights, reducing manual effort and errors. Additionally, features like delta sync, effective-dated records, and user reconciliation ensure that these updates are timely, consistent, and audit-ready, enhancing both data integrity and compliance.
2. Cloud vs. On-Premise Options
- Cloud-based provisioning tools offer unmatched agility and scalability. They enable rapid deployment, real-time updates, and low infrastructure overhead, which is ideal for businesses operating in SaaS-heavy environments. With built-in support for SCIM and APIs, cloud platforms simplify user access across distributed systems. They're especially suited for fast-growing teams with dynamic access needs.
- On-premise solutions, on the other hand, remain vital for enterprises with stringent compliance, data residency, or legacy integration requirements. These tools offer more control over data, support integration with older systems, and help meet industry-specific audit standards. While deployment is more resource-intensive, they provide the reliability and customization many regulated industries demand.
At Tech Prescient, we enable secure, real-time provisioning with tools that integrate into your existing identity governance stack, helping you modernize access control without disruption.
How to Implement Automated Provisioning
Implementing automated provisioning is not a one-click deployment; it’s a strategic process that requires coordination across HR, IT, and security teams. A successful rollout starts with defining roles clearly, establishing trusted data sources, and rigorously testing the access workflows. Here’s a step-by-step guide to get it right:
- Define Access Roles and Policies Before any automation begins, it’s critical to map out who needs access to what and why. Create standardized roles based on departments, job functions, and seniority levels. By doing this, you eliminate inconsistencies and guesswork when provisioning access. Policies should define entitlements, access duration, and approval workflows. These role definitions also support audit readiness and policy enforcement down the line.
- Connect Authoritative Sources (e.g., HRIS) HR systems like Workday or SAP SuccessFactors serve as the source of truth for employee identity data. Integrating them ensures that any lifecycle event, like hiring, transfers, or exits, triggers provisioning or deprovisioning automatically. Connecting your IAM or IGA platform to these systems allows for real-time, rule-based access updates. This ensures access decisions are always based on verified, up-to-date identity information.
- Test Workflows for Edge Cases Automated provisioning must go beyond the “happy path.” You’ll need to test for edge cases like contractor rehires, job role overlaps, temporary access, or emergency overrides. By simulating these scenarios during rollout, you avoid broken workflows that lead to provisioning delays or access leaks. Include both technical QA and functional stakeholder validation to ensure accuracy, consistency, and business fit.
- Monitor Logs and Conduct Regular Audits Even the most well-designed provisioning system needs ongoing oversight. Enable detailed logging of all provisioning activities, including who got access, when, and why. Set up dashboards and audit trails that help identify anomalies or policy violations. Regular reviews not only keep the system compliant with standards like SOX or HIPAA, but also tighten security by identifying orphaned or misassigned accounts.
Final Thoughts: Why It Matters in 2025
As organizations embrace Zero Trust security models, automated provisioning has become more than just an IT efficiency play; it’s now a foundational part of enterprise identity strategy. From enabling real-time access governance to supporting AI-powered decision-making, the right provisioning system drives both security and agility.
Platforms like Tech Prescient help future-proof your identity architecture by combining deep integrations, intelligent automation, and compliance-driven workflows.
Get ready to streamline and secure your identity lifecycle now.
Frequently Asked Questions (FAQs)
-
What is automated user provisioning?
Automated user provisioning is the process of granting and managing user access to systems, applications, and data using pre-defined rules, without manual effort, making onboarding faster, more secure, and consistent across the organization. -
What is the difference between provisioning and deprovisioning?
Provisioning gives users access to the resources they need, while deprovisioning removes that access when it’s no longer required; both are essential to managing the user lifecycle and maintaining security. -
What tools support automated provisioning?
Platforms like Microsoft Entra ID, Okta, SailPoint, and OneLogin support automated provisioning by integrating with HR and IT systems to enforce access policies, sync user data, and streamline identity management. -
What is the main benefit of automated provisioning?
The key benefit is reducing manual errors while improving speed, security, and efficiency in managing user access, helping IT teams scale operations without compromising control. -
How does automated provisioning support compliance?
By enforcing consistent access rules and creating detailed audit trails, automated provisioning helps organizations meet regulatory standards like SOX, HIPAA, and GDPR with greater ease and accountability.